| Home | The Book | Training | Events | Tools | Stats |
March 31, 2008
April Fools!...You're Hosed!
Following the same pattern as numerous holiday-related spam messages luring recipients to malware-loading sites, I just saw one for April Fool's Day. It's a simple, all-text message, which might slip through spam filters when sent from a newly-added botnet computer (whose IP address isn't on a blocklist yet):
Subject: Happy April Fools!Happy April Fool's Day. http://83.85.[removed].[removed]
Fortunately, the destination of the one I received has already been cut off at the knees, so I haven't yet seen what this campaign serves up, whether it's an elaborate graphic (as in Halloween 2007) or just a simple text page disguising the background malware loading to unpatched PCs.
Naked IP address links in spam are the most dangerous ones to click. Don't do it!
Posted on March 31, 2008 at 02:07 PMMarch 26, 2008
Yay! SophosLabs Asking the Right Questions
A SophosLabs blog entry reveals startling statistics about the quantity of potentially deadly web pages that host malware installers of one type or another. They claim that their scans unearth a newly infected page every 14 seconds.
Quick, tell me how many different web pages you visit in a typical 24-hour period. I don't think I could give you an accurate count of my activity, but I'd wager that a web-enabled individual visits a couple hundred pages a day. Given that the web encourages you to have the attention span of a gnat on crack, the average number is certainly much higher for younger folk who believe they have the mental agility to hypertask.
According to SophosLabs, if you visit a couple hundred pages a day, it is likely that at least one of those pages will host malware that is dangerous enough for Sophos security software to block. Since Justin or Tiffany in their family home bedrooms don't access the Internet through Sophos security software, their unpatched PCs are just begging to be taken over—even if they are visiting normally trusted sites for homework.
The big, as-yet unanswered question, however, is through what means the Bad Guys are luring potential victims to compromised web pages, especially those set up intentionally to screw visiting PCs. From the blog:
How are users getting to these sites? Via search engine results or directed to them by spam? Where are the sites? Are they newly infected sites or sites that have been around for a long time?
SophosLabs promises to use its research resources to investigate those questions. I hope they go even further if one of the answers is that spam contributes to visits. I'd like to know what it is about the spam that lures victims. Sophos captures a lot of spam, so perhaps they can correlate spamvertised links against infected page URLs. Get those wise computers a-crunchin'.
Posted on March 26, 2008 at 11:33 AM
We all know the shame associated with being caught Googling yourself in the privacy of your own home, so it is with trepidation that I admit to searching the videos available on the iPhone's YouTube selections for my Mister Spam Man music video. If you search for spam man, it's right up there at the top.
Kewl.
Posted on March 26, 2008 at 10:43 AMMarch 21, 2008
Watching a Phishing Attack in Progress Breaks My Heart
It's one thing to see a phishing attack underway and reporting the hacked server to the site owner in the hopes of getting the fake lookalike site shut down in a hurry. It's quite another to see that a phisher has been successful in tricking everyday folks into giving up their passwords and credit card data.
Such, sadly, is the case of an amazon.com phisher who must have bought a very cheap phishing kit that stores the captured data in a plain text file on the hacked server. Worse still—for victims, that is—the text file is easily accessible to anyone who bothers to check out the root address of the URL. In this case, the root was just an IP address that is owned by a Polish internet provider and web hosting service. The destination is an unused web server, complete with PHP installation that allows phishing kits to install a little bit of software to simulate the appearance of any financial or retail institution.
Based on the timestamps of subdirectory creation on the server, the phishing email message I received came through within a couple hours of the phisher setting up the site. As I write this, it has been less than four hours since the email batch containing my address was sent (it's anybody's guess how many batches were sent or when). In that time, the phony form has been filled out and submitted 11 times. Of those 11, eight were submitted by those who knew phishing when they saw it.
It's the other three, however, that really make my heart sink. These three were taken in by the well-crafted email message and bogus web site. I say "well-crafted" only in the sense that it had the right professional graphics look, and the content or formatting errors could easily escape the eye of a harried user fearful of losing access to Amazon. But the come-on has been the same since the earliest phishes: the request to "confirm your identity." It's the oldest trick in the book, provided they've ever read the book (which, of course, they can buy at amazon.com...nnww [nudge-nudge, wink-wink]).
Data from three victims certainly isn't any kind of statistical sample, so I'm not about to draw any overreaching conclusions from what I see. Thanks to date-of-birth info, I see that this current group ranges in age from their 80s to their 20s; they are of both genders; and they are geographically diverse in the U.S.
By now, the phisher has probably hijacked the Amazon accounts and changed the passwords to prevent the real owners from regaining control. Amazon is a nifty account to hijack—just click on the Electronics department, and imagine how much damage a crook could do, putting a giant flat-panel TV and a digital SLR camera or two on the account's credit card, shipping as gifts to an accomplice's home.
The credit card data is a separate asset, which the crook will sell through numerous brokers in the electronic equivalent of back rooms. The phisher who bought the kit may actually be aced out of his score because the kit's author or any of the crooks who find the open text file might beat him to the back room.
I feel like I'm in one of those science fiction stories about someone who knows the future and sees across the street someone for whom disaster lies around the corner. This is going to end badly, and there isn't much I can do beyond trying to get the site shut down.
In the time I've spent editing and completing this article, two more victims have given up their Amazon account and credit card data. I don't think I'll sleep very well tonight.
Posted on March 21, 2008 at 02:51 PMMarch 18, 2008
High-Tech Consultant, a.k.a. Idiot
A spam message made the rounds yesterday from a Frenchman promoting some sort of online multi-language dictionary. To prevent his hit counter from incrementing by one, I haven't visited the site to see what it's about; nor did I follow the link to a Google video (about an online dictionary?). In any case, I guess his dictionary couldn't handle the words in my earlier articles, Issuing a License to Email or More To: Field Inanity, because he sent his spam with hundreds of email addresses exposed in the To: field. His address collection is in alphabetical order of account name. The bunch in the message I received contained 443 addresses from cv-idione to dossiers.
The message body (in French) was brief and included an apology if the recipient did not like receiving the message. But no opt-out link or provision.
Yes, that was bad enough, but then one of the recipients had to reply with the French equivalent of "buzz off." He did so, however, by hitting Reply All in his email program. Thus, all 443 original recipients received yet another copy of the original email (of course, he quoted the entire thing). The jaw-dropping part of the matter is that the Reply All guy signed his message with the attribution:
High-Tech Consultant, Founder
The rest of his signature included his phone numbers (landline, cell, Skype, fax), URLs, and physical address. I can't tell if he is trying to piggyback on his countryman's stupidity to promote his service or if he is just an idiot. Either way, I wouldn't hire this guy to change a light bulb.
Posted on March 18, 2008 at 09:30 AMMarch 16, 2008
Are ISPs Accountable for Bots on Their Systems?
The European Network and Information Security Agency (ENISA) commissioned a study on the economic impact of network and information security. ENISA is an agency of the European Union, and its focus is clearly on what's happening in the EU. But, as we all know, security is a worldwide issue, so their findings aren't necessarily applicable only to the EU.
One of the recommendations was most striking:
Recommendation 4: We recommend that the European Union introduce a statutory scale of damages against ISPs that do not respond promptly to requests for the removal of compromised machines, coupled with a right for users to have disconnected machines reconnected by assuming full liability.
The authors of this report readily admit that this "is the most controversial of our recommendations." They provide an apt analogy wherein the highway system requires police to get drunk drivers off the road before the miscreants harm others and themselves. All licensed drivers know they're not supposed to drink and drive, but some do so anyway; likewise, your aunt may have heard your warnings about opening unsolicited email attachments, but couldn't resist unzipping the "shocking Britney photos," turning her PC into a zombie that sends spam and launches DoS attacks under the command of a botnet herder. Should her ISP act as cops to prevent her PC from inflicting more harm around the Internet?
I long believed that the ISP stands in the ideal spot between the user and the cloud to perform this type of service; and yet I've treated this dream as being merely fanciful. Some ISPs have taken small steps to limit potential damage by blocking PCs from sending spam directly to outside mail servers ("blocking outbound Port 25"). But a bot can still do harm in other ways that such blocking won't affect.
Some ISPs got suspicious if one of its subscribers sent huge blasts of email frequently. The botnet herders figured this out and now commonly instruct their bots to send out smaller chunks less frequently—but with more bots to keep the overall volume up.
Short of invasively scanning their customers' PCs for malware, could ISPs know which customers were infected? Mechanisms are already in place to capture the IP addresses of spam sent to spamtrap addresses and other types of attacks aimed at honeypots. Heck, after a 10- to 25-thousand dictionary attack day at my own email server, I could supply hundreds, if not thousands, of IP addresses of botnet machines.
Currently I don't bother reporting these infections to ISPs owning the IP address blocks because I have little faith in the report leading to a blocked account or, better still, cleaned-up PC.[1] I simply can't imagine a big broadband ISP setting itself up for a customer service nightmare of turning off hundreds of customers per day. The telephone support lines would get hot enough to set most of southern Asia ablaze. Nor are big ISPs going to send technicians to every infected customer's home to rid the household's PCs of infestation (especially since most customers would balk at paying for such a service, despite their complicity in causing the problem in the first place).
Meanwhile, I sense that ISPs would rather sit back and let security researchers find and destroy the command-and-control mechanisms behind the botnets. Botnet herders prove themselves to be nimble and smart, finding new ways to make themselves hard to find.
Botnets represent the most serious potential threat to the Internet. They're like thousands of sleeper cells who know no national boundaries and who slavishly respond to their commander around the clock. If we don't start neutralizing the botnet cells voluntarily (whether it be ISP, massive public user education, or both), I worry that legislators will bull their way through our china shop and make things worse.
ISPs could do everyone a favor and step up sooner rather than later.
[1] I have had success when the IP block is owned by, say, a government agency. A couple of years ago, I was getting some nasty spam that I was able to determine originated from a Southern California agency. A day or so after my report, I received word back that the IT folks there had located the rogue computer—a laptop that an employee had occasionally used at home. The infection took place at home, but the zombie also did its spamming while the computer was at work, plugged into the agency local area network.
Posted on March 16, 2008 at 01:37 PMMarch 14, 2008
How to Know Your Web Site Has Been Cracked
[Updated: 15March2008 0932PDT]
Over the last couple of days, the malware industry (and thus its blogs, news releases, and such) have been waving their collective arms in the air about a significant number of web site infections—infections that cause unprotected and unpatched PCs stopping by to be loaded with all kinds of nasty crap. According to multiple sources, the infections count more than 10,000, spread primarily among otherwise trusted web sites.
Although this revelation is pretty shocking—because a visit to a regular, trusted site could lead to a bad moon rising—there was scant advice to the typical, non-technical web site manager to find out if the crackers have infected his or her site. Most of what advice I did see appeared to be aimed at IT guys who closely monitor their web server activities as full-time jobs. Some of the affected sites, however, are mom-and-pop type web sites. And Mom doesn't know how to "run security scans to detect deficiencies in code" (advice from McAfee Avert Labs).
So, if you run a mom-and-pop web site, here is one way to begin your investigation, using (almost) everyone's old friend, Google.
Use the Google search facility to target your web site by name and for a string of characters that signal this particular infection. For example, to check this site (spamwars.com), enter the following search into the Google text box:
"2117966.net" site:spamwars.com
Observe the quotes around the evil dot-net domain name. Substitute your own domain name after site:. If you get the message that your search did not match any documents, you're probably in good shape (against this particular attack, that is). If, on the other hand, links to your site's pages come up, you've got some cleanup to do. Be sure to advise your web hosting service immediately. Even after you clean up, the Google cache will still probably contain pointers to your old, infected pages. You want to make sure that the active links to the current pages lead to cleanly-served pages. Additionally, if your server caches search results (only your web service administrator) knows for sure), you need to get those caches cleared.
The experts are still trying to uncover exactly how these corruptions are being accomplished (a PHP forum program is a current suspect, but ASP servers are also being affected by a different attack). How ever it's being done, don't feel like your site was specifically targeted. An infection of this magnitude was certainly an automated affair. Your site's underlying server software just happened to offer the open hole through which the crackers entered. Until that hole gets identified and plugged, your site will probably continually be vulnerable (sigh).
It's bad enough that the crooks have destroyed email as a communications medium. Now they're going to impose fear in the everyday activity of surfing our favorite web sites. This could get very ugly.
Posted on March 14, 2008 at 04:44 PMMarch 11, 2008
Note to Friends: MS Office Attachments Can Be Deadly
I have a friend here and there who insists on forwarding the cute singing dogs PowerPoint presentation that had been forwarded to them by their nieces, who got it from...who knows where? I call these types serial forwarders, potentially almost as dangerous as serial murderers. Whenever they receive a funny/poignant/thoughtful/quasi-spiritual email attachment from someone they know, they immediately open it and then forward it to their "closest friends" distribution list.
Of all the types of email attachment possibilities, Microsoft Office document files frighten me the most. Word, Excel, and PowerPoint document files are routinely sent around the Internet as a way to share data. When I'm working on a book, I submit chapters to my editor as MS-Word .doc files; those files are marked up with comments and come back to me via email attachments, still as MS-Word files. Back and forth the files go, and I have no idea how well-protected my publisher's employee computers (or the ones they use at home) are. Familiarity with Office files breeds complacency and a misplaced trust in a file type that can be abused by the knowledgeable crook.
Today Microsoft released a batch of security updates that addressed vulnerabilities in Microsoft Office applications, including those that run on the Macintosh. One vulnerability affecting Excel has been exploited in the wild since November 2007, leaving tons of folks exposed to the potential of having a remote attacker execute other code on victims' computers.
Microsoft Office documents aren't the only ones to have such vulnerabilities. We receive a steady stream of patches for Apple's QuickTime, Adobe Acrobat and Flash, RealPlayer, Windows Media Player...the list goes on. Unfortunately for users, the list includes popular programs whose documents are frequently attached to email blasted to personal distribution lists.
As primarily a Mac user, I can be smug when someone tries to send me a .exe or .pif file because such files won't run on Mac OS X to do any damage to my machine or data. But send me an unexpected .doc, .xls, .ppt, .pdf, .swf, or .mov file, and you're getting too close for comfort.
So, keep your dancing kitty animations and flubbing public speaker video clips to yourself. Send me the YouTube URL instead.
Posted on March 11, 2008 at 03:37 PMMarch 10, 2008
More Worthless Stats
I have a gmail address whose account name I have never published or revealed to another soul outside of Google. In fact, the only times I use the address are for access to other Google services. Unfortunately, the account attracts its share of spam, presumably via dictionary attacks.
Out of curiosity, I checked the account today to see what has been happening in the last 30 days. The Spam folder contained 75 messages. Here is how the message content measured up:
| Category | Count |
|---|---|
| Penis-related | 69 |
| Replica goods | 4 |
| Pr0n | 1 |
| Unknown | 1 |
On the face of it, Google does a decent job of diverting spam addressed to my account. And yet I'd expect Google to do a better job of completely blocking such email. Perhaps they are blocking medz spam that advertises brand-name pharmaceuticals—spam that floods my regular email server. The penile spam that made it into my gmail Spam folder isn't at all subtle, frequently using leet-speak spelling for male body part lingo (rhymes with d0ck). It would seem easy enough to identify that kind of junk for what it is.
I do wonder if my gmail address is actually on the address lists of spammers, or whether 75 dictionary attacks within the last 30 days got lucky. Dictionary attacks can be massive, such as the 25,000+ attack that came my server's way on March 9, 2008 (shown in the Spam Statistics page for that week). In truth, I hope my address is on the lists sold and traded among spammers because it helps dilute the quality of the lists (albeit microscopically).
Anything that helps reduce the potential return on investment for spamming activity is A Good Thing.
Posted on March 10, 2008 at 03:18 PMMarch 09, 2008
So Many Dumb Articles and Papers
Maybe I'm just cranky this week, but a lot of journalistic bytes were occupied by reports of studies regarding malware infections in business computers and consumer identity theft. The data points provided in the results were, to my mind, essentially worthless because they revealed only the most easily tabulated information while offering no answers to the real questions that should be asked.
Allow me to look at two in particular.
Exhibit A came from eWeek Mid-Market in the form of results of a survey about malware infections in small- and medium-sized businesses—acronym: SMBs. The article is titled "Survey: SMBs Plagued by Spyware," offering analysis of results of a Computing Technology Industry Association (CTIA) survey. One of the conclusions of the survey is that malware infections cost a typical 50-person shop $8,239 per year in lost productivity.
Taking someone's pulse is easy. That's what this survey did. Understanding why the pulse measured as it did is far more difficult—and far more interesting if you want to get to the bottom of the problem. And that's what I want to know about the malware infections covered in the survey. They exist, sure, but how did they occur in the first place? That, to me, is the real question that needs answering. Did the infections come from weaknesses in the business' IT infrastructure? Did they come from virus-laden email messages passing through the corporate email system? Did they come from automatic downloaders at malicious web sites; and if so, were the sites visited as the result of spam email or compromised legitimate sites? Did they come from email messages opened at work by employees accessing their home email accounts?
I mean the questions are endless. And unasked.
Exhibit B came from a prestigious academic institution: Berkeley Center for Law and Technology. Titled Measuring Identity Theft at Top Banks, this study attempted to take a different type of pulse reading on "the relative incidence of identity theft at major financial institutions." Banks and other commercial entities weren't about to cough up data on customers getting screwed, so the author used the Freedom of Information Act to obtain Federal Trade Commission consumer complaint data from three different months of 2006. There were certainly a lot of data points: over 46,000 complaints that identified an institution.
Now, "identity theft" has a number of guises, as the study readily admits. The study was not able, for instance, to tell if a particular identity theft report was the result of a new account having been opened fraudulently or an existing account having been hijacked. Nor was any distinction drawn between theft with or without an online component. The study appeared to be more interested in the institution names supplied in the complaint form.
The tabulated findings were both predictable and troubling. Predictably, big-name banks that issue credit and debit cards rate high among reported incidents. Troublingly, telecommunications companies (e.g., AT&T, Sprint/Nextel, Verizon) were also among the most-reported.
(What are all these telecom companies doing in identity theft reports to the FTC? I think that finding, in itself, deserves investigation to find out exactly what consumers are reporting. Let's face it, you've got to be pretty pissed off to bother filling out the FTC complaint form. What's happening to all of these pissed-off consumers?)
My issue with the entire study comes from what I believe is a faulty premise stated in the paper's conclusion section:
In order for the market to effectively address the ongoing identity theft epidemic, consumers need reliable information about incidence of the crime among institutions. If data were available on this crime, consumers could choose safer institutions, regulators could focus attention on problem actors, and businesses themselves could compete to protect consumers from this crime.
As with Exhibit A, this paper fails to address the issue of how identity theft occurs at the institutions it has identified. To blame one institution as being inherently less secure than another based solely on the number of theft incident reports just doesn't seem right to me. I have a hard time blaming a financial institution whose customers are phished to death because of the Willie Sutton Rule. If, despite warnings on the bank's web site, a customer falls prey to a clever phisher, that customer has given away the keys to the account. How can anyone blame the bank for believing someone with your full credentials isn't you? If you gave a house key to a tradesman, and he robs you six months later, are you going to file a complaint or law suit against the maker of the door lock?
These two exhibits are simply emblematic of the tons o' surveys and studies about malicious online activity that don't connect the dots. Where there is a successful online crook, there is at least one victim. My inbox and trash pile tell me that email connects those two dots on a consistent basis. That's why I believe the it's vital to arm all email users with the knowledge to identify and ignore every crook that seeps through the technological cracks.
Posted on March 09, 2008 at 01:57 PMMarch 03, 2008
CAPTCHA Right Back Atcha
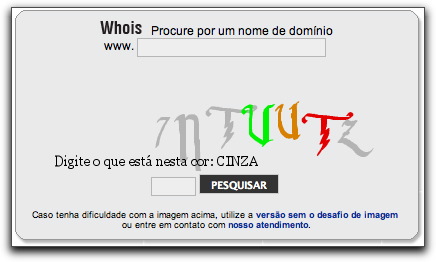
As technology employed by spammers for electronically deciphering CAPTCHA images improves (so they can do things such as sign up for tons o' free email accounts or spam the crap out of blog comments), CAPTCHA images try to make themselves increasingly difficult to read...especially for humans. Check out the following nightmare I encountered while trying to report a security issue at a Brazilian (Portuguese) site:
Are those two "u" characters in the middle or a "v" and a "u"? Unless you guess correctly the first time, you won't get a second chance. The replacement image for the next try has different characters to misread.
If good guys and bad guys keep fighting this battle, we humans may be better off reverting to foot messengers and smoke signals for their speed and convenience.
Posted on March 03, 2008 at 09:03 AM