| Home | The Book | Training | Events | Tools | Stats |
June 21, 2010
A New Hour, A New Canadian Spamacy
Here we go for lunch time here on the West Coast:
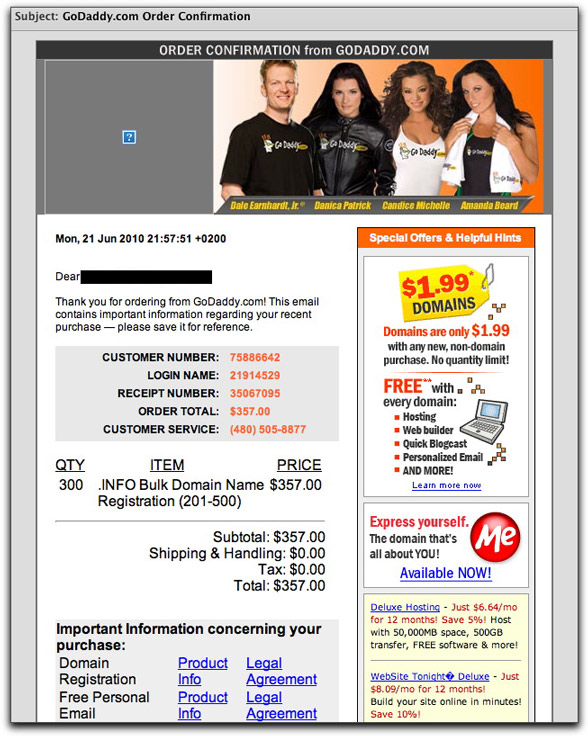
This claims to be an order confirmation from GoDaddy.com for $357.00. But all of the links lead to the same page from today's earlier obfuscated JavaScript page — which, in turn, takes you to the same Canadian Pharmacy domain being used for the last couple of days.
[Yawn.]

This is getting tiresome, Canadian Pharmacy:
Subject: ClickandBuy purchase confirmation
Dear [recipient email address],
You have made the following purchase using ClickandBuy:
Merchant: E-DevInvent GmbH
Date: Mon, 21 Jun 2010 17:29:20 +0100
Selected offer: 1000 Strip.TV Credits
Amount to pay: EUR 320.00 Currency Exchange Rate: 1
ClickandBuy account number: 81424628In order to answer this email and/or contact the ClickandBuy Service
Team, please click to attached file.
You will be redirected automatically to our contact form.ClickandBuy Customer Care Team
Attachment is a base64-encoded HTML page (login.html) whose primary content is the same type of obfuscated, script-kiddy JavaScript mentioned here. The destination URL is the same Canadian Pharmacy site referenced here.
These guys have been so egregious in their flouting of antispam laws around the world for so many years, it's hard to believe law enforcement hasn't been able to coordinate a multinational investigation to shut these guys down.
June 20, 2010
A Triple WTF?
Okay, strap your brain down for this one.
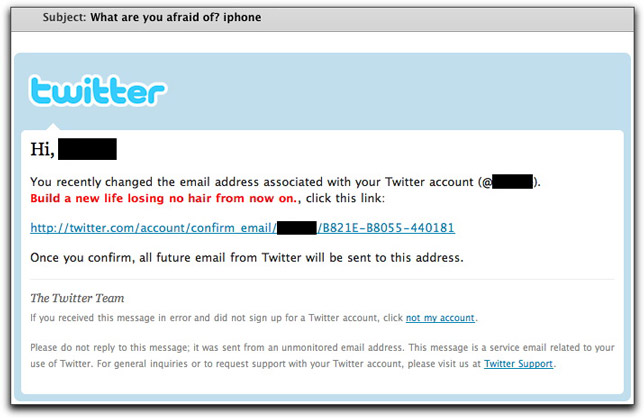
No sooner do I finish with a phony-amazon-order-to-medz misdirection, than a triple misdirection lands in the inbox. The inbox listing looks like the ordinary run-of-the-mill spam, with a medzy feel to it. The From: field is an unrecognizable aol.com email address, and the Subject: line reads, "What are you afraid of? [recipient email account name]". Surely it's a way to entice me to order up some illegal prescription medz.
But no!
The message has a largely Twitter look to it, but with a twist:
Under the guise of a Twitter email address change request, this message then adds a big red sales pitch on a cure for hair loss. This message, by itself, ranks high on the list of mind blows.
But there's more.
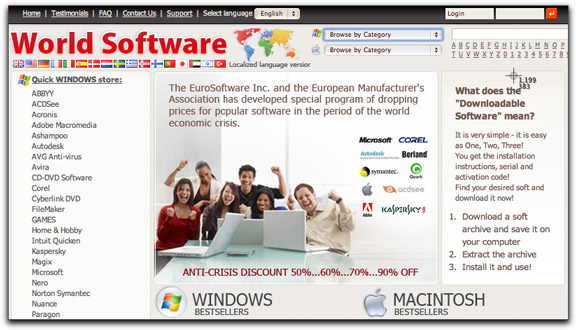
If you're fool enough to follow the link in search of a hair loss cure, you're in for yet another mind blow (perhaps enough to cut off circulation to even more of your hair). The destination isn't a medz site, a Twitter credentials phishing site, or a malware installer site (directly, that is). No, here is the destination:
The image may say "World Software," but the page identifies itself as a different, Eurpoean entity. They advertise all kinds of downloadable software — a.k.a. pirated software. Trust me: You can't buy a legitimate copy of the full $2600 Adobe CS5 Creative Suite for $250.
What the splashy web site doesn't tell you is that you get the added bonus of software that already has hidden malware installed in it. Even Mac users won't be immune because to install the fraudulent software, you'll be granting the installer full permissions to install whatever it wants at the same time. The malware is ready to pwn your computer to turn it into a botnet node and steal every login credential you type. In fact, you'd save yourself a lot of time by just sending your banking login credentials along with your credit card number when you order their non-upgradeable, unsupported products. At least then you'd know when your accounts were compromised.
Whew! I'm worn out from all the mind-bending tricks up the spammers' sleeves today.
Posted on June 20, 2010 at 12:05 PM
I admit to not having attended Business School, but I don't think I need an MBA in Marketing to know that explicit deceit is not a good way to attract customers. The Canadian Pharmacy jerks are doing just that — essentially letting potential customers know within one click of an email that they've been tricked. As if they're saying, "You stupid idiot! Now buy some Viagra!"
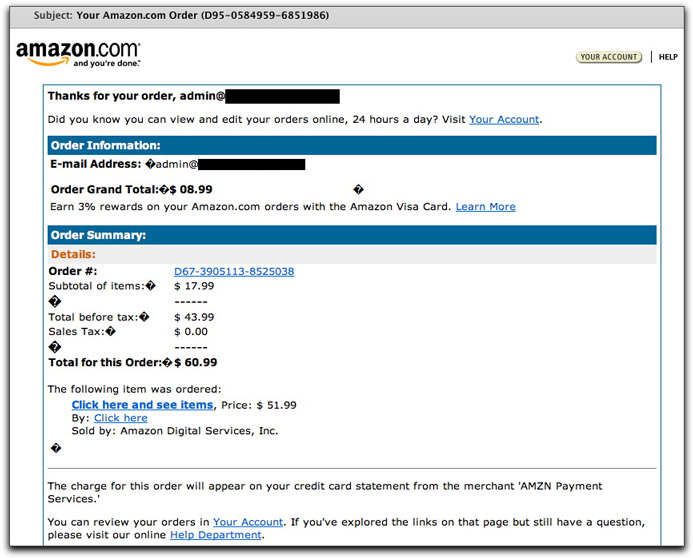
That's what is happening in today's fire hose spew, claiming in the From: and Subject: lines to originate from Amazon.com:
Ignoring the fact that none of the numbers in this bogus order notice add up, every link in the message points to a domain registered way back yesterday. The site hosts the pharmacy web page directly. (The little diamond/question mark symbols are from a high ASCII non-breaking space character that doesn't render in my email reader.)
I've seen plenty of these mind-blowing misdirections in the past — surprise, surprise...all leading to medz sites — and I just don't get it. I'd really like to know the twisted thinking behind this kind of effort, both on the part of the sender and on any recipient who then orders up some pillz as a result of being knowingly fooled.
Posted on June 20, 2010 at 11:24 AMJune 19, 2010
Worm Notice [Not] from Microsoft
It's probably just because I've been in the industry for so long, but I got a huge chuckle out of a bogus email spew overnight that claims to come from "Microsoft Support."
Subject: Your Computer has probably been infected
Dear Microsoft Customer,
Starting 17/06/2010 the ‘Conficker’ worm began infecting Microsoft customers unusually rapidly. Microsoft has been advised by your Internet provider that your network is infected.
To counteract further spread we advise removing the infection using an antispyware program. We are supplying all effected Windows Users with a free system scan in order to clean any files infected by the virus.
Please install attached file to start the scan. The process takes under a minute and will prevent your files from being compromised. We appreciate your prompt cooperation.
Regards,
Microsoft Windows Agent #2 (Hollis)
Microsoft Windows Computer Safety Division
This is wrong is so many ways:
- Microsoft never sends out this type of email.
- Being an American company, it would use the American style of date if it were to use the shortened version. The writer of this missive is definitely from outside North America.
- Microsoft would never readily admit that its software allowed infection by anything.
- How would an infection on my ISP's network (whatever that is) cause my computer to be infected?
After my chuckle, however, I could readily imagine the sinking feeling that occurs when you read something that might be official (assuming you didn't know better) that implies something serious has happened to your computer. I tried to run the attached file (setup.zip) through VirusTotal, but the site is down (coincidence, or DDOS by the perps?).
Unfortunately, this attack will probably be fairly successful in pwning a bunch of new computers, using them as botnet nodes, and stealing login credentials from every protected web site the victim visits.
Posted on June 19, 2010 at 09:23 AMJune 18, 2010
Canadian Pharmacy Needs a Dose of Immodium
The Spamhaus Number One Spammer, Canadian Pharmacy (or affiliates), has been pouring out more poisonous junk recently than the BP oil well.
Most recently, the messages include a small HTML document that is sent as a Base64-encoded attachment. Decoding the attachment reveals a whole lot of JavaScript code that has tons of red herring statements in it (real script-kiddie stuff), but all boils down to a document.href statement that points to a URL whose page is always z.html. Of course, that URL is not the final destination, but merely a waypoint onto the spamvertised web page where that god-awful Canadian Pharmacy peddles its potentially deadly crap.
In the last few days, the social engineering side of the campaigns — the message Subject: lines and enticing bodies — had been directed to recipients who might fall for the "secret admirer" scam. Subject: lines were things like "Love Of My Life", and message bodies were along the lines of:
You Complete Meopen attach and read all ;)
The HTML file attachment for many was named "loveletter.html."
Then, overnight, they (or a different affiliate) supplemented their repertoire with some Angelina Jolie and other "Holywood" [sic] superstar orgy videos, with subject lines in all caps that include the word SCANDAL. "[C]lick attached link and see video now", the message urges.
This morning saw another group, titled "adultfriendfinder new messages", a message body indicating I have three messages from young 20-something women. Yeah.
I urge you not to go down the trail. It is very possible that affiliates are being paid for visits whose referrers are the domains hosting the z.html files. Rewarding those bastards will just keep it coming.
Posted on June 18, 2010 at 10:10 AMJune 17, 2010
Changelog Malware Loader
Filed under "Keep It Simple Stupid" comes the following malware delivery spam with an attachment:
From: Dave Cross
Subject: Changelog 07.06.2010
Dear ladies and gentlemen,
as promised,
Dave
The attachment, named Changelog_15.06.2010.zip in the message I saw, has about 30% coverage at VirusTotal.
I suppose the unwitting knowledge worker at a company might fall for this one. And then pay the price.
June 15, 2010
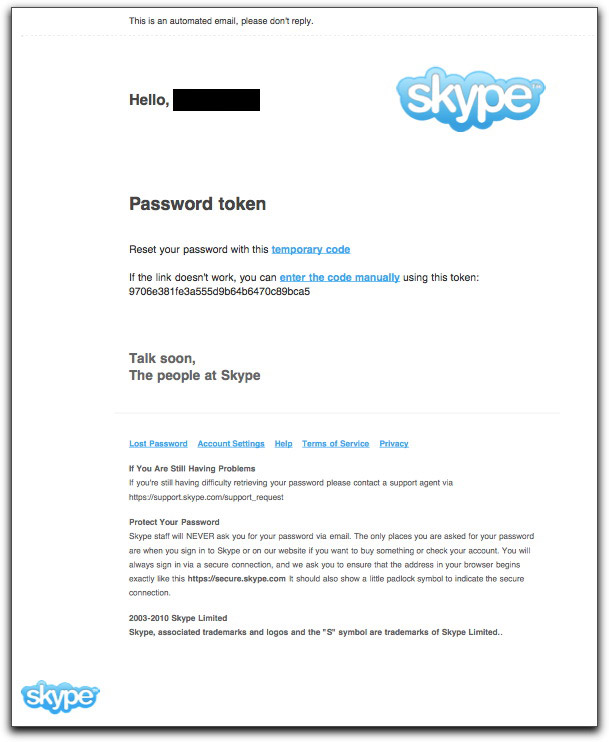
And Now Skype
All this "reset password" spam is really frosting my cake. With inundations for Twitter and Facebook password reset spam already clogging things up, I just saw the following one for Skype:
When I trace the links through the redirects, I get to a site from those Canadian Pharmacy scumbags.
In general, any time a random "reset password" email arrives in your inbox — and you didn't request to reset your password from the site — ignore it, delete it, move on.
Posted on June 15, 2010 at 09:48 AM
Pathetic.
Subject: Please look my CV. Thank you. MyID NR2936234.
Good day!
I have figured out that you have an available job.
I am quiet intrested in it. So I send you my resume,Looking forward to your reply.
Thank you.
Attachment, named resume593.zip, has a better than 50% VirusTotal recognition as a Trojan.
Posted on June 15, 2010 at 09:12 AM