| Home | The Book | Training | Events | Tools | Stats |
September 29, 2006
Another Spammer D'Oh!
I love it when a wannabe spammer who doesn't understand the technology is so eager to flip the switch to send out spam through botnets that he or she screws up Big Time. It's even better when the mistake reveals some inner workings.
Thus my glee to receive the following spam message template instead of the message filled with "mail merged" words/phrases plugged into the %placeholders:
%GREET%DEGREE - 2007
Academic %QUALIFICATIONS %AVAILABLE from %NONACCREDITED %UNIVERSITIES.
Do you have the %KNOWLEDGE and the %EXPERIENCE but lack the %QUALIFICATIONS?
Are you getting %TURNED down time and time again for the %JOB of your
dreams because you just don't have the right letters after your name?Move ahead in your %CAREER %TODAY!
%BACHELORS, %MASTERS and %PHD's %AVAILABLE in y our field!Call to register and receive your %QUALIFICATIONS within days!
24 hours a day 7 days a week! - Confidentiality assured! - Worldwide!
%NUMBER
%EXIT
The machinery behind this mailing failed to replace the placeholders with various synonyms, greeting and exit paragraphs, or—double oops—the phone number to call to get your phony degree. It looks as though this spammer could use a short course in setting up a spambot. Idiot!
Posted on September 29, 2006 at 02:28 PMSeptember 27, 2006
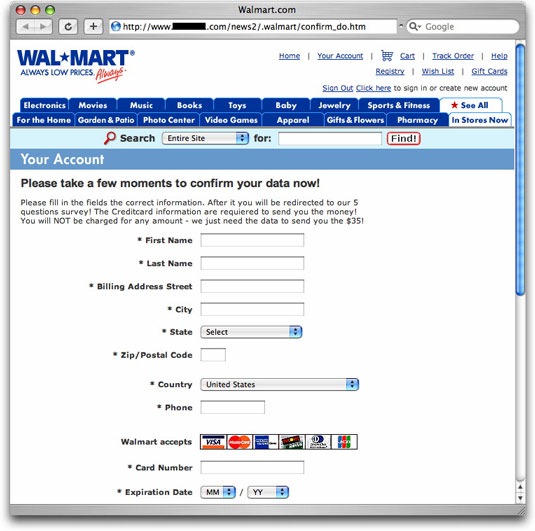
Wal*Mart Phishing
What's more popular than eBay and PayPal together? Wal*Mart!
That's why a new phishing scam I saw today is so potentially ruinous to lots of folks. Here's how it works:
An email message bearing the Wal*Mart logo (served up from walmart.com, no less) arrives with the following content:
Dear Customer,
CONGRATUALTIONS!!
You have been chosen by WAL*MART online department to take part in our quick and easy 5 question survey.
In return we will send $35 to your confirmed Credit Card - Just for your time!
This survey has been sent only to a few people from our random generator!Helping us better to understand how our customers feel, benefits everyone. With the information collected we can decide to direct a number of changes to improve and expand our online services.
This information you provide to us is all non-sensitive and anonymous - No part of it is handed down to any third party groups.We kindly ask you to spare two minutes of your time in taking part with this unique offer!
To Continue click on the link below:
https://www.walmart.com/cservice/survey?customersurvey=546
Sincerely,
Wal*Mart Online ServiceEmail PID: 546
Copyright 2006, Wal*Mart. All rights reserved.
That link is what the user sees. Behind it, in the HTML, is the true link, which goes to a hijacked site belonging to a California high school track team. Here's the page you'll eventually see there:
Millions of trusting folks shop at Wal*Mart. If they receive this phishing message, they probably won't be able to discern that it's not coming from Wal*Mart. The prospect of getting 35 bucks for filling out a survey is too much to resist.
If this one spreads, it will trap an awful lot of innocent victims. Please spread the word to everyone you know.
Posted on September 27, 2006 at 11:23 AMSeptember 22, 2006
Email Moebius Strip
Ah, the frustrations of trying to do the right thing in today's spam-infested waters.
One of today's phishing sites is located in South Korea in an IP block run by a not-very-responsive outfit (surprise, surprise). But this block also had a separate technical contact that gets closer to the actual IP address of the server that had been hijacked by the phishing crook.
In addition to emailing the fraudulent phishing page report to the main abuse address (whose previous response time was glacial—or the hacked server crapped out from old age), I included the address of what might be a real person at the organization responsible for just a small slice of the main IP block.
(In truth, my expectations weren't high to begin with. The email address user name is "mrzombie" at a dot-net address. Although the dot-net domain is hosted in a Korea, was this a legitimate user name, or a deflection tactic to prevent address harvesting from whois records? I may never know for sure.)
The copy of my report that went to the tech contact bounced with the following report:
(reason: 553 Blocked for spam)
At first I thought perhaps my inclusion of the original phishing message source code could have triggered a spam filter. I resent the message without the source code. Just a two-sentence message that included the link within their IP space.
That message bounced with the same result.
Unfortunately, the bounce message (and it was done with a separate bounce message, not an immediate rejection, like it should) doesn't tell me why my message is considered spam in this server's eyes. It's either because the phishing link includes the string "paypal" or, more likely, it's because my email message originated at a Comcast IP address. That's how I connect to the Internet, although I don't use Comcast's email server for outgoing mail.
Comcast used to have a terrible reputation for not blocking spam blasts from bot-infected customers, so perhaps I understand why mrzombie's server bounced my messages. But, as happens in these cases, that leaves me no easy way (I could hunt down some anonymizer somewhere, I suppose, or try my Earthlink web mail account) to communicate with mrzombie to let him know that one of his servers is open to hijacking by crooks.
And a lot of people tell me I'm crazy to suggest that email is broken.
UPDATE (09:30:00 22Sept06): I did send the message through my Earthlink web mail account (which I hadn't used in so long, they had stopped putting messages into my inbox). So far, no bounce message. Even though the message headers show the origination point as being my Comcast IP address, perhaps Earthlink's DomainKeys signature saved the day. Now, Mr. Zombie, tear down that phishing page!
Posted on September 22, 2006 at 09:14 AMSeptember 19, 2006
Using CAN-SPAM Against Consumers
I was looking through the source code of a spam message whose characteristics are identical to several that have come through lately from the same source. These guys have huge IP address blocks that they use, and they keep adding blocks all the time.
High-volume spammers who don't use botnets to send their spam typically do what they can to stay within a millimeter of the CAN-SPAM law to avoid problems on that front. Among the provisions of the law are those that mandate that a spammer identify itself honestly in the message and provide a way for the recipient to be taken off the mailing list. To that end, I've seen several veteran spam outfits include their names and mailing addresses in the bodies of the message—but doing things like inserting variable spaces between characters, substituting zero for capital "O," and other things that make it harder for text filtering to spot the spam.
That these outfits already have my email address is unfortunate, but at the moment, they don't know for sure that their messages are actually getting through. I never unsubscribe from a mailing list to which I have not explicitly subscribed, because history reveals that such unsubscriptions give the spammer a fresh email address that they can resell to other spammers or use in a different campaign. Still, I like to know how these guys identify themselves in the spam message.
In today's message, the spammer apparently satisfies the identity/unsubscribe provisions of the CAN-SPAM law, but he does it in a way that won't let me even preview any of that without revealing that I have seen their message. For, you see, the CAN-SPAM-abiding stuff is only visible in a downloadable image. The URL for downloading that image has lots of code numbers on it—numbers that very likely can be tied to my email address in their database. The HTML tag for the image includes what is known as an "alt attribute," which displays text when the image is not displayed (as when you have downloadable images blocked in your email viewer). The alt attribute contains the following instructions:
alt="To view details on the sender, enable image viewing."
Right. Enable image viewing, and thus send up a signal flare that your email address is actively read and lets their crap into the inbox.
Imagine that! A spammer has found another hole in what is already a Swiss cheese law.
Posted on September 19, 2006 at 08:50 AMSeptember 18, 2006
Scary Stuff
Unfortunately, plenty of legitimate Web sites get hijacked by phishers. The crooks find a way into the system and either set up new accounts or simply create a new subdirectory, in which the lookalike Web site is planted.
Most of the hijacked sites, however, are not places you'd expect high security. They're typically sites set up by small shops or organizations with a passion for their subject matter, but their creators are not security experts.
But today I received a phishing message whose link led to a hijacked site belonging to a Kansas bank. The crook had created a semi-hidden subdirectory (a name beginning with a period, which doesn't show up on default directory listings). The bank offers online banking, as well, but I don't know if that portion of the site has been compromised. More troubling, however, is that they don't seem to think the hijacking is anything worth taking care of anytime soon. Six hours after I reported the situation, the phishing page is still running.
I'm glad I don't have an account there, and I hope you don't either.
Posted on September 18, 2006 at 09:05 PMSeptember 09, 2006
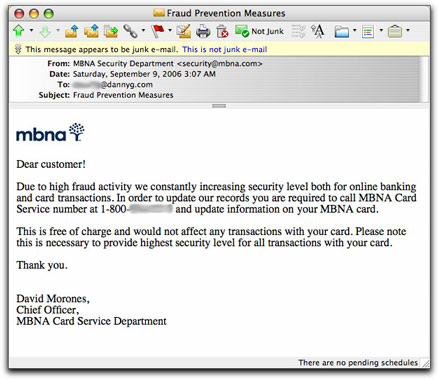
Phone Phishing
I had heard of this ploy, and now I've finally seen one in the wild.
Even without diving into the source code, the email message has all the hallmarks of a phishing message from a financial institution. But instead of directing the recipient to click a link to a fraudulent site, the message provides a toll-free (in the U.S.) phone number to call.
Here's what the message looks like:
I haven't called the number for a couple of reasons. First, Caller ID is not blocked when phoning toll-free numbers, so I don't want to give my number away to crooks. Second, it is possible to have toll-free calls diverted to very costly international calling services without the caller's permission (this is illegal, but, hey, these are crooks).
From what I've heard, however, a call to this number would get me a recording that requests personal identification data. My responses would be recorded and picked up by the crooks who will then use or sell the data at my peril.
Because I didn't have any business with MBNA, I knew right away this was a hoax. The message's opening "Dear customer!" is also a dead giveaway to those who see lots of phishing messages. But to the uninitiated, it sounds legit. And the 800 number makes it sound even more so.
The truth, as always, lies in the one piece of message header information that is very difficult to forge. Something tells me that MBNA (now a part of Bank of America) would not send customer advisory email messages from Dutch cable/DSL provider chello.nl.
UPDATE (15 September 2006): I just received one of these claiming to come from PayPal. Watch out!
Posted on September 09, 2006 at 01:12 PMSeptember 08, 2006
Clueless in Bethesda
Last week I contacted the owners of a Web site that had been hacked by phishers so they could get the fraudulent material off their site ASAP. (OK, I do this several times a day, but I'm referring to one specific instance.) When I send these email messages, I do so from the abuse@ address of the domain having received the phishing message.
The site belonged to an Irish pub in Bethesda, MD.
A week later, I receive—addressed to my abuse address, mind you—an automated bulk "Weekend Update" email message listing their special opening schedule to coincide with some televised football (soccer) matches from the U.K.
When this outfit's email server winds up on blocklists, they'll be the first to complain, "We don't send spam!" To which I advise consulting this blog entry.
Posted on September 08, 2006 at 09:20 AMSeptember 02, 2006
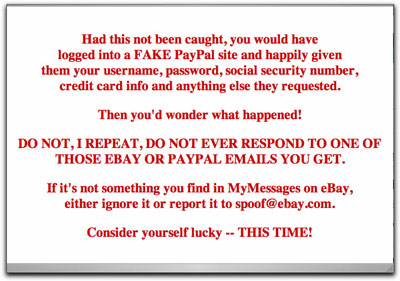
Are Phishing Sites Being Re-Hacked?
In the course of my get-the-phishing-site-shut-down activities, I check back with the URLs I report to see how quickly (or if) the sites have been shut down yet. The majority of phishing pages I see come from a legitimate server that has been cracked by crooks who put their bogus stuff in (sometimes partially hidden) subdirectories. Once such a page has been shut down, the site's true owner or ISP sometimes redirects the URL to the site's real home page. Or, more typically, the URL is just left to dangle, returning a standard 404 "Not Found" response to the visiting browser. As long as the crook can no longer gather usernames and passwords from ill-informed victims, anything is okay with me.
In the last few days, however, I've seen two separate instances in which the original destination page had been replaced by a stern warning to the visitor that by following the link in the phishing message, he/she could have gotten into big identity or credit card theft. Here is one of them:
Now, I'm all for consumer education, but the source of these messages is almost as curious as the phishing attempts. Neither one identifies the source of the message as being associated with the ISP or site owner. You'd think that the site or ISP would want to take credit for having shut down the phony page and alerting potential victims about the scam (although admitting to having been cracked takes some guts).
More curiously, the first one I saw had a completely different look to it, far from perfect English syntax/spelling, and even handed out grades to the phishing crook for his level of proficiency (reportedly quite low) needed to hack the site. This one was "signed," but by someone using the name of a character from the original Star Trek series.
These two separate incidents make me wonder if some anti-phishing folks are fighting back with the phisher's tactics of taking over sites that had been taken over, replacing the bad stuff with, well, less bad stuff.
I won't condone cracking anyone else's site, even if the owner or ISP left the keys in the ignition (read: didn't change default passwords or haven't patched their systems). This is definitely a possible trend to watch.
Posted on September 02, 2006 at 01:02 PM