| Home | The Book | Training | Events | Tools | Stats |
January 30, 2005
A Spammer Revives a Lost Art (Poorly)
Long before computer screens could portray curvy lines and paint in color, many clever geeks created "art" by carefully laying out regular alphanumeric characters (printed line by line). When viewed from a few steps back, the display or printout represented peoples' faces, buildings, just about anything. It was like a mosaic effect, and was sometimes called ASCII Art, because the characters were from the standard character set of numbers, letters, and common punctuation in the ASCII character set. Even in the pre-personal computer days, teleprinter operators commonly exchanged this type of art to be printed on paper rolls.
An important aspect of this kind of art is that the output is expected to be displayed or printed in a monospaced font. Even spacing between characters is vital to conveying the image.
One spammer appears to have revived the art form for his medz spamming. He creates words using a variety of underscores, slashes, parentheses, and vertical bar (pipe) characters. If you have the right font installed (most Windows users would), one of the words looks like this:

My system didn't have the desired font installed, so all I could see is:

Near the bottom of the message were the ASCII art words "click here," which were surrounded in the message body by an HTML link tag, making the entire ASCII art version clickable.
Other than the fact that his message was sent from a zombie PC, I wonder how a variety of spam filters will treat this message. It is over-encumbered with codes for non-breaking spaces, which may be a telltale sign. He also includes some <font> tags specifying a size of one pixel—usually a dead giveaway to spamminess.
But before you quickly open unsolicited messages to see if they contain ASCII art, be sure you follow the instructions in Spam Wars to pre-inspect messages safely. You don't want to open a message that either has a Web bug in it or silently loads some nasty stuff into your PC.
Posted on January 30, 2005 at 12:32 PMJanuary 29, 2005
(Sigh) More PC Hijackings on the Way Today
Imagine you get an email message with the following From: and Subject: info:
From: "PayPal Support"
Subject: Sony DSC-F828 8.0MP Digital Camera
If you're a digital photography buff, you might be curious enough to check out the message (I hope in a safe manner described in Spam Wars). Here's the message body:
Sony DSC-F828 8.0MP Digital Camera
Your order # 12405 has been accepted for the amount 840.00$ Your card will be charged in that amount .Thank you for your purchase.
You can check the order in your profile.
http://not_the_real_domain.net
I would imagine that most everyday email folks seeing this message would be incensed at the notion of their credit card being charged $840 without their permission, and would follow the link.
That would be one of worst mistakes you'll make all week, especially if you don't have a well-patched Windows PC.
The actual link (not shown here) takes you to a page that innocently says there is nothing to see. But hidden within that Web page's HTML are two iframe elements, one of which loads a file from the Web called "installer.htm".
That can't be good.
And, indeed, it isn't. Through some more indirections invisible to you, the site uses a known Windows vulnerability to install external software into your PC without your knowledge or consent. By simply visiting that seemingly empty Web page, you have just allowed your PC to be hijacked by, well, I don't know who exactly, but someone who will likely hire out your PC's computing cycles to what are called "botnets." It could also be a "keylogger," which silently records your usernames and passwords to financial sites.
How many PCs will be infected today as a result of this email message? I shudder to think.
UPDATE: I should have mentioned that this tactic has been used in previous months, including the same "order number" and dollar amount in the messages. I also contacted the Canadian ISP hosting the damaging site (netfirms.com). They claim 24/7 support with a 4-hour turnaround. Nine hours after they confirmed receipt of my report, the site is still active. (Deeper sigh)
UPUPDATE: The evil Web page has been taken down, but it took the ISP 43 hours to do so. I guess they had to wait for the "A" support team to show up on Monday morning. Meanwhile, the damage has been done.
Posted on January 29, 2005 at 09:28 AMJanuary 27, 2005
A Real Puzzler
I just don't understand some spammers. Make that a lot of spammers. Case in point:
Subject: Sexually Explicite: Please enjoy my free pics
On the face of it, despite the misspelling of "explicit," this message appears as though it might attempt to conform to the CAN-SPAM rules. It seems to be properly labeled and is not deceptive (provided the message body is about the same subject). It makes one think for a moment that perhaps—just perhaps—this spammer has made adjustments in response to the recent bust of some Las Vegas spammers who, among other things, allegedly failed to label their sexually explicit spam properly.
But then I check the source code of this message's body. There isn't one CAN-SPAM compliant thing about it. No mailing address. No unsub option. Possibly a forged header field. Just a link, an image, and a text advisory that the site is "only for grownups." Then I also realize that the misspelling in the Subject: line might cause the message to slip through filters that block messages bearing the mandated "sexually explicit:" label.
It all makes me wonder why the sender bothered with the labeling if everything else about the message fails the test. The spamvertised Web site is hosted in the U.S., so unless that site redirects visitors offshore, it might be a relatively easy target for enforcement (well, one can dream). The domain registration address is in Belize (oh, and the Moon is made of green cheese).
Here's hoping that lots of recipients used the label as a guide to delete the message without previewing or opening it and thus prevent the hit counter on the image hosting site from incrementing.
Posted on January 27, 2005 at 09:16 AMJanuary 25, 2005
Destroy Your Reputation: Hire Affiliate Spammers
I don't know what some companies are thinking when they launch affiliate programs that enourage affiliates to advertise a major brand. Some affiliate mailers are uncontrolled spammers who mail to harvested addresses, blaring what might have once been a reputable brand name into the inboxes of recipients who smell spam from a mile away.
Over the years I've written off companies—I won't do business with them ever—because rogue affiliates spam me in an effort to direct my business to the brand names. Omaha Steaks, for example, is on that list.
I now add Blockbuster Video.
Digging a bit into Blockbuster's affiliate plan, I found that they use a third-party company to handle the program. If you want to become a Blockbuster affiliate, you register with this outside company. This company's Web site is a little confusing because they say it's "powered by" yet a different company name, a name whose domain appears in the browser's Address field. It's hard to know who's on first.
Checking the agreement to which potential affiliates are supposed to adhere, there are various requirements about being CAN-SPAM compliant and that the sender must have proof of (not necessarily confirmed) opt-in registration from a recipient. I have no idea where the affiliate for the Blockbuster offer I received got the address, but I can tell you that I did not opt into anything at the sender's home-bizness-sounding domain.
And there's the rub: If I wanted to report this suspected offense to the affiliate program company, I'd have to supply the email address that received the spam so that the affiliate could (theoretically) supply proof of opt-in-ness. My guess is that the registration info would be similar to the bogus IP address and time stamps I've received in other spam messages (where I'd have to have been in China when I registered). But if I supply the address, the spammer would simply remove me from his database (a process called listwashing). It's highly unlikely that the spammer would suffer any consequences from the company managing the affiliate program (perhaps a "naughty, naughty" finger wagging).
I understand why companies don't want to get into managing affiliate programs in-house, especially if they don't have the expertise. But the longer the chain from brand to emailer, the more chance rogue elements will slip up, and get your brand in hot water.
In the meantime, Blockbuster Video is forever blackballed at my domains. For this kind of malarky, I have a one-strike policy. My server, my rules. If I were a Blockbuster retail customer, I'd take my business elsewhere.
Posted on January 25, 2005 at 04:39 PMJanuary 24, 2005
Domain Name Pseudo-Branding
In Spam Wars I claim that most high-volume spammers don't attempt to flaunt a brand-name domain. Many legitimate companies spend fortunes on building domain name brands so that the next time you sit at your computer and think about buying a product or service in their category, you intuitively enter a name-brand URL. That's why domains such as amazon.com, expedia.com, monster.com, and lots more are indelibly fixed in our heads. They don't call it "branding" for nothing (cue the sizzle sound).
Spammers, on the other hand, have no qualms registering and using gibberish domain names, especially if they use them for short periods or in rotation with others, just to complete a particular spam campaign. Whatever branding they might wish to promote at the Web site doesn't show itself in the spam, which would be too easily blocked by spam filters.
But occasionally, I see a spammer who is enamored—at least for a little while—with a particular keyword that is buried within a series of registered domain names. I'm not talking about typical words that get repeated over and over in domain names (such as: herbal, great, free, email, offer, and meds). Rather the words are more identifiable. They also tend to gravitate toward offers for porn and online dating/chat sites (is there a distinction?).
Two partial brand names I've seen recently in my Suspects bin have the words "hotty" and "hookup" in them, in combination with one or more other words. The "hotty" spams are all the same format; all the "hookup" spams are the same. I don't visit the spamvertised Web sites, so I don't know if the brand names carry over to their product or service offering. I'm sure that all "hotty" domains redirect visitors to the same destination, and all "hookup" links lead to the same spot.
Spam fighters commonly exert extra energy to explain the motivation behind a particular spammer's modus operandi. If the tactic is harmless (as this one seems to be), it's a waste of time figuring out why the spammers do what they do. It could be convenience, laziness, or simply a spammer being in a "hookup" mood this week. The downside for spammers, however, is that the more they repeat a pattern, the easier it is for spam filtering to catch it next time. Hookup with that one, hotty.
Posted on January 24, 2005 at 12:12 PMJanuary 19, 2005
Attack of the Killer Dictionaries!
Holy Mama! When I checked the statistics for Tuesday, January 18, I was greeted by an incredibly high amount of dictionary attack activity at the domain I use to track this stuff. While dictionary attacks (attempts to send mail to as many user name combinations of a domain as possible in the hopes of finding a few good ones) ratcheted up to over 50,000 in a 24-hour period. Normal activity is in the 4000-7000 range.
Posted on January 19, 2005 at 06:39 AMJanuary 15, 2005
Phisher Can't Keep His Scams Straight
Many of the phishing messages that come my way are "from" institutions with which I don't do business. I don't get as many Citibank ones as I used to, but I do see a lot for Washington Mutual (wamu) and Suntrust. Therefore, it was no big deal to see one come in with a partially corrupted subject:
Subject: Error found, please submit , suntrus informatiql
Certainly not a professional job, as phishers go. Perhaps some Suntrust customers would be fooled into opening it. If they do, however, they're greeted with a Washington Mutual phish ("Dear wamu customer"). No reference to Suntrust whatsoever.
This message carries on a grammar error I've seen for months:
Note: If you choose to ignore our request, you leave us no choice but to temporary suspend your account.
It's another reason I feel the messages and software are being distributed in a kind of do-it-yourself or affiliate phishing "kit."
Anyway, this phisher must have found out the mistake. Less than three hours later came another phish with the same message and same disguised URL to a hijacked Brazilian Web server:
Subject: James from wamu.com - please submgz
He still has some corruption problems, but unsuspecting wamu customers will likely open this message. Some will be taken in by the warnings (while overlooking the bad grammar).
In one of my recent radio interviews (plugging Spam Wars), the host told me of a close call he experienced with a phishing message. He was on the phone with his father, when his dad received one of these messages. His dad was about to go to the phisher's Web site and enter his personal identity info, when the host luckily interceded. Had he not been on the phone at that instant, his dad's bank acount and/or credit rating would have been toast.
One of the verses of the song "Teach Your Children" (Crosby, Stills, Nash, and Young) begins: "Teach your parents well." That goes double if they're on the Internet.
Posted on January 15, 2005 at 08:04 AMJanuary 13, 2005
Same Tricks, Different Language
Every once in awhile a message written in Russian gets through my server filtering. My Mac OS X computer dutifully displays the Cyrillic characters, which, had I not studied ancient classical languages in college, would look Greek to me.
After checking the source code of today's arrival to make sure there were no images or other potentially nasty things inside, I opened the message to see the rendered characters. Then, with the help of Alta Vista's Babel Fish language translation site, I discovered that the spam was selling some kind of real estate processing scam. Probably similar to the English-language spams that promise tons of money for processing FedEx refunds (oh, please!).
My Russian friend learned some other tricks from English-language spammers. Following an assertion that this message is not spam comes this paragraph:

Loosely Babeled, it begins, "This distribution is produced in accordance with st.29 of ch.2 of constitution RF." I'm taking the last reference to be a citation to the Russian Federation constitution. I don't happen to have an English copy handy, but seeing this reminds me of the common disclaimers of being CAN-SPAM compliant, or the old chestnut that the message complies with a U.S. Senate bill that was never passed.
While selecting and copying the text from my email program, I uncovered text at the bottom in a white font:
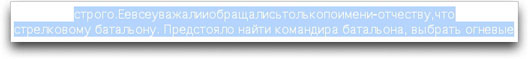
The translation of this hidden text starts with a bit of gibberish, but eventually comes in the "clear" as reading: "patronymic, that to rifle battalion. It was in prospect to find battalion commander, to select fire". To me this looks a lot like the spam filter hash busting text you frequently see above and/or below English-language spam—text grabbed from literature and such to fool the filters into thinking the message is legit.
If it's any consolation (I doubt it), your fellow Russian spammees are fighting the same battles you are; and the spammers are using the same tactics as those who spam in English.
Posted on January 13, 2005 at 11:44 AMJanuary 12, 2005
Knowing Your Business
Years ago I read what was then a classic article in the Harvard Business Review. I forget the title now, but its author helped readers examine their companies to uncover what their real businesses were. My description makes it sound simplistic, but the article had numerous examples of how major businesses failed to understand what their true missions were, and got swallowed by companies that had figured it out. Like the way railroads thought they were in the railroad business, rather than the transportation business—and let airlines own the skies.
What brought this up was a message in my "spam suspects" bin (surprise!). The Subject: line (for a change) accurately indicated the subject:
Online Dating Service
There's no need to bore you with the details. This spammer, though, didn't try to disguise the destination URL for all his hot online dating action. No, the link was plain as day...to a domain whose name contained the words "cheap" and "mortgage" (along with some other characters).
The domain is hosted in China, and the info in the registration (minted all of six days ago) looks bogus to me. From what I can tell, there is no city on Earth named Kraczevic, and it certainly isn't in Zambia.
So, is this a case of a mortgage lead spammer trying his hand at online dating spamming? Or is it simply a confused online dating spammer? I doubt this guy needs the Business Review article. He knows his business. It's spamming. Whatever makes a buck through high volume, zombie relayed, forged header spamming.
Someone might want to send this guy an article on brand awareness.
Posted on January 12, 2005 at 08:48 PM
Last night I saw a spam message come through that advertised some kind of identity theft protection service. I've read the message a few times, and I'm still not sure what they're offering, nor will I visit the Web site to find out more—but I digress.
The message starts out like a quasi-personal message ("My name is so-and-so"). After a paragraph of blah blah blah comes this admission (identifying data changed):
This is an unsolicited e-mail.You can also contact me at (P.O.Box xxx,City, State ZIP) This is the only e-mail that you will receive from me,unless you reply back for more information,or if you would like to speak to me reply back.
Here's a guy who, aside from failing to format his HTML message in a readable form, seems to know his stuff with respect to the CAN-SPAM law. The law, as we all know, sanctions his unsolicited email if he doesn't use deception and offers a way to opt-out of future mailings. Perhaps he feels that his one-time-only strategy substitutes for the law's requirement to offer an opt-out link.
In any case, on the face of it, in his message—while still spam by anyone's consent-based definition—the guy seems straight-up in declaring his methods.
Long-time spam fighters (and Spam Wars readers) know that the first two rules about spammers are:
- Spammers lie.
- If you think a spammer is telling the truth, see Rule #1.
Therefore, it should be no surprise that six hours later, the same spam message arrived. Everything was identical except that the sender used a different IP address within the same block of Texas DSL accounts. Perhaps he disconnected his modem between floods, and the service issued him a new IP address.
So now he's told me twice that I won't be hearing from him again. Maybe he really means it now. Oh, see Rule #2.
Posted on January 12, 2005 at 08:10 AMJanuary 11, 2005
You've Got Mortgage!
For all its myriad flaws, the U.S. CAN-SPAM law attempts to address the lying and deception (to both computer systems and humans) that spammers seem to take great pride in practicing. With a year of the law under our belts, we see clearly that it has not had any effect on huge classes of spammers. They'll deceive their way into your inboxes and lie within the limited From: and Subject: lines to get you to read their garbage.
Medz spammers tend to practice most of their deception on the computer level, spending most of their time, it seems, on getting past content-based spam filters. Hence the ads for \/a1iuum and V1@gr@.
The mortgage spammers, however, have absolutely no conscience when it comes to tricking you into opening their messages and visiting a Web site. I see a ton of messages like the following one, whose Subject: line reads, "amazed editor's hand, accompanying":
Sir:
We have had trouble getting a hold of you by phone. As we promised, your morttgage app was apprroved with 3.9 %
Please correct your info here, so we can start
http://www.gibberish_domain.com/
Thank you
Amber Saldana
Let's count up the lies:
- I can assure you they haven't been trying to reach me by phone.
- I haven't filled out a mortgage application in nearly four years, the last time I refinanced my home.
- No mortgage broker would approve a non-existent application submitted by someone named "Sir."
- Since I submitted no info, there is no info to correct.
Those are the lies right in the message. The other lies are between the lines.
When you read this message, doesn't sound as though it is coming from a lender or broker? Who else could "approve" a mortgage application? What you can't tell, however, is that this spammer and the site it would take you to, have nothing to do with granting mortgages. Their business is capturing mortgage leads, that is, names and contact info that mortgage brokers use to initiate the mortgage application process.
Lead generation in many industries is an old business, and there are numerous un-sleazy ways to generate leads. For example, capturing inquiries to advertising and even those magazine "bingo" cards you see to request more information are forms of lead generation.
There seem to be enough mortgage brokers out there who turn a blind eye to the source of the leads (for which they pay handsomely, I might add) that the lead liars continue to spam. It also means that enough recipients are responding to make it economically inviting for the spammers to continue. Unfortunately, it doesn't take too many respondents to make the spamming pay.
The brokers see the list of leads and not (so they'll tell you) the deceptive messages (commonly sent through zombie PCs) used to get those leads. It's what I call the Sargeant Schultz defense.
I recall reading awhile back about some legal prosecutions against this practice, but even if they were successful, they haven't come anywhere close to inhibiting the practice.
By the way, I'm not suggesting that you shouldn't use the Web to obtain a mortgage. I used such a service for my last refinancing and had a favorable experience. But I sought out the service. It didn't barge its way into my inbox with a pack of lies.
Posted on January 11, 2005 at 10:12 AMJanuary 10, 2005
Blog Archive Fix
A visitor alerted me that McAfee antivirus software got all excited when he or she attempted to visit the November 2004 archive of this web log. The problem was that I was showing in plain text (not an active link) two examples of how phishers trick unpatched IE/Windows browsers into displaying the wrong URL in the Address field. I have replaced the two text examples with images (again, no active links) so you can still see what to be on the lookout for—done so in a way that antivirus software should be cool with.
Thank you to the anonymous reporter.
I'm actually quite glad that there is antivirus software looking out for users while they're on the Web. Norton for Mac OS X doesn't seem to care. Hmmm.
Posted on January 10, 2005 at 10:20 PMJanuary 09, 2005
Pathetic PayPal Predators
I was looking around more of the source code served up by the bogus PayPal settlement phisher message (doing so in a safe environment that can't corrupt my computer). I earlier explained that the page was abusing some IE vulnerabilities. Lo and behold, I found the following <meta> tag in the page:
<meta name="Description" CONTENT="Secunia - Internet Explorer Cross-Site Scripting Vulnerability Test">
Those who monitor broadcasts from the IE and Windows security patch planet will immediately recognize that tag description from a proof-of-concept page posted to the Web by security software firm, Secunia. In fact, this pathetic phisher took the script source code straight from the Secunia page, replacing Secunia's example HTML code with his own.
Tsk, tsk, tsk. I'd expect a phisher who hijacks servers and sets up snarky redirects to be creative enough to write his own version of the trick. At least devise your own script variable names and remove the meta tag identifying the source of your trickery!
This guy is a complete thief, from beginning to end, with all the creativity of a gnat.
Posted on January 09, 2005 at 05:31 PM
A new round of PayPal phishing messages seems to be on the prowl. Picking up on the real class action lawsuit against PayPal, the current predators want to make you believe that you are entitled to a payout. To receive the payout, they tell you, you must visit a link in the message and fill out your debit/credit card information so that funds will be credited to you.
The link, by the way, is to a numeric IP address hosted in Mexico. The page at that destination relies on visitors using Internet Explorer for Windows, because it abuses ActiveX and various vulnerabilities to trick visitors into believing they're really at PayPal, when, in fact, they're filling out a form hosted in Mexico. Submitting the form (which has blanks for PayPal login info, credit card number, security code, and PIN number) sends that information off to a server hosted in South Korea.
See, spam-watching can give you a geography lesson at the same time. Moreover, I'm pretty sure the data will cross international borders at least once more before being bundled for sale on the black market.
Each successful ripoff of a PayPal customer from this phish message is extra sad for a number of reasons. First, the amount in question (not that you'd ever see it from this scam) is all of $43.99. Imagine giving up your identity for the promise of 44 bucks!
Second, the message includes a real link to PayPal's real settlement site, which takes you to a page explaining this very scam, with a sample of an earlier attempt to do the same thing.
Third, if you bother to read anything about the real settlement, you learn that you would have had to apply for your claim by last October. If you didn't apply, you get bupkis.
Fourth, the settlement documents clearly state that payments to class members will be either by way of their PayPal accounts (the scam message says this would be illegal—feh!) or, if you asked for it in your claim form, a check by postal mail. There is no reason on Earth why you'd have to give anybody further personal information to collect your settlement, even if you filled out the claim form.
Finally, from what I can tell, the final settlement has not yet been ordered by the court. Nothing happens until that happens.
When PayPal sent a legitimate message about the proposed settlement in July of 2004, the phisher-sniffers among recipients thought it was a fake. But it was real. Just goes to show you how scammers are eating away at the Internet, byte by byte.
Posted on January 09, 2005 at 05:09 PMJanuary 06, 2005
A Nimble 419er: Abu Oma (& Mother)
I don't normally bother reading every 419 (advance-fee) scam letter that arrives. I mean, there are only so many hours in a day, and untangling near-English (intentional or otherwise) has grown rather old. Plenty of other people on the Web perform a variety of forensic analyses on these missives that nonetheless hornswaggle too many greedy victims out of hundreds of thousands of dollars each.
Every once in awhile, though, my curiosity gets the better of me. Just to keep up on the latest 419 schemes and see if a chuckle lies within. Last month's plea from a woman claiming she was near death due to (I kid you not) prostate cancer shows you that there is occasional entertainment value to this tripe.
Thus, today, I found one in my Suspects pile claiming to be from "Abu Oma & Mother." Their sad story had them being refugees from Sudan, now seeking asylum in Senegal. Unlike hundreds of other stories I've read, theirs lacked a certain logic, but the story goes that Abu's father had been assassinated in the Sudan. Not particularly up on his geography, Abu tells me:
My late father HON DR. FELIX OMA who was the former ministre of finance and economy in Sudan before he was assinated by the rebbles in the captal city of Khartoon 2003.
Sorry, Abu. My mind drifted to picturing the Flintstones' kid, Pebbles, in a cartoon.
Abu and Mom not only managed to get out of the country, but they also got $10.5 million out, too. They now want to come to some other country (I guess it doesn't matter which one) as soon as they find a "trust worthy foriegn personality to help us transfer the money and invest it in his country." The rest is classic 419 stuff.
Out of additional curiosity, I did a little due diligence. Actually appallingly little due diligence. Searching for "Abu Oma" in Google, I found that he (and Mom) have been at this under the same name for about a month. Using the precise same Senegalese telephone number (probably a cell phone) for a contact number, he made similar pleas earlier for the same amount of money. Last month, he was the son of a murdered Sierra Leone general, named Almammy ("How I luv ya") Abu.
Okay, the picture is finally coming clear. Mother Oma is a transnational bigamist, whose husbands unfortunately get killed after amassing exactly 10.5 mill. Sort of the inverse of the movie "Speed." Keep your secret bank stash under $10.5M, and you live; reach that magic number, and you'll be Bam-Bammed, while your widow and son Abu head for the computer to give away a chunk of your hardly-earned money to a complete stranger.
What if I helped them come here? Might I fall under the spell of the apparently desirable Mrs. Oma? Would my stepson, Abu, take on my family name as he did with his other "dads?" They'd help me amass a fortune that could reach $10.5M. Uh oh.
If you should get an URGENT BUSINESS OPPORTUNITY message from Abu Oma Goodman (& Mother), do some due diligence first.
Posted on January 06, 2005 at 05:50 PM
An exact copy/paste from my email log:
Subject: Save hundreds -- pucrhase unexpenisive OEM software
Would the software arrive on floppy disk? Dunno.
Posted on January 06, 2005 at 09:31 AMJanuary 05, 2005
Somniregistrationism
According to a message in my Spam Suspects folder, I must be registering at Web sites in my sleep.
In this case, I received notification congratulating me on registering at a site for freelance professionals. The message showed my login ID and gobbledygook password (nothing at all like the ones I use for registrations). At least this subject matter is, unlike the real estate broker lists I somehow got on, closer to home. When it comes to being a freelancer, "I are one."
The message provided an unsubscribe link (no postal address), but I never, never, never unsubscribe from things to which I had not subscribed (awake or asleep).
Checking the sending IP address, it is currently not showing up as a spam source, but the domain registration for the spamvertised site is full of obvious errors, such as using a 5-digit postal code for a Canadian address and a non-existent (in North America) telephone Area Code—all of which I reported to Internic.
I can't say for sure that this was intentional spam on a massive scale or if "someone" submitted my email address in a registration form at this site. If the latter, it still doesn't matter. The site is definitely at fault for not using a confirmed opt-in system that would not automatically subscribe me without first asking me to confirm the registration. Unconfirmed registrations are too easily abused.
This one got me angry enough to file a complaint that could eventually lead to the spamvertised domain being yanked (if the contact info is as bogus as I think it is, the owner won't be notified to fix the problem—boo-hoo). I'll sleep even better tonight, and won't be tempted to register to sloppy sites in my sleep.
Posted on January 05, 2005 at 09:28 AMJanuary 04, 2005
The Folly of Challenge-Response
I've been getting more challenge-response challenge messages recently advising that an email message I "sent" was being quarantined until I click on a link in the message. The latest one included this advisory:
If you do not visit the above URL within 7 days, your message will be DELETED and I will not be able to receive messages from you in the future.
The subject of the original message was included, and I recognized it as a common virus subject line ("You cannot do that!"). The original message that triggered this challenge message was a virus that had forged my email address in the From: field. Another exceedingly common virus trick.
I detest getting these challenge messages to stuff that didn't come from me. They load up my inbox with automated garbage. I'm often tempted to click the URL (after doing research to see that the link isn't doing anything sneaky) to force the original virus message to wing its way to its intended recipient.
The email address of the recipient isn't revealed in the challenge message, so I cannot write to her to explain why Challenge-Response shifts her spam/virus burden onto others. After 7 days, my address will be blacklisted at her end. I hope she never writes to me for scripting advice because my response will never get to her. To head off that problem, I'm blacklisting her entire domain (see how this escalates?) because I don't want to get any more C-R spam from this outfit. Adios.
Please, folks. Don't let the instant gratification of Challenge-Response blind you to the harm it inflicts on others. In my eyes it turns you into a spammer.
Posted on January 04, 2005 at 07:22 AMJanuary 03, 2005
More Spammers' Pants Ablaze
If you're an amazon.com customer, as I am, you probably enjoy getting those little notices that your recent order has shipped. "O frabjous day!" I thought to myself recently upon learning that the next DVD series of 'Rumpole of the Bailey' was in on its way.
The next day, however, wasn't so frabjous. Sitting in my "spam suspects" folder at my server was a message with this ominous subject:
Subject: Your order has been shipped
The From: line listed a human name, with a mismatching, non-corporate aol.com email address. The body of the message started as follows (identifiable bits disguised):
Thank you for shoppingl. This e-mail is to confirm that your order shipped on 13-12-2004. Based on the shipping method chosen at the time of purchase, your order is expected to arrive within 1-5 business days. If you have questions about the products you have ordered, order status or other customer service matters, please call 888-555-5555 or visit website http://www.foo_bar.com/order.html
Don't laugh at the date. Europe and many other places in the world put the month and date in the opposite order than the way we do in North America, so there's nothing wrong with December 13, 2004.
The URL of the Web site of my supposed purchase makes the place sound like an informational site for people interested in poker. Other than that, the message contained no corporate identity or details about what I had supposedly ordered. The message did contain a customer number and order number.
Even if you aren't an active online shopper, you might likely get incensed by a notice suggesting that you have ordered something you don't remember. You wonder if something has been charged to your credit card, and if so, how much?
This ploy—certainly not new—is intended to get you to visit the linked Web site to clear up some mistake or misunderstanding. There is no order. There is no credit card charge. And there are no customer and order numbers, except perhaps as a way for you to enter an identification number that validates your email address as being "live," and you being a click-through victim.
And that the Web site in question is associated with online gaming gives me an even greater reason to warn you off. These outfits tend to have good programmers working for them. It wouldn't surprise me to find the home page of this site including some source code subterfuge that redirects your browser to Popup Hell or surreptitiously installs Bad Stuff on un-updated Windows machines.
This deceit deserves the complete ZERO RESPONSE treatment, not only to keep the spam economy out of the trickster's pockets, but to protect yourself, as well.
I know it's hard to resist when the message sounds so real. Catch the rest of the message body:
To check your delivery status, and see carrier and tracking information, click here [no link in message, oops --DG]. Please note that tracking information may not be available immediately.
Note that your order may be shipped in separate boxes and may be delivered at different times. Systems and accessories may ship separately and have different estimated ship dates. Please use the Order Status tool to get more information regarding expected delivery date(s) for your order(s).
If your delivery requires a signature and you are unavailable to sign for the shipment, you may contact your designated carrier after their first delivery attempt to arrange for pick-up to prevent your package(s) from being returned to sender. Carriers typically attempt to deliver three times before returning to sender. Want to check details of your order, print an invoice, or review order history? Log into My Account. Note that your invoice may not be available online until 24 to 48 hours after shipment.
Should you have any additional questions, please visit us at http://foo_bar.com
ALL SALES ARE SUBJECT TO TERMS AND CONDITIONS OF SALE. YOU CAN FIND THEM BY VISITING OUR WEBSITE. Thanks again for your order. We appreciate your business.
A lot of this sounds as though it was lifted from a shipping confirmation of a legitimate online retailer. But the ALL CAPS line is the one that will get even slightly suspicious recipients to visit the site, and possibly put themselves in peril.
I know that barrister Horace Rumpole is oft quoted as saying "Rumpole does not prosecute!" But I wonder—if the jurisdiction were right—whether he'd like a shot at these sleazeballs.
Posted on January 03, 2005 at 04:52 PMJanuary 01, 2005
Spammer's Pants on Fire
You have certainly seen spam disclaimers that say you received the message because you had signed up somewhere before.
The ones that really get me are like one I received today (specific identities disguised):
You have received this advertisement because you signed up to receive offers from foo_bar.com and/or through one of our affiliate partners. You signed up at www.another_foo_bar.com on 12/4/2003 20:16:00 with the following IP address 142.179.53.xxx.
Spam Wars readers know full well my feelings about "partners." According to this message, I supplied my email address while connected to the Internet at the IP address shown. I believe this disclaimer is intended to impress and/or intimidate me into believing that it must be true because it has all kinds of technical stuff associated with it. But a quick check of the address shows it to be in Calgary, Alberta. The last time I was in Canada (Montreal) was 1988. And I don't dial into the Internet from California by way of Calgary.
This kind of deception should be outlawed. It's more evidence supporting Spam Rule #1: Spammers Lie.
Posted on January 01, 2005 at 09:13 AM