| Home | The Book | Training | Events | Tools | Stats |
August 24, 2006
Is spamwars.com Being "Joe-Jobbed?"
Over the past few days, a few people have used the Contact Form here to leave "interesting" comments for me, such as:
- remove me from your database
- Stop spamming me
Unfortunately I get no further details, but the signals indicate that there is spam that either purports to come from spamwars.com or spamvertises the site.
For the record:
- No email originates from the spamwars.com server.
- Any email that I send with a From: field showing a spamwars.com domain is a one-off, personal message, usually in response to another personal message. Such emissions from me are extremely rare, as most of my email goes out from another domain.
- I do not maintain any kind of email address database or mailing list.
- I do not send out newsletters. The RSS feeds from my blog (to which users anonymously subscribe through their browsers or newsreaders, and read when they want to) are the only non-Web based communications vehicle I use for this site.
- I do not, nor have I ever asked or hired anyone to, send automated email advertising this site. To do so would be beyond stupid.
If you receive a spam message that in some fashion points back to spamwars.com, please use the Contact Form to send me the complete source view of the message so I can analyze it on this end.
It's possible that one of my blog entries pissed off a spammer; or a phisher would like to see my success at taking down phishing sites cut short by damaging the reputation of the site. How pitiful.
Posted on August 24, 2006 at 11:27 PMAugust 14, 2006
Phishers Giveth
In their never-ending quest to lure unsuspecting victims to log into phony lookalike Web sites, phishers pull every kind of trick. They've all begun to merge before my eyes, so it's not easy to know if I've seen a particular ploy before or not. Maybe I just haven't seen this for awhile.
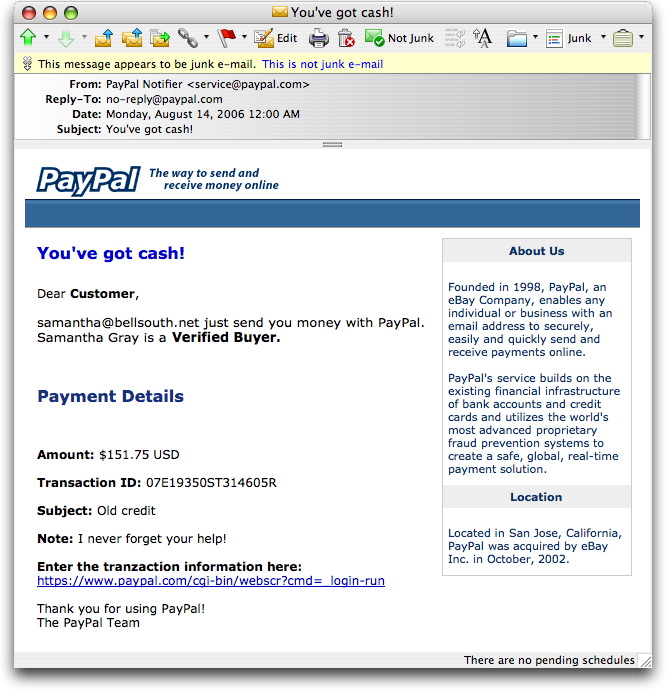
It's quite common for a PayPal phisher to send a message that claims you've paid for something out of your PayPal account—when you know damn well that you didn't. All huffy and irate, you follow the link and log into the site. Whammo! Your PayPal ID and password are gone.
Tonight's missive is just the opposite. Someone named Samantha Gray has supposedly sent me money via PayPal. Here's what the message looks like in my email client:
Things fall apart at the end of the message with the spelling of "tranzaction," but I'll bet plenty of greedy recipients will overlook such details on their way to collect their $151.75. Log into the page (hosted at a hijacked Brazilian server), and you really ought to receive a message that starts:
You've got trouble!
Posted on August 14, 2006 at 12:36 AMAugust 13, 2006
Don't Phishers Do the Math?
How smart is it to blast out phishing spam nationwide (if not worldwide) when the only possible customers of the financial institution being targeted are in the Texas Gulf Coast region?
I got a typical "error in your billing information" phishing message purporting to come from the Texas Dow Employees Credit Union. I checked out their real Web site, and they claim to have 93,000 customers in the gulf coast region (in and around Houston).
The chance of one of these messages reaching the inbox of a TDECU customer has got to be less than miniscule (if, as a California resident, I'm on the target list). Subtract from that the number of recipient customers who (I hope) smell a rat and won't respond. Better still, as I was composing this blog entry, the owner of the hacked site with the phony page shut it down (within minutes of reporting!).
What I like, in a way, about this kind of phoolish attempt (like the ones that get sent through email systems that tag the Subject: line as SPAM or PHISHING before the recipient sees them) is that somewhere along the line, the individual who caused the message to be sent had to exchange something of value to get the message out—usually through botnets these days. It may not be a high expense, but these guys are working on low margins and very low response rates. If a phishing run yields no account names and passwords, the "investment" was a failure.
My biggest wish in the spam world is that spamming, phishing, and other criminal activity no longer pays for itself and the word spreads among the crooks (and wannabe crooks). When the crooks contribute to their own failure through stupidity, who could ask for anything more?
Posted on August 13, 2006 at 03:21 PMAugust 06, 2006
Attack of the Dictionaries!
When I first set up my email account (eons ago), the default configuration was as what is known as a "catch-all" account. In other words, an email message addressed to any user ID at my domain would be handled as if it were addressed to my preferred user ID.
These days, running your email server with a catch-all account is tantamount to suicide by spam—spamicide, if you will.
My email server is set up to accept messages addressed to only a handful of user names, while any attempted connection for the purpose of sending to a different user name is immediately rejected. If you are a real correspondent, you will be alerted within seconds of clicking the Send button that something is amiss. If you're a spammer sending through zombie PCs, the zombie ignores the rejection and carries on with its mindless spamming to the next address on its list.
I talk more at length about dictionary attacks in Spam Wars, so there's no need to embellish here. I bring up this subject because I noticed a huge spike in attempts to send mail to unassigned user IDs yesterday. The usual background noise of such mail is on the order of 1500-3000 per day. Saturday's spike (visible for one week on the Spam Wars Spam Stats page) shows more than 21,000 such attempts. If I still had my email server set up in catch-all mode, those 21,850 spam messages would have been processed by my spam filters, with some (way too many, probably) getting into my inbox.
In the past, such massive attacks usually come from one IP address (I recall Hong Kong and Canada being past sources). I don't have the time now to look through the logs to find the source, and the incentive to find the originating IP address is probably a waste of time anyway because the attack was most likely done through a multi-step relay with no traceable (by me) record of the real source.
These are the kinds of things that occur every day in spamdom. Most ISPs today expend resources fighting off such attacks, and everyday email users aren't even aware that such things happen. But believe me when I say that we're all paying for it one way or another.
Posted on August 06, 2006 at 01:14 AMAugust 02, 2006
Phishing By Dummies
If there were a book titled "Phishing By (Not For) Dummies," a message I received today would deserve a mention.
It was a usual PayPal phishing message, except for the Subject: line:
IMPORTANT: Alert about your AOL billing information on file
The phishing site was hosted on a hacked Web site hosted in Germany. That's usually pretty good because German ISPs don't have much of a sense of humor when it comes to this kind of activity. In addition to alerting the address in the whois record, I fortunately know just enough German to wade through the ISP's site to submit the proper report. I knew that studying all those Märklin sites and magazines would pay off.
Posted on August 02, 2006 at 04:57 PM