| Home | The Book | Training | Events | Tools | Stats |
October 28, 2008
Help (Money Launderers) Wanted
In times of rising unemployment, money-laundering spam like the following one probably attracts a few more respondents than normal.
Subject: New job offer from international company.Dear Sir/Madam,
AutoPay Inc.looking for local branch adminitsrators in Uited States only!
You will work in your city, no trips, no relocation.
Vacancy: regional payment administrator (male and female) , salary: 2600-2800 per week.1)21 years and older,
2)2-3 hours per day (monday - friday),
3)education - any basic.For more details mail to: [removed]@aol.com
Sincerely, Wilford Connolly.
AutoPay Incorpotation.
I also foresee retirees suffering from diminished investment income falling for this scam—spelling notwithstanding.
Posted on October 28, 2008 at 07:45 AMOctober 23, 2008
Spear 419ing
You've probably heard of spear phishing, a technique of targeting employees—if not specific employees—of an organization to fool them into revealing information about computer system security (e.g., username/password combos). There is less automation in spear phishing than regular phishing because the crook makes an effort to simulate details about the organization in the phishing email message, thus making the recipient believe the message originated from within the system.
Today I saw an example of "spear 419ing," a highly targeted advance-fee fraud attempt tailored just for li'l ol' me as book author. Here is the message:
DEAR SIR/MADAM,
I AM TUNDE GLOVER.THE MANAGING DIRECTOR OF FRANKLING.KINDLY BE INFORM THAT I WILL LIKE TO ORDER THE BELOW BOOK TITTLES:
JavaScript Bible, 6th Edition --------------------15 copies
JavaScript & DHTML Cookbook, 2nd Edition--------------------15 copies
Dynamic HTML: The Definitive Reference, 3rd Edition--------------------15 copies
CALCULATE THE TOTAL COST AND THE SHIPPING COST TO MY
ADDRESS BELOW
VIA
FEDEX PRIORITY OR DHL WORLDWIDE EXPRESS OR GLOBAL
MAIL.LET ME HAVE YOUR
TERMS OF PAYMENT.
FRANKLING INC
2 odunlami street
lagos island
lagos state
23401
nigeriaphone:+234[removed]
[removed]@yahoo.com
AWAITINNG TO RECEIVE THE QUOTE BY TODAY
The message was sent through the real yahoo.com email system. It therefore included the DomainKey signature to help guarantee its delivery through server-side spam filters that look for such things.
All three links in the HTML message were to book listings at my dannyg.com web site. This guy did his homework.
And so did I.
Discounting the excessive use of all caps and a claimed address in Nigeria, there were (for me, anyway) two additional giant red flags that this message was a scam:
- He's using yahoo.com email for criminy's sake!
- In a part of the world where nothing gets done today, he's insisting on a quote today.
Next stop: Google.
The name Tunde Glover turned up only a handful of references to a computer game artist or designer. There were no listings for a Franking Inc in Nigeria.
Then I tried the street address, "2 odunlami." Holy crap!
If such a place exists, either it is a reputable building with which the crooks want to feel associated, or it's a massive den of thieves.
One point is certain: This isn't the first time these crooks have targeted books in their scams. I found tales of small publishers who accepted credit card orders, rushed the books out by FedEx, and then had the credit card charged back later—leaving them out both the books and hundreds of dollars in unrecoverable shipping charges. In fact, according to one victim, before the chargeback came through, the scammer placed an additional order. The crook also wanted the publisher to buy him a cell phone and put it into the next shipment. It wouldn't surprise me if some of the "payments" for this scam also come by way of bogus foreign bank checks for more than the invoice amount. Such checks literally take weeks to (not) clear...meanwhile the "customer" had insisted on instantaneous shipment of the goods and the excess payment amount immediately wired to Africa.
I had seen ship-it-to-Africa-today scams for years and years. Most commonly, the crooks target eBay sellers of expensive goods (jewelry and electronics mostly). The game is to yank the chain of customer satisfaction—something that legitimate merchants take great care to meet. And, let's face it, merchants deal with new, unknown people all the time. Spotting a scammer isn't always easy. In a business downturn, it's too easy to get caught up in the excitement of a big order that has to be handled right away. But it's exactly at that moment when you have to keep your wits about you and protect yourself or your company first.
Interestingly, the version of the scam that I received doesn't explicitly say that payment will be by credit card (as most of the others did). He says (allow me to lowercase it for you), "Let me have your terms of payment." I'll bet if I insist on a Western Union money transfer—the way scammers want money sent to them—the crook would come up with enough excuses to fill a 747 Freightliner. Today.
Posted on October 23, 2008 at 08:53 AMOctober 21, 2008
Fake CAPTCHA on Phony Phishing Site
I'm always amazed to receive a phishing message aimed at customers of a tiny institution that I had never heard of prior to receiving the message. That a phishing crook bothers to send what should be highly targeted messages to any ol' email address just seems like a waste of even cheap spamming resources. It's the inverse of shooting fish in a barrel—more like shooting fish in the Mediterranean Sea from Mars.
Today a phisher introduced me to an existing online payment system that was news to me. I'm not going to advertise for them, so don't expect me to name the real site here. Wikipedia has an entry for them—for whatever that's worth (hell, someone even put up a now badly-outdated entry for me).
The phishing message consisted of an image (downloaded from a free image hosting service) containing the text of the message. To entice action on the part of the recipient—if he or she should be the one-in-ten-million customer of the targeted institution—the message claimed that the user had to click "here" (anywhere on the image, actually) to acknowledge a few items in the terms of service shown in the image.
I looked over the genuine company's Terms of Service document and saw that the wording for the phishing message sections was copied directly from the real document. Of course no one reads Terms of Service documents (well, I do) or remembers them (well, I don't) to recognize whether something showing up in an email message reflects changes to the original. But the key point is that by copying verbatim from official documents, the phishing message used terminology that was localized to the institution (the first time I've heard of withdrawals or payments referred to as "spends"). Thus, if our Martian's bullet should find a Lusitanian toadfish off the Moroccan coast, the fish would recognize the ammunition.
Upon safely checking the phishing site, I found the usual form requesting login credentials. In an effort to make the phishing page look official (the layout reproduction was very well done), a CAPTCHA image is displayed. The format and look of the image is identical to the type used by the real web site's login page. The big difference, however, is that unlike real CAPTCHA images, this one doesn't change with subsequent reloading of the page. It's the same darned "2015" every time, whereas the real site's CAPTCHA image changes with each reload, as it should. Unfortunately, I doubt many potential phishing victims would know to test for this behavior.
The phishing site is being hosted through an Afghan ISP. In the site's source code, I also found a pointer to an Indian site where the well-crafted page originated. I don't think the Indian phishing kit creator wanted that kind of advertising. Oopsie.
Oh, and the Indian original fake site had the same CAPTCHA image.
Posted on October 21, 2008 at 09:34 AMOctober 14, 2008
A Botnet By Any Other Name...
Some malware researchers have been popping champagne corks the last day or two over signs that the Storm botnet appears to have stopped recruiting new PCs for its army. Recruitment activity seems to have been completely dormant for the past month. In the meantime, Microsoft reports having cleaned up over 270,000 Storm-infected PCs through its own malicious software removal tool in the past year.
While I laud the work of these researchers and follow their activities avidly, the audience I try to reach—the average email user—hasn't a clue about botnet names or what distinguishes one botnet from another. That Storm is down but Srizbi is up doesn't mean squat to the recipients of spam generated by either's army. My spam levels haven't subsided to any significant degree—in fact, there has been an increase here in the past few weeks.
Other botnets have imitated the social engineering tricks "pioneered" by Storm, so a typical email user can't tell which botnet is responsible for the latest phony e-card malware lure (as I've been seeing the last couple of days here). Nor does it really matter.
As long as email users continue to fall for whatever tricks are foisted upon them—whether it be to have their PC turned into a botnet soldier, or to buy crap or visit web sites promoted by botnet-using spammers—the spam will continue. If the world has re-learned nothing in the past few weeks, it is the economy (stupid). The overt and covert economies of spamdom, which include building botnet armies to send spam, still have enough money flowing through them to keep the spam senders, address harvesters, and private information-stealing crooks in business. Only when a critical mass of everyday email users stops acting on spam in ways that fuel spammers will the levels start to go down. Unfortunately, due to the extremely low cost of flooding the internet "tubes," the critical mass of which I speak, is an extraordinarily high percentage of email users. Helping achieve that critical mass is what I work toward, and is the toughest challenge I've battled against in my life. It's way too early to sip the bubbly.
Posted on October 14, 2008 at 11:05 AMOctober 12, 2008
A Skype Invitation to Disaster
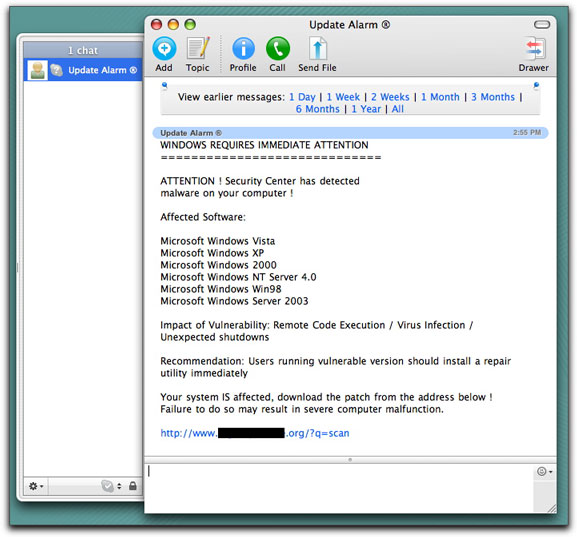
The following chat popped up under Skype today:
Putting aside the fact that I was running Skype on a Mac, this "Update Alarm" sender (with a Registered Trademark symbol, no less) insists that there is malware running on my Windows machine, and that I should click the link to obtain the patch. Although I've blocked out the domain name in the image above, I can say that it is a credible name to the unaware recipient (the name contains the word "registry," which sounds very technical and must be feared).
(As an aside, I get very little Skype spam, probably because my ID is a little strange. Yet today, in addition to the one above, a plea from an allegedly sex-starved woman also popped up. I fear that my strange Skype ID is now hosed.)
Out of curiosity, I did a safe view of the source code of the home page of the site. The domain is supposedly registered to someone in Prague (possible, but I wouldn't wager any money on it). The home page is loaded with tons of JavaScript, including a routine that reads an external file consisting of a list of PC files that this page claims to be scanning. The scan, however, is just a loop timer that displays the file names as the list is read. No actual scanning takes place.
Next, a random number is generated with JavaScript to show how many files on a visitor's system are "infected." That's so different visitors likely get different results.
At the end of this phony baloney scan, a visitor is supposed to be sufficiently frightened to purchase the cleanup software. I don't know what this particular piece of software does, but I can guarantee that if you were to buy and install it, your PC would never be the same. And I don't mean that in a good way.
Now, this trick has been around long enough for tricksters trying to pull this off from the United States have been convicted of wrongdoing. This guy's site is hosted in the U.S., so perhaps the Federal Trade Commission will pursue the matter.
One reason that tricks like this Skype message are so effective is that we computer users—of all flavors—are suffering from a serious case of update fatigue. We're constantly bombarded by legitimate update messages for our operating systems, our browsers, our iTunes, our Java runtimes, our Acrobat readers, our antivirus programs, our Microsoft Offices...the list of automatically-updating real software is endless. By and large, we get so many of these update announcements—usually popping up when we're in a huge crunch to finish some time-critical task—that we'll click "OK" or "Install" just to get the program to STFU. And when a crook dangles the threat of a computer infection—booga-booga—most users don't know if the alert is coming from their anti-whatever software. The idiocy of a Skype message supposedly detecting a PC's malware infection does not compute for typical PC users.
What makes me the maddest about this venerable trick, is that the crooks like to make you think they're looking over your shoulder to protect you. In truth, they're feeling up your skirt or pants leg.
Posted on October 12, 2008 at 04:19 PMOctober 08, 2008
Financial Crisis as Universal Spammer Hook
It doesn't matter what they're selling. Spammers will find some connection between their garbage and the latest financial situation to lure you to visit a web site.
When a German-language spam arrived here with all kinds of talk about "die Bankenkrise" (bank crisis) and "Panik," I first imagined that the link would be to some sort of e-gold or other type of squirrely money equivalent.
Hier ist Ihr Geld sicher: http://www.[removed].org(Your money is safe here)
What exactly is this safe haven for our dwindling cash?
Would you believe an online casino?
Mit freundlichen Grüßen,
Danny
October 07, 2008
Malware Attachments Still Circulate
It's getting harder and harder for malware-laden attachments—especially those bearing the commonly-used filename extensions—to get past server-based security software. But that doesn't mean the crooks won't keep trying. The key is to modify the package enough with each iteration to prevent the file from being identified as a known hunk o' crap.
The first goal of an attachment delivery message—once it has made it into an inbox—is to create enough curiosity or outrage in a simple message to get the recipient to open the file. I personally believe that the outrage approach is more easily exploitable against cautious recipients who are more likely to trash an email from an unknown sender containing an unexpected file.
An example arrived today that will surely get the dander up on quite a few recipients:
Subject: Your bill. Please pay within the next week.The bill is attached. Password is 123.
The attached file is named bill.zip, and VirusTotal reports that only 22% of its list of antivirus products identified it as anything suspicious. A lot of very big antivirus names missed it (at this hour, anyway). So, if the recipient was outraged at receiving a bill from a karate studio (as indicated in the forged From: field of the copy I received), he or she would open the file to find out what it's about and contest it...by which time a Trojan downloader has already been installed on the PC.
It's just another example of what I call the "impending doom" trick to get recipients to act. With the world financial situation going through troubled times, I fully expect crooks to experience a boom in doom.
Posted on October 07, 2008 at 08:38 AMOctober 06, 2008
A 419er Overloads Hook with Bait
You've seen the typical 419 letter: Someone died a horrible accidental death in Africa, and left millions without an heir.
You've seen the typical 419 lottery letter: Your email address was picked at random to be the winner of a multi-million (dollars/pounds/euros) prize.
Today I saw a hybrid—not only of these two scams, but a further scam-de-scam-scam on the scam. The 419er's story has more layers than an onion.
The sender identifies himself as follows:
FROM: MR. EMMANUEL.U.EMERUEM
PUBLICITY SECRETARY,
FOREIGN PAYMENT PROCESSING UNIT,
UNION BANK NIG. PLC
Our Ref: UBN/IRD/UBX/021/07
I'm omitting the telephone number and email address—the only two pieces of information that are real. When I saw the sender's name, I did a "redrum" check to see if he was at least trying to play a clever trick. I think I gave him too much credit.
The body of the message is overlong (and in all capital letters), so I'll peel the layers for you one by one.
Layer I.
A bunch of American contractors/philanthropists (?) and their families died in a bomb blast a few years ago (obligatory link to a 2003 BBC News item included for good measure). Despite a desperate search, no heirs could be found, and $4.7 million is sitting in a Nigerian bank.
Layer II.
The President-elect of Nigeria wants to "salvage the image" [lower-cased for your protection] and "restore the international relationship" of Nigeria. This magnanimous president directed the Nigerian bank to conduct "an electronic computer random ballot system for all emails [sic] users drawn from over emails [sic] address [sic] of individual [sic] and companies from Africa, America, Europe and Asia." [sick] Wouldn't ya know it, my email address was picked as the lucky winner! I am advised to "donate to some motherless or orphanage homes to help the less prevelages. [sic] It is mainly for the upliftment [sic] of human growth." (Not to be mistaken for human growth hormone spam.)
Layer III.
Lest I dawdle in claiming the winning prize, Mr. Redrum then reveals that "a woman with British passport came to my office few days ago with a letter, claiming to be your true representative." OMFG!! Someone's trying to cheat me out of my prize! "If we do not hear from you within the next three working days from today the fund will be remitted to Mrs. Susan Barker and this bank will not be held responsible and this our email communication shall be our evidence against you in case of any scandal or law action by you against the management of this bank."
Holy crap, that's a lot of bait on the hook. It's like the kid who uses up too much material to explain missing homework: "A burglar stole our dog who ate my essay after a plumbing leak soaked my backpack."
Because some people still fall for 419 schemes, this tall tale will certainly get those types of folks to act. Even if they're not sure about the "prize" money, they may be concerned that someone is going around Africa claiming to represent the recipient. Except that the sender doesn't have a clue who the recipient is—"ATTENTION DEAR FRIEND"—and there is no one making such claims. Anyone foolish enough to contact this guy by email or especially by phone is treading dangerously close to being conned by very convincing crooks, and taken for big bucks.
Posted on October 06, 2008 at 12:23 PMOctober 02, 2008
Why Risk Your Company's Reputation With Lies?
Scenario: You have what appears to be a legitimate business with an online presence. To solicit new business, you fill out response forms at other web sites with a message that includes an outright lie.
What were you thinking?
Here is what a recruiting company in Mumbai, India sent me via the spamwars.com contact form:
Hi Sir,
This is vijay here received your e-mail on my ID: [removed]@gmail.com, this e-mail is in regard to assist you in recruitment and staffing, as we are our a leading staffing company + BPO. We understood your requirement, For more details you can write us on vinod@[removed real company domain].com. Awaiting take this relationship forward as business partner.Regards
vijay
HUMAN RESOURCE
CRUX MANAGEMENT SERVICE Pvt Ltd
Mumbai
Not only have I never heard of this outfit, I certainly did not send any email message to this guy or anyone at the company. And, as a one-man show, I am not hiring and have nothing to outsource. And don't get me started on the lack of English skills to instill confidence in your professionalism.
I wonder if they run radio commercials in India. If so, they can add the tag line: "That's Crux Management Service...building our business through lies and bad grammar. That's Crux Management Service."
Posted on October 02, 2008 at 09:05 PMOctober 01, 2008
Riding the Coattails of Credibility
The expression "riding someone's coattails" is an idiom in American English that means using your connections with someone successful to gain success for yourself. The picture we're supposed to imagine is an influential person entering an exclusive venue in white tie and tails—with someone less deserving being dragged into the exclusive venue by literally standing on the tails of the influential person's coat. I can see the 1930s cartoon scene in my mind already.
The modern-day equivalent is called slipstreaming.
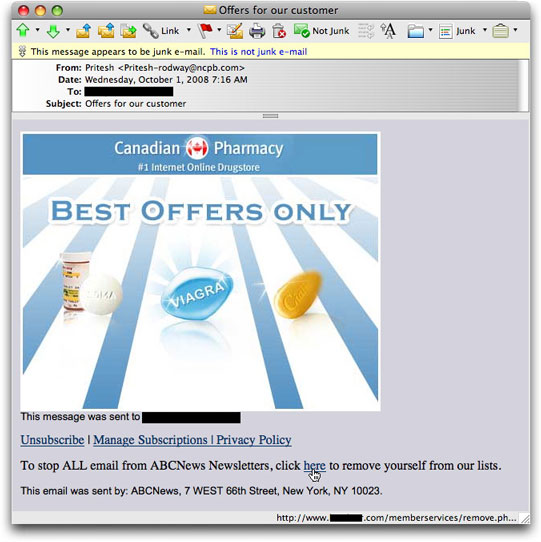
Whatever you call it, I saw a medz spammer doing it today. The following arrived at one of my spamtrap addresses:
Although the ad supposedly promotes a place called Canadian Pharmacy (how many hundreds of these—#1 or otherwise—are there?), note that the message claims to have been sent by way of ABCNews Newsletters, complete with CAN-SPAM-compliant mailing address and opt-out link. But ABC News had absolutely nothing to do with this mailing. All links, from the clickable image to the Privacy Policy, point to a newly minted domain whose registration lists a Russian owner (not likely accurate). The web site is hosted in Panama.
As long as the spammer is lying about being a Canadian pharmacy, he might as well go the full distance and lie about the offer being sent from a legitimate news organization, as if ABC News endorses the company. In the meantime, a lot of recipients will think ABC News is a spammer, as ABC News unwillingly rides the spammer's coattails to contempt.
Posted on October 01, 2008 at 08:14 AM