| Home | The Book | Training | Events | Tools | Stats |
June 30, 2006
Validation
In Spam Wars, I mention a high-powered friend of mine in the consulting business who has gathered over 100,000 email address during his years of schmoozing (and believe me, this guy is a First Class Schmoozer). Most of these addresses weren't gathered through any opt-in mechanism, but from a variety of sources, including the business-card-left-in-a-fishbowl technique at trade shows.
Here's what I say in the book when he explored trading lists with another consultant:
My friend fears that if he attempts to requalify his list by asking everyone to go through a modern confirmed opt-in process that he’d lose a large percentage of names. Would that weaken his reach or offering? My own sense is that, due to increased personal, technological, and legal sensitivity to spam, he would be better off with a smaller, confirmed opt-in list.
Now comes word that the Leukemia and Lymphoma Society actually went through a complete requalification of its 33,636 newsletter email addresses to help reduce the headache of getting so many spam reports and undelivered messages. While the resulting list count dropped to an alarmingly low 4,510 addresses, some magical things happened as a result:
- Spam reports dropped to zero.
- The average open rate more than doubled.
- The clickthrough rate nearly quadrupled.
- The total clicks per campaign remained virtually the same.
A responsible emailer—holy cow!
Posted on June 30, 2006 at 11:21 AM
At times I get so many phishing messages that I don't bother reading their contents. I simply look through a message's source code for the destination URL, verify it's still active, trace the source of the domain/hosting outfit/IP block owner, report it, and delete the message. I periodically through the day check whether the reported pages have been taken down to help me know which ISPs respond quickly and which don't. (I have to say that Yahoo! domain registration and hosting folks have really stepped up their response lately. Bravo!)
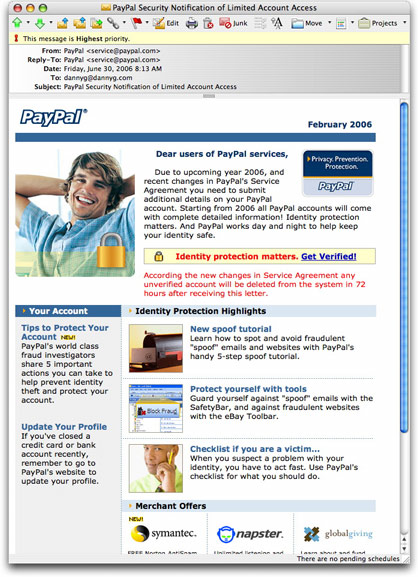
But something caught my eye as I scoured a PayPal phishing message today that caused me to look more closely at the content of the message. Here's a partial screenshot:
I won't even get into the goofy bit about the message supposedly being dated February 2006 and talking about the "upcoming year 2006" and the message being sent on 30 June 2006—it's just too easy a target.
No, what makes this message so insidious is that it will probably convince a recipient that it's legit because it talks so much about how to spot spoofs, how to protect your account, and so on. I could see many a recipient thinking, "A crook wouldn't put so much in a message about detecting crooks." And they'd be dead wrong.
Unfortunately, the items that should be links, like the "New spoof tutorial" heading, are not. But even if they were links to the real PayPal spoof tutorial, I don't think it would matter. All that the recipient would focus on are the bits in red, claiming that unless updated information is provided, the account will be deleted in 72 hours.
The only clickable link in the message (the "Get Verified" link) takes the recipient to a PayPal login lookalike page that has been installed on a hijacked web site in Switzerland. (Unfortunately, it's the site of a Swiss web design firm—one that apparently knows about graphics, but not security.)
From comments I see all around the Internet, I would guess that a high 90-percentile of PayPal (and eBay) users have never read the spoof information that financial sites provide for their customers. The remaining have read it because they were victimized by phishing or some other kind of fraud. The 90-percentile group doesn't want to hear about it.
It reminds me of the incident about six months ago where the Attorney General of Colorado arranged to make a personal appearance at a senior center to show attendees how to protect themselves from the types of consumer and investor fraud perpetrated specifically on senior citizens. I'm not talking about some flunky from his office—the real Attorney General. The grand total attendance at this event: one journalist. But I'll bet that when senior citizens get taken, they just about ram down the AG's door to complain that they're not being protected.
On the subject of online safety, you can't even lead a horse to water until it's dying of dehydration.
Posted on June 30, 2006 at 10:29 AMJune 26, 2006
419er "Major Negron" Has Apparently Moved On
A few weeks ago, I supplied details about a 419 scam claiming to come from a "Major James Negron" of the 1st Armored Division stationed in Iraq.
The gang is at it again, but this time the email message from "j negron" doesn't talk about Iraq or the U.S. Army or hidden millions. The message's subject is very much like the Army ones:
Subject: AN INSIGHT
But this time, the 419 pitch is different:
Dear friend,
I am an Auditor who is willing to place in investment opportunities available..
I have certain amount of money i wish to invest in private and start-up companies with potentials for rapid growth in short-times. I am intrested inplacing part of the fund in your company (if any), If by-laws allows for foreign investment. If on the other hand you do not have a company,
I will be happy to listen to any business propositions you may have.
I will like you to contact me through this e-mail [removed]@virgilio.it .As well as sending me your company profile (if any)or other necessary informations.
At the meantime, I will appreciate it if you can provide me a few details of yourself.(full name, age ,address and occupations e.t.c) Please acknowledge the receipt of this mail.
Thanks and God bless.
Your Faithfully,
j negron .
This 419 approach is anything but new, but the results are the same for anyone who responds: Promises of money to be sent to your bank account, except that there are some screw ups along the way that require your advance payment of fees, taxes, and other banking or transfer charges—thousands of dollars out of your pocket that you'll never see again.
The "God bless" in the signature is as cynical as posing to be a U.S. soldier stationed in Iraq. As the U.S. economy tanked following 9/11, and non-profit organizations were having a hard time raising donations, the 419 brigade used tactics similar to the one above, promising to donate money to charities, often tugging on the religious heart strings of potential victims. It was despicable behavior, but these psychological thugs have no conscience.
I wonder where "j negron" will appear next.
Posted on June 26, 2006 at 11:08 AMJune 25, 2006
Mortgage Spammers Getting More Desperate
Americans (and probably Canadians by osmosis) have a fixation with their credit histories. Television ads bombard us with making sure we know, and know how to improve, our FICO scores (a shorthand numerical credit ranking system). The higher the score, the easier it is to get credit on better terms (i.e., lower interest rates for things like homes and cars). There are now even laws that require the major credit reporting agencies to provide (upon request) a complete credit history record each year; the agencies also offer paid services for more frequent reports and "credit watch" services that alert you if someone inquires about your credit worthiness.
This is certainly no secret, and it's not lost on mortgage spammer—or just one mortgage spammer in this case. I believe it's the same root spammer who floods my inbox with mortgage offerings daily. There is a sameness to the messages that gets pretty boring after awhile, even though the domains of the links change frequently.
Here are the Subject: lines of two I saw today:
Subject: Danny Goodman Bad TransUnion Report
Subject: Bad info on your Equifax Credit File Danny Goodman
On the surface and to an untrained eye, these titles might seem to indicate that the sender had made credit inquiries and found something snarky in the reports. Of course if you hadn't authorized anyone to make such an inquiry, you'll rush to open the message to find out what it's about and who is looking into your history.
That's what the spammer is counting on, even though the deceptive practice is highly illegal in the U.S.
Of course the payload includes no information whatsoever about your [fill-in-the-blank] agency report. Instead, it's run-of-the-mill mortgage lead spam junk, making the spammer sound like a mortgage broker, when, in fact, he simply gathers leads and gets paid handsomely by the real mortgage broker for each lead.
This guy really shouldn't send so many similar messages so close together. It leads one (me) to contrast and compare the messages for various clues. Forget the domain registrations—the details are obviously bunk (that is, unless FTC investigators with warrants get involved—hint, hint). But the messages are also obviously made up from a template that inserts words in an almost Mad Libs way. Here are today's pair:
How are you, Danny Goodman
Your Credi*t is NOT a issue. If you own Property and want funds to expend anyway you wish or plainly wish to reduce your installments;
These suggestions will only be available for the next 48 hours.
http://[removed].net
I will provide you a decision within 27 mins., 99% acception!
Regards,
Sheldon Brown
And:
Greetings, Danny Goodman
Your Cr-edit is NOT a issue. If you own Real Estate and want capital to utilize anyway you wish or just like to decrease your payments;
Our endeavors will only be useable within the next 48 hours.
http://[removed].net
Our Office will send you a answer in 20 mins., 99% approval!
Regards,
Colin Wayne
This is from the same campaign I wrote about earlier that had the busted mail merging software. Same garbage, newer domains (the ones in today's messages were registered yesterday).
I've forwarded these messages to the FTC refrigerator, as usual. But this time I've also sent them to the legal departments of TransUnion and Equifax, who may have trademark beefs with this clown.
With mortgage rates inching upward and applications inching downward, mortgage spammers may be getting more desperate to get people to open their messages. Screwing with peoples' heads about their credit reports is really getting up there in the Nasty Department. They're not leaving much room to escalate the attacks. I think the only more alarming Subject: line deceptions remaining are kidnapping ransom notes and death threats.
UPDATE (23:24 PDT): "Everyone" knows that there are not two, but three major credit reporting agencies. Sure enough, the third got mentioned in a subsequent mortgage lead spam from the same guy. Here are the ones that have arrived during the rest of the day:
Subject: Negative Experian Report Danny Goodman
Subject: Danny Goodman Bad info on your Experian Credit File
Subject: Negative info on your TransUnion Credit File Danny Goodman
Subject: Negative Experian Report Danny Goodman
So much spam to forward to the FTC and the credit bureaus; so little time.
Posted on June 25, 2006 at 09:15 AMJune 18, 2006
Attention Foreign Spammers: Don't Use Babel Fish!
If you are mailing your trash to English-speaking recipients and you don't know English, then don't bother using the Babel Fish Translation web site to convert your Russian or Korean or Chinese into English. The more florid your original, the less intelligible the translation.
Here's a come-on that would make Sherlock Holmes scratch his head:
I just familiarity to let you know how well along I am with this product.
I have been mounting receiving tag people emails with vacation of tetimonials and requests for this product. It is gaining a great deal of for a second time and it is international.
I am shuffle you will have at insignificant same results and will send me a tale genuineness it.
I'm not about to follow the link to find out what they're selling, but "product" is Spamese for medz of one kind or another.
Maybe the spammer is English-speaking and wrote this lofty prose while on the medz he sells. If so, add this warning: "Side effects may include mental illness."
Posted on June 18, 2006 at 11:09 AMJune 16, 2006
Anonymous E-Card = PC Wipeout
This morning's inbox included a message purporting to come from an electronic greeting card company. Although the company appears to have been around for awhile, I won't mention its name because its site is an advertising nightmare: attempted popup windows, banners with jiggly and phony "Congratulations" windows urging you to claim your hourly prize, blah blah blah. It may be a legit company, but I can't stand to look at its home page.
Back to our story.
The email message begins:
A friend has sent you an ecard from [redacted].com.
To: Dear darling,
Message: i hope you like this card that i have made only for you
Send free ecards from [redacted].com with your choice of colors, words and music.
Your ecard will be available with us for the next 30 days. If you wish to keep the ecard longer, you may save it on your computer or take a print.
To view your ecard, choose from any of the following options:
I imagine that most people receiving this message would be thrilled to find out that a "secret admirer" is sending them an e-card. You couldn't stand in the way between their clicking finger and the mouse button.
And that's where everything starts to go wrong.
Clicking the supplied link with a PC takes you to a different site and immediately begins downloading a one megabyte file. But it ain't no greetin' card.
The file is an executable program (.exe extension). After safely downloading it in a non-Windows environment, I sent it through VirusTotal, which checks the file against 26 antivirus systems. This file wasn't identified as malware by any of the major antivirus programs (e.g., Symantec, McAfee, F-Prot, Sophos). Thus, if you had received this message and clicked on the link, even if you had the latest antivirus updates installed, the file would have downloaded without complaint.
I've submitted the file to the SANS Internet Storm Center for further analysis. If I hear anything back, I'll post an update here.
The bottom line, for the umpteenth time, is that clicking on links in any email message—especially a message that seems too good to be true—is like playing Russian Roulette with a live bullet in every chamber.
By the way, there were numerous additional clues in the source code of the message that this was really bad stuff. The most telling is that the actual link (not the one visible in the message, but the actual destination in the HTML tag that made the link) uses a form of URL that is increasingly used to disguise the destination. The format is known as a decimal URL. Unlike the types for which this site offers decoding tools, a decimal URL consists of a 10-digit number for the site address (the part immediately following the http:// part). For example: http://1109855782 (don't worry, it's the address of the Spam Wars site home page).
The decimal URL format is on the rise, from what I've seen. Each time I've seen it in use (again, always apparent in the message's source code, where the greatest deception and secrets lie) the destinations are used for nefarious purposes—phishing, malware installations, etc.
Interestingly, major Mac OS X browsers (Safari and Firefox tested so far) do not resolve decimal URLs. Chalk up another one for the guy on the righthand side of the screen in the current U.S. Mac TV ads. This means that Bad Guys can use decimal URLs in the kinds of messages like the one I received today to filter out those users whose machines are immune to their malware (Firefox on Windows does resolve decimal URLs). Only those who successfully follow the email message link are equipped to be infected by a zero-day infestation.
Natural selection at work perhaps.
UPDATE (19 June 2006, 08:00:00 PDT): Still nothing back from SANS yet on this (I submitted twice), but others are getting into action, as well. The site's hosting company is in denial (or their support people are as clueless as the one I chatted with earlier this week). In the meantime, "simplypeachy" has dug deeper into the file and finds some typical Trojan activity going on (e.g., setting up the PC to be controlled as a zombie via mIRC).
Posted on June 16, 2006 at 10:17 AMJune 15, 2006
Pump-And-Dump Techniques
Penny stock scams litter many an inbox. The recipient supposedly gets some inside information about a low-priced stock that is going to "explode" in a day or two because of news that will be announced on that day. The scammers, of course, wait for the suckers to bid up the price in anticipation, and then they quickly sell for a tidy profit ahead of those who caused demand for the stock. Thus the name: pump-and-dump. I have seen at least one study that traced performance of spammed penny stocks, and the typical pattern is an immediate increase in trading volume, during which the price may "surge" a few cents; after that, the stock goes into a steady decline.
Finding the sources of these messages is difficult. The return addresses are uniformly bogus, they're relayed through botnets, and there are no links to follow because the action to be taken by recipients is through their brokers or self-trading accounts. Yet the fact that the messages generally are not openly sponsored by any reputable person or organization doesn't stop the gullible from losing money in the process. Also, because the SEC did hunt down some of these guys once, the P&D spammers include disclaimers that will get them off the hook if they should be caught. Oddly (or perhaps not), there are apparently enough gamblers in the market to ignore the disclaimer warnings to keep the scam working.
P&D messages that have text in them are usually easy to filter because they include readily identifiable phrases and abbreviations. That has led the P&D scammers to embed their complete spiel in an image that accompanies the message. My seldom-used Comcast inbox seems to be a magnet for these types.
I wonder if some ISPs are now using character recognition on embedded images to filter out this junk because I just saw something today that shows the scammer jumping through extra hoops to avoid such a possibility. The typical P&D image has been divided into many pieces, and the HTML in the message assembles the attached pieces into a (mostly) readable end product. Here's what it looked like in my email reader (I've blurred the identifying stuff):
The little extra white spaces makes it look a bit like a ransom note, which would give me pause (but then I don't invest in individual stocks). I looked into the recent record of the stock being pumped in this message. It had hit a one-year low point yesterday, so that's a good time to pump it up. Unsurprisingly, trading volume today was more than 2.5 times above average. If you had owned this stock at yesterday's closing price ($0.22), you could have sold it for as much as $0.29 today, for a better than 30% return. But if you had tried to buy any today (there appears to have been some after-hours activity that drove the opening price to $0.26), you'd have lost by the end of today's trading.
If you'll excuse my high-finance terminology, I simply find a stock touted by an unnamed spammer to be too icky.
Posted on June 15, 2006 at 02:03 PM
Don't you just hate it when a spammer/scammer misconfigures his botnet so that only a tantalizing bit of the message comes through without the full payload? Call me crazy, but I like to see what scams these jerks are trying to pull off.
The message in question originated from a server in China (duh), but contains forged parts of the header to make it look as though it came from a U.K. company in the pneumatic tools industry (the domain has been registered since 1997, so it's not bloody likely that this company has anything to do with the message).
The part that got my initial attention was:
Subject: Danny Goodman Administrator has been fired
It's hard to tell what this is supposed to mean. Have I been fired? Did I fire my Administrator?
One of the nice things about being self-employed (for the last 25 years, thank you), is that I know everything about my operation. (The bad thing is that my boss is a slave driver and my employee is a lazy bum.)
In any case, in the context of my "organization," this subject makes no sense.
The body of the message is no more revealing:
{%BEGIN_SPLIT76%}
Danny Goodman, Our Company
That first bit is either a placeholder for a mail-merge type of insertion or other directive that the bot should be using to help compose the body. But then it gave up the ghost.
If this doofus fixes his problem, and I receive his result, I'll update this posting. I'd actually prefer that he believe the messages went out correctly and led to ZERO RESPONSE—my favorite result.
UPDATE (16 June 2006): From some additional samples I've seen, this spam was nothing more than a misconfigured mortgage spam. The model is confirmed in a properly configured message that used the same techniques. Subject: Danny Goodman Boss will be fired and then Danny Goodman, Our Office spoke last week,. The rest is standard mortgage spam fare. At least now I have something to report to the FTC.
Posted on June 15, 2006 at 09:52 AMJune 13, 2006
A Tech Support Dialog
I usually like the types of online organizations that provide a live chat method of support. When reporting phishing sites, time is of the essence, and if a web hosting service or domain name registrar lets me alert a real person immediately about a fraudulent site, then there's a good chance that the report will get the necessary attention and escalation, rather than sitting in an email queue.
Fairly frequently, in my experience, the live chat support folks are literate, reasonably technically knowledgable, and downright helpful. This is not one of those stories.
A standard phishing email message arrived here, and I followed my usual protocol to get the site taken off the air as soon as possible. This one had a newly minted domain name with the word "paypal" right in the name. Unfortunately, the site was hosted in China, whose ISPs generally don't react quickly to phishing reports (in English, at least).
But I was in luck. The domain's whois record showed that it had been registered through register.com. I checked the register.com tech support site, and found that they offered live chat support. Great! Or so I thought.
My first couple of attempts using Firefox on my Mac didn't work completely. The chat interface was loaded as a Java applet in a separate window, and I could see the comments from the register.com support person, but I could not type into the field where my comments were to go. I tried a second time, and then again in Safari, but it wasn't going to work.
So, over to a Windows machine, where, with Internet Explorer (always giving me the heebee jeebies) worked. I was on live with a support person. I'll leave out his name because these days, one never knows where on the planet a tech support person is situated, or under what nom de keyboard he or she might be working.
Here is the transcript of what turned out to be an extremely frustrating session:
Register.com:Thank you for visiting Register.com's Live Support. How can I help you?
You: Phishing domain registered through register.com: paypal-[redacted].com
Register.com: Could you provide me with your domain name please?
You: dannyg.com
You: I am not a register.com customer
Register.com: Okay.
Register.com: Thank you for the domain name. Please wait while I check for this domain name in our records.
You: I am reporting a fraudulent site whose domain is registered through you.
Register.com: Okay.
Register.com: can you provide you with that domain name?
You: paypal-[redacted].com
Register.com: Okay.
Register.com: Let me check for the domain name.
Register.com: What is the problem you are facing?
You: the domain is for a fraudulent paypal phishing site. Here's the url:
You: www.paypal-[redacted].com/PayPal/cgi-bin/webscrcmd_login.php
Register.com: Thank you . Please wait while I check for it.
Register.com: What do you find fishy about this?
You: Do you know what phishing is?
Register.com: I am sorry.
You: Pass this info along to your security folks. They'll understand.
Register.com: What due you find fraudulent about this?
You: The page is an imposter. It is not a real PayPal page, but instead captures usernames/passwords of PayPal customers for fraudulent activity.
Register.com: I will surely pass this issue to the appropriate department.
Register.com: Is there anything else I can help you with?
You: I doubt it.
Is it possible in the year 2006 for an individual working in the Web site domain industry to have not heard of "phishing?" Apparently so.
Like a lot of companies, Register.com appears to see the world through rose-colored glasses...a world in which there are no disputes, no crooks, no frauds perpetrated through their services. I searched their support pages for key words in these areas and came up empty on all counts. Whatever you do, don't make it easy for someone to report Bad Stuff, and don't train your people to be on the lookout for Bad Stuff.
Visualize me walking away slowly, shaking my head.
UPDATE: I'm happy to report that within about six hours of my attempt, the phishing site is no longer active, and the domain is no longer registered. I'm not claiming responsibility for the closure, but I sure hope I helped the cause.
Posted on June 13, 2006 at 10:54 AMJune 11, 2006
Old Phishing Wine in Old Phishing Bottles
If you are a crook and want to elicit a click response from a target, all you have to do is make the recipient believe that he/she has been charged money for something he/she didn't order. I've seen this ruse many times by criminals wishing to get you to visit a site that silently installs malware that takes over your PC (written up in Spam Wars). Phishers use the same ploy, claiming that the email message from PayPal (or whomever) is a receipt for a mythical payment. If you wish to dispute the charge, simply "click on the link below" to log in and resolve the issue. Where you click, of course, is on a link that leads to a bogus lookalike site that asks for your PayPal username and password. Enter that data, and kiss your PayPal account (and any funds therein or linked thereto) goodbye.
Phishing filters on incoming mail servers and in email programs might be on the watch for the usual types of content that phishing messages contain. But such filters won't catch a message whose only readable body content is contained in an image, like the following:
Even if the recipient has automatic downloading of images turned off, you can bet your bottom dollar that when the From: line reads "PayPal <service@payal.com>" and when the Subject: line reads "Your payment has been sent to mailto:sales@sonyusa.com"—and there is nothing else in the message except an image to be downloaded—the recipient will ask to download that image to investigate without hesitation. The impending doom of being charged many hundreds of dollars for something not ordered, nor shipped to a recognizable address, will override calm logic that shouts, "Why is this supposedly one-off message in the form of an image?"
Again, the real "secrets" of this message are to be found in the source code view, where nothing remotely connected to PayPal is in the unforgeable areas of the message header and body. I maintain that it is easier for a non-techie email consumer to learn how to identify bogus phishing messages in the source code than it is to learn how to use an iPod with iTunes. Unfortunately, and despite the huge risks of falling for phishing scams, the will to learn the right way to spot the scam messages isn't there.
Posted on June 11, 2006 at 11:20 AMJune 08, 2006
An Iraqi 419er (Probably Not From Iraq)
I've heard of 419 scams posing as appeals from U.S. military personnel in Iraq, but I usually like to see one in the flesh before commenting.
I didn't have to wait long.
I'll repeat the plain text body of the message (Subject: INSIGHT) in its entirety and add my two cents in various places in [brackets].
Dear Friend, [You know me that well, eh?]
My name is, Major. James Negron [Why the period after "Major"? Is it an abbreviation for Majorette?] and i represent a faction of American soldiers [I thought the "factions" were on the other side],serving in the military of the 1st Armored Division in Iraq, we came across your e-mail address(s) [Yes, I have multiple e-mail addresss.] in the process of research and enquiry into an immense millitary global data base. [I strongly doubt that any military (or millitary) database has my email address in it. Maybe the NSA, but not the military.] I believe you are familiar with the war situation in Iraq ? [Hmm, let me think....] Besides the killings, a lot of activities do occur; antique sales, stocked foreign cash discovery and lots more. We are lucratively involved in these activities, myself and my colleagues want to send consignments out of iraq, which will be discussed upon your acceptance of this transaction and we require a worthy,upright and business minded individual for safe keeping outside the Iraqi state. [What better way to find such an individual than sending out random email messages to "Friends."] You might have an insight through;http://news.bbc.co.uk/2/hi/middle_east/2988455.stm [Wow, hundreds of millions of dollars uncovered...this is real news! Oh, the article is three years old.] and details will be sent upon signal of interest. [I'll let you know through the Signal Corps.] Our contact email ; [removed]@virgilio.it [That's an Italian address, and so is the computer from which this message was sent.] Thanks for your co-operation
BSN2410. [??]
Signed,
Major. J. NEGRON [This capitalization of the name is a sure sign of a non-American author.]
So, what is this scam?
It is most likely the foreign check scam, in which someone sends you a check from a foreign bank. You are supposed to deposit it in your local bank account and wire by Western Union, say, 80% of the total to someone in another country. Your take is supposed to be 20%. Not a bad deal for doing next to nothing.
The problem is that even if you wait for the bank to tell you that the check has "cleared," it really hasn't. A few weeks later you learn that the check you deposited was made from the same material used for the Wham-O Superball. The bank wants its money NOW. You have no recourse, even though the bank told you the check had cleared. You are screwed.
I believe the most despicable part of this scam is that it preys on the sympathy that Americans (pro- and anti-Iraq War alike) have for the soldiers who are on the front line of battle. Who wouldn't want to help a soldier reaching out to someone back home? It is precisely that kind of emotional appeal that scammers use to cloud your judgement and sweeten that which should fail the "smell test" on several accounts.
Maybe we should send a brigade of the 1st Armored Division after these scammers. Now there's a war I think everyone could get behind.
UPDATE (4:25pm): Just got another one from "Major. Jeffrey Burton" with the exact same message, but different Italian contact address. Now I wonder if the scammer is reading this blog, because the "signature" line has the last name in all lowercase letters: "Major. J.burton". As they say in the chat rooms: lol.
Posted on June 08, 2006 at 08:58 AMJune 07, 2006
Mortgage Spammers Digging a Deeper Hole
The U.S. CAN-SPAM Act includes the following provision:
Prohibition of deceptive subject headings
It is unlawful for any person to initiate the transmission to a protected computer of a commercial electronic mail message if such person has actual knowledge, or knowledge fairly implied on the basis of objective circumstances, that a subject heading of the message would be likely to mislead a recipient, acting reasonably under the circumstances, about a material fact regarding the contents or subject matter of the message (consistent with the criteria used in enforcement of section 45 of this title). (15 USC 7704(a)(2))
In plain language: Don't screw with recipients' minds via the Subject: line to get them to open your spam message.
Over the past few days, I've seen mortgage spammers thumbing their noses at this provision with a vengeance. Look at this sampling:
- Crucial Comment of Default from Lender Danny Goodman
- Important Comment of Repossession from Bank
- Danny Goodman Criminal Activity Review
I'd expect this kind of thing from crackers who want to get you to visit a web page or open an attachment that silently loads malware to take over your PC, but all the mortgage lead clowns are doing is drawing more attention to themselves. Which is good, in a way, if the FTC is able to get on their cases (it's probably just one clown). As long as these spamming jerks keep sending it to me, I'll keep forwarding it to the FTC (spam@uce.gov), as you should, as well.
While seasoned spam haters recognize these subject lines as being bogus without even viewing the message's source code, the vast majority of casual email users' knees will buckle upon seeing any of these subject lines with their names in them. They don't understand that any kind of critical message of this variety would never be sent (or sent exclusively) via email. Real threats arrive by certified or registered postal mail.
Posted on June 07, 2006 at 12:19 PMJune 06, 2006
Headers Tell All
I know that most email users are absolutely terrified by the headers of email messages. They're hidden from normal view so as not to overwhelm Jane or Joe User with technical jibber-jabber. But the message header, despite the fact that so much of it can be forged by any spammer or cracker, contains valuable information for determining whether a message is legitimate or immediately worthy of the trash bin.
There are also occasionally some gems buried within headers that reveal how much contempt spammers have for their victims.
Take a message I just saw spamvertising the college-degree-in-a-month scam. It's the kind that doesn't mention the name of the institution, and simply provides a telephone number in the 206 area code—a number provided by a message-forwarding service. These messages always violate several provisions of the U.S. CAN-SPAM law, and I'm always eager to forward them to the Federal Trade Commission's spam refrigerator (spam@uce.gov) for possible use as evidence in future prosecutions.
Anyway, this message had a bunch of forged header fields, including the following:
Organization: lose.lose
I couldn't have said it any more succinctly.
Posted on June 06, 2006 at 11:16 PM