| Home | The Book | Training | Events | Tools | Stats |
December 31, 2008
Bank of America Phisher Wants it All!
There are phishing forms and there are phishing forms. To escort 2008 out the door, today's Bank of America phisher hijacked a skateboard park site to host his brand of reach-into-your-soul-and-yank-it-out form. To arrive at this form, an unsuspecting BofA customer would have to not notice that the usual two-page login sequence was not followed. Only the first, "Enter Online ID" page appears, and not the second level stuff (which, by the way, is not 100% foolproof anyway).
Look at the huge list of things asked of this form:
- State where your accounts were opened :
- Online ID :
- Bank of America ATM or Check Card PIN :
- Passcode :
- Social Security Number :
- Account Number :
- Routing Number :
- Last Eight Digits of ATM or Checkcard Number :
- E-mail Address :
- E-mail Password :
- Card holder name :
- Address1 :
- Address2 :
- City :
- State :
- Zip :
- Country : U S A
- Phone Number :
- Credit/ debit card number :
- Exp date : /
- Code verification number :
- Mother Maiden Name :
- Mother Middles Name :
- Father Maiden Name :
- Father Middles Name :
- Date of Birth :
- Driver License# :
"Middles Name" notwithstanding, anyone who hands over all of this information will find themselves cloned in the banking and credit worlds—with everything of value headed outward. If this crook wanted to be especially cruel, you would have given him all he needed to lock you out of your own email account permanently.
The only reason this guy doesn't ask for your shoe size is that the datum is not resalable. If it were, he'd ask!
Posted on December 31, 2008 at 10:21 AMDecember 23, 2008
Make a Christmas Phish
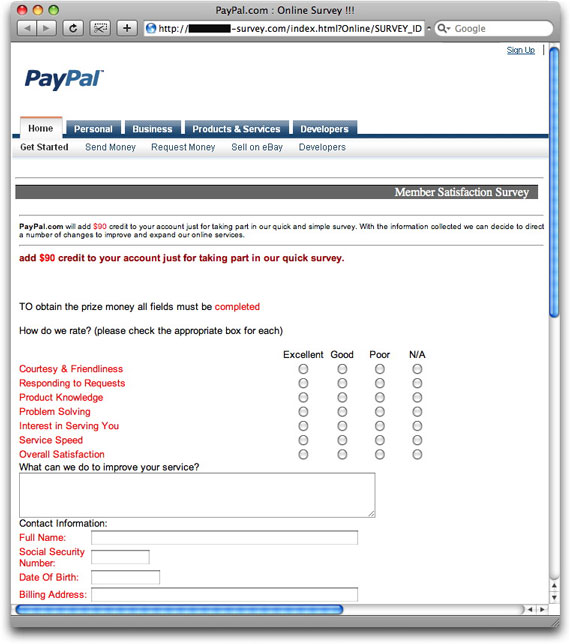
Pity the poor illiterate crooks who don't have anything else to do at Christmas except con unsuspecting souls out of their PayPal account credentials, credit card data, and bank account numbers. This guy tried to be creative, but lost his way at the very end:
Paid Paypal Survey: One Way To Earn Your MoneyDear Customer,
In an effort to continually measure the service quality given to our members we send out random surveys
asking for valuable feedback on how we are doing and how we can improve.
There are only a few questions to score and should only take a few moments of your time.
Your patience will be rewarded with $90 direct deposit to your account and your name will
automatically be entered into our quarterly drawing for a $2009 grand prize.
Sincerely, PayPal Team
PayPal Survey!
www.paypal.com/survey [hidden link to a different URL]
--------------------------------------
DO NOT REPLY TO THIS EMAIL. IF YOU HAVE QUESTIONS PLEASE CONTACT US.
Note: If you received this message in your SPAM/BULK folder, that is because of the restrictions implemented by your ISP *
For security reasons, we will record your ip address, the date and time. Deliberate wrong imputs are criminally pursued and indicted.
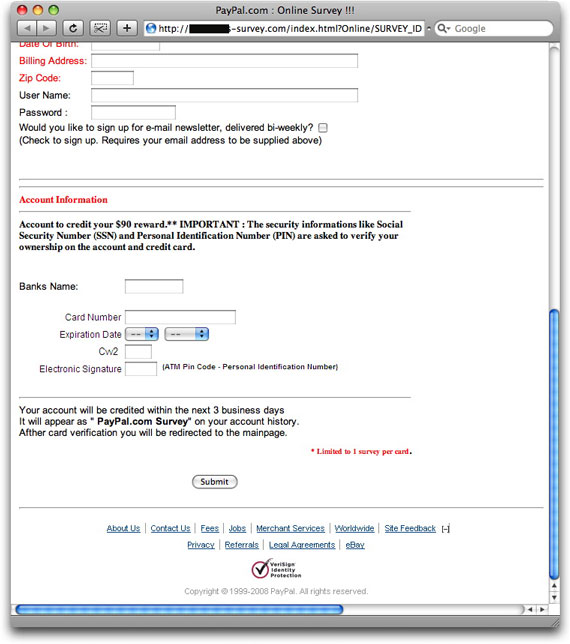
The destination web site offers plenty for the gullible recipient to do:
Just look at all that information being requested! Why on Earth would PayPal need all that stuff to shove ninety bucks into your PayPal account?
May Santa drop a truckload of coal on this heartless hole.
December 19, 2008
Amazon Prime Phish
Amazon Prime is a subscription service from amazon.com that lets you get "free" two-day shipping with every order. I say "free" in quotes because Amazon Prime does have an annual cost, but one that frequent Amazon customers certainly recoup fairly quickly.
And so, consider the Amazon Prime customer who receives the following message:
From: Amazon.com Customer Service
Subject: Your Amazon.com Prime Cancellation Confirmed
Hello from Amazon.com.
Your Amazon Prime membership has been cancelled, per your request.
Our records indicate that you haven't used your Amazon Prime membership benefits, so I've requested a full refund of $79 for the membership fee. The refund should be processed within the next 2-3 business days and will appear as a credit on your next credit card billing statement.
Please know that we value your business, and we hope to see you again soon at Amazon.com.
We always strive to provide a high level of service, and we would appreciate your feedback. Please let us know if we resolved your inquiry.
If yes, click here:
Please note: this e-mail was sent from an address that cannot accept incoming e-mail.
To contact us about an unrelated issue, please visit the Help section of our web site.
Best regards,
http://www.amazon.com
Of course, if the recipient was concerned and did the right thing—log onto amazon.com through normal means—there would be no change to Prime status. But clicking the link would lead to a lookalike login page, where one's username and password credentials would be lifted. Minutes later, their Amazon accounts (and associated credit cards) will have been hijacked.
Thankfully for the phishing message I saw, the phony site (hosted in Russia) was taken down. But the template is set. It will be used again with a different web site destination. Amazon Prime customers: Beware.
Posted on December 19, 2008 at 08:33 PMDecember 18, 2008
Beneath the Latest Blasts
I was wondering why, despite some very pointed filtering on my email server, a fair amount of sex chat lures have made it to my email client—where Entourage has successfully spotted every one as spam and diverted them accordingly. The rendered body of all of these messages claims to be from someone who "was just reading your profile online," and implores me to visit via MSN. Uh, no thanks. But a peek at the source code reveals why this recent flood may be making it into a lot of inboxes.
The message bodies are intentionally malformed HTML documents. They start like this:
<html> <body><br />
Hey there, i was just reading your profile online and i would love to chat<br>you should come on MSN i am waiting [removed]girl69@hotmail.com or on yahoo IM [removed]xoxo@yahoo.com
</body>
But before reaching the final <html> tag, the author has inserted a <style> tag whose content is a humongous semicolon- and return-delimited list of 1000 (exactly) words, names, and numbers. None of the text inside the tags is rendered, but does get studied by at least some content filters. Here's how the list starts out:
Mario;retour;apartar;painfully;Mon;Pronti;Charron;cancel;catastrophe; coppia;Busch;ministro;identified;Amerikaanse;answering;asap;Blues; recognized;oranges Schmitt;amp;establishes;Tom;Communist;arranges;Cairo;Mission;osteen; Eller;Scurry;Bezos;sawdust;wesentlichen;reformsgolpe;Antingen; confidence;Barnes;afternoon Nestor;Huang;center;adds;menschen;Rhythm;vorsichtig;gegaan;avail; Circumstances; ....
Oddly enough, this collection was not randomly assembled for each message. They were all identical. Perhaps it is a carefully researched collection of text that has proven to get past various Bayesian filters. Also identical were the forged Sent: dates and times (17 December 2008, at 14:50 PST). Subject: lines varied a bit from a presumably canned list (e.g., Hey Baby, i think i love you, Chat With Me, etc.).
I won't say how many made it to my email client, but suffice to say it was enough to get my attention. Just not enough to get me to dial up MSN and chat. Sorry, grrrls.
UPDATE (17:50PST): I guess it wasn't a carefully-crafted list of hashbusting words after all. Just saw another one with a smaller list of 156 different words hidden in a <style> tag, beginning with: ghoulish;automate;inc;acquire;chord;autopsy;lubricious;flintlock;dexterity;depressant;
Posted on December 18, 2008 at 04:46 PMDecember 09, 2008
Inappropriate Spamvertised Domain Names
I saw a spam message spewed by one of the (way too) many e-marketing scumbags that just seemed to be counterproductive. The spam was selling vehicle warranties, but the links were to a domain name that included the phrase
cancercare
This was in a plain text message, so the URL and domain name were very much in the open. Maybe I'm dense, but I don't see the connection between cancer and warranty coverage for my automobile transmission.
If there really is a company selling such warranties through this e-marketing outfit, I hope they both get what they deserve: ZERO RESPONSE.
Posted on December 09, 2008 at 10:32 AM