| Home | The Book | Training | Events | Tools | Stats |
December 20, 2004
(In)SecurityHere's another trick that phishers and scammers try in the hope that the victim operates on auto-pilot rather than being even slightly suspicious. The image below is a snapshot for a PayPal phishing form in the Apple Safari browser.
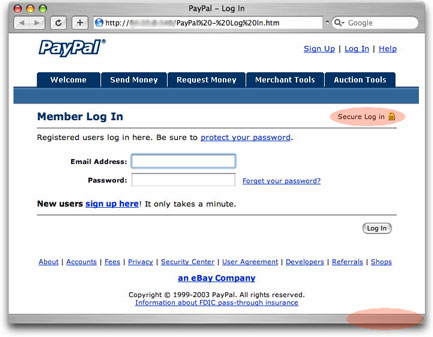
Note the reddish highlighted area near the top that says "Secure Log in" with a little padlock icon. I'll wager that lots of folks seeing this would believe that the current page is using the type of secure connection that the real PayPal Web site uses.
Bzzzt! Wrong!
There are two clues against this. First is the URL in the address box at the top of the browser window. The protocol is http:, not the https: that indicates the "secure socket layer" kind of connection. Second, each browser has its own way of indicating when it's connected through a secure connection. Safari has a bold black padlock icon and the name of the domain down in the lower right corner of the browser's border—missing in action in the snapshot. Other browsers usually have some kind of lock icon outside of the browser's display area.
I frequently wonder if secure connection indicators should be more obvious, like turning the browser's entire window border into bright hazmat yellow and black diagonal bars. The current indicators are so subtle that I believe a lot of users don't pay much attention to them one way or another, and could too easily be fooled by the trick in our phisher's form above.
UPDATE: I was reminded that Mozilla/Firefox browsers also turn the background color of the Address box a different color when you access a secure page. I actually use Firefox for my personal secure transactions and did notice this at one time. But even this indicator is too subtle, IMHO. Subtle enough for me to forget about it in the browser I use most often.
UPUPDATE: It also turns out that Internet Explorer 6 on Windows XP with Service Pack 2 can be vulnerable to a spoof that causes the browser to display a secure URL in the Address box as well as the secure icon where it's supposed to be...but the displayed page could belong to somebody else, including a scammer simulating the real page. If that page has a form asking for username and password, the form gets submitted to the Bad Guy. There are ways to lock down IE6 to prevent this kind of spoof (short of using less vulnerable, alternative browsers), but you'd have to be led to a trick site by following a link. Avoiding links in unsolicited email messages and popup windows is a good start. An even better start is to not view unsolicited messages in the first place, and use a browser (like any of the Mozilla derivatives) that has good popup blocking built-in.
Posted on December 20, 2004 at 08:35 PM
