| Home | The Book | Training | Events | Tools | Stats |
October 29, 2010
Spamming for Electronic Cigarettes
My spam folder today was inundated by lots of messages hawking an electronic cigarette (Wikipedia article on the controversial subject). My concern isn't necessarily about the product, but rather about the spamvertiser for this campaign.
The links I've seen are to domains registered yesterday (literally) through a Chinese registrar, and none of the domain names refer to the brand name being promoted: E-Lux. That's the company name, we're supposed to believe. We're also supposed to believe — according to the raft of icons and badges at the bottom of their web site pages — that E-Lux is all square with the Better Business Bureau, and the site is all VeriSign Secured and McAfee Secure.
I call BullShit.
The BBB has no listing for any company with or near that name.
This spam flood is coming from the same guys who peddle other medz and lure folks to malware distribution sites (or attach malware). Aside from whatever medical risks one would take from these products (on the bold assumption that you'd even see anything make it through U.S. Customs), divulging your credit card info to these guys could set you on a path to credit card and identity theft.
That's not going to help you stop smoking.
Posted on October 29, 2010 at 09:23 PMOctober 18, 2010
About Copying Email URLs
The other day the U.S. Postal Service sent (via snail mail, obviously) a pamphlet educating recipients on how to avoid becoming fraud victims, including Internet fraud. One of the "Play It Safe" recommendations is:
Never click on a link inside an e-mail to visit a Web site. Type the address into your browser instead.
The first sentence is spot-on. The second, however, needs to fill in some important gaps.
It's a well-known fact that people make mistakes — especially typing mistakes. Crooks know this, too, and do their best to profit from that human flaw. If you're in a hurry to visit one of your normally trusted financial sites, you can easily hit a neighboring key along the way. In earlier days, crooks would gobble up domains whose characters were adjacent to those that spell "paypal" and domains for major banks. I suspect this type of activity still goes on whenever a new "hot" domain name gets publicity. Any real site that has login credentials is worth mimicking with a lookalike site to capture a valid username/password pair (that is likely used on other sites of more value).
Even though I'm normally a good typist, I don't trust myself when it comes to visiting sites associated with anything of value to me (like passwords of any type). Sometimes you have to do the typing, as in the first time you visit your bank's web site. But when you do so for that first time, do it slowly and carefully; check the URL that you typed before hitting the Enter/Return key. Once you feel comfortable that you are at the genuine site (and before you log in), create a bookmark/favorite for that page. Thereafter, use only that bookmark to reach the site.
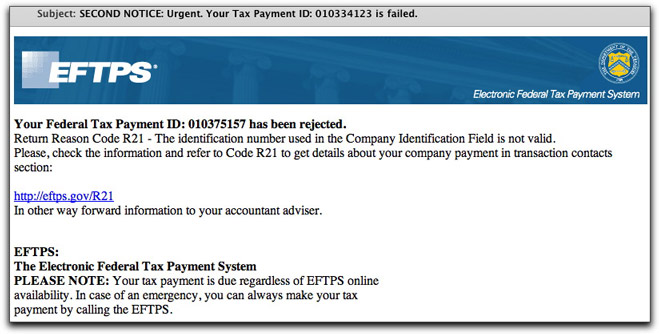
As I was thinking about all of this, it occurred to me that some anti-fraud promoters might suggest copying a link in an unsolicited or suspicious email message and pasting it into the browser's Address field. Yet another round of phony IRS EFTPS spam started arriving today, showing a visible link that looks convincingly real:
Subject lines I've seen:
Subject: We Decline Your Federal Tax Payment ID: 0103767647.
Subject: Your EFTPS Tax Payment has been reejcted. Report ID: 010376138
Subject: Your Tax Payment ID 0103725687 is failed. Udpate Information.
And the message:
Today's series of messages have numerous intentional spelling errors (which vary from message to message), perhaps intended to push recipients' curiosity buttons ("How could the IRS be so sloppy?"). The visible link looks official enough, so I wondered if recipients would try to copy and paste the URL. Copying a live URL can take a bit of rodental dexterity. Unlike inline text, you can't easily click on the text to select it without activating the link. I then wondered if users would try to right-click (or whatever alternate click method they use, including on the Mac) to see if a context-sensitive menu could help.
If you right-click on a link, one of the menu choices is something like "Copy Link." What do typical users think that menu choice does? I'd wager they believe it copies the visible link into the Clipboard. In truth, however, the command copies the hidden URL coded into the HTML element — which could be anything. If you then paste that copied link into your browser, it's as good as directly clicking the link in the email message. D'oh!
Posted on October 18, 2010 at 10:50 AMOctober 08, 2010
Another Fake IRS Email Message
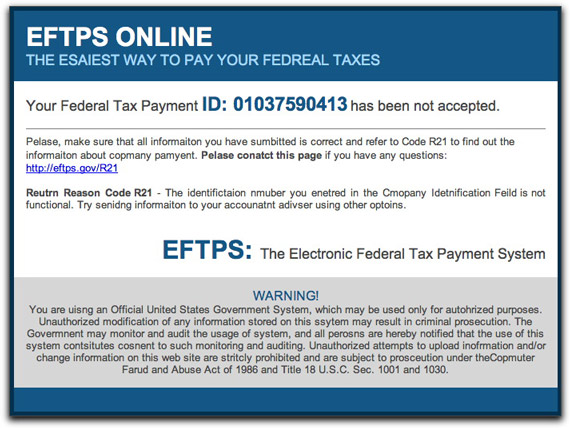
Today's load of crap comes courtesy of someone impersonating the Internal Revenue Service's Electronic Federal Tax Payment System (EFTPS). The real one is a system set up to facilitate electronic submission of tax forms and payments. The message today claims to be of an urgent nature:
The visible link is to the correct domain, but the actual URL of the link is to a hijacked web site. There, you will be immediately redirected to another domain that was registered yesterday (literally), and is currently being hosted in (drum roll)...Russia.
You need a Windows PC to visit the bogus site, and I don't have one available at the moment to throw into the volcano. This leads me to believe the site's intention is to load malware onto visitors' PCs, rather than phishing for login credentials. Unauthorized access to one's EFTPS account could cause harm by tampering with account information, but I think that the crooks would welcome all operating systems into that mix. Even so, the login credentials could be valuable because it's pretty likely they're the same ones used for other financial web sites.
Whatever.
As I continue to promote: The more dire and urgent an unexpected email messages sounds, the more likely it's a complete fake. If the IRS needs to contact you about something serious, it won't come in the form of an email that doesn't even mention your name (or your correct tax ID).
Posted on October 08, 2010 at 10:45 AMOctober 06, 2010
Google Resume Malware Lure
I left my last job in 1981, so I knew instantly that this email message was not 4realz. But lots of folks are looking for work, and when a message claiming to come from Google Staffing arrives, you probably pay attention.
And that's bad.
Here's the message, with a From: field showing resume-thanks@google.com:
Subject: Thank you from Google!
[Google logo]
We just received your resume and would like to thank you for your interest in working at Google. This email confirms that your application has been submitted for an open position.
Our staffing team will carefully assess your qualifications for the role(s) you selected and others that may be a fit. Should there be a suitable match, we will be sure to get in touch with you.
Click on the attached file to review your submitted application.
Have fun and thanks again for applying to Google!
Google Staffing
The attachment (mine was named CV-20100120-112.zip, as in Curriculum Vitae) has decent antivirus coverage (68%, including all brand-name AV tools), so that should help slow the success of this particular Trojan. The sender went one extra mile to try to trick techie recipients who might look into the message's header. He forged the sending domain to read "google.com", but the IP address belongs to someone else entirely. Any techie who fell for that wouldn't make it through the first interview if they should ever really apply for a Google job.
Employment continues to be a HUGE avenue for spammers, scammers, and crackers. Any time you receive an unexpected email regarding a new job, you should deploy all defensive shields immediately.
October 03, 2010
Spam For a Scam
Look at this unsolicited email offer for low-priced Apple merchandise:
Subject: BRAND NEW APPLE i-PHONE 4G/ i-PADS/i-MAC: ORDER 2 GET 1 FREE
COMETS TECH UK is An Authorized and Registered Company with APPLE INC,We are offering APPLE i-PHONE AND i-PADS PC, BRAND NEW AND UNLOCKED,Factory Sealed Boxes,complete Accessories and 1 year Manufacturer’s Warranty
and Guaranteed to work with all GSM Carrier Worldwide.
http://www.apple.com/iphone/
APPLE i-PHONE 4G 32GB = $400
http://www.apple.com/imac/
Apple iMac 27" 2.8 Quad Core i7 8GB = $1200
Apple iMac 21" 2.8 Quad Core i7 8GB = $950
free shipping worldwide
http://www.apple.com/ipad/
APPLE i-PADS PC 16GB/3G with WiFi = $450
APPLE i-PADS PC 32GB/3G with WiFi = $550
APPLE i-PADS PC 64GB/3G with WiFi = $650
free shipping worldwide
ORDER 2 Pcs Get 1 FREEALL OUR APPLE i-PADS/i-MAC ARE ORIGINAL FROM APPLE INC USA AND THE i-PHONES ARE 4G UNLOCK,OPEN TO ALL NETWORK WORLDWIDE..
We ship worldwide via FEDEX,UPS and DHL in 3/4 days.
FOR MORE ENQUIRIES AND FAST RESPONSE PLEASE EMAIL US
Comets-Tech Lmtd (UK)
Dominion Court,41 Station Road,
Solihull,Birmingham B91 3RT, UK
Aside from the too-good-to-be-true angle with a two-for-one sale, there are a number of more subtle clues that this is a scam. First, there is no way in hell that Apple would "authorize and register" a dealer to sell goods at discounts of such magnitude (and wouldn't a UK dealer be "authorised"?). Nor would Apple allow any true dealer to flagrantly screw up its trademarks (or even use them without acknowledgment). There is no such thing as an "i-PHONE" or "i-PAD" from Apple. Additionally, the current iPhone model is iPhone 4, not "i-PHONE 4G".
Last, the return email address is a free email account at live.co.uk. If you dig deeper into the email message header, you discover that the email originated from a (presumably botnetted) computer in South Africa.
I'm sure these scam artists will be quick to accept your credit card info. From there, they'll either defraud the credit card company or hijack your account (cue nightmare for you). Just don't keep watch for the Fedex, UPS, or DHL van because it's never coming.
Posted on October 03, 2010 at 11:31 AMOctober 01, 2010
Spooforama [Updated-2]
Whenever you receive an unexpected email message whose content gets your blood a-boilin', that's when it's time to crank up your Suspicion Machine 3000 to eleven. That's even more the case when the email message appears to come from an individual or company you know (and perhaps love). I have two recent cases to report.
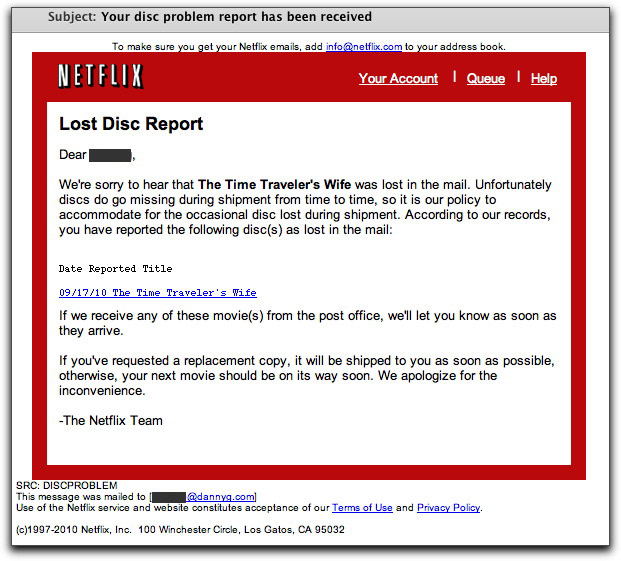
Exhibit One tries to look like a message from Netflix. The Subject: line reads "Your disc problem report has been received." It has been a long time since I've had a Netflix disc problem, so I don't know for sure what their current problem response email messages look like. But they could certainly look like the one I received:
So, this message claims that I had reported a lost copy of "The Time Traveler's Wife." The chance that any recipient of this email message had actually reported this DVD as being lost in transit approaches zero. And that's exactly what the sender hopes. He wants the recipient to react by thinking, "Hey, I didn't report that DVD lost. Hell, I haven't ever had that movie in my queue!" What does the sender hope for next? Why, for the recipient to click the link to investigate.
And then the trouble begins.
The link, of course, is not to Netflix, but to a page inserted into a hijacked web site. The page is named 1.html, a temporary fingerprint of one of the malware/spammer gangs.
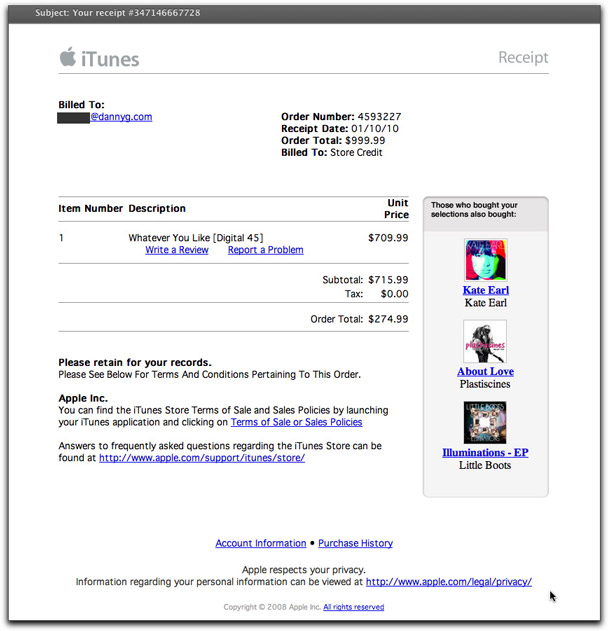
Exhibit Two attempts to get your adrenaline flowing by posing as an iTunes receipt for something costing hundreds of dollars:
The originator of this pitch isn't quite as clever as the one who assembled the faux-Netflix message. This looks nothing like the real receipts that iTunes sends out. Additionally, the dollar amounts (which appear to be filled in with random numbers) don't even come close to adding up.
I'm thrilled to report that the domains for the links I've seen — a batch of gibberish .info domains created way back earlier today — have all been suspended. Kudos to whoever is responsible for the quick action. Therefore, I can't tell if these links were to plain old phishing sites (to capture one's Apple ID login credentials) or to a malware/spam network.
The quick takedown work won't stop this or other miscreants from composing future email messages that attempt to trick recipients into action. That's the key, folks. The Bad Guys want you to react to their message content and then act by clicking, opening, or installing. Any message that asks for these kinds of actions deserves special scrutiny.
UPDATE 1Oct2010 1330 PST: The campaign continues, but the link is now to a single medz spam site, apparently hosted by a bulletproof hoster in Russia.
UPDATE 2Oct2010 0915 PST: Messages continue to flow with the same type of Subject: line and outer content wrapper. But the bulk of the body is now a direct medz ad. I've seen this sequence of content changes over the course of a couple of days before. The links are to a different set of .info domains (which have not been shut down), from which visitors are redirected to the medz spam site mentioned in yesterday's update.
Posted on October 01, 2010 at 10:00 AM