| Home | The Book | Training | Events | Tools | Stats |
October 21, 2009
iPhone Rip Off (Sans iPhone)
Oh boy, do we have a crook here who's gonna clean up (sad to say). Look at this turdlet:
From: "APPLE IPHONE SALES"<sales@apple.com>
Reply-To: <unlockedapple[removed]@gmail.com>
Subject: APPLE 3G 16GB IPHONE ( APPLE FACTORY CLOSEOUT SALES )FOR MORE INQUIRY CONTACT
unlockedapple[removed]@gmail.com
appleunlocked[removed]@gmail.com
PHONE: +44702[removed]BRAND NEW APPLE IPHONE 3G 16GB UNLOCKED WITH COMPLETE ACCESSORIES NEVER USED COMES ALONG WITH 12 MONTHS INTERNATIONAL WARRANTY.SIM FREE WORKS WITH ALL NETWORK .
UNIT PRICE :: $180USD
SHIPPING TYPE :: FEDEX EXPRESS AND UPS
BUY 3 UNITS GET 1 UNIT FREE
BOX CONTENT
iPhone
Stereo Headset
Dock
Dock Connector to USB Cable
USB Power Adapter
Documentation
Cleaning/polishing clotFOR MORE INQUIRY CONTACT
unlockedapple[removed]@gmail.com
appleunlocked[removed]@gmail.com
PHONE: +44702[removed]
Oh, yeah, I can't wait to do business with this guy.
First, he forges the From: field to make me believe the message originated from apple.com. Then he provides gmail contact addresses and a U.K. cell phone number. Operators are standing by at a Starbucks table, ready to take your order.
Second, the iPhone 3G is still a current model. When the time comes, Apple will find a way to close out supplies on its own, thank you.
Third, the supposed contents of the box include things that Apple doesn't include with the iPhone 3G, such as a dock and a polishing clot (or even a cloth). My god, man, can't you even copy the contents straight from the Apple Store web page? Sheesh!
Hmm, let me guess. All transactions will be by Western Union money transfer. And all shipments will never occur, because these phones don't exist. But put the words "unlocked" and "iPhone" together at an attractive price, and peoples' brains short circuit.
Posted on October 21, 2009 at 10:07 AM
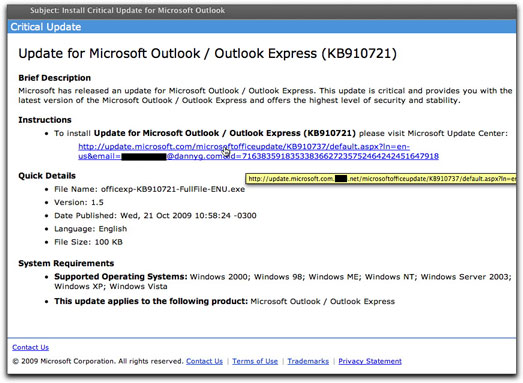
An earlier campaign to infect Microsoft Outlook users (reported back in June of this year), must have been a success, because it's back. There are some subtle differences between the two email messages, one of which isn't so funny. Here's the new one:
Among the amusing differences is that, although the name of the malware delivery file mentioned in the message (officexp-KB910721-FullFile-ENU.exe) is the same, today's message shows that it is now the new and improved version 1.5 (instead of 1.4). Oh, goodie!
As before, the domain of the infection site was born yesterday, and the originator of the campaign hopes that recipients were also. At the destination page of the link, rather than using an automatic drive-by type of installation, the new web page encourages visitors to download and install the file. Better to get the victim involved, I suppose.
What troubled me even more about this particular effort is that the hidden link looks just like the visible one, with the exception of the additional malware delivery domain inserted after "microsoft.com". In other words. What you can't see in the image above (because it's cut off) is that the recipient's email address is submitted as part of the URL. All those attributes after the "?" symbol aren't needed to visit the malware page, but it could mean that the Bad Guy is capturing valid (and gullible) email addresses in the process. Valid email addresses are one currency of the underground spam economy. A click of that link could earn you a whole lot more spam and malware email messages, while Bad Guys trade and sell your address. Put that stuff into a balance sheet, and all you're left with is "net" liabilities.
Posted on October 21, 2009 at 09:38 AMOctober 07, 2009
419er Uses Google Docs To Spread Scam [Updated]
Oh, those wily 419ers. They'll find a way to abuse every possible free service on the intertubes. Why bother paying for a botnet to do the mailing when Google will do it for you for free?
A crook using the name Chai Poon supposedly from Singapore (I'm not buying any of it) wants me to help him grab millions from a dormant bank account previously owned by the late [person with the same last name as mine]. This angle — some rich guy with the same last name as the addressee died without known heirs — always cracks me up because the email message doesn't mention the addressee's name or name of the "deceased" anywhere in the body.
At the bottom of the email message was this odd (for 419 messages, that is) addendum:
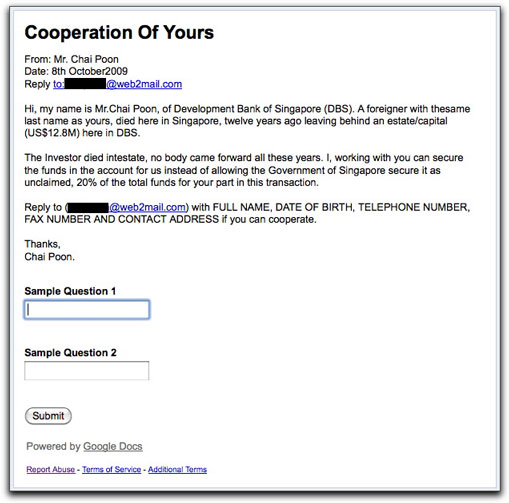
I've invited you to fill out the form Cooperation Of Yours. To fill it out, visit: http://spreadsheets.google.com/viewform?formkey=[removed]
At the end of that google.com link is the following form (whose top part is identical to the email message):
I expected the form to be something for a potential victim to fill out, with fields like the ones outlined in the message. But nooo. It's just an empty form with placeholders. You may ask, "What gives?"
The only reason this crook is using Google Docs is so that he can use gmail to send his missive to recipients. Yes, the headers reveal that the true sending IP address belongs to gmail. I'm curious to know if recipients at gmail would automatically receive these messages because they were sent from a valid gmail account. If so, that's one way to improve deliverability.
And, just in case Google shuts down his gmail account (dutifully and honestly shown in the From: field), he wants victims to contact him via a completely different free email account.
You may note that the Report Abuse link in the Google Docs page has been visited. Due to the massive size of Google, however, I doubt that takedown action will be very swift.
Update 12October2009: Five days later, the Google Docs page is still alive. Despicable, Google.
Posted on October 07, 2009 at 04:09 PMOctober 02, 2009
Medz Spammer Abusing Reader's Digest
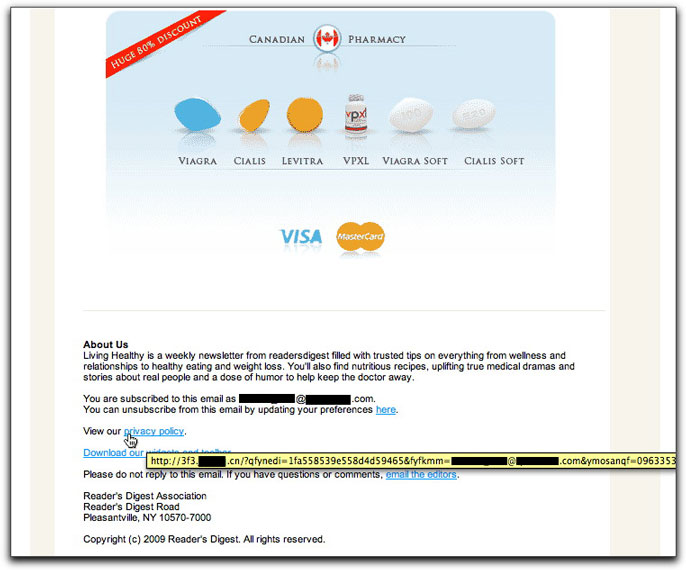
Those Canadian Pharmacy a-holes are flogging a new email piece that tries to make it look as though Reader's Digest had sent the message:
What will catch a lot of recipients off-guard is that every freakin' link in the message, including those supposedly to unsubscribe and read the privacy policy, goes to the Chinese web site. Not only that, but the links contain the recipient's email address, such that even just a click can verify your address as being active (the ad image at the top was not coded with the email address).
I'm hoping that one of these days, these guys will poke the wrong tiger once too often.
Posted on October 02, 2009 at 08:48 AMOctober 01, 2009
Medz Spammer Wants Orders NOW
There's an old sales tactic that encourages potential customers to purchase sooner rather than later. Basically, the seller must convey some sense of urgency to the purchase. "While supplies last." "Sale ends Monday." "Limited time only." Heck, I'm using the very same tactic with a sale I'm currently running on my iPhone apps.
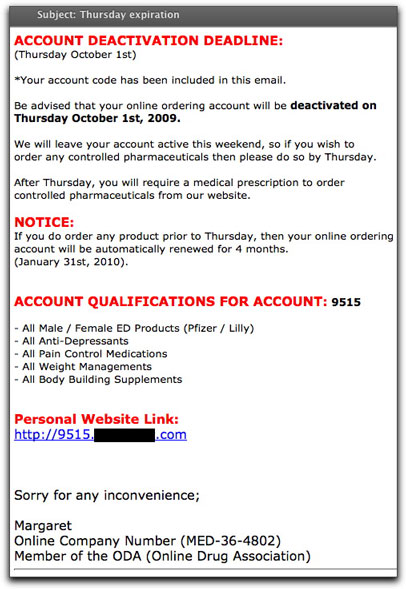
It's one thing to use this tactic with honesty. It's quite another to cook up some lie to increase the sense of urgency to buy now. That's exactly what one medz spammer is doing (a medz spammer lying...surprise, surprise!). The bogus urgency is in the form of a notice of "account deactivation deadline." I'll bet you didn't even know you had an account.
Because you don't.
In any case, the fear being peddled here is that unless you order today, any future prescription medz purchase will require a prescription. What a crock! These outfits wouldn't know what to do with a prescription if it landed in their laps.
Here's the mailing piece:
I got a laugh at the end of the message when this seller claims to be a member of the Online Drug Association. From what I can gather, there is no such organization (although there is a Japan Online Drug Association). If you Google the association name, you do get hits, but DO NOT CLICK THOSE LINKS. Finjan rates those sites as being dangerous for your computer's health.
My advice to anyone receiving this email message: Delete Now!
Posted on October 01, 2009 at 08:19 AM