| Home | The Book | Training | Events | Tools | Stats |
March 29, 2009
Mix 'n Match Phisher
When I was in elementary school, one homework project was to create color drawings of the planets of the Solar System. Believe it or not, I was no more talented as an artist when I was in 4th grade as I am now. I couldn't draw a circle with a compass back then, just as I can't now electronically draw a straight line with the constrain key down.
My very artistically-enhanced older brother took pity on my poor excuses for drawings and pitched in to help with some of the toughies, like Jupiter and Saturn. His drawings were magnificent, and it would have been painfully clear to a chimp that as you flipped through the planets, the quality of the drawings was, um, inconsistent. My teacher was certainly not fooled, and my grade for the project was adjusted accordingly.
What brings that childhood memory to mind is a PayPal phishing message I just saw. The message body clearly came from a phishing kit. The language of the body is accomplished and there are no spelling mistakes. But the sender had to fill in a couple of pieces of data in the email message, notably the From: and Subject: fields. This is where his crayons went askew, as the English language does not seem to be his forte:
From: PayPal <supports@paypal.net>Subject: Need PayPal Accaunt Information
Oh, dear. C-minus.
Posted on March 29, 2009 at 04:36 PMMarch 27, 2009
Phony Classmates Spam
People have love-hate relationships with Classmates, a site that tries to connect fellow school classmate alumni. I had a very bad experience with them in the early days, wherein very soon after I signed up with a special address, that address became a spam target. I immediately severed my relationship with the site, and, well, that's one more no-longer-usable account name for the spamtrap list. I also object to some of their banner ads that suggest that they somehow know you are being sought by your old classmates—a preposterous idea. Other people I know haven't had the problems I experienced and use the service all the time.
All the more odd to find a spam message today that claims (in the highly forgeable From: header field) to come from classmates:
From: "Classmates Support Center" <announcecenter41@classmates.com>
More appalling, however was the rest of the message:
Subject: Classmates private: Exotic Dancing (Last rated by Brittany Montano)Announcements: Posted March 27, 2009
News from Classmates - Classmates Hot Body Dance Video Competition!
Today: "Girls in beautiful black underwear dancing in the pub, showing off perfect bodies. Unbelievable Final!"Proceed to view full video:
http://classmates.messagecenter.disbursements.personalid-gjhqakl4r.authentication.[removed].com/registration.htm?/based/application=5uasps5kj90xc3b
Added 73 minutes ago. Message ID: CM-oxst28fjpgp2wxe
2009 Classmates, Get news as it happens.
This just seemed way too bizarre to be true, and, of course, the domain name of the link (if you know enough to get past the five (!) subdomains) is not to classmates.com. The domain is one that was created way, way back earlier today.
I suspect that the destination page uses the old "install the codec to view the porn" trick to get visitors to install malware. The only boob you're going to see is yourself in the mirror once you find your PC is pwned.
The destination page might also query users for their classmates.com user IDs and passwords. Not that one's classmates.com account has much worth hijacking, but any pair of login credentials is gold because users tend to use the same pairs for multiple sites, including those whose accounts have real value. Automated crook systems are out there pounding every online financial institution and e-commerce site with known login credentials to gain access and bleed you dry.
Classmates.com does have lots of satisfied customers, and if those trusting souls receive this message, the unwitting ones will click the link and potentially get in big trouble. How about I threaten clickers with a black mark on their permanent records?
Posted on March 27, 2009 at 08:43 AMMarch 24, 2009
PayPal Phishing via Attachment
The usual modus operandi of the phisher is to spam an email message claiming to come from an organization (e.g., financial institution) and bearing a link to a web site (usually a hijacked site) where a phony login screen appears. BTDTGTTSAWIO.
I saw a PayPal phishing message today that tried to work around smarter email recipients who know not to click on links. Here's the message:
Subject: You have successful added a new email adress [sic*2]Dear PayPal member,
You have added [removed]@hotmail.com as a new email address for your PayPal account.
If you did not authorize this change, check with family members and others who may have access to your account first. If you still feel that an unauthorized person has changed your email, submit the form attached to your email in order to keep your original email and restore your PayPal account.
Thank you for using PayPal!
The PayPal TeamPlease do not reply to this email.
This mailbox is not monitored and you will not receive a response.----------------------------------------------------------------------------------------
Copyright © 1999-2009 PayPal. All rights reserved.PayPal Email ID PP007
The attachment is a file named Email Reset Form.pdf.html. The file name is using one of the oldest tricks in the book, namely to use a double extension in the hope that the user has the default "hide extensions" option turned on in Windows, thus making the file look like a PDF file. While we know that a PDF file is not guaranteed to be safe, I doubt most non-techie users have the same fear, and would treat the file as something to open safely.
Wrong!
The file is a base-64 encoded HTML file. Opening it from an email client would launch the user's default browser and load the page. The page contains nothing but a meta-refresh tag that automatically navigates to a hijacked server in Texas. And that destination has yet another meta-refresh tagged page going to a DNS server in Florida that has been pwned to serve up a thoroughly bogus, but extremely believable PayPal login page.
It appears to me that everything about this campaign except the Subject: line of the message is from a polished, off-the-shelf phishing kit. Maybe the scammer needs the funds to take the next semester of English language class, where they teach adverbs and spelling.
Posted on March 24, 2009 at 10:16 AMMarch 22, 2009
Phony DHL Invoice Malware Delivery
Here is the text of a fake message claiming to come from DHL, the international package delivery company:
Subject: DHL Tracking number #W46JA79872R0U24Hello!
We were not able to deliver postal package you sent on the 14th of March in time because the recipient’s address is not correct.
Please print out the invoice copy attached and collect the package at our office.Your personal manager: Simone Gallegos,
Customer Service: 1-800-CALL-DHL
Fax: 888-221-6211
DHL International, Ltd. All Rights Reserved.
The goal, of course, is to get you to open the attached file named DHL_DOC.zip. A quick test through VirusTotal shows that a mere 7% of tested antivirus products immediately identify the file as malicious.
Before you think that no one could fall for something like this, consider that as I sit here, I am, indeed, awaiting delivery of a parcel from Germany that will arrive at my post office, but that is carried part of the way via DHL (and Deutsche Post). True, I didn't send the parcel (as this message relates), but when your brain sees things that it recognizes, it may fill in blanks the wrong way. In any case, there are a gazillion clues in the email message's header that this announcement is bogus, but not every recipient of this malware lure will be as perspicacious when it comes to suspecting email messages.
As I said the other day, treat all incoming email as suspicious until you can confirm otherwise. And by "confirm," I don't mean double-click attachments to see what happens.
Posted on March 22, 2009 at 04:25 PMMarch 19, 2009
How Spammers Poke and Prod You
I had a note from a Dispatches reader the other day who was psyched into opening a medz spam. Now, this reader claims to be a spam wars veteran ("I have a huge problem with spam mail."), and has even grown inured by it ("As i am used to it,...."). That latter situation is the sad state of affairs we are in. No matter how good your filtering (if you have any), some spam gets through, and you grow accustomed to some level of intrusion into your inbox.
What upset this correspondent was that the medz spammer used what I call the "impending doom" type of Subject: line to get his attention. In this case, the line was:
Subject: your ip saw on illegal sites
Grammar problems aside, if you sense from a Subject: line that you are being wrongly accused of something, your first instinct is to jump into it and defend yourself. For example, my correspondent was confident that the accusation was false, yet he admits "this title made me feel very bad."
As I have recounted many times before, both in the Spam Wars book and in previous Dispatches postings, the more a Subject: line in a message from an unknown sender tries to stimulate you to action, the more you should suspect the message is a complete fraud. The stimulant might be an accusation, as in this case, or some OMG! news item (e.g., a world leader dying or massive regional tragedy). The tactics have been used repeatedly over the years for tricking recipients to open attachments, to visit drive-by malware installation web pages, and, as in this case, to see the umpteenth pitch for medz, knock-off luxury goods, or adult content.
My attitude in general about email is a very cynical one. I suspect every email message from an unknown sender in my inbox to be unwanted until I am convinced otherwise. Sometimes, that means I have to inspect the content (viewing only the source code without downloading images or other external content), but because I start out with a negative vibe about the message, I'm never disappointed. On rare occasion, I'm pleasantly surprised to find a personal message from a real human about a subject of interest to me.
I still have fond, sepia-toned memories of my early days in email—before you could even send a message from one provider to another. I'd log onto The Source or CompuServe and find only messages from people who wanted to communicate with me for who I was, not for the money in my wallet, the value of my email address on a list, or the processing cycles in my computer. I'm afraid those spam-free days have done the ol' 23 skidoo.
Posted on March 19, 2009 at 12:20 PMMarch 16, 2009
Malware-Laden Ecards Keep Coming
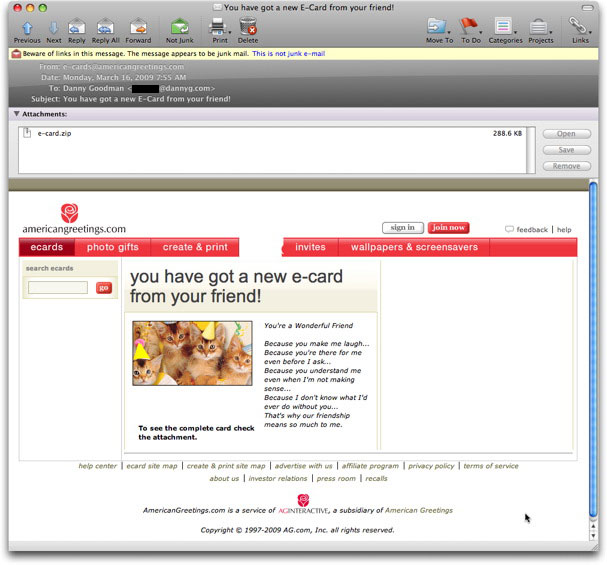
It's an oldie but apparently a goodie: an email message that claims to come from a legitimate e-card company bearing an attachment that will be cause for anything but a celebration.
The message sender in the one I saw today went to some lengths to recreate the look and feel of the americangreetings.com web site—a genuine service of a well-known (here in the U.S.) company, American Greetings. Except for one rendering glitch in my email reader, it has all the right elements:
I mean, who can resist an email with a picture of kittens wearing Photoshopped party hats?
The email claims to display the start of an e-card message, the remainder of which is promised to be in the attached file, e-card.zip. There is no identification of the sender, and the false message beginning is so generic, it could be in a printed greeting card at the store. On the other hand, all of the links on the page go to real americangreetings.com pages. That could help some recipients believe the message and attachment are legit.
A VirusTotal run of the file comes up with hits for nearly 60% of the tested antivirus brands. It is most commonly identified as being of the Buzus class, which opens a backdoor to an infected PC, allowing it to be pwned via IRC.
Tell your friends and neighbors.
Posted on March 16, 2009 at 08:53 AMMarch 09, 2009
419er Seeks Dumbest Guys in the Room
The Enron debacle, portrayed in a book and movie titled The Smartest Guys in the Room, lives on in a preposterous 419 letter arriving today. The basic claim is that Ken Lay and Jeff Skilling deposited 37.5 million Pounds into Deutsche Bank in London back in 2001. Then the usual blah, blah, blah about no beneficiaries and other garbage to entice recipients to capture around $20 million for their trouble.
Here's the whole tale, coming from someone claiming to be the Auditor General of the bank (yah!):
Dear,
First of all, let me start by introducing myself. My name is Mr. Ray Smith,the Auditor General of Deutsche Bank London. I have an urgent and very confidential business proposition for you.I am the accounting officer of Mr. Ken Lay, Enron founder, who deid on July, 5th 2006, at the age of 64 and his friend and partner Mr. Jeffrey Skilling, Ex-Enron CEO who was recently convicted 24 years for his involvement on the collapse of Enron, the energy trading giant in America.It will interest to know that on Wednesday, 7th February 2001, Mr. Ken Lay deposited a total sum of 20M pounds and on Tuesday, 24th April 2001, Mr Jeffrey Skilling deposited 17.5M Pounds in our Bank. These funds were deposited into a non-existing company's account which I opened in our bank (DEUTSCHE BANK LONDON) under their instructions, to avoid raising an eyebrow but unfortunately for them and fortunately for me, the 2 men are gone.
You can read more about the sentence by visiting the below websites:
http://www.chron.com/news /specials/enron/
http://www.accountancyage.com /accountancyage/news/2171002 /enron-ceo-sentence-slashed
http://www.economist.com /business/displaystory.cfm ?story_id=8082101
So right now, we have the sum of 37.5M Pounds lying in the 2 accounts without any proof of ownership as it was opened with non-existing companies name and the bank is not aware of the real beneficiaries as the accounts did not bear any name. As their accounting officer and financial adviser in charge of these accounts, I can comfortable present you to the Bank as the real beneficiary of the funds and they have no right to deny the application.
Consequently, my proposal is that I want to seek your consent as a foreigner to stand as the owner of any of these accounts, since it has no trace or beneficiary which makes it easier and fine to transfer to your designated bank account as the beneficiary. The nature of my work as a staff of the Bank will not allow me lay claim on the funds, hence this proposal to you and be informed that as long as you are ready to cooperate and be truthful to me, I can assure you that the sky will be our limit.All documents and proves to enable you get any of the money will be carefully worked out and more so, I assure you that the business is risk free, as everything will be handled in accordance with the International Monitary Guidelines. I am offering you 40% for your cooperation in achieving this aim.Please, if you are interested in working with me, I will like you to send the below informations to enable me procure the necessary documents that will back up the transfer to your account:
1. YOUR FULL NAMES AND ADDRESS.
2. AGE AND MARITAL STATUS.
3. OCCUPATION.
4. NATIONALITY.
5. TELEPHONE AND FAX NUMBERS FOR EASY COMMUNICATIONS.
As soon as I receive your acceptance mail by forwarding the above informations, I will prepare the paper works in your name for onward remittance of the funds into your designated account.
Lastly, I want you to understand that this transaction requires trust,honest and above all, utmost confidentiality, to avoid escalating.
Regards.
Mr.Ray Smith
The Auditor General,
Deutsche Bank London.
Gee, you'd think that the Auditor General of a major European bank in London (England, whence English) would know how to spell "monetary."
I guess this guy hopes to find one of two types of people.
The first would be someone greedy enough and lacking a conscience who wouldn't mind grabbing a bunch of money that was (had it really existed) rightfully due former stockholders and others with claims on the company's assets. Lots of innocent folks had their life savings wiped out when the company went bust. Sadly, there probably are people out there who wouldn't mind lighting cigars with Benjamins sourced this way.
The second type would be someone who really did get screwed by Enron and sees this as an opportunity to get back what they lost. That would be the saddest case—someone who lost big time due to one scam, about to lose some more from another scam using the first scam as bait.
I'll bet the original author of this 419 letter got such a buzz coming up with the idea that he was up the whole night composing it and looking for supporting news stories on the web. And here I am, breaking the confidentiality. Oh, boo hoo.
Posted on March 09, 2009 at 10:21 AM