« Fake Adobe Creative Cloud Invoice | Main | How Low Will They Go? This Low! »
| Home | The Book | Training | Events | Tools | Stats |
October 27, 2014
The Right Kind of FearIt starts innocently enough. An email arrives:
From: email account security <notice@windows.com>
Subject: Mail Account Full, Upgrade To Receive Incoming Mails
The message body consists of a warning that would certainly get the attention of any Windows user who relies on email for personal—and more importantly—business communication:
Dear Email Account User,Your Email Account has exceeded it's storage Limit,
Most incoming messages may be placed on pending due to our recent Upgrade.
Verify your Email account immediately to get your Account Storage Upgraded.if not verified within 24 hours, we shall delete all your Email Account incoming messages.
Click here to Upgrade your email account storage now.
Thank you.
2014 Microsoft Security.
Suddenly the implication is that Microsoft runs your email (talk about Big Brother), and its security department is getting ready to cut you off.
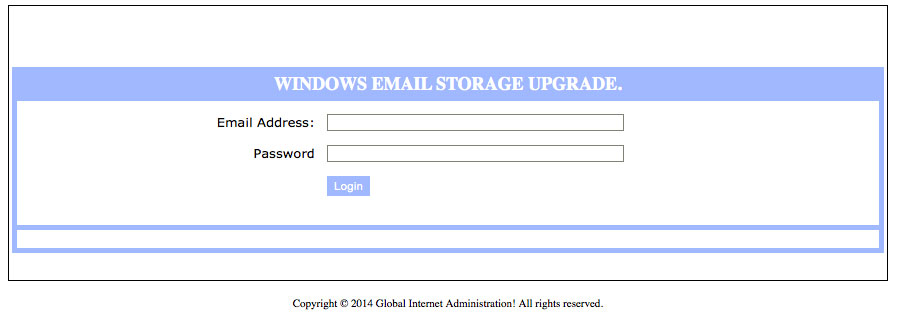
If you don't know to roll the cursor atop the link (or tap and hold on a touch screen) to see the URL associated with that link (a Thai business news website), or if URLs are mysterious gobbledygook to you, you may be so concerned that you click the link, perhaps in mini-panic. I was curious to see what the link's destination page did. Only after checking the source code of the page in an absolutely safe environment, I determined that the page consisted of a simple form (no redirection, or object or image loading going on, as usually happens). Here's the page:
If you supply the username and password and then click the Login button, your credentials pass through a program on the highjacked server, which passes that information along to an unknown Bad Guy. Web page copyright notice aside, there is no such organization called Global Internet Administration (and I felt very silly even typing that phrase into Google to confirm my suspicions).
So, what does the Bad Guy get in return? Of course he already has your email address, otherwise you wouldn't have received the message in the first place. But he doesn't know if your address—among the millions to which this message was sent—is still an active address and monitored by a human until you respond via the form. He also gets the Golden Key—your password—to your account at your email account domain. The most valuable domains in this case are the ones belonging to businesses (rather than the big ISPs like comcast.net). The smaller the company, the more valuable the credentials because if you use your computer for other corporate network activity, you probably use the same credentials to access the network. That's all an above-average cracker needs to rip his or her way through your company's computing systems. You just laid a Welcome mat before an unlocked door to the server room, offering access to financial accounts, trade secrets, and other users on the network (and thus their computers, contact lists, and so on).
I'm convinced that repeated newsworthy tales of computer security breeches have not hit home to the typical corporate computer user—despite having had multiple credit cards forcibly replaced in the past couple of years due to "hacks". And I'm not just talking about low-level computer-phobic employees. Top executives are perhaps even more vulnerable due to beliefs of invincibility or the false notion that the IT department offers 100% protection against attacks.
Rather than do the "right thing" upon receiving a message like the one above—contacting the IT or tech support desk to find out if the message is legitimate—users would rather bypass the hassle and try to handle it themselves. But unless such users are technically equipped to examine the 95% of the iceberg lurking below the surface before acting, the security of the company network is doomed.
At the same time, I understand that hounding IT for each and every attempted intrusion might engender its own terror. A condescending support tech who makes the user feel stupid for not summarily deleting such messages does just as much harm by encouraging users to poke around further, usually to a point that leads to successful phishing or malware installation. All it takes is a sigh or sarcastic tone from the support tech to discourage future requests for help. In truth, the user should be lauded as a hero whose actions become a teachable moment not only for him or herself, but for the rest of the staff.
Ultimately, I want users to be more concerned—nay, frightened—about the consequences of clicking that link or opening that attachment rather than the bogus threats or fake business opportunities and phony overseas purchase orders arriving in unsolicited email messages. The bomb starts ticking when the message lands in the inbox; acting on anything in the message leads to instant explosion.
That's the message that must get through to every internet-connected user on the planet.
Posted on October 27, 2014 at 11:20 PM