| Home | The Book | Training | Events | Tools | Stats |
August 14, 2012
Phony London Olympics Lottery
Woohoo! I just won not only a million pounds, but also "free entrance tickets to watch the games live in London" How lucky can a guy get?
It's the old advance-fee (a.k.a. 419) scam. Maybe my email address was on a slow list. Or the scammer just doesn't give a damn that the games are over. Here is some of the text from the Word attachment to my otherwise non-descript email message:
2012 London Olympics Promotion Draws Notice
Attention: Dear Winner,
This is to inform you that London 2012 summer Olympic awareness and promotion company and London 2012 summer Olympics Organizing Committee (LSOOC) here in London (U.K) has held an Internet Raffle Draw today among all internet email users around the globe and your email address was among the 10,000,000.00 (Ten million) email addresses that was randomly picked by the computer during the Second Quarter Raffle Draw in conjunction with Microsoft (SQRD).We are therefore with great pleasure to notify you that your email address happened to come out top number (6) out of the 10,000,000.00. (Ten million) email addresses on the final email ballot draw.
Please note that this has made you the jackpot winner of £1,000,000.00 (One Million British Pounds Sterling Only) and free entrance tickets to watch the games live in London.Participant’s email addresses were sorted globally (Powered by Microsoft) from companies, individuals, Government's agencies, co-operate bodies, charity homes etc and computed “RANDOMLY" via E-sorting balloting to select respective winners around the globe.
Be aware that this Internet Raffle Draw (IRD) was organized by London 2012 summer Olympic awareness and Promotion Company and London 2012 summer Olympics Organizing Committee (LSOOC) to create awareness to the world as England is finalizing their preparation for the hosting of the 2012 summer Olympics.
What I really like about this message is that it is littered with copies of London 2012 Olympics logos and art. My hope is that the International Olympic Committee will hunt down these assholes for abusing the "Olympics" name, as they are wont to do. The fact that the scammers are in South Africa should present no geographical barriers to the IOC. Maybe give the guy a call on the number provided in the message, arrange a meeting, bring the cops...ooh, let me dream!
Posted on August 14, 2012 at 05:54 PM
Today's menu features our chef de la malware cooking up fake Amazon and Bank of America emails that try to trick recipients into visiting hijacked web sites or opening Trojan attachments. If you take a bite of those messages, your privacy and personal data will get the runs.
Both of these message campaigns have circulated for several days, so they may not be news to everybody. Still, they're worth seeing to help you spot similarly constructed fakes in the future.
The one first claims to come from amazon.com, although in the copy I saw today, the crooks couldn't get their spam machines to behave properly and had the phony From: field say it's from UPS Global Express. This message, whose Subject: line reads:
Subject: We can not charge your credit card
is funny in a sad kind of way. Although attempting to imitate the look of an amazon.com HTML email, the message's grammar is ridiculously bad:
Your credit card was blocked.We tried to withdraw money from your credit card, but your bank decline it. In the attachment you will be found a invoice from your last order. Please pay this invoice as soon as possible.
Whoever wrote that would have his knuckles cracked with a ruler by the school teacher who taught English to that eastern European student. Simply atrocious.
The second message claims to come from Bank of America—yet another attempt by the crook to hang his hat on a hook of this large financial institution. I'm not aware of the service referenced in the message, but it might have something to do with corporate accounts:
Subject: CashPro Online Digital Certificate Granted
August 14, 2012
Dear Customer,
This email is being sent to inform you that you have been granted a new digital certificate for use with Bank of America CashPro. Online.
Please login to CashPro Online, you will be guided through a simple process to create and install your digital certificate.
Also you can download new digital certificate at https://cashproonline.bankofamerica.com/AuthenticationFrameworkWeb/cpo/login/protected/pickUpCert.faces.
If you have any questions or concerns about this digital certificate, please contact your Client administrator.
Thank you for your business,
Bank of America
CashPro Online Security Team
Please do not reply to this email as it is an automated message and the email box is not monitored.
The Bank of America Technical Help Desk can be reached at:
United States & Canada: (888) 589-3473
EMEA: +44 (0) 20 8313 2154
Asia: (65) 6239 3300
Australia: (61) 2 9931 4333
Latam: (469) 330-1160
)Copyright 2011 Bank of America Merrill Lynch. All rights reserved. CashPro is a registered trademark of Bank of America Corporation.
The links, of course, are to a hijacked web site that redirects to the usual JavaScript-based malware loading techniques. If this message lands on a PC that is used for corporate online banking (online banking and email on the same machine? NO NO NO), and if the recipient isn't smart enough to spot a phony, the crook has hit the Big Time. You'd think by now that businesses that do online banking would at least be equipped with anti-virus software to spot the more egregious attempts to take over the computers. But the tactic must work sufficiently often to get the crooks to keep trying. Sucking tens or hundreds of thousands of dollars from a single business bank account makes the cost of sending gazillions of spam messages and recruiting money mules seem like pocket change.
I hope you enjoyed today's meal. The chefs are hard at work on new dishes to trick the unwary.
Posted on August 14, 2012 at 01:38 PMAugust 13, 2012
More Fake Bank of America Malware Lures
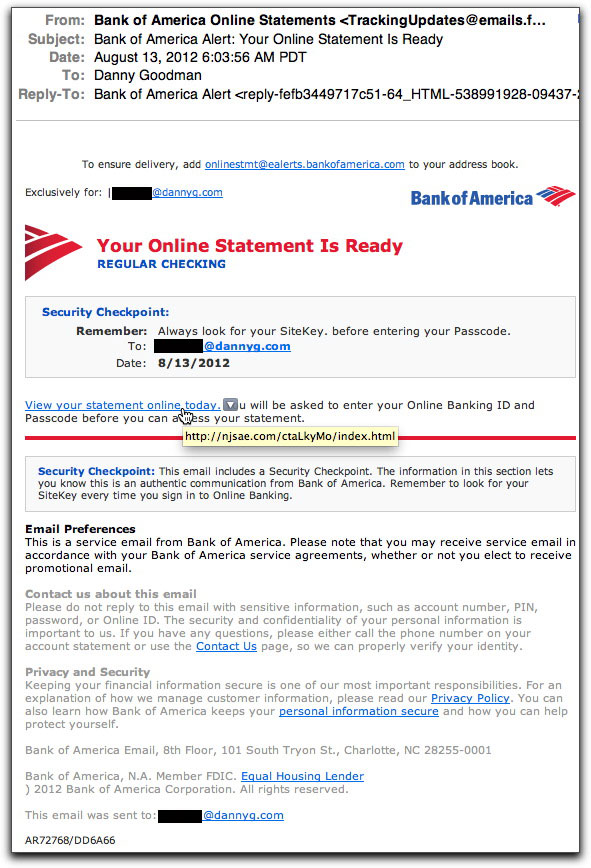
The Bank of America continues to be a popular brand name abused by those crooks out there who want to trick recipients into clicking their way to infection. They got their hands on a real Bank of America email notification—most likely stolen from one of the PCs they own from a previous infection—and used it to generate a pretty convincing replica of the type of notice a BofA online banking customer might receive. In this case notice that "Your Online Statement Is Ready", timed to arrive just about when BofA online statements for consumers are, indeed, ready:
You'll save yourself a lot of potential aggravation and loss by rolling your mouse pointer over the action link, as shown above. Of course then you have to recognize that the actual URL of the link appearing in the tooltip is not to BofA, but to some other site (in this case a hijacked site of a fraternity chapter). And to save you further possible aggravation (I know you can't wait to enter that URL into your browser...but please don't) the destination is one of those "WAIT PLEASE Loading..." pages whose innards attempt to load up to three obfuscated JavaScript scripts—the same script at three different compromised sites, just in case one or more of them gets found out and taken down.
Shout it from the rooftops with me: CHECK IT BEFORE YOU CLICK IT!
Posted on August 13, 2012 at 08:54 AMAugust 09, 2012
Fake GoDaddy Emails
This morning saw the arrival of a malware lure email I had not seen before. In the tradition of so many other emails abusing various brand names, this one puts on a GoDaddy mask, trying to get you to click on a link that loads malware on unprotected machines. Here's the email:
Subject: Domain Access Verification
Dear Secure Certificate Customer,
We have received a Certificate Signing Request for your domain.
Our query of the Whois database returned your name as the administrator for the domain in the certificate request.
In order to verify the validity of this request and that it was submitted by the entity to which the domain in the request is registered, please signify your final approval or disapproval of the certificate request by clicking the link below.
https://certs.godaddy.com/anonymous/domainapproval.seam?vk=644536_f70498c2fd6
Approval of the request will enable us to continue processing your request. Failure to approve the certificate request will lead to denial of the request.
If the Verification Page requests it, please use the following Verification Key: 880754_57598
This part of our authentication process serves to ensure that only the entity/individual that controls the domain in the request can obtain a certificate for your domain.If you encounter any problems or have any questions, our Customer Support Department is ready to help, around-the-clock, seven days a week.
Customer Support:
E-Mail: [removed]@godaddy.com
Phone: 480.505.8852
Fax: 480.393.5009For further information, log in to your account at https://certs.godaddy.com.
There is no customary GoDaddy garish artwork in the message—or even what I'd expect in the way of blaring the GoDaddy brand in the message body. Perhaps this is from a template that will show up with links that appear to go to other registrars. I say "appears," because the actual links are to a hijacked web site that start you down a redirection path ultimately leading to malware installation.
I knew this message was phony baloney without even opening it because I had moved whatever domains I once registered (or inherited) at GoDaddy to a different registrar. But if this message hits a genuine GoDaddy customer who normally maintains domain registration, it could be a computer that has access to some pretty sensitive corporate stuff—exactly the kind of stuff malware would love to snarf.
Be careful out there.
August 03, 2012
Fake Reuters.com Malware Lure
Today it's the Reuters.com brand that attracted the malware delivery jerks. The message disguises itself as a confirmation of having signed up for online news delivery. Here is the full text:
Subject: Welcome to Reuters.com
Dear Reuters.com Member,
Welcome to Reuters.com!
Please click here to activate your account.
Your User ID is [removed]@dannyg.com.
Be the first to know the latest business , financial and world news headlines as they happen. Reuters.com is continuously adding new and innovative tools and products to help our users access the latest news and information -- anytime, anywhere .
Start enjoying the benefits of being a reuters.com subscriber now:
Download analyst research reports from a number of respected sources
Create research watchlists and portfolios to track stocks and other investments
Use screeners to search for stocks and funds that meet your needs
Set up alerts to track market activity , companies and portfolios
Sign up for daily newsletters to get the latest financial and world news
Access Reuters award-winning pictures and videos
Reuters.com delivers professional-grade news, opinion and analysis, providing key decision makers their "inside edge."Sincerely,
Stanley Macias
Global Editor, Reuters.com
This email is automatically generated and was sent to you to complete your registration on reuters.com.
To unsubscribe or to change your preferences, please click here. If you did not recently register on reuters.com, please contact us at http://reuters-en.custhelp.com/cgi-bin/reuters_en.cfg/php/enduser/home.php.
The message body is designed to look like a text-only version, but it's HTML and loaded with links. A few of the links actually go to reuters.com, but the majority of them—including the one for unsubscribing—goes to a hijacked web site that serves up a JavaScript redirector to the real bad stuff.
When you first get this kind of email, you might believe that the alleged sender is spamming you. When it comes from a brand name you know, you might get enraged: "So Reuters is spamming me now?" Thus riled up, you head for the unsubscribe link to tell reuters.com to which Hell to go. And that's when the malware trouble begins, without reuters.com ever having been involved.
Posted on August 03, 2012 at 09:11 AMAugust 02, 2012
Xanga Malware Lure
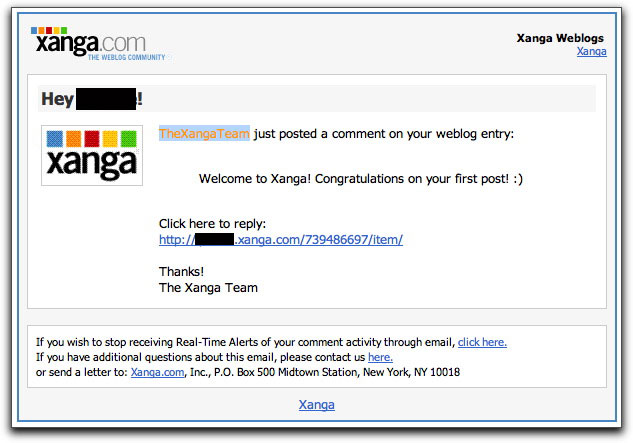
Xanga, a blogging site, is the latest lure that malware pushers are using to trick unsuspecting recipients into downloading potentially dangerous junk. The message claims to come from Xanga, advising you of a comment someone made on your blog entry:
The parts I blacked out show the username of the email account to whom the email was addressed. All of the links (including the alleged opt-out link) lead to a web site other than xanga.com, where you'll see the old "Please wait a moment. You will be forwarded..." message while obfuscated JavaScript begins you down the road to malwaredom.
The message body got pretty mangled along the way because in the one I saw, a bunch of CSS code was included in the text-only version, and rendered in my email reader. Can you say "doofus?" A quick look at the message's headers clearly shows the message has no connection whatsoever to xanga.com.
It was easy for me to suspect foul play right in my inbox list because I don't belong to Xanga. But I suspect any Xanga member might be fooled into clicking the link. I just hope those folks have antivirus software installed, or they could be in for a world of hurt.
Posted on August 02, 2012 at 09:49 AM