| Home | The Book | Training | Events | Tools | Stats |
February 26, 2008
Macs Finally Getting ECrook Respect
A long-running thread in the malware world is that the Mac OS isn't a big enough target to attract malware authors. I don't subscribe to that belief, as I detail in Spam Wars. But I did see today clear evidence that another type of Internet crook—the so-called OEM software download seller—recognizes a market when he sees it.
The message is titled:
Subject: Hpg Hey you Apple Fans LTKS
Although I've seen some recent Subject: lines reference Macs, the message bodies hawked Windows software, typically Vista. Today's message, however, really spoke the Mac language:
Cheap Apple s0ft: iWork, iLife, .MAC etc.
The links were to oh-so-ubiquitous spammer blogspot.com sites. Per usual, the BlogSpot pages automatically redirected to the actual selling site—a domain supposedly registered in China, currently hosted in South Korea. This site is not Mac-specific. Instead, it's a full-service supplier of pirated, unsupported, un-upgradeable software of all kinds. There is, however, a Mac department.
Of course, the particular software products pitched in the email aren't particularly expensive, even at retail. It's certainly not worth the risk of your credit card data to attempt to buy this crap, thinking you're going to save twenty bucks. Additionally, remember that when you install a lot of Mac software, you are commonly presented with a dialog requiring your system password. That permission grants the installer free reign over your system. If any of this downloadable software contains some, um, extra, unadvertised goodies—malware—you'll have given it a free ride into your system. Every computer system is vulnerable if you give the bad guys the master keys.
Mac or Windows, I wouldn't let any of this "OEM" software come within a ten-foot pole's reach of my computer.
Posted on February 26, 2008 at 08:19 PMFebruary 25, 2008
419 Stupidity...Squared
Sometimes the bizarre-ness (bizarrity?) of an incoming scam spam is so high, I just don't know where to begin. There's something here for everyone.
First, the come-on:
Subject: ORPHANAGE PART TIME OFFER
From: ANN ORPHAN HOME PROPERTY
To make a long (and I mean long) story short, the pitch comes from someone claiming to be Richard Johnson who says he (now aged 75) runs an orphan home in the United Kingdom. The orphanage runs on donations. (At first, I thought this was just going to be a begging letter.) Mr. Johnson's problem is in handling donations that come from the U.S. because he says he has difficulty cashing U.S. money orders and bank checks in the U.K. What he wants to do is set me up to process deposits from his "business partners" into my U.S. bank account, deduct my percentage, and then wire the rest via Western Union.
He warns me that I had better not try to screw him out of the money:
But the problem i have is trust,But i have my way of getting any one that gets away with our money,i mean the FBI branch in Washington gets involved.
What he doesn't tell me is that the financial instruments arriving in my mail box will be counterfeit money orders, fraudulently-obtained funds (from defrauded online auction bidders), or simply rubberized checks. I'll be pressured to wire his generous portion of the amounts to him right away before the frauds are uncovered or the checks bounce back into my lap. I would never, ever, be able to recover the wired money, and my bank will wash its hands on the matter—after I've repaid the overdrawn funds and forked over bounced check fees.
The warning about them calling the FBI on someone for not complying is a real stitch. When I read that, I almost wrenched my funny.
As is often the case with 419 scammers, this one uses a free email account to open the line of communication. This one is a Yahoo! email account, with the username (get this): richardluvgirls2 (makes me wonder what ever happened to richardluvgirls1?). I mean, is this an appropriate handle for an orphanage owner? I think not.
A little bit of due diligence—all of two Google searches—proved enlightening.
First, this email address user ID has been on a few different 419 scams since November, 2007. Someone was actually contemplating visiting Nigeria to meet with whoever was using the email address. Yikes! (How has this account not been shuttered by Yahoo?)
Second, the bulk of the email message I received had been in circulation since at least last summer. The scammer's name and email address for earlier campaigns were different; our "Richard Johnson" had also done a fairly poor copy-and-paste from an earlier specimen to come up with today's entry.
This is where the typically bad 419 scheme mailing ends. But there's a topper for this one.
The To: field of the message contained 100 addresses in plain view (one of my pet peeves, as regular readers know). But whoever sold these addresses to our aged, orphanage-running schnook has a bit of a wicked streak in him. From all appearances, the addresses were harvested from an old newsgroup archive of SpamCop messages. Moreover, the harvesting appears to have simply looked for any unbroken string of characters surrounding an @ symbol. I recognized a few of the complete addresses as regular contributors, but most of them look like they were ripped from message header fields (Message-Id: in particular) that can't, in any way, evaluate to true email addresses. Most posters to spam-related message boards utilize intentionally obfuscated addresses to prevent their actual addresses from being harvested. It's not surprising, therefore, to find "addresses" in the To: field aimed at foobar.edu (go Foobar U!), an enforcement user ID at sec.gov, and SpamCop's devnull dumpster. Fewer than 10 of the 100 were real addresses, every one of which belonged to a spam fighter.
I'm comfortable predicting that the response rate from this batch of 100 messages will be zero. What I can't predict is how many additional 100-address batches this guy sent, and where those addresses originated.
The work-from-home "payment processing" scam still manages to attract victims. Given the downturn in the U.S. economy, high gas prices, and mortgage squeezes, a lot of email users may be susceptible to this con—or at least versions that are better-written and more believable on their faces than Little Orphan Richard's attempt. With this scam, it doesn't matter if you're a Windows, Mac, or Linux user. If you nibble at this bait, you'll be in for a world of hurt.
Posted on February 25, 2008 at 05:47 PMFebruary 23, 2008
Opting In Ticks Me Off
In Spam Wars I urge caution when confronted with forms that control your email preferences. In the past I have seen plenty of confusing, double-negative statements next to checkboxes that would take a logician to decipher. I thought that practice was a thing of the past, or at least relegated to really sneaky marketers.
Until today.
I registered at a web site that supports a British cultural magazine, to which I subscribe. The publisher behind the magazine produces a number of small-niche magazines that appeal (not to pat myself on the back) to a fairly intelligent clientele. Okay, we're downright snooty and snobby. But that's not the point.
What got my goat was a series of checkboxes at the bottom of the form. Disguising the name of the publishing house, here is what confronted me:
From time to time [removed] will allow carefully selected parties to contact you about their products and services. Please indicate below your preferences.
The initial state of all three checkboxes is unchecked. If you read the first one and don't want to get emails, then you'll leave it unchecked. But if you assume that leaving the remaining two unchecked also keeps you off the lists, you'd be mistaken. To be kept off all lists, you have to use the correct matrix: no-tick, tick, tick (I think).
That's downright disgusting. There is no need to introduce asymmetry to the selection process—except to confuse or deceive registrants. Shame on this web site form and its perpetrators.
[BTW, the business in the wording about "work-related direct mail" acknowledges fine points of British anti-spam laws. Work-related and general consumer unsolicited email have different protections under the law.]
This outfit has turned a previously happy paying customer into someone suspicious of its every move. Good work, chaps!
Posted on February 23, 2008 at 09:47 PMFebruary 19, 2008
IRS Refund Scam: Old Wine, Old Bottle
It's déjà vu all over again, but with monetary inflation thrown in for good measure.
Yes, here in the U.S. we're nearing income tax season. We have the Internal Revenue Service (IRS) on the brain, and it's usually not a good feeling, either because we owe money, or we have to fill out those infernal forms by April 15th.
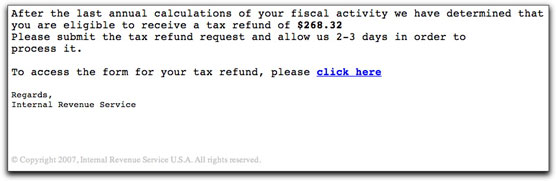
Ah, but a crook is here to brighten our day (and lighten our sense of personal identity security). Our inbox shows this initial bit of info, which might be unnerving:
From: "IRS" <service@irs.gov>
Subject: IRS Notification - Fiscal Activity
"Fiscal activity?" What could that mean? We rush to open the message, which at least bears no attachment.
Inside we find the latest version of a con:
I say "latest version" because I displayed a more artfully crafted instance from almost two years ago here. Notice that the amount has risen by over a couple of hundred smackers.
The URL behind the "click here" is to a hijacked Romanian web site. And, damn, if it doesn't look legit (except for the .ro URL, that is). The first screen pulls the IRS logo from the real IRS site, and many of the links point to irs.gov, as well:
The amount of this supposed refund is duly and prominently displayed on the page. There was no indication of the amount being passed along to the phony site in the link URL, so I guess everyone is getting a $268.32 refund on this campaign. Whoopee!
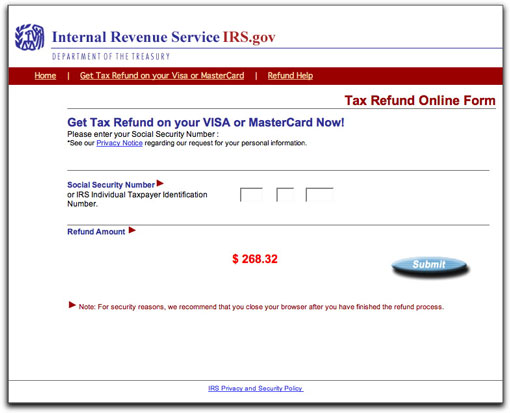
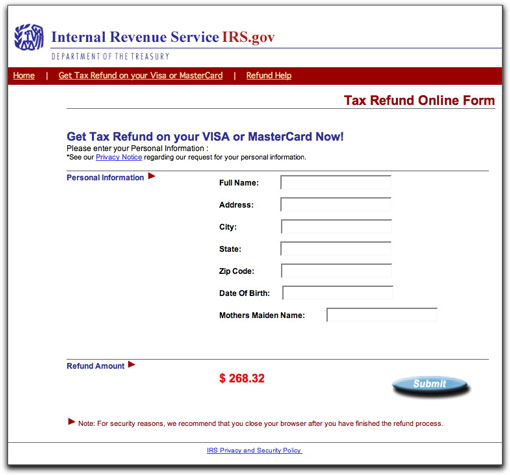
If you're dumb enough to fill out the first page with your Social Security Number, you'll proceed to the next page, where additional identity data is requested of you:
It's kinda funny that the IRS wants your mother's maiden name here, yet they do not collect that information on otherwise invasive tax forms. But, ooh, that logo looks real, and the Submit button has a drop shadow. It must be legit, right?
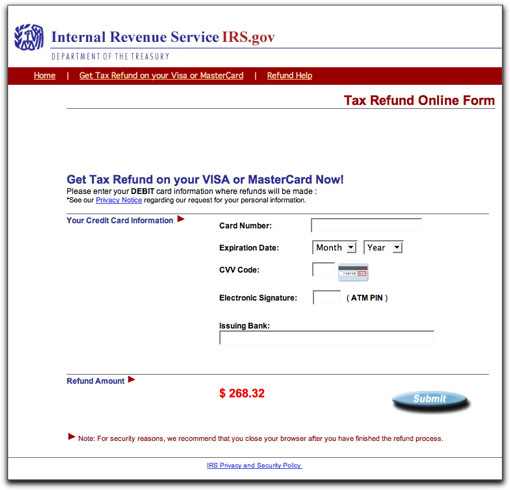
Onward to page three, where you are asked for your credit or debit card information:
The program running behind these pages is not merely a form-data-grabbing automaton. It actually tries to verify that the credit card number you provide is a valid number (or at least valid first eight digits). It simply won't accept totally bogus numbers.
I get a kick out of the Note at the bottom of these pages, recommending that you close the browser after submitting the refund request. I think that's to prevent the casual user from accidentally noticing after the fact that the URL in the address bar isn't irs.gov or anything close.
If this seemingly complex web site seems like a long way to go to capture personal identity and credit card data, you'd be right. But it means that such data is still valuable enough to make it worthwhile for someone, somewhere to develop the software behind this activity. This is most likely a kit of some kind that anyone desiring to rip off people from their home-based business can find on the Internet. Thus, the "kingpin" behind it all collects moolah no matter what—and, as has been detected elsewhere, may even be stealing the captured data from the kit buyers who do the legwork installing the kit on hijacked servers and paying for the botnet mailings.
So, what's the difference between the IRS refund scams of 2006 and 2008? Simply the promise of a $204.52 larger refund.
The value of identifying a scam when you see it? Priceless.
Posted on February 19, 2008 at 05:41 PMFebruary 18, 2008
Lots of Undetected Malware Attachments Floating Around
For about the past ten days, I've been receiving numerous messages with From: fields identifying the sender as coming from my domain, and content bearing password-protected .zip files. Unfortunately, most of the big-name antivirus products don't appear to be identifying these attachments as being evil. The sender is trying various social engineering tricks to get recipients to open the attachments. The tricks aren't anything new, but they bear repeating, especially for those who don't normally get this kind of stuff. Here are my observations.
First, the From: fields all have an address bearing @dannyg.com, signifying to me that the program used to send this garbage automatically plugs the recipient's domain into the forged From: field. Account names used with the sender's supposed address are names such as info, mail, service, news, and admin. I try to put myself in the shoes of an employee at a small company with its own domain. How would I react to receiving a message claiming to be from service, mail, or admin @ my company's domain? The sender hopes I'll feel comfortable believing that the message is coming from inside my own world.
[Examination of the message's header, of course, reveals that the message originated from anywhere but inside the recipient's email system.]
At this point, the recipient's guard may be reduced a bit. How about the Subject: lines? Here are some that I've seen:
- Account Error ID#5203
- You've received an E-Card from a dear friend.
- Your Membership Details!
- Free one year trial
- Visa and Mastercard and Amex news
- Sorry your account has been suspended
To a trained eye, these lines are immediately bogus. But to the casual email user, a few of these are really eye-catching—especially because they have the "stamp" of being "from" his or her own domain. There's no doubt about it: a goodly number of these messages will be opened.
What's inside these messages?
All of them include instructions like this:
Please use the following password to read the attachment
Password: 2960
[In the more than half-dozen samples I've seen, the so-called password numbers are all different. Frankly, I don't even know if the password is required to open file successfully because I won't try it on a Windows machine here. The file doesn't open at all on a Mac.]
Several messages I've seen have additional verbiage that makes you wanna open that attachment:
The message cannot be represented in plain text because it contains personal and sensitive data, so the message has been attached. The message has been sent as a secure passworded attachment. Partial message is available as a secure passworded attachment.
Again, put yourself in the shoes of a reluctant email user at a small company. A message arrives claiming to be from "admin" within your company's domain; the Subject: says that your account has been suspended; the message body says that the message can't be shown because it has personal and sensitive data, requiring you to open it via a password. You're already terrified by (or disgusted with) the IT department (that must be where "admin" is, right?), so you open the attachment.
And here's where the pain really begins.
I've run a few of the attachments through VirusTotal as they arrived. Sadly, each new variant I received failed to be recognized by most of the major antivirus programs. Tonight's release wasn't caught by Kaspersky, Microsoft, Sophos, or Symantec, to name a few of the biggies. It's possible that some of these products will detect problems once the attachment attempts to worm its way through your system, but I'd be pretty nervous to be alerted after the fact, because you simply can't know if a new undetected process running alongside slipped under the radar.
Telling your email users (and your emailing mother, for that matter) not to open attachments is insufficient warning when recipients are faced with the types of mind games inflicted by the creators of these campaigns (to generate more botnetted zombies). Training for email users needs a far more proactive approach so that safe email handling behavior becomes automatic.
Posted on February 18, 2008 at 11:20 PMFebruary 17, 2008
Beijing Olympics Scams Ramping Up
Nothing makes for a great come-on like a hot topic. The upcoming Beijing Olympics has already been in the news for various reasons. As expected, scammers are eager to ride those coattails to riches.
I just saw a 419 lottery scam using the Beijing Olympics as the primary hook:
Subject: CHINESE OLYMPIC COMMITTEE LOTTERY DRAWCHINESE OLYMPIC COMMITTEE LOTTERY DRAW
2008 BEIJING OLYMPIC GAMES
CHINESE OLYMPIC COMMITTEE LOTTERY DRAW
REF #:-EU/2457/2008/008This is to inform you that your Email ID has won US$1.5Million in the
second dip of our computer ballot email lottery with the said winning
number giving below;
[more blah blah blah]
Yet, in keeping with tradition, this lottery claims to be run out of The Netherlands. One is to mail his or her claim for this prize money to a free aim.com email account—how official for Postbank NL!
So, get ready to be inundated over the next several months with Beijing Olympics This and Beijing Olympics That. Confucius say: "Delete!"
February 10, 2008
The Art(lessness) of the Subject Line
Once a spam message squeaks past server and client spam filtering, the message's Subject: line is the spammer's primary weapon in overcoming human defenses. There are plenty of obvious spam Subject: lines, but the craftier spammer uses every trick in the book—including illegal (in the U.S.) deception—to lure recipients to open the message.
Although I can spot 99.9999% of spam messages by my combined spot check of the From: and Subject: data in my inbox list, I know that it's not always possible for others to do the same, even if they are very spam aware. Many email users in their jobs receive valid business-related email messages from customers or colleagues whose names they don't recognize by the From: field and what in other situations might look like total spam Subject: lines. Thus, it's vital to protect yourself from the spam message that gets opened through no fault of your own—and very often through the deception of the spammer.
I decided to get a view of the Subject: lines that came my way in a recent 24-hour period. This data is preserved in my mail server log, which is one of the data sources I use to assemble daily data for the Spam Stats page at this site. The Subject: lines of all messages that get processed (including the ninety-some percent of the ones that get immediately trashed at the server) are preserved.
If you're interested in the hard data, you can download the 100KB text file containing all the Subject: lines for Friday, February 8, 2008. I've sorted them alphabetically, which reveals when I get flooded with the same message from the botnets. It also indicates at a glance which opening words are used most often.
There is a huge batch of Russian-language spam (using the koi8-r character set). This past week, the floodgates opened from Russia (without love) to my addresses. Too bad for them that their messages are so easily detected and trashed at the server.
Opening words "get," "save," and "we have" are the most common. Of the nearly 2500 messages, 53 claimed to be replies (Re:) to messages I never sent. Here are some other counts:
- 184 contained "medications," "meds," or "medz"
- 108 contained the string "hydro" (as in Hydrocodone)
- 82 contained "pain" (usually with "killers" or "relief")
- 46 contained "weight" (with variations of "lose")
- 32 contained "sex" (mostly for meds)
- 47 contained "debt"
- 1 contained "mortgage" (see this dispatch)
- 23 contained "hey" (because I wouldn't see it otherwise)
- 24 contained "penis"
- 6 contained "dick" (and none referring to someone named Richard)
- 101 contained "save"
- 31 contained "free"
- 29 contained "discount"
- 23 contained "replica"
- 23 (different ones) contained "Gucci"
- 7 claimed to be confirmations for things I didn't order
- 5 times I won money (uh huh)
- 10 were Subject: nipples why guys got them
Some Subject: lines really troubled me because of the harm they are likely to inflict on unsuspecting and trusting recipients. Perhaps the most troubling was this one:
Subject: Free Bible Software - Just Download and Go
I didn't see the three messages bearing this or similar Subject: lines, so I can't say for sure what the payload is. I'd wager that it can't be goodware that gets installed. Preying on people's faith to get them to screw themselves is despicable (as many 419ers know to do).
Did I really learn anything from this exercise? Hmm, probably not. I did find it interesting to slice and dice the data in this manner for the first time, but it's not something I'm likely to do often. The results certainly reveal that spammers don't seem to care that they are sending the same message over and over to the same recipients on the same day. With the incremental cost of one spam message sent through a world full of bots approaching zero, it's probably chepaer to not better manage the process.
I do, however, enjoy the fact that spammers are wasting some of their resources, no matter how small. That all but about 50 of the messages listed in the downloadable file were deleted before they ever reached a server directory or file is a great source of glee. I would be even happier if not one of these messages addressed to other recipients triggered visits to spamvertised web sites. Response has to drop to zero for an extended period before the spammers will start to look for other ways to steal.
Posted on February 10, 2008 at 06:36 PMFebruary 08, 2008
Russian Girl With an Identity Crisis?
First came a lengthy broken-English plea from someone identifying herself as a Russian named Nelya. She included two photos of herself, one of which I show here. I won't reprint the second photo, but suffice it to say, I can report that she has a piece of jewelry in her pierced navel.

The gist of her plea is that she is unable to find a suitable mate in Russia, and a TV program advised her to use a marriage agency to find a man in other countries. She claims that her intentions are pure:
Money not the most important for me during this life. During this life I want happiness, I want love, I want relations and happy family.
The agency gave her my email address because "you also search the woman for your life." Since "I can not use a computer well" she had to get help from the manager of an Internet cafe "to create to me a letter box."
She signs the letter "The lonely woman from Russia Nelya!" and provides a gmail address.
Eleven hours later, I receive another message. It's the same letter. Same photos. Same navel jewelry. But now her name is Julya with a different gmail address.
Or is it perhaps her identical twin sister? Oh Happy Day!
Posted on February 08, 2008 at 11:17 AMFebruary 07, 2008
Brand Name Rewards Spam
As a follow-up to yesterday's airline confirmation spam, I want to make clear that Southwest Airlines had nothing to do with the offer or the spam. Nor did Apple have anything to do with today's installment of the same type of crappage:
Subject: Test and Keep your Apple MacBook Air

I guess Apple couldn't find anyone to test a MacBook Air. Yah!
These "with participation" spams use the good brand name of a company whose products or services consumers like and trust in order to coax recipients to open the message and then act. The brand-name companies don't have a clue that their products are being spammed until after the fact. I've seen spammers wave high-value gift cards (Target and Macy's before last Christmas) and tickets to popular TV shows, such as Oprah (I believe that it's in violation of FCC regulations for TV show tickets to be anything but absolutely free) as lures to grab "participants" (a.k.a. greedy people wanting something for nothing—which turns out to be not for nothing). The brand name always appears in the Subject: line to make sure you see it in your inbox.
Spammers who operate these programs in the open (i.e., they provide CAN-SPAM compliant identities and addresses) include disclaimers that apparently keep the brands' and FTC's lawyers at a sufficiently safe distance. The outfit trumpeting Southwest Airlines' brand yesterday included a notice in the email message that it "is not affiliated with, sponsored by or endorsed by any of the listed products or retailers." This statement is in the grayed-out fine print that no one (except me) reads.
Companies that send these spams call their activities "rewards programs." Reward, as in a treat they toss to a dog for rolling over. As in the $20 they leave on the nightstand at an hourly-rate motel.
Posted on February 07, 2008 at 08:52 AMFebruary 06, 2008
Flying Close to the Sun with Wax Wings
Here's a simple two-part quiz.
Q1. What does the following email Subject: line mean to you?
Subject: Airline confirmation: southwest airline confirmation
A1. In the travel biz (and elsewhere), a confirmation is an acknowledgment of an existing reservation; it's an assurance that a seat, a car, a room is being held in your name. True, sometimes there are snags (e.g., overbooking), but holding that confirmation gives you the power to really get in the agent's grill with your demand for whatever it is the outfit has confirmed.
[TV game show bell, signifying a correct answer.]
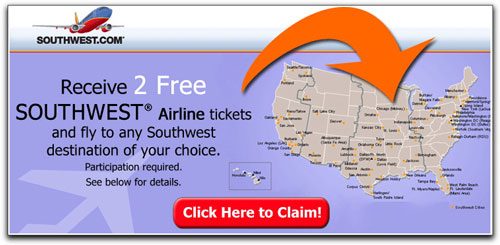
Q2. What does the following image in the message body mean to you?
A2. Oh goodie! I can click the red button (actually, a flashing animated image in the original) to claim my two free Southwest Airline tickets...tickets that (according to the Subject: line) have been confirmed! Woohoo!
[Loud TV game show "wrong answer" buzzer sound.]
Oooh, sorry. No, the correct answer is "Ugh, I'll have to jump through hoops from now until Julune, hand over all the email addresses of my friends to spammers, and probably buy stuff first."
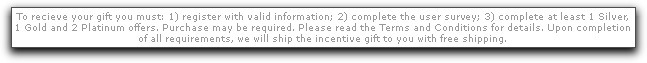
The "details" are presented in small, gray text (and in a spelling-challenged way):
"Free" may not be exactly free, certainly not when you measure the time you'll spend completing the various precious metal offers. And that "Purchase may be required" stipulation? "Maybe" my eye.
The FTC recently settled with a company making similar offers. To the tune of $200,000. According to the FTC press release:
When consumers arrive at Member Source Media's promotional Web pages, they are led through a series of ads for goods and services from third parties. To "qualify" for their "free products," consumers must first wade through pages of "optional" offers. If they clear this hurdle, they discover that they must "participate in" a series of third-party promotions that requiree [sic] them to do things such as purchase products, subscribe to satellite television service, or apply for multiple credit cards.
It's unclear to me if the offenders in the recent FTC action mentioned the "participation" business in their email messages. It could be that our Southwest Airlines offer spammer includes these disclaimers to stay just this side of last month's ruling. I also haven't visited the site to see how they state their offers and details—links are heavily coded with an identifier for my email address, and I don't want to validate it as being a good one.
But, even if they tell you up front what hoops you will be jumping through, I still have an issue with the Subject: line of this email message. Part of the FTC complaint addressed deceptive headers in the other case, leading me to hope that there might be something for them to look into here.
The CAN-SPAM law has had a weird effect on different types of email marketers. Those who use genuine confirmed opt-in mechanisms to stay in touch with their customers have been sweating the details to make sure they comply with the law completely and unambiguously. Then you have the spam mills operating in the open who seem to want to test just how high their Icarus-like wax wings will let them fly. Is there a potential upside to global warming?
UPDATE: See the follow-up to this entry.
Posted on February 06, 2008 at 10:13 AMFebruary 05, 2008
Impending Boom/Doom Tricks
Spammers desperately want you to open their messages (the ones that get through spam filters) and then trick you into performing whatever action will get you to give up something of value, even if it is just a click of a link. Among the most deceptive tactics that seem to work (because they continue to be used year after year) are the Subject: lines and message bodies that promise impending boom (e.g., lottery windfall, love of a secret admirer, free iWhatever) or impending doom (e.g., verify your account info or else, IRS documents attached, "Dude, you're gonna get caught, lol").
Resisting these false come-ons can be difficult, especially those of the impending doom variety. They typically arrive with enough of a believable warning and not enough information to get that mouse button a-clickin'. After all, no one wants to be accused of doing something wrong, especially when, dammit, they've done nothing wrong.
The following spam message that came my way will certainly get lots of adrenalin flowing in recipients (linked domain partially obscured by asterisks):
From: Catherine Gill (Investigator)
Subject: Alert: Account LockedURGENT - February 4th, 2008
Hello, we have been informed your credit has been suspended.
All credit cards and credit lines are curently locked.
Until the current investigation is completed, we ask for your
patience.Thank you.
John O.http://www.*****debtrepair.net
Let's face it, the U.S. economy is in a downturn, and more than a few people are having tough times financially; for many consumers, their credit cards are a lifeline. Spammers know this, and are eager to prey on these financial fears.
Recipients of the above spam message will be too freaked out to notice the spamminess of the message (too many red flags to mention). Instead of doing the right thing—checking directly with their credit card companies to find out if the claim is true—they'll click the link because it's easier than wading through automated telephone menu systems at the credit card companies.
The identity of the spamvertised domain owner is hidden (never a good sign of legitimacy for a commercial venture). Upon checking the source code of the site, it turns out that this is simply a lead-generation site for debt consolidators. There is nothing there about you or your accounts being frozen. Instead, you are invited to fill out a form with your name, email address, phone, and a couple bits and bobs about your current debt (how much it is and how late you are). By submitting the form, you agree to be contacted by phone by up to three debt consolidators—even if you are on the FTC Do Not Call list. Oh yeah, they got their bases covered (at the site anyway, their email exhibits multiple violations of CAN-SPAM).
It's clear that lead-generation spammers have abandoned the mortgage game in favor of the debt consolidation game—simply riding the economic wind currents. They get paid richly for the leads they generate through this 100% deceptive email advertising. There oughta be a law against...oh, wait, there is.
Posted on February 05, 2008 at 09:21 AMFebruary 04, 2008
Why I Don't Use Google Ads at Spamwars.com
Some of my friends think I'm crazy for leaving money on the table by not including Google ads on this site. It is true that I am a control freak, and it is the lack of control—or need to continually monitor what's going on—that gives me pause.
I was reading a news item at an online security magazine called SC Magazine. The article relayed findings from a security researcher about previously undisclosed not-very-nice things that recent RealPlayer 11 installations were doing behind user's backs and under their noses (a verbal M.C.Escher image). At the end of the article was a box with three Google advertisements in it. All three invited users to download RealPlayer—more specifically, "Real Player." Not one of the three links pointed to Real's site, but all three domains had "realplayer" in them. I don't know what you get when you visit those sites, and I'm not about to find out.
Given the keywords that appear in my blog entries, I shudder to think what ads would appear on my site. No thanks. I'll peddle only my own fish here.
Ads by Goodman
Buy my book and bring me in to train your colleagues on email safety.

When most email users receive a message from an unknown sender (as displayed in the From: field in the inbox list) with the following subject:
Subject: Your Receipt No.30345387
they'll open the message to see if there was a mistake of some kind. "I didn't order anything," they think to themselves in a huff (or in whatever else they're wearing). The message body, of course, doesn't provide any details about the alleged transaction; only the following:
Mon, 4 Feb 2008 05:45:40 +0500http://[removed].com
I'd wager that at least eight out of ten recipients couldn't tell you what time zone is being referred to in the time stamp. Not that it really matters, because the "time stamp" is as phony as a $3 bill. But it does look sorta official if you don't know what it means—look at all those numbery things!
The spamvertised domain name isn't one that anyone could recognize, consisting of a mashup of two essentially random English words. A check of the domain registration shows it to be supposedly owned by someone in China, in particular, a name I've seen on so many spam domain registrations (including these), I'm beginning to wonder if it's the Chinese equivalent of "John Doe."
Checking the source code of the spamvertised web site, I see that it is one advertising itself as "Canadian Pharmacy." Based on the huge lists of pills and maladies written into the code, it looks as though if you have any condition whatsoever, they have medz for it.
To assuage the hesitations of a potentially cautious consumer, the page includes a Frequently Asked Questions section. Some of these are rich (English majors, be prepared to wince):
Why is your product so cheap?
There is a number of reasons for that. We do not spend anything on marketing, there are no taxes to be paid as the product comes into the country unregistered, the manufacturer is located in an offshore zone and the production costs are way lower. No child labor is used.
Oh, I feel so much better that you claim child labor isn't being used. Offshore apparel makers claim the same thing...until the factories get busted by the authorities.
Where are your Physicians Licensed?
Our physicians are U.S licensed. We use only board certified physicians and U.S licensed pharmacies.
Wait a minute! Since when are Canadian pharmacies licensed by the U.S.?
At the bottom of the page they clear up the licensing issue (Not!):
Licensed by The College of Pharmacists of British Columbia.
The page even includes the true address and phone number of the real College (although not of the pharmacy, itself). At the College's web site, you can download a list of licensed pharmacies. Horror of horrors: Canadian Pharmacy is not listed!
There is also a link to a page explaining their "Anti-spam policy," where they swear up and down that they support "ONLY permission-based email management practices." They (obviously) strongly encourage using the unsubscribe form to be removed from the list. And if you believe that your email address will be completely suppressed, there is a beautiful red bridge at the mouth of San Francisco Bay I'd like to sell you.
By the way, according to the source code, the main page also includes a Flash gizmo. I wouldn't put it past this spammer to have wired that auto-downloadable object to attempt to install malware onto susceptible PCs. As it is, if visited with a JavaScript-enabled browser, the page passes along quite a few technical statistics of your browser without your knowledge.
The amount of deception used in the original email and then on the spamvertised web site—not to mention the potential peril to which you expose yourself by actually buying and ingesting the pseudo-medz offered there—is off the charts. Sadly, even if I had my way of teaching every email user on the planet about how to avoid being sucked into these schemes and spammers started falling by the wayside, the last spammer on Earth would be a medz spammer who supplies bogus medz from outside the U.S. And I don't mean from Canada.
Posted on February 04, 2008 at 09:36 AM