| Home | The Book | Training | Events | Tools | Stats |
October 28, 2014
How Low Will They Go? This Low!
I'm trolling through some archived spam today and encountered what is one of the most despicable malware lures I've seen. Because the crook is attempting to emulate a British public health organization, it would horrify someone from the UK more than from other countries:
From: " National Institute for Health and Care Excellence" <results@nice.org.uk>
Subject: Blood Test Results EmailDear [email address removed]
We have been sent a sample of your blood analysis for further research.
During the complete blood count (CBC) we have revealed that white blood
cells is very low, and unfortunately we have a suspicion of a cancer.
Wite Blood cells 1200 Low
Hemoglobin 12 Normal
Platelets 19000 LowWe suggest you to print out your CBC test results and interpretations in
attachment below and visit your family doctor as soon as possible
Sincerely,Dr. Avery Ernie
Copyright 2013 National Institute for Health and Care Excellence. All
rights reserved.Attachment: test results 114AF-1.zip
Of course the only disease associated with this email is the malware infection caused by opening the attachment—a certain death sentence for your PC and security.
Posted on October 28, 2014 at 03:23 PMOctober 27, 2014
The Right Kind of Fear
It starts innocently enough. An email arrives:
From: email account security <notice@windows.com>
Subject: Mail Account Full, Upgrade To Receive Incoming Mails
The message body consists of a warning that would certainly get the attention of any Windows user who relies on email for personal—and more importantly—business communication:
Dear Email Account User,Your Email Account has exceeded it's storage Limit,
Most incoming messages may be placed on pending due to our recent Upgrade.
Verify your Email account immediately to get your Account Storage Upgraded.if not verified within 24 hours, we shall delete all your Email Account incoming messages.
Click here to Upgrade your email account storage now.
Thank you.
2014 Microsoft Security.
Suddenly the implication is that Microsoft runs your email (talk about Big Brother), and its security department is getting ready to cut you off.
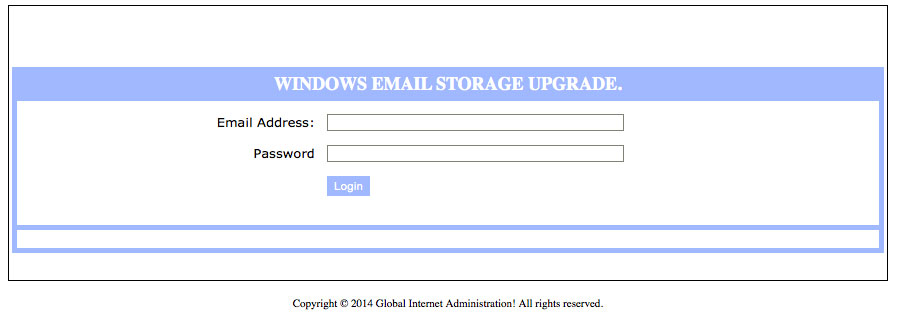
If you don't know to roll the cursor atop the link (or tap and hold on a touch screen) to see the URL associated with that link (a Thai business news website), or if URLs are mysterious gobbledygook to you, you may be so concerned that you click the link, perhaps in mini-panic. I was curious to see what the link's destination page did. Only after checking the source code of the page in an absolutely safe environment, I determined that the page consisted of a simple form (no redirection, or object or image loading going on, as usually happens). Here's the page:
If you supply the username and password and then click the Login button, your credentials pass through a program on the highjacked server, which passes that information along to an unknown Bad Guy. Web page copyright notice aside, there is no such organization called Global Internet Administration (and I felt very silly even typing that phrase into Google to confirm my suspicions).
So, what does the Bad Guy get in return? Of course he already has your email address, otherwise you wouldn't have received the message in the first place. But he doesn't know if your address—among the millions to which this message was sent—is still an active address and monitored by a human until you respond via the form. He also gets the Golden Key—your password—to your account at your email account domain. The most valuable domains in this case are the ones belonging to businesses (rather than the big ISPs like comcast.net). The smaller the company, the more valuable the credentials because if you use your computer for other corporate network activity, you probably use the same credentials to access the network. That's all an above-average cracker needs to rip his or her way through your company's computing systems. You just laid a Welcome mat before an unlocked door to the server room, offering access to financial accounts, trade secrets, and other users on the network (and thus their computers, contact lists, and so on).
I'm convinced that repeated newsworthy tales of computer security breeches have not hit home to the typical corporate computer user—despite having had multiple credit cards forcibly replaced in the past couple of years due to "hacks". And I'm not just talking about low-level computer-phobic employees. Top executives are perhaps even more vulnerable due to beliefs of invincibility or the false notion that the IT department offers 100% protection against attacks.
Rather than do the "right thing" upon receiving a message like the one above—contacting the IT or tech support desk to find out if the message is legitimate—users would rather bypass the hassle and try to handle it themselves. But unless such users are technically equipped to examine the 95% of the iceberg lurking below the surface before acting, the security of the company network is doomed.
At the same time, I understand that hounding IT for each and every attempted intrusion might engender its own terror. A condescending support tech who makes the user feel stupid for not summarily deleting such messages does just as much harm by encouraging users to poke around further, usually to a point that leads to successful phishing or malware installation. All it takes is a sigh or sarcastic tone from the support tech to discourage future requests for help. In truth, the user should be lauded as a hero whose actions become a teachable moment not only for him or herself, but for the rest of the staff.
Ultimately, I want users to be more concerned—nay, frightened—about the consequences of clicking that link or opening that attachment rather than the bogus threats or fake business opportunities and phony overseas purchase orders arriving in unsolicited email messages. The bomb starts ticking when the message lands in the inbox; acting on anything in the message leads to instant explosion.
That's the message that must get through to every internet-connected user on the planet.
Posted on October 27, 2014 at 11:20 PMOctober 20, 2014
Fake Adobe Creative Cloud Invoice
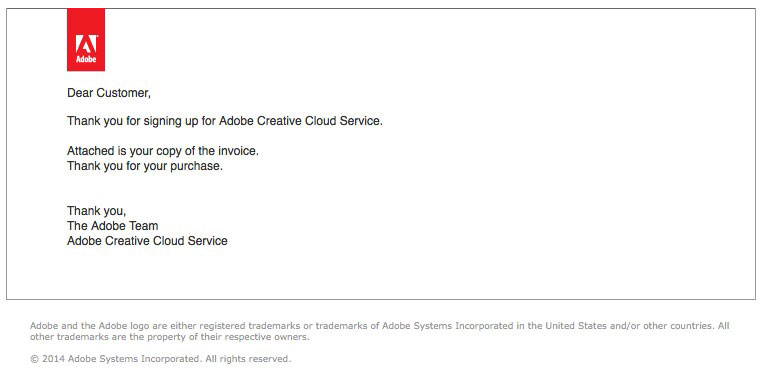
Received this scary (as in Halloween-scary) malware delivery that purports to come from Adobe (From: Adobe Billing; Subject: Adobe Invoice):
The attachment in my copy was a file named adb-102288-invoice.zip. If you get the same message, the number part of the file name will most likely be randomized, so don't expect a perfect name match.
What freaks me out about this mailing is that the .zip file passed through VirusTotal with a perfectly clean score. But woe be unto the person who opens that file. That warning should go for both Mac and Windows users (and perhaps even Android). The malware file has most likely been processed through known Bad Guy services that make just enough modifications to such files to eliminate (for a short time) the possibility of being filtered by antivirus incoming email checkers, yet still delivering the damaging part of the malware. Once the file has passed into recipients' inboxes...well, consider an army of undead, crawling through your computer and your company networks to suck brains.
If you try to be careful and check attachments against services such as VirusTotal, it's clear that such vigilance is not enough. Your suspicion radar dial must be turned up to eleven. In this case that would lead you to inspect the header of the email, where it clearly shows the email originated from a block of IP addresses in Morocco—not exactly in Adobe's backyard.
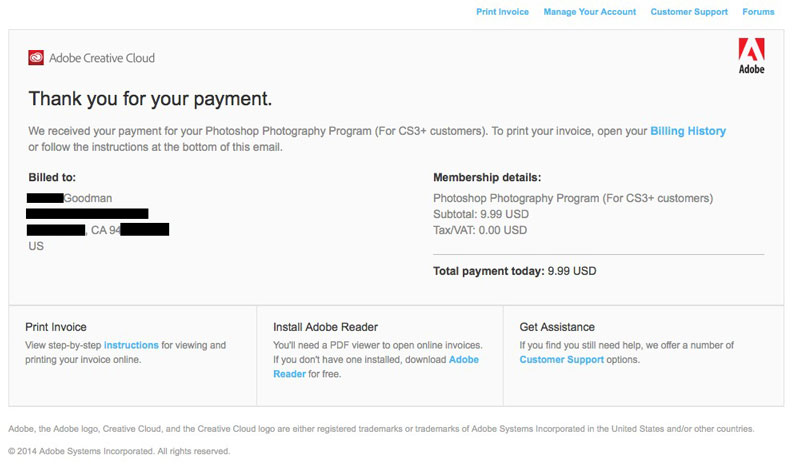
Incidentally, here is a genuine invoice payment notice from Adobe for Creative Cloud:
There is no attachment. Even so, I'm not a fan of the use of links to reach your account information. I'd rather they instruct recipients to log into https://accounts.adobe.com manually or via previously set browser bookmarks.
Posted on October 20, 2014 at 10:40 AMOctober 09, 2014
More iTunes 2-Factor Phishing
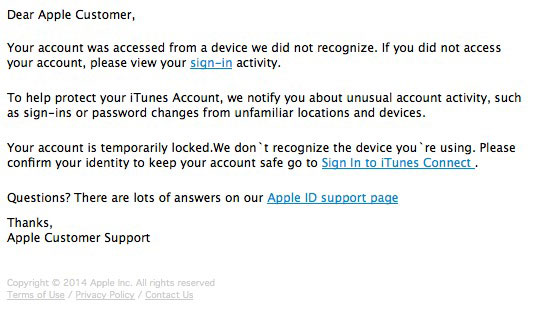
Arriving today is a variation of the Apple Two-Factor ID phishing scam I wrote about recently. Claiming to be From: Apple Support with the Subject: iTunes Sign-in Alert!, this one builds on actual wording that Apple uses in a variety of ways (not always email) to the fact that you are using a previously unauthorized device to access your iTunes account. With millions of Apple customers upgrading to iPhone 6-generation devices, those who had previously signed up for two-factor account safety have seen these kinds of alerts, so they may not seem so frightening—more frustrating actually, because they've already registered their new phones. Such users can easily chalk up the email to Apple's systems getting confused and having to re-do their registration.
Crooks know this, and try to trick anyone with an iTunes account into handing over their iTunes login credentials (frequently linked to a credit card and much other personal information). Today's email begins "Your account was accessed from a device we did not recognize." And note how they try to emulate the look and feel of a genuine Apple communication:
If you know to roll the mouse over one of the active links (or press and hold the link if you're on an iPhone/iPad device), you'll soon see that the link goes to a domain other than apple.com. More importantly, if the email message has unnerved you enough to make you worry about your account, log into your account as usual (via the iTunes app), and not through links in email messages. You will quickly see that everything is normal.
Posted on October 09, 2014 at 08:00 AMOctober 06, 2014
Worthless Rewards Spam Piling Up
I wrote the other day about spam flogging phony retail rewards programs. They seem to breeding like fruit flies. I haven't been keeping a comprehensive log of the retail brands being fraudulently used to trick recipients into taking surveys and participating in all kinds of worthless promotions that never result in getting any rewards.
Here are the brands I remember:
- Costco
- CVS Pharmacy
- Home Depot (high-volume spam on this one
- Kohl's
- RiteAid
- Victoria's Secret
- Walgreens
In the past, participants who fall for these promotions have had to follow a tortuous trail of site visits, surveys, software installations (always a big signal flare of no-goodness), surrendering personal information, and ratting out your contact list friends and family members. The tactics were profitable for the crooks in the past, so you can be sure they're still at it.
Although there actually are free lunches on the Internet (some fine advertising-free web browsers, for instance), a $50 or $100 gift card offer sent to millions of email users isn't one of them. Save yourself a lot of anguish, and, more importantly, prevent the spammers from making even a fraction of a cent from you. Don't follow the links, and delete the messages.
Posted on October 06, 2014 at 04:18 PM