| Home | The Book | Training | Events | Tools | Stats |
February 28, 2006
A Spammer Makes My Case
I rant regularly about how the spam economy (the "spamonomy") keeps spammers going as long as spam recipients keep contributing to it—knowingly and un-. In a Washington Post/PC World spam article interview, an anonymous spammer confirms my belief:
Q:Will spam ever go away?A:Spam will never go away. If nobody was really interested in spam and people never bought anything that was advertised to them, spam would go away. That's simply not the case.
There you have it from the horse's, um, mouth. It'll probably be my dying breath "rosebud" sentiment: ZERO RESPONSE.
Posted on February 28, 2006 at 12:39 PMFebruary 26, 2006
Diplomas for Dollars
It's no secret that a lot of people—including some in very high places—have, let's say, embellished their resumes to help them get ahead in their careers. Almost like clockwork, some executive or political mucky-muck is exposed for overstating his or her (although they seem mostly to be his) educational background. The CEO of Radio Shack was a recent victim of his own puffery.
Phony college degrees have provided an industry unto itself in the spam world. Some spam messages try to be coy about it. But not one that arrived today:
Subject: get the better job - buy a diploma today
And then the pitch:
WHAT A GREAT IDEA! We provide a concept that will allow anyone with sufficient life experience to obtain a fully verifiable university diploma.Bachelor, Master or even a Doctorate.
Think of it, within a month you too could be a college graduate.
The only "it" I can think of is that you'd have to be a complete idiot to try to get away with a purchased diploma these days, especially if you intend to work at something other than a McJob.
When I was a kid, the teachers threatened you to behave by warning about black marks on your "permanent record." That, of course, was a complete crock.
But this is the 21st century, and the World Wide Web has become everyone's permanent record. Google, Yahoo, MSN, and others assist anyone and her uncle to peer into your permanent record (and that blog entry about how you got wasted the other night at that big party, and then drove home without getting caught by the cops, and then your roommates dressed you up in goofy clothes while you were passed out on the couch, and they posted the photo, and then...). When recruiters Google you and try to find a Web site for the source of your non-existent degree, they won't find any mention of Upper Weslyan University of Lower Slobovia, except perhaps at ftc.gov.
With nearly ubiquitous Internet access, search engines, the Wayback Machine, and free long distance telephone calls, those who want to look into your alleged background have enough tools at their fingertips to "out" you in short order.
Then you can add that to your resume.
Posted on February 26, 2006 at 12:26 PMFebruary 21, 2006
Trust But Verify
One of my credit cards offers online access to check current activity and such. I check that Web site almost daily to make sure there isn't anything suspicious going on.
(The card company, itself, is pretty good at detecting problems. A couple of years ago, my card was double-swiped at a San Francisco restaurant. In a few weeks, someone with a card made with my magnetic stripe data tried to buy gas in Florida. That's how a lot of card crooks test the validity of a stolen card or stripe—by attempting to make a small purchase where they don't have to hand the card to a clerk and can make a fast getaway. Anyway, the transaction didn't pass the card company's "smell" test, and they contacted me immediately before the transaction ever posted.)
When I went to log into the site today, I was surprised to see not only a completely new-looking site, but my bookmarked URL had been automatically redirected to a URL I didn't recognize. Here was this well-designed page, begging me to enter my login name and password.
The sound of bells you might have heard in the distance were the alarms going off inside my head.
A radical transformation such as that in this day and age is incredibly suspicious. I don't recall receiving any notification about a change in Web access, nor do I remember seeing any advisories about this on the old site yesterday. There have been cases in which financial institution Domain Name Service data has been temporarily compromised, redirecting users to fraudulent copies of the good sites, so I was aware that this was a possibility.
Before proceeding one step further, I got on the phone to my credit card company. After following the right breadcrumb trail through their electronic phone system, I spoke with a customer service person for their Internet services. She informed me that they did, indeed, change over the Web site, URLs, and such. To make doubly sure that she was legit, I was satisfied that the information she provided to me about my account was something that only the card company would know.
I share this experience primarily to demonstrate how watchful we must all be, and offer an example of how to go about checking out your suspicions without exposing yourself to even more risks. You can't be too careful these days, but you can be too trusting.
Posted on February 21, 2006 at 12:03 PM
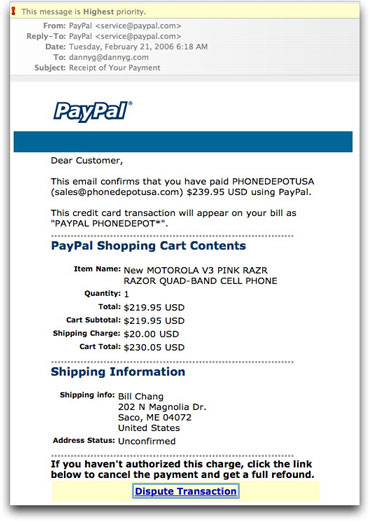
I saw another installment of an old trick. An email message arrives acting as a receipt indicating that you have supposedly paid for something (usually an electronic gizmo) fairly expensive. In the past I've seen messages like this for $800 digital cameras and such. Today's message is for a $230 cell phone. The basic idea is to get the recipient so mad ("I DIDN'T BUY THAT THING!") that he or she immediately clicks on the link to get to the bottom of the snafu.
I've seen links in these messages lead to Web pages whose sole purpose is to install malware silently into the recipient's PC. The one I got today has a link to a phishing type of Web page with a form asking for everything but your shoe size.
The email message is very convincing-looking:
There is one telltale sign that the message didn't source from PayPal in that it begins "Dear Customer." Real PayPal receipts address the customer by the full registered name. Of course even this information is fairly easily obtained from harvested email addresses that include your plain-language name along with address.
The only way you can tell that it is definitely bogus is by checking the email message's header (as I describe in Spam Wars). This message clearly did not begin its life at a PayPal email server. If there is any doubt at this point, however, a smart PayPal user would log into PayPal (not via any link in the message, but by either typing the full https:// address or using a previously saved bookmark to the real site) and check to see if PayPal showed any record of this transaction. You'd find that this transaction does not exist, and you are therefore not on the hook for $230.05.
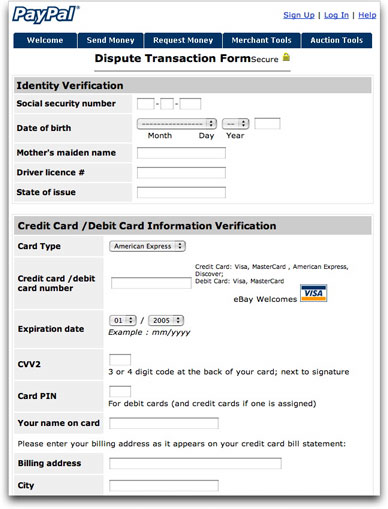
Failing good sense, a click of the "Dispute Transaction" link—a very hazardous thing to do in any case—leads to a Web page that also looks very convincing as a PayPal page:
There is enough personal information in this form for a chimp to impersonate you and give you a year or more of identity theft hell. The page also claims to be secure ("Lookie! We show a little padlock on the page!"), but the browser does not indicate a secure connection (and the URL is to a plain http protocol, not https one). The URL, by the way, is one of those numeric IP addresses. Like so many other phishing sites these days, the page was placed inside someone else's Web server. I guess you could call it a serverjacking.
Remember advice from the book: The more a message tries to provoke you to action (especially regarding financial stuff), the more likely it is a phony, even if, on the surface, it looks legit.
UPDATE: I just noticed that the arithmetic is incorrect in the "receipt." One should assume that by now, PayPal's computers know how to add. Phishers, on the other hand,....
Posted on February 21, 2006 at 09:24 AMFebruary 20, 2006
No Audit Trail = No Response
I received another one of those spam messages that insists that I had responded to something else, thus giving my consent to be mailed.
As revealed in the source code view of the message, the subject matter is travel (one of my least favorite subjects). Here is the spammer's assertion:
Danny Goodman you responded on Apr 9 2004 12:18 with dannyg@dannyg.com.
The spammer is from California (or so his CAN-SPAM mailing address indicates), so I'll take the 12:18 time to be California time, and PM at that.
Nowhere in this assertion is an indication where I supposedly responded. Looking up the spamvertised domain flaunted throughout the message reveals that its record is not yet in the whois database, meaning that the domain was likely created within the past 24 hours. It is therefore unlikely that I "responded" to a Web site that didn't exist nearly two years ago. And since he won't tell me where I responded, I can only assume this information is false.
For the fun of it, I also checked my calendar to see if I was doing anything special on that day. It turns out that I was at a meeting with one of my clients from 10:00am to 3:30pm, plus a fair amount of driving time tacked onto each end. There was certainly no recreational Web surfing going on during that time. I doubt that I even had Internet access during that meeting.
Thus, this spammer is either making up this supposed response, or he bought my email address from a source bearing equally phony opt-in credentials. Without an audit trail—or a trail he's willing to reveal—such assertions are completely worthless. They also tell me that this guy is another spammer liar (Rules #1 and #2) who won't get my address verified by me unsubscribing from this list.
Posted on February 20, 2006 at 10:56 AMFebruary 17, 2006
Stifling Curiosity
Ask most everyday spam-besieged email users about the problem, and they'll likely tell you that they want "someone else" to fix it. That could be their Internet provider, their email client program maker, or some vague geeky entities out in the ether. In other words, they want others to do all the work to keep spam at bay, so that the users don't have to deal with it.
The irony is that if email users did less than they do with regard to spam, phishes, malware mailings, and the like, we'd be in better shape than we are.
My contention is that the spam economy is what keeps spamming (and everything related to it) alive and well. The spam economy (or, as I call it, the "spamonomy") is driven by the money and activities of recipients of such missives. Obviously, those who buy from spammers fuel one part of the spamonomy. But, as I expound at length in Spam Wars, seemingly innocent activity, such as opening messages that send Web beacons and clicking on spamvertiser links, also feeds the spam economy, even if you don't buy from spammers. Your verified-active email address is currency among spammers. Clicking a link that hits a Web site can be an income source for the spammer. Filling out a form with your demographic information in a phony survey, a purported sweepstakes entry, or a mortgage application is a huge income source for the spammer when that information gets sold to others.
Think of it this way: Any response you make to an unsolicited bulk email message contributes to the spamonomy.
Even if you believe you're onto spammers' tricks, it can be difficult to resist the curiosity that they play on. They supply just enough information in a message to get you to click on a link to lure you into your contribution to the spamonomy. Case in point: A message whose From: and Subject: lines read:
From: "Schmidt Ora"
Subject: Danny Goodman : Approval #18783-05
Then the message:
Hello Danny Goodman,
After a review of all your data, we are pleased to notify you of
your acceptance.Secure site: http://[removed].com/3/?k=clmk2k5
Please submit your information on our webpage above
Waiting to hear from you,
Kinsella Nettie
Those who have been around the block a few times recognize this as a mortgage spam, but not every recipient would. (Not having visited the URL, I'm making a supposition.) But I'd wager that lots and lots of recipients click the link to find out what it's about. Ka-Ching.
Or how about the one that arrived earlier this week? In the list of waiting mail, it looks like this:
From: mail@best-postcard.com
Subject: You have received a postcard
Just opening this message in an email program (or Web browser) that has JavaScript enabled triggers a series of scripts that load hidden pages from at least three different servers (one in Russia, another in China), all using various obfuscation tricks to hide their true activities from non-techy eyes. You don't even have to click anything—just opening the message puts you and your computer in serious jeopardy. If your computer is hijacked, it becomes part of a bot-net, and your PC's processing cycles and broadband connection are leased out to spammers and virus writers around the world; all email addresses stored in various files throughout your computer are harvested for spammers to use; your financial logins and passwords may be snarfed from right under your fingertips. Your commission: $0.00. Less, actually, once you determine you've been Trojaned, and you have to get your machine cleaned.
It's a fact: It's hard to do less with spam/virm than you're already doing. Social engineering tricks peppering your inbox and instant messaging windows lure smart folks into doing things they know aren't good for them, yet plenty of recipients go right ahead and click away. Clamping down your curiosity about what's behind Door Number 2 is extremely difficult.
Until sufficient numbers of us adapt a healthy sense of suspicion about every piece of email or instant message we don't immediately recognize, we're doomed to keep feeding the spamonomy forever. Despite the help they've provided so far, all the filters and lawsuits in the world won't be enough. Enough bad stuff dribbles through—and enough recipients open, read, click on, and buy from these messages—to keep the spam economy flowing. The costs of sending the garbage is so low that even a teeny-tiny response is enough to make the effort pay. That's why the world's email users have to work extra hard to do less.
Learn how to open suspicious email safely, without exposing yourself to danger (like the postcard one described above). Become invisible to senders you don't want to hear from. When they can no longer make enough money to keep their efforts going, they'll turn their attentions elsewhere. Anywhere but our inboxes.
Posted on February 17, 2006 at 04:43 PMFebruary 15, 2006
Watch Out Chase Customers
A very convincing Chase Bank phishing message and associated Web site will certainly trick lots of customers.
The come-on is a "$20 Chase Gift Certificate" for filling out a survey form. The URL of the phony Web site has the words "chase" and "survey" as components, and the message proudly displays this URL because it is, I guess, believable. The Web site page is very well done, and asks for your account username and password, as well as a Chase card number, PIN, and expiration date. Although the page is not served up as a secure page, I don't believe a lot of victims will notice the lack of the lock.
Spam Wars readers would know, however, how to check a few things before getting into trouble. First, the header of the phishing email message (at least the one I received) shows it to have been sent from an @home account in the Netherlands. Second, a lookup of the "chase" domain shows it to be registered to someone in France (certainly bogus data), and created only yesterday (14Feb2006).
The craftsmanship of this one is deadly for the unwary.
UPDATE: Received another copy sourced from blueyonder.co.uk, which indicates that these phishing messages—like most of them—are being relayed through Trojaned PCs. I also found the Spanish hosting service for the Web site (it wasn't clear earlier) and made my direct report.
Posted on February 15, 2006 at 10:50 AMFebruary 14, 2006
419er Gets 376
According to several accounts, a Nigerian court found Harrison Odiawa guilty of violating the Advance Fee Fraud Act. The court found that he had conned a U.S. businessman out of nearly $2,000,000 (!) in a bogus government contract scheme. Evidence at trial included the typical phony documents that 419ers are so fond of creating.
For his efforts, Mr. Odiawa was sentenced to 376 years in prison and ordered to repay $1.6 million to the victim. Unfortunately, the 376 years are spread across so many charges, and that the sentences are to be concurrent, he'll be out in 12 years. I just hope the prison doesn't offer Internet access to inmates.
It is also reported that the victim had previously been sentenced to two-and-a-half years in a U.S. gray-bar hotel for money laundering and wire fraud charges. One report says he was convicted of conspiracy to defraud the Nigerian government out of $20 million, even though the contract was bogus.
If more potential victims understood that they might be strung up for participating in these frauds, they might think twice before doing the math to calculate their take of the (nonexistent) mystery money.
Greed on both ends of the deal. I don't know if everyone got what he deserved in this case, but it's a start.
Posted on February 14, 2006 at 09:16 AMFebruary 09, 2006
Rule #3 Lives!
Spam Wars readers know that Rule #3 of spam is "Spammers are stupid." An advance-fee (419) spammer/scammer sent one of the usual appeals to me via my contact form. The message was from the ever-present Mariam Abacha (not really, but hers is a popular name among Nigerian 419 scammers)—the real Mrs. Abacha's late husband was a dicator...blah...blah...blah.
Submitting spam messages via forms of this type—rather than by traditional email—is nothing new. Bloggers who allow open comments have been fighting spam form submissions for a long time.
Whenever a message arrives here via the form, I like to think that a human actually filled out the form, but in the case of something like this, I know better. I can't imagine that anyone in his or her right mind would bother to take the time to send a 419 message to a Web site that ridicules these scams left and right. And lest one think that this message was sent maliciously, I'm reminded of Hanlon's Razor, which says:
Never attribute to malice that which can be adequately explained by stupidity.
The sender was definitely from Nigeria (as logged by the form processing software), but it was probably some guy sitting in an Internet cafe.
There was, however, something striking in the message. Beyond the fact that a good portion of the message lacked any kind of logic or even a good indication of what my cut of the $10 million transfer would be, there was this statement in the list of "conditions":
4. You will be ready to pay US$800Dollars only for stamp duties fee.
What's interesting to me about this is that it's the first time I recall seeing a 419 scam message that openly admits that the scammee will have to fork over some up-front dough. Perhaps this note helps weed out the respondents who complain bitterly at first about having to front any money. The ones who respond to this new appeal are self-selected to be immediately open to sending funds to Western Union offices in Nigeria. I can tell you, however, that this won't be the only fee that will need to be paid. I've seen real examples of how these scams can extend for months while the scammer comes up with all kinds of excuses (always some bank's fault) to extract some more hundreds and thousands of dollars, with no end in sight—except for the end of funds available to the victim.
I've already said too much, and have put my windfall into jeopardy because I just violated one of the "conditions:"
2. This deal must be kept secret forever, and all correspondence will be strictly by email / telephone, for security purposes.
Oh, yes. Unencrypted email sent to your yahoo.co.uk address is sooo secure. And telephone? Dear "Mrs. Abacha," don't the newspapers sitting around the Internet cafe have stories about NSA eavesdropping here in the States?
I'd like to think that resorting to sending a message in this fashion to a single recipient is a sign that 419 scammers are not getting the response from email like they used to. Thus, in my dreams, scammers are having to look to other, less efficient ways to hunt down potential victims. The form processing software is something that the hosting service for this site provides to all customers if they want to use it. Even so, I believe the sender would have had to cull the form submission URL from the Contact page's HTML source code (the URL references a template that I named, so it's not some default value), meaning that it's harder to look for this type of URL than it is to harvest email addresses from Web sites. Maybe someone is selling a list of those URLs to spammers. Not a high-value proposition, IMO, because it's a lot of trouble to reach a single individual who is probably more experienced and scam-savvy than the typical 419 victim.
If these clowns want to waste their time, then I don't mind taking a one now and then for the team. The time they spend working on my fruitless 419 appeal is time they can't spend finding a gullible victim.
Posted on February 09, 2006 at 04:45 PMFebruary 01, 2006
Another E-Marketer Liar
Perhaps there are legitimate e-marketing firms out there, but every time I see another example of one slick emarketing site lying through its Privacy Policy, it makes me want to puke.
This afternoon I've been pelted with spam originating from an e-marketer that spews CAN-SPAM compliant email. That, of course, doesn't make it not spam in the eye of the recipient, but it keeps them out of the FTC's crosshairs on the face of it.
Well, maybe not.
There is deception going on here, but you have to study the firm's Privacy Policy, and then be the "lucky" recipient of email demonstrating that they don't seem to give a rat's ass about the policy. Here's the relevant portion:
Through the Site, Company operates the service [trade name removed], by which it delivers advertisements and offers by email to its “list members,” that is, people who sign up for the Service through our opt-in process via our Site or through one of our many partners’ sites. List members choose the topical categories they are interested in and sign up for those particular lists. They will then receive email messages only from those lists and only for so long as they wish to continue to receive such messages. Before any mailing goes out, our staff personally screens each marketer’s message to make sure that is relevant to the list’s topic.
I can tell you that I have never signed up to any list offered by the company. And, as Spam Wars readers know, the "partners" garbage usually means that they bought lists that have no audit trail, and could have even been harvested.
So, the pitch to this outfit's potential clients is that an email marketing message would be sent to me only if I have chosen a "topical category" in which I'm interested. OK. Here are some of the offers that came in today:
FROM: "SUPER BOWL SURVEY"
SUBJECT: SUPER BOWL XL SURVEY - COMPLIMENTARY XBOX 360 ...
FROM: "AIRLINE PROMOTION"
SUBJECT: TRAVEL AT NO COST ON THE AIRLINE OF YOUR CHOICE...
FROM: "NATIONWIDE FINANCING"
SUBJECT: 60 SECOND AUTO LOAN APP. ALL CREDIT TYPES ACCEPTED.
I have to tell you how glad I am that I only view the source code of these messages. Each message consists of two images, each surrounded by a link. One link/image pair is for their disclaimer/opt-out statement to meet CAN-SPAM requirements. But the other image's URL is coded with all kinds of stuff: certainly something identifying the promotion, and perhaps an ID equating to my email address in their database. Just opening the message with images turned on would have tripped their hit counter (indicating that the From/Subject lines were good enough to get you to open the message) and perhaps validated the email address as being "live." I haven't seen them, but I'd imagine that the images are drop-dead gorgeous, and will get many recipients to click through. Aarrgh!
Back to the message subjects. How any marketer in his/her right mind could classify me as an ideal target for any of these promotions is beyond a mystery:
- I stopped watching pro football before Steve Young stopped playing football.
- Arthritis and tedonitis have kept me away from video games since the days of ColecoVision.
- I have taken exactly two round-trip (and no one-way) airline voyages since the beginning of the year 2001.
- I get a new car approximately every 15 years, and I'm currently leasing the one I drive now until I buy it at the end of the lease.
This outfit, on behalf of its paying clients, fired three torpedos my way. As they say in the game Battleship: Miss! Miss! Miss!
And so, e-marketers continue to make splashy sites to sell their services to unsuspecting (or "nudge-nudge-wink-wink") companies with products/services to sell to consumers. They produce a professional-looking presentation, and an eloquent Privacy Policy geared to assure prospective clients that they're the Good Guys.
But they lie.
Posted on February 01, 2006 at 03:23 PM