| Home | The Book | Training | Events | Tools | Stats |
November 27, 2004
The Phisher Doth Protest Too Much
I don't know why I've been pounding on phishing scams lately—perhaps it's because they've been pounding on my inbox.
But today's deliveries included a bogus PayPal notice that is really counting on recipients using Internet Explorer for Windows, all unpatched. The HTML message includes a sidebar with this little tidbit:
A genuine PayPal link will always begins with "http://www.paypal.com"
Remember to check your browser's Address/URL Bar to be sure you are on an authentic PayPal site.
Please make sure the link you click on starts with "https://www.paypal.com"
(Note the conflict between "http:" in the first item and "https:" in the last.)
The message displays what looks like a link with PayPal's actual address (with the secure https: protocol), but, as I revealed in the previous entry here, the source code applies the "hex zero" trick that hides the bad part of the address in the IE Address field:

Other wording in the message blares: "This is NOT a SCAM or HOAX. Please check your address bar to make sure you are on the authentic PayPal website." Except that the phisher's site is not served by a secure server, and will reveal "http:", not "https:" in the Address bar, as the real PayPal site does. Of course not many Web users would notice the subtle, but incredibly important difference. I've yet to see a phisher's Web site operate as a secure server, but anything is possible.
Like I say frequently in Spam Wars, the more a spammer or scammer professes honesty, the more likely the opposite is the case.
Posted on November 27, 2004 at 07:33 PMNovember 25, 2004
Phishing Spree
The last few days have brought quite a few phishing messages my way. Looking back I see Well Fargo Bank, Suntrust, Western Mutual, eBay, and PayPal. They use a variety of URL cloaking techniques, but nothing new.
Since the Windows patch for one trick has been out for awhile, I thought the trick would go away. But it has shown up a few times recently. In unpatched Windows systems, the status bar view of the clickable link fails to show the full URL, only the bogus part that looks legitimate. In the message's source code view, you can spot these easily, like this one:
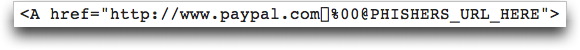
Those weird characters (following "paypal.com") fool unpatched Windows machines to hide themselves and everything after them. But when you click the link, the browser goes to the Bad Guy's Web site.
The other technique is more difficult to sniff out, because the click link goes to a real URL of a real Web site. Unfortunately, the Web site is usually a server that is set up insecurely (typically a small business, but sometimes even biggies) and has been cracked. The cracker has installed a special directory in which the phishing page and server processing code is located. The rest of the site works like normal, and the site's owner has no idea the hidden stuff is there, robbing unsuspecting visitor's of their identities. Over the years, I've alerted numerous site managers about the invasions and got them to remove the offending directory and change their passwords to keep intruders out.
Despite their frequently professional looks and seemingly earnest messages enticing recipients to give up information almost down to their shoe sizes, the source code of these messages contain lots of other clues that wouldn't fool any Spam Wars reader.
Posted on November 25, 2004 at 11:02 AMNovember 22, 2004
A Mixed Message
Is it intentionally bad spelling to get past filters? Or bad grammar from a non-English-speaking spammer? Or a spammer who has been reading too much spam about other subjects?
Subject: Save hundreds -- pucrhase unexpenisive OEM software
The spamvertised link (for pirated software) is hosted in China, and bears a domain purportedly registered to someone in Russia. The message was sent through a Trojaned PC (a customer of @Home Kabelinternet) in the Netherlands.
My best guess is that the Web site will simply grab your credit card data and send you on a not-so-fun ride to credit card or identify theft hell.
Posted on November 22, 2004 at 11:29 AM
After several years of watching spamvertised domain names in spam links (and adding them to my "delete at the server" list), I used to wonder if spammers would get tired to concocting yet more combinations of words that convey "meds," "savings," "rx," "pharm," "free," "herbal," "4U," and other likely suspects. My list continues to grow, but they've had to branch out to other techniques to find unclaimed .com domain names.
Because the actual linked domain can be hidden behind HTML message links that say anything, a lot of domain names in the last year or so have been either total gibberish (like a cat walking across a keyboard during domain registration) or, more recently, almost dictionary-attack-like combinations of two or three real words (in English) that have nothing to do with the spam subject. I'd share some of them with you, but I don't want to advertise these sites for the spammers.
As long as spam recipients continue to preview messages from, click-through to, and buy from spamvertisers, the spam meisters will continue to concoct yet more domains du jour.
Posted on November 22, 2004 at 10:32 AMNovember 21, 2004
Medz--Coming and Going
Of course the medz spammers have been around forever, many of them offering prescription drugs without prescriptions. Sometimes it's the real stuff, sometimes not.
But now that Vioxx has been taken off the market, I've seen new rounds of spam to lure former Vioxx users into class action lawsuits against the drug's maker. I won't visit the Web sites that these messages link to, but they and the messages they send seem to be operating within well-known spam regions of the Internet. I suspect they are more into gathering live email addresses (and perhaps other personal information) than doing anything to assist those who believe they were harmed by the drug.
Just one more spam angle that we should ignore at all costs.
Posted on November 21, 2004 at 09:01 AMNovember 17, 2004
Phisher, Buy a Calendar!
An eBay phishing message arrived today (check the posting date) that might have a hard time convincing recipients of its urgency. It said in part:
We recently have determined that different computers have logged onto your eBay account, and multiple password failures were present before the logons. We now need you to re-confirm your account information to us. If this is not completed by August 30, 2004, we will be forced to suspend your account indefinitely, as it may have been used for fraudulent purposes.
The due date was in bold, just like I posted it here. Darn it! Too bad I've been suspended since August, yet used my account regularly since then.
Among the "secrets" in the source code view of this message was that the link, while displaying a genuine ebay link, actually led to a Web site identified only by a numeric IP address. Buzz off, phisher!
UPDATE: The same formatted eBay phish has arrived a few more times, sometimes with a November date, other times with an August date. The destination IP addresses are all over the place: China, India, and Guatemala. I get the feeling that this message form is part of a "kit" that someone is selling to wannabe phishers, some of whom are too stupid to change the default "deadline dates" to something more realistic.
Posted on November 17, 2004 at 09:04 PMNovember 15, 2004
How Spammers Respect You
There is a good article in the New York Times (registration required) about a Virginia spammer who was found guilty of various offenses related to his bulk mailing business. One of the offers was a work-from-home scheme for processing FedEx refunds. I know a lot of those messages came my way.
According to the article, thousands of people per month paid $40 for what turned out to be little more than access to a Web site listing delinquent FedEx accounts. Here's how badly the spammer feels about what he had done:
"When you're marketing to the world, there are enough idiots out there" who will be suckered in, McGuire said in an interview.
I urge you to think twice before opening a suspicious message from an unknown sender; and never ever buy from a spammer.
Posted on November 15, 2004 at 08:23 PMNovember 13, 2004
Foreign Language Spam
In "Spam Wars," I write about clueless spammers who "think locally and act globally." They compose spam in non-Roman languages (commonly Russian and Chinese) and address the spew to a .com domain. Of course, nothing about a .com domain indicates that its owners and recipients are exclusively English-speaking, but the chance that they'd know (or that their computer could even display) Russian is miniscule, compared to someone at, say, a .ru address.
And so, today I saw a spam message in the queue whose title was all gibberish. Inspecting the source of the message, I traced that it had originated from Israel. The Subject: line language was, I now assumed, Hebrew. The message body was simply an image (retrieved from an Israeli web site) and—if I had opened it in my email viewer—a hit counter supplied by a third-party source (Finland-registered, U.S.-hosted). Fortunately, my safe way of previewing suspicious mail prevented the suspect hit counter from incrementing a single digit.
The image, I discovered separately, contained Hebrew text and graphics clearly aimed at Israeli kids (fuzzy cartoon characters with big googly eyes). The domain name indicated that it was for kids, while its .il country domain further pointed to an Israeli connection. The spam message body would have also downloaded MIDI and MP3 sounds, had I opened it normally (whew!).
It's hard to tell whether the outfit being advertised (a domain with a few years' seniority) was doing the advertising, or if a Trojaned PC somewhere in Israel had been hijacked to email a kind of Joe Job against the site—while driving the hit counter via a quasi-sneaky way. The IP address of the message's entry point was a dial-up provider in Israel, so there are a few possibilities behind this "campaign."
On the one hand, I hope that the advertisers weren't so Spam Rule #3 Stupid as to send Hebrew ads to the great Internet void. On the other hand, I hope that some unsuspecting Israeli computer user hasn't had his or her computer hijacked by ne'er-do-wells.
Posted on November 13, 2004 at 03:27 PM
Dictionary email attacks really shot up here on Friday. Instead of the usual 5000-7000 attempts, the zombie PCs around the world tried over 11,000 times to send mail to invalid addresses at my venerable dannyg.com domain. Other spam activity here seemed (alas) normal.
I believe that the army of zombie PCs being remote controlled by some Really Bad People is an enormous potential threat to the Internet. I have my fingers crossed that the infections and the control codes are diverse enough to prevent one controller from taking over the world's zombies. In the meantime, please, everybody install, update, and use accredited antivirus and antispyware software (i.e., not the stuff offered to you in spam messages or popup ads). And tell your friends!
Posted on November 13, 2004 at 08:46 AMNovember 11, 2004
Welcome to the "Spam Wars" Blog
I'm proud to launch this web log in support of my latest book, "Spam Wars." This is where I'll have a chance to keep the book up to date and comment on the latest tricks perpetrated by spammers, scammers, and hackers.
I've seen the first copies coming off the press. Yippee!
I'm as excited about this, my 40th book, as I was about my first. I hope you enjoy it and learn from it to help rid the Internet of the multiple scourges seeking to take advantage of unsuspecting email users.
Posted on November 11, 2004 at 08:20 PM