| Home | The Book | Training | Events | Tools | Stats |
November 23, 2011
It's Wednesday
So that means yet another installment of "The Lure," a nearly daily attempt to trick email recipients into clicking links that lead to malware installers. Yesterday's story can be found here.
Today is the sad story of, well, I'll let the crook weave the tale:
From: [RandomName]@[YourDomain]
Subject: Help! I'm in trouble!
I was at a party, got drunk, couldn't drive the car, somebody gave me a lift on my car, and crossed on the red light many times, I've just got the pictures, maybe you know him?
Here is the photoI need to find him urgently!
Thank you
[RandomName]
As with other recent versions, this one's links go to HTML pages on hijacked web sites; the HTML page has an iframe element that loads the Russia-based main.php page containing obfuscated JavaScript.
What hair-raising tale will come tomorrow?
Posted on November 23, 2011 at 09:56 AMNovember 22, 2011
main.php Malware Lure du Jour
Attempting yet another adrenalin-rushing trick to get you to click a link:
Subject: Need your help!
Hello! Look, I've received an unfamiliar bill, have you ordered anything?
Here is the billPlease reply as soon as possible, because the amount is large and they demand the payment urgently.
Looking forward to your answer
Fingerprint: 41723bdf-658c9e0a
As with the most recent rash of these, the link is to an HTML page inserted into a hijacked web site. That page loads an iframe whose obfuscated JavaScript content comes from a main.php program on a Russian site. Follow my trail of woe about this scheme.
November 21, 2011
Phony iTunes Gift Certificate Notice
Another variation on a well-worn campaign to trick recipients into opening an attached malware loader:
From: iTunes Store
Subject: Thank you for buying iTunes Gift Certificate
Dear customer,
You have received an Itunes Gift Certificate in the amount of $50
You can find your certificate code in attachment below.Then you need to open iTunes. Once you verify your account, $50 will be credited to your account.
So you can start buying video, music, games right away.iTunes Store.
[File: Gift_Certificate_iT1642.zip]
Resist! Resist! Resist!
Posted on November 21, 2011 at 11:14 PM
Can't these wannabe criminals read instructions?
The idiot du jour sent out a blast of Bank of America phishing messages in batches of 1200. How do I know it was exactly 1200? Because this clown included all 1200 email addresses in the highly visible To: field. I have no way of knowing how many of those addresses are valid nor how many servers of those addresses will let this phishing message pass into their inboxes, but it's bound to be some. And if any of those machines are compromised with malware, all 1200 addresses will be snarfed up and fed back into spammers' databases. Whoopee.
I did get a chuckle, however, when the jerk realized that he made a booboo and resent the message with the addresses set to BCC:. It means that he either was able to send only half as many messages as he had planned, or paid twice as much for the botnet resources. Anything that cuts into a crook's profit is OK with me.
Incidentally, the email message — festooned as it was with real Bank of America web site image files — included a section that began thusly:
This email includes a Security Checkpoint. The information in this section lets you know this is an authentic communication from Bank of America.
This little phrase has been circulating in BofA phishing messages since about June 2010. It must be part of a phishing kit sold by über-crooks. As I have said many times, the more an unsolicited email message claims to be legitimate or not spam, the more it is lying. The inclusion of some words in an email messages has no bearing whatsoever on the message's authenticity.
I really, really, really am the Tooth Fairy!
See?
Posted on November 21, 2011 at 11:05 AMNovember 17, 2011
Adobe License Malware Lure
This is getting pretty tiresome (here and here) but the spammed email content is different enough to note.
Here's a sample message (order number in the Subject: field varies from message to message):
From: [variable random name] <support@adobe.com>
Subject: Order N41066
Good day,
You can download your Adobe CS4 License here -
We encourage you to explore its new and enhanced capabilities with these helpful tips, tutorials, and eSeminars.
Thank you for buying Adobe InDesign CS4 software.
Adobe Systems Incorporated
It's not clear why they're promoting an older generation of Adobe CS, since there is no Adobe product at the end of this rainbow anyway. Perhaps it's just a distraction to make the recipient think about something other than the possibility that the link is potentially extremely dangerous.
As with recent mailings with different content designed to get you to click without thinking, the current links go to HTML pages of hijacked legitimate web sites. The pages contain an iframe element that loads a main.php program from a Russian web site. That program serves up an obfuscated JavaScript script that can start your PC down the road to surrender. I've seen only a handful of Russian (.ru) domains in these iframe URLs over the past weeks, so they must be hosted on bulletproof services.
I'm officially bored with the whole thing but will continue to post future emails that employ different social engineering tactics.
Posted on November 17, 2011 at 10:15 AMNovember 09, 2011
Wire Transfer Malware Lure
The same folks who brought you the main.php malware lure (and many others before) are today using a phony wire money transfer notice as a way to induce you to click on their malware-laden links. Here's a sample:
From: Frederick MCNEILL <support@federalreserve.gov>
Subject: Wire Transfer Confirmation (FED 4478LH086)
Welcome,
Your Account # Business Account ***
Wire Debit Amount: $38,836.61
Transfer Report: ViewMake sure that everything is as you requested. The wire transfer will be processed within 2 hours.
Frederick MCNEILL,
Federal Reserve Wire Network
The links are to hijacked web sites, but the fraudulently-inserted pages are named funct.html and others. Those pages are blank except for an iframe that loads...ta-da!...a main.php page from a recently-minted Russian domain. It's the same type of script-kiddy obfuscated JavaScript as reported here recently.
Silly little games.

Another day, another Bank of America phishing attempt. This one tries to work double-duty by phishing not only for your BofA login credentials, but also identity data for every credit card you own.
The email message is pretty standard phishing stuff (although the Subject: line and message body don't really connect):
From: Bank of America <support@bankofamerica.com>
Subject: Bank of America SurveyQJRPRKRVWE
As part of our security measures, we regularly screen activity in the system.
We recently contacted you after noticing an issue on your account.
We requested information from you for the following reason:
We have observed activity in this account that is unusual or potentially high risk.Please download the form attached to this email and open it in a web browser.
Once opened, you will be provided with steps to restore your account access.
We appreciate your understanding as we work to ensure account safety.Sincerely,
Bank of America Account Review Department[file: SurveyQJRPRKRVWE.html]
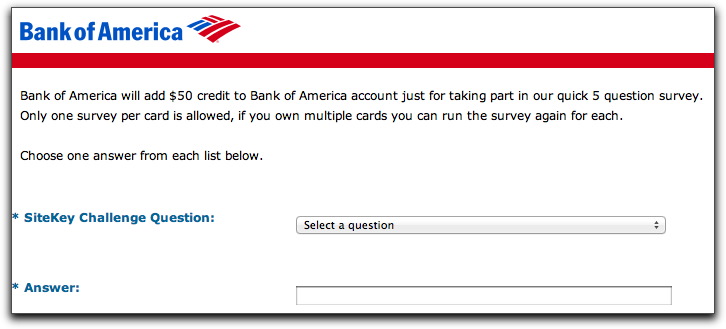
The file is, indeed, an HTML file, base64 encoded. That allowed me easy conversion offline to view the source code and see if it was safe to render in a browser (making sure it doesn't try to download any malware crap automatically). With the help of images downloaded directly from bankofamerica.com, the page starts out with the survey come-on:
Note that it encourages you to take the survey as many times as you have credit cards because supposedly you'll get fifty bucks in each card. Yeah, well....
The "survey" consists of six (not five) challenge question selections. I don't believe these questions/answers have anything to do with the phishing attempt.
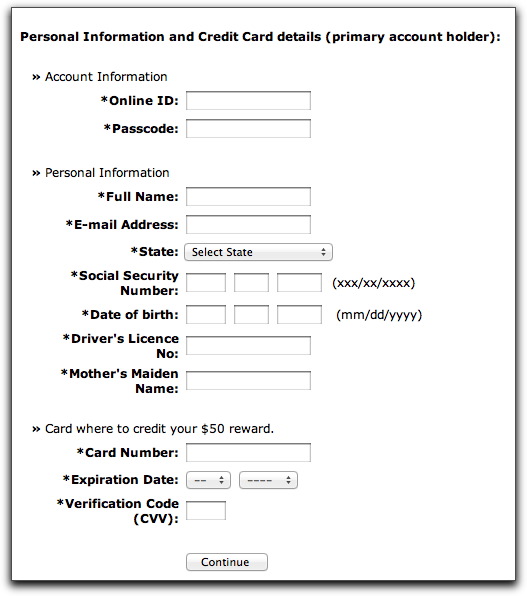
No, the real gold for this criminal comes in the latter portion of the page:
The most valuable info on the form are the BofA login credentials. With those two fields, the crook can clean you out. Credit card and other identity info are just sprinkles on the doughnut. If you were to fill out the forms (the HTML includes JavaScript that forces you to enter valid-looking info into the fields) and click the Continue button, the data goes to a PHP program running on a web server that has been hijacked from an established design firm in Russia.
And poof goes your bank account and identity.
Posted on November 09, 2011 at 10:39 AMNovember 07, 2011
Phony Invoice Malware Delivery
Don't fall for the email message and attachment claiming to be an invoice from companies you don't work with. I saw a message today that wanted me to believe I had been invoiced by Kraft Foods:
From: Quincy MIMS Kraft Foods Corp.
Subject: Re: Corp. invoice from Kraft Foods Corp.
Hi
Attached the intercompany invoice for the period July 2011 til Aug. 2011.
Thanks a lot for supporting this process
Quincy MIMS
Kraft Foods Corp.[file: Invoice_10_26_J84240.zip]
This is the same style of campaign that has been clogging the tubes for months now — including the ones that say they were generated from an internet-connected printer. I suspect the template for this message replaces things like the company name, person's name (which is capitalized in a form common in some European countries and elsewhere...but not in North America), and attached file name with strings from mail merge-type lists.
Of course, even if I did business with Kraft Foods and was in the Accounts Receivable Department of my own firm, I'd be just as wary of this message and its attachment until I could be satisfied (through study of the email headers and other contextual clues) that this was a legitimate email. It helps, too, that my local antivirus software recognized the attachment for the malware that it was.
Posted on November 07, 2011 at 07:41 AMNovember 03, 2011
Fake Airline Ticket
Today I saw the umpteenth variation of a long-running campaign designed to trick recipients into opening a dangerous attached file. This one tries to get your adrenalin flowing by claiming to be an airline ticket ready for you to use to JFK in New York:
From: "American Airlines" <report-no.754@aa.com>
Subject: Order has been completed
Hello,
FLIGHT NUMBER 983
ELECTRONIC 566673600
DATE & TIME / NOVEMBER 09, 2011, 11:53 PM
ARRIVING / NEW YORK JFK
TOTAL PRICE / 214.34 USDYour bought ticket is attached to the letter as a scan document.
To use your ticket you should print it.Thank you for using our airline company services.
American Airlines.[attached file: AA_Ticket_#3713.zip]
I assume that various numbers in the message will vary from message to message.
Logic dictates that if an airline were to send you this kind of information, it would mention the departure city. Perhaps this is part of the lure to malware file: gotta click it to find out if the ticket is from your nearest airport, right?
Additionally, a quick check with the American Airlines web site reveals that the flight number in my message is for a trip that goes from Minneapolis to Miami to Guatemala City. You'd have a tough time getting off at JFK in the hopes of snagging a "Book of Mormon" ticket.
Opening that file is a one-way ticket to Hell (not the one in Michigan).
Posted on November 03, 2011 at 06:38 PM