| Home | The Book | Training | Events | Tools | Stats |
September 25, 2008
Malware Lure Spoofing CNN Web Site
The news flash malware lure is on the march once again. This time, it's World War III. Here's the message:
Subject: The beginning of the Third World War.Important! The beginning of the Third World War: The Russians used nuclear weapon against Georgia. According to Pentagon, the bomb of 17 megatons in TNT equivalent (which equals to 27 bombs that were used in Hiroshima) was launched at Tbilisi, the capital of Georgia, from the Russian submarine in the Black Sea. According to tentative data, Tbilisi and its suburbs in the radius of 20 km have been leveled to the ground. George Bush, speaking in the name of the whole America, made an official statement, claiming the readiness of the USA and all the NATO members for the retribution operation against Russia and the use of nuclear weapon. Click the link below to view George Bushs address: http://cnnworld.org/index.php?video_id=75198
I normally block the URLs when relating these types of messages, but in this case, the domain name is an important part of the story.
In many past posts about apocalyptic malware lure messages, I recommend visiting legitimate news sites to confirm that the message is a hoax—by the lack of any mention of the end of the world. The site I typically turn to first is cnn.com, mostly because it's easy to type.
At first glance, the domain name in the message might look believable to many. It's short and sweet.
It was also registered yesterday.
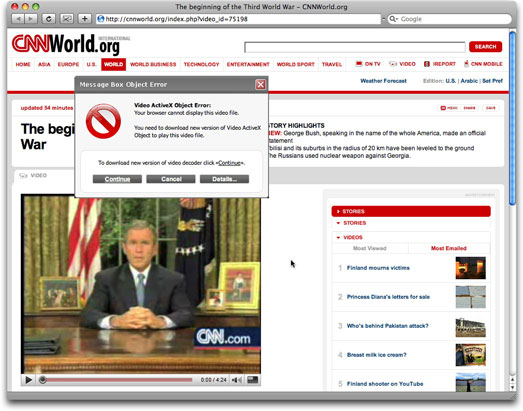
If you were to visit the URL in a web browser (DON'T DO IT!), you'd see a page that, again at first glance, has a believable look and feel of the CNN International page:
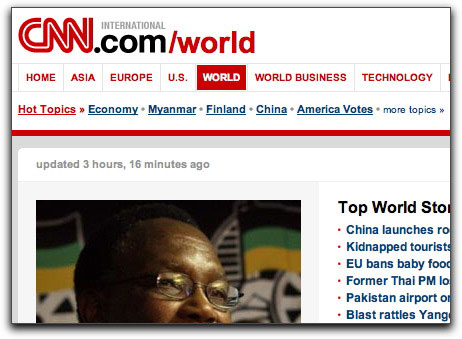
This is what the upper left corner of the real CNN International World page looks like:
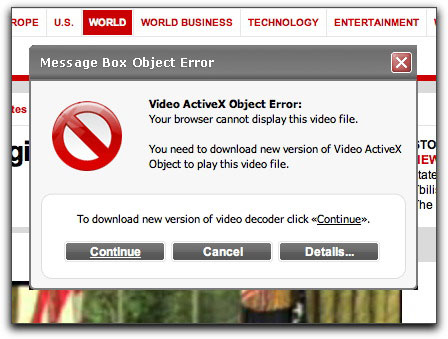
Now, onto the "dialog box" that talks about an ActiveX problem. Here it is in detail:
The alert is a Dynamic HTML absolute-positioned element made to simulate a dialog box window (it's even draggable). If you click the Details button, an alert dialog tells you to download the codec. If you click the Cancel button, you are placed into an infinite loop that forces you to agree to download the codec unless you kill the browser.
Of course, the download is no codec. It's a malware loader named codecpack.v.1.1.18.exe. Unfortunately, at this hour, VirusTotal shows a measly 17% (6/36) detection by antivirus products.
And the botnets grow....
UPDATE (2:54PM PDT 25Sep2008). The site is hosted in Iran, as are the domain's DNS servers. Domain name registrar is eNom.
Posted on September 25, 2008 at 12:09 PMSeptember 20, 2008
Do People Believe 419ers? You Bet!
My local small town newspaper has a Police Blotter section every week, where reports of various incidents are described. I'm also a radio communications hobbyist and occasionally listen to a police band radio (oh, yes, I'm one of those geeks).
Every month or so, the Police Blotter listings include some type of report of attempted or successful internet fraud, whether it be an ebay auction gone bad or a 419 email. Yesterday, while listening to the local Sheriff's radios, I heard a dispatcher sending out a deputy to someone who received an email about UPS holding a millions dollars for a citizen. The deputy didn't even have to acknowledge before I suspected a 419 attempt in the works.
This morning I got a chance to see the email because one arrived at my server. Here's the content in full:
Subject: contact ups immediately
Hello Dear,
I have register for your Cheque Draft.But the manager of Eko Bank
Benin told me that before the check will get to you that it will expire.
So i told him to cash $1.5millions united state dollars all the necessary arrangement of delivering the $1.5millions united state dollars in cash was made with UPS DELIVERY COURIER COMPANY.
This in the information they need to delivery your package to you.
DR. JAMES WALTER
EMAIL: ups_de_benin14@[well-known-free-email].com
1.YOUR FULL NAME
2.YOUR HOME ADDRESS.
3.YOUR CURRENT HOME TELEPHONE AND CELL NUMBER.4.YOUR COUNTRY
5.A COPY OF YOUR PICTURE
Sincerely JOHN BEN
(The funniest part of the message is that supposedly UPS of Benin hired a very well-educated person to handle customer service.)
But let's examine what happened here. A resident of my county received this message and gave it enough credence as either a legitimate offer or a serious enough crime to report to the local sheriff (perhaps thinking they were being specifically targeted). I didn't hear the disposition, but it's unlikely that the deputy had enough online fraud experience to evaluate the offer or know to whom a report should be forwarded.[1] It's folks like my fellow county resident—who may be new to email or haven't ever heard about 419 scams—that I fear for the most. Their hides haven't hardened to the impenetrable shells that we who receive thousands of spams a day have developed over the years. They are susceptible to online scams and are in bad need of public education about them.
-----------------
[1] Don't get me wrong. The dealings I've had with my county sheriff deputies over the years have really impressed me. Mostly Andy and none of the Barney.
September 19, 2008
Impending Doom. Click Now!
Those of us who battle spam daily can usually sniff out the purpose behind blatantly false email messages. Take this one, for example:
From: cory hardison
To: client
Subject: Your internet access is going to get suspendedYour internet access is going to get suspended
http://[removed].com
The inbox listing shows only the From: and Subject: fields. A spammer has only those two fields to make his first impression on a recipient. If it's in an inbox listing, the message has probably survived one or more automated antispam filters. But can the combination of From: and Subject: lines get past a supposedly smarter human filter? If the recipient opens the message, will the message body be sufficiently compelling to incite further action—a visit to a web site?
My first thought on the message above was that it was another impending doom message intended to lure recipients to a malware installation page. This tactic had been used years ago, but usually with the From: field forged to suggest it came from the recipient's own IT department (e.g., if the message was addressed to dannyg@example.com, the From: field was admin@example.com).
Upon safely checking the source code of the destination page, I discovered that the site was instead one of seemingly thousands of phony Canadian pharmacies (running on a bot-infected computer on the Japanese @NetHome network). This type of misdirection always puzzles me. Given the fact that the message is intended to instill fear and dread into the recipient, how is that person supposed to react to a medz spam site instead? Is he so relieved that his internet access won't be suspended that he'd better stock up on Viagra to shtup his significant other? Or is she supposed to reflect on how afraid she was and pick up some illegal (if not deadly) anti-anxiety drugs to lessen the impact next time?
Perhaps I'm just saturated by American marketing methods, but I don't understand how this type of advertising can possibly be worthwhile. If the spammer wants to go through all kinds of motions and not sell anything, let him hire Jerry Seinfeld and Bill Gates to appear in the message and at least try to entertain us.
September 18, 2008
Guarding Passwords with Sieves
I've written before about the faults of so-called "security questions" that are parts of some login credentials. These questions are intended to offer a way for the site to "assure" that anyone trying to do something sticky with the account (e.g., resetting passwords or retrieving lost passwords) is the user ID's owner. The problem, however, is that such questions are all too often very simple things about favorite such-and-such, city of birth, or similar twaddle that are likely to be data that socially-minded Web 2.0 users have posted to dozens of web pages.
Such, apparently, was the case of Vice Presidential nominee, Sarah Palin, whose Yahoo email account was reportedly cracked this week. If we can believe the self-confessed cracker's own account, all it took was a little bit of Googling to answer successfully the three challenge questions (one of which could have had a lot of possible combinations in the answer).
Certainly, the target in this case was a potentially juicy one. But even if you're not in the public eye, your login credentials to a variety of accounts could be of substantial value—if not directly monetarily, then for possible leaks of inside corporate information or even offhand comments in email that could get you fired or worse.
When I'm faced with a choice of security questions, I aim for the one whose answer is the least-possibly guessed by an internet troll. At the same time, however, I have to pick one whose answer I will not forget. Sometimes the choices are so limited, it's damned impossible to be opaque.
I'd much rather be allowed to create my own security question because there are people I've known, places I've been, things I've seen for which no internet trail exists—yet those things are so ingrained in my life's memory that I'll always remember them. They're just not important enough to others for me to broadcast in my blog or trumpet on a Facebook page.
Posted on September 18, 2008 at 04:34 PMSeptember 09, 2008
Statement of Fees 2008/09
Delivering malware via email attachments is almost out of fashion, but the approach is not entirely gone. The purpose of the email message body is to provide a believable story that entices unsuspecting recipients to double-click the attachment.
Here is today's story:
Subject: Statement of Fees 2008/09Please find attached a statement of fees as requested, this will be
posted today.The accommodation is dealt with by another section and I have passed
your request on to them today.Kind regards.
Franklin
The attached file is named Fees-2008_2009.zip. Unfortunately, at this hour, VirusTotal reports a mere 33.33% coverage (12/36). A lot of major antivirus makers don't report this file as being bad.
And that's bad.
Posted on September 09, 2008 at 10:03 PM
I suppose lots of people list themselves with job-finding sites. From what I can tell, there are also a number of web sites that have the name CareerBuilder in them, from dot-com to Inc. Thus, when a message with the following Subject: line lands in your inbox, a lot of recipients are likely to notice:
From: James Morgan / StandardP Inc
Subject: Job Alert From CareerBuilder Inc
Here's the whole pitch:
Dear Potential Employee You have been contacted as a potential employee who has registered on one of the Websites owned by CareerBuilder Inc.
StandardP Inc is looking to fill Entry Level Payment Clerk Positions.
Full paid training will be provided , full time and part time positions
are available. Good communication skills and responsible personality
is a plus. Second language is not necessary but a plus!
StandardP Inc is a leading provider of business process outsourcing
services including accounts receivable management, customer relationship
management, and other services.Principle Responsibilities:
* Process all work on a daily basis as described in training and
at direction of Management.
* Process all work in priority order.
* Balance at a batch level as well as balancing the data path/directory
at EOB each day.
* Responsible to keep all pertinent back up to substantiate payment
posting as necessary.
* Responsible for organizing backup and archival information as described
in training.
* Responsible for reconciling any differences found in balancing
at a batch level as well as at EOB.
* The job can be done from your own home however employee is responsible
to be present on last day of each month for Mandatory Month End Close
at your local office.Requirements
Qualified Candidates Should Possess:* High School Diploma.
* Some PC skills.
* Excellent written and oral communication skills.
* Ability to work independently and in a team setting.
* Ability to uphold highest level of confidentiality.
* Ability to work in a multi-tasked environment.
* Ability to accommodate schedule as listed below.We offer a competitive salary and comprehensive benefits package,
paid time off. If you have the background we seek and are looking
for a position in a dynamic, fast paced organization with career growth
opportunities, please submit your resume. Interested candidates only,
no third parties.
If you are interested please email at [removed]@live.com to receive
further information about the positions available and our company.James Morgan
Direct manager
StandardP Inc
What the ad isn't telling you is that the post is for a Money Launderer, first class. Somehow, that terminology didn't make it into the job description. The same, or similar, ad for "StandardP Inc" has appeared in blog spam postings and even (temporarily, at least) in some free job posting sites.
I giggle at the line about a second language being a plus. Which language, I wonder? Russian? Romanian?
An added teehee comes from the usage of a free live.com email address. Now, that shows a class act for any company trying to hire employees.
It's easy for me to spot bogus offers like these. First of all, to suggest, as this message does at the top, that I have registered at a career-related web site is a joke. I left my last 9-to-5 j.o.b. in March of 1981—I'm determined to make a go of this independent contractor/freelance thing one way or another. Second, the messages were addressed to an address of mine that had been compromised some time ago at someone's malware-infested Windows PC. That address is circulated widely among botnet patrons. The two copies I saw came from bots in Russia and Dubai.
Other recipients, however, may not be as circumspect, especially if they are desperate for work, or looking for that work-at-home opportunity to earn some extra income. Although a mule and an ass are separate animals, you'd be the latter upon becoming the former.
Posted on September 09, 2008 at 04:37 PMSeptember 06, 2008
OMG! A Spammer Lied!
A penis pill purveyor has been sending out messages that have two short sentences of clearly visible text, all of which is a clickable link. That text reads:
Your IT department has been paid to allow us to send you these mails. Check out the results
The messages also include light grey hash-busting text in the hope of bypassing whatever spam filtering "your IT department" has installed to keep this type of crap out of your inbox.
I wasn't born yesterday, but the domain for the link was. In a double joke, the registrant used a domain registration service that doesn't reveal any information about the registrant beyond his name: SUNMM in this case. As if spammers use real info in their domain tasting scams!
No one reading this blog, of course, would believe for an instant that this spammer had greased the palms of the IT department to get past the barricades. But it wouldn't surprise me to find non-techie employees at decent-sized companies taking this at face value. They either fear or dislike the IT department. In the first case, they obey anything that has an "IT" stamp on it—fake or real—and will immediately click the link; in the second case, they'll get angry that those nerds in the IT department are getting rich off spammers, and will check out the link to see what the pitch is all about. If the spammer—the one doing the mailing, not necessarily the one selling the pills—gets paid for hits on the spamvertised web site, he wins. He now has verifiable statistics that his botnet emailing system works (delivering suckers potential customers), meaning he can pitch it to other sellers.
Many of these messages naturally arrive at servers like mine, where I am the IT department. If only they'd offer me some coin to spam me. I could use the dough, and I have Dave Null's inbox ready to receive in large quantities.
Posted on September 06, 2008 at 10:41 AMSeptember 01, 2008
Malware Spam for a September Morn
Ah, it's a new month, and here in the U.S., we have the Labor Day holiday. Except for those whose holiday is being stolen by the Gustav hurricane, there will be lots of picnics, ball games, and end-of-summer parties. In the meantime, your email inbox is filling up with the usual crappage.
On the malware lure front, a long-running e-card scam is continuing, as the perps take over additional web sites to host their downloadable deliveries. New this morning are a couple of strange malware lure samples whose Subject: lines drop the names of—ta-da—Obama and McCain. The actual Subject: lines I've seen don't make much sense, but what else is new?
- Obama Announces for President -- In Hit Show '24'
- McCain, Obama: Cosmo Cover Also Tasteless, Offensive
- Obama Promises Change for a Nation, Change For a Twenty
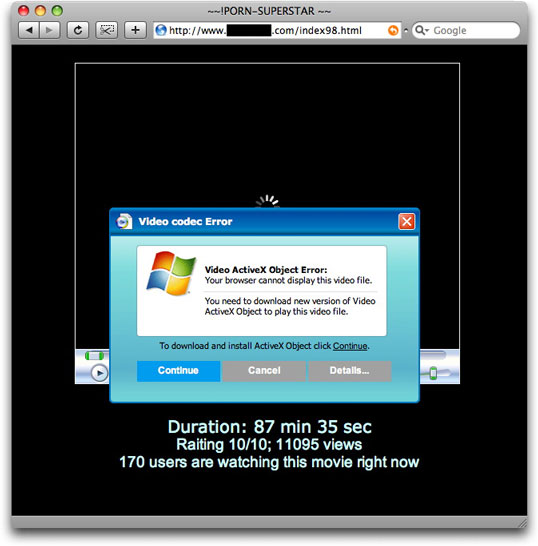
The messages encourage you to follow a link to a hijacked web site, where the crooks have inserted a page named index98.html. A visit to the page automatically downloads video98.exe (for which VirusTotal shows a very high recognition rate). Whether or not the auto-download works, a visitor to the page (why are you doing that?) sees the following:
What looks like a dialog box is actually an absolute-positioned div element—a Dynamic HTML technique used by some to create content that is draggable around the browser window. Unlike a real dialog box, however, if you try to drag this one beyond the edge of the browser window, it is clipped by the browser window. In the meantime, the image of the video viewer—and that's all it is: an image—is an animated .gif image with the spinner spinning away, as if the player is "tapping its foot" waiting for the visitor to act.
What strikes me most about this page, however, is the choice of page title, which appears in the browser window's titlebar. It's either a leftover from some other campaign, or it's the final "grabber" to encourage visitors to download that malware loader...I mean, video codec.
But the email messages were about politics. As if politics and porn are somehow related....
Posted on September 01, 2008 at 09:45 AM