| Home | The Book | Training | Events | Tools | Stats |
September 23, 2011
The 419 Amateur Hour
Long before American Idol, America's Got Talent, and similar reality TV shows, were radio and TV broadcasts called "amateur hours," where unknown performers of all types would compete for the home audience's postcard votes. Alas, I'm old enough to remember seeing The Original Amateur Hour hosted by Ted Mack.
The term "amateur hour" is commonly used today to describe an attempt to appear professional, but failing to make the grade in a face-plant kind of way. Such is the attempt of a 419 advance-fee scammer whose email came my way today. Unlike the more typical 419er, this guy went a few steps further to build out the story behind his scam, including building a custom web site trying to be that of the financial institution where the pot o' gold is (not) being held.
Let's start with the email message:
From: wilsonbongani_financier@[removed].mn
Subject: THIS MESSAGE IS NOT SPAM IS FROM SALAM SECURITY DEPOSIT BANK SOUTH AFRICA (REPLY URGENTLY)
I am Mr. Wilson Bongani the Financial Officer SALAM SECURITY DEPOSIT BANK (www.salamsd.co.za)
Address- N0. 13 Embankment Road Centurion Pretoria Republic of South Africa
Tel- +27-730-[removed]
Fax- +27-886-[removed]DATE: 23/09/2011
Good Day,
I the undersign Mr. Wilson Bongani the accountant officer to late Mr. Tarek Muhammad Aldaghdadi, the citizen of Saudi Arabia the contractor, who perished in a plane crash ( Concorde Air Flight Af4590) with the whole passengers aboard on 15-Oct-2008. And for your perusal you can view this wesite:
http://news.bbc.co.uk/1/hi/world/europe/859479.stmFinal meeting held on 20th of September 2011with our Bank and South Africa legislature representatives Dr. James Henry, Agreed that after this year 2011 if nobody come up for the claim of Late Mr. Aldaghdadi funds South Africa Government will take over the funds on 20th January 2012 based on Art 47.2 1993 of the penal code of Gauteng High court.
As per South Africa Government legislature all assets from deceased party who does not possess a (will) we be taken over by the South Africa Government after 4 years if not claimed by direct bloody or relative relations/business partner or next of kin. I write to inform you that the Bank authorized me to look for his business partner/next of kin for the inheritance of US $4.800,000.00 ( Four Million Eight Hundred Thousand United States Dollars) deposited with our Salam Security Deposit Bank here in South Africa.
In view of this I got your contact through a trade journal and I have agreed to give you 50% of the total of the money if you can handle this transaction in ultimate sincerity and secrecy. upon the receipt of your response, I will tell you the next step to take and I will not fail to bring to your notice that this business is risk free and that you should not entertain any fear as all modalities for fund transfer can be finalized within five working days, after you apply to the bank as a business partner to the deceased.
Please treat this with utmost confidentiality and send me the following information’s
{A}. YOUR FULL NAME:
{B}. YOUR ADDRESS;
{C}. YOUR DIRECT CELLPHONEAs soon as I received all this details I will proceed the immediately
Thanks / Regards,
Mr. Wilson Thabo Bongani
CFO Salam Security Deposit
Te- + 27-730-[removed]
Fax- + 27-886-[removed]
Private Email- wilsonbongani_financier@[removed].mn
He starts off on the wrong foot in the Subject: line of the message, as I've written previously.
Endemic to this type of scam appeal are the reference to a real-life tragedy (complete with BBC news clip from July 2000, not October 2008, doofus) and the frequently clumsy language (a poorly worded reference to a "bloody relative" is my favorite).
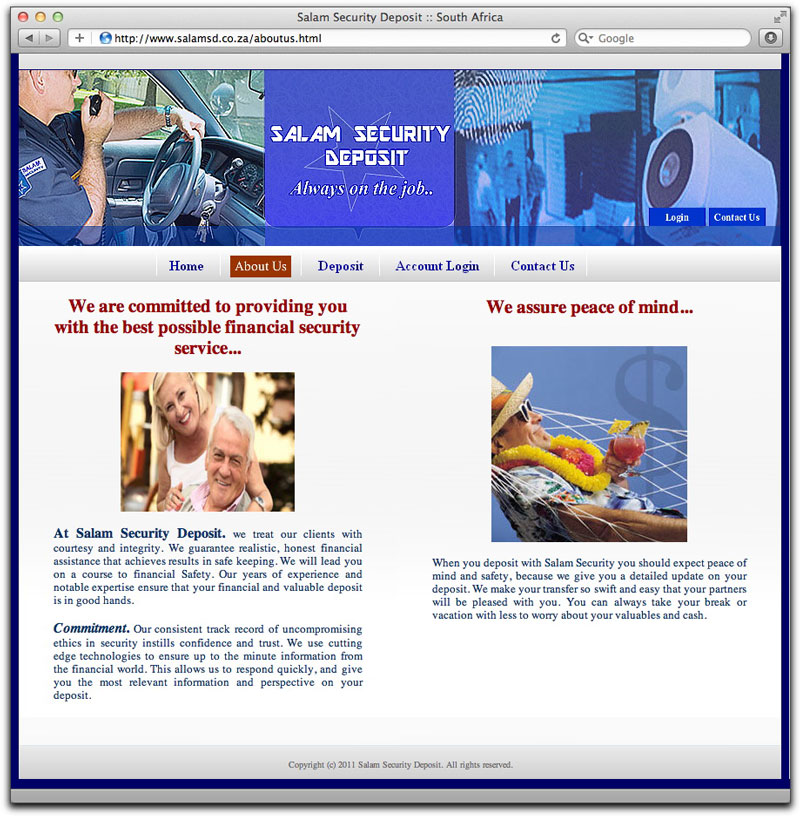
I was curious about the link to Salam Security Deposit Bank. Of course I've never heard of the outfit, but that doesn't mean it might not exist. It's typical of a 419er claiming to represent a financial institution to hijack the good name (and address, but not telephone number) of a real bank. After checking the site for safety, I viewed it in a browser. Here are some sample pages from the site:
Can you say "stock photos"? Most of the images — including those of the supposed officers of the company — are scaled incorrectly so they stretch. I couldn't imagine anyone in charge of the image of a financial institution's web site would let that go. The "peace of mind" photo isn't exactly dignified for a serious financial institution.
And then there's that image of the security officer at the upper left. Odd, isn't it, that the vehicle of this allegedly South African country is a left-hand drive in a country where right-hand drive prevails? Besides, what the hell does a home security guard have to do with bank deposits?
If you bother to read any of the text, it's boilerplate mumbo jumbo that one would use to play buzzword bingo. It says lots, but really says nothing.
Page design is something out of the 1990s. So is the Dreamweaver code.
Finally, what's the likelihood that someone named Golden would found a firm with a distinctly Arabic name? Shalom, maybe, but not Salam.
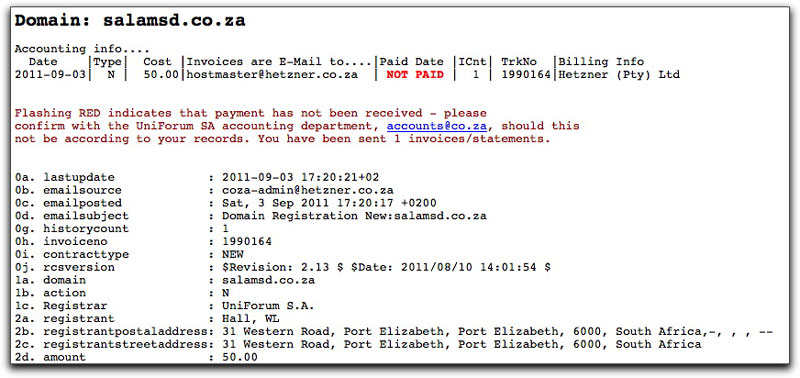
Among the other things I do with a suspicious web site is check the domain registration. That's where I got another laugh. The registration records begins thusly:
Oops! It appears that since they opened the domain earlier this month, they have yet to pay for the registration. Not too good for a "financial planning and depository firm that prides itself on unparalleled service and performance." Maybe the 50 Rand fee (just over 6 U.S. bucks) is too much for the firm to handle or they lost the combination to the vault.
So, our little 419 scammer exerted a bit more energy than most. Unfortunately, the result is poor. As, I hope, will be the response to his con game.
Posted on September 23, 2011 at 05:18 PMSeptember 20, 2011
Fake Western Union Transfer Notification
Yet another attempt to trick [greedy, lazy, feeling-lucky, down-but-hopeful] recipients to open an email attachment that is going to take over your Windows PC:
From: Money Transfer Notification 648
Subject: Western Union: Money Transfer For You
Advice Note!
Dear Client , You have received a remittance, more information about the money transfer is in the attached file.
Money Order can be cashed at any branch or bank in Your city
With Respect to You , Western Union Holdings Inc[Attached File: WesternUnion_personal-1703114.zip]
Numbers in the above (the From: field and attached file name) likely change from message to message. VirusTotal shows only about 36% coverage at this hour.
Sorry to burst your bubble: Anonymous money gifts do not fall out of the sky. Anonymous Trojan loaders, on the other hand, are a dime a dozen.
Posted on September 20, 2011 at 10:23 AMSeptember 12, 2011
Fotos of Girls Attached...NOT!
This campaign started up yesterday. Frankly, it's a little confusing, but the goal is the same: to trick recipients into opening an attached file claiming to be one thing, when in truth it's a Trojan loader.
The email begins with a claim that you are registered as some domain you've never heard of. I think they meant registered at rather than as, but that's just me trying to read between the lines. Then comes some statistics about the supposed girl sending the message. Her status is "ONLINE", along with thousands of other girls. A variable number of "fotos" are attached. Here are a few examples (misspellings left intact):
You are currently registered as: latinloveline. com
- Age: 27- Neme: Madie
- Seeking: A Male. Group 23-49
- Status: ONLINE
- Service: latinloveline. com 9419 Girls Currently Online
- Fotos: 4 fotos in attached file.
- Title: "Cam2cam
I am sweet, single, open minded, sexy and most importantly I am HOT! I have many suitors and still undecided on whom to be my BF and sex My Turn On's... "
===================================
You are currently registered as: fling. com
- Age: 23- Neme: Latrina
- Seeking: A Male. Group 18-46
- Status: ONLINE
- Service: fling. com 4161 Girls Currently Online
- Fotos: 8 fotos in attached file.
- Title: "I am an event coordinator ready to coordinate some events for us. I have a lot of outdoor fun planned followed by more fun in the bedroom or any room ... "
===================================
You are currently registered as: asianloveline. com
- Age: 29- Neme: Mandi
- Seeking: A Male. Group 23-48
- Status: ONLINE
- Service: asianloveline. com 7759 Girls Currently Online
- Fotos: 4 fotos in attached file.
- Title: "Hi guys im very hot and sexy....
i see my self very much sexy and attractive...and im fun to be with in bed..i can fullfill your fantasies babe..... "
I laughed when I saw the target demographics because I'm well past the top end. I might have a skin tag that falls within the range.
Alas, I suspect this campaign will be relatively successful in attracting new PCs to a network of remotely-controlled computers. Although the Trojan file has so-so coverage by antivirus products, my guess is that a high percentage of recipients who are fooled into opening the attachment aren't sufficiently protected.
Attachments from unknown senders are killers. Pass the word...to everybody.
Posted on September 12, 2011 at 09:57 AMSeptember 08, 2011
The ACH and NACHA Pestilence
By now, every email user and his/her mother must have received a message referring to something called an ACH transaction. Here are a couple of recent samples:
From: "account manager" <account.manager@nacha.net>
Subject: NACHA security nitification
Dear Valued Client,
We strongly believe that your account may have been compromised. Due to this, we cancelled the last ACH transactions:
-(ID: 31832211)
-(ID: 59887961)
-(ID: 20998130)
-(ID: 31053612)initiated from your bank account by you or any other person, who might have access to your account.
Detailed report on initiated transactions and reasons for cancellation can be found in the attachment.
[Attachment: Report-8764.zip (12KB)]
From: "account manager" <account.manager@nacha.net>
Subject: ACH Payment 7073592 Canceled
ACH Payment Canceled
The ACH transaction (ID: 96840217), recently initiated from your checking account (by you or any other person), was canceled by the other financial institution.
Rejected transaction
Transaction ID: 8574210513218
Reason for rejection: See details in the attachment
Transaction Report: report_082011-65.pdf.exe (self-extracting archive, Adobe PDF)
13450 Sunrise Valley Drive, Suite 100 Herndon, VA 20171 (703)561-1100 2011 NACHA - The Electronic Payment Association
The real NACHA (at nacha.org) oversees electronic payment rules used by financial institutions. I doubt many consumer recipients of these malware-laden email messages have heard of NACHA or the ACH (automated clearing house) network through which payments flow. That only ramps up a recipient's curiosity about the attachment, and the crooks know it.
Unfortunately, the Trojan loader attachments have been updated daily (if not more frequently) to evade detection by antivirus software. It's not uncommon for a fresh attachment to be recognized by fewer than 20% of the products tested by VirusTotal for many hours.
The perpetrators of this trick really hope to hit the motherlode by reaching the inbox of a corporate worker who knows about the ACH network and is involved with financial transactions. Once the crooks have slithered their way onto victims' PCs, all kinds of logging code can be loaded onto the machines, and the serious thievery can begin (e.g., initiating bank transfers to money mules).
NACHA is well aware of these scamming email messages. Here is the important part of their message to potential victims:
NACHA itself does not process nor touch the ACH transactions that flow to and from organizations and financial institutions. NACHA does not send communications to persons or organizations about individual ACH transactions that they originate or receive.
In other words, any message you receive about an individual transaction claiming to be from NACHA is completely bogus. That should be enough of a signal to the smart email user that the attachment should be avoided at all cost.
Posted on September 08, 2011 at 10:31 AM