| Home | The Book | Training | Events | Tools | Stats |
October 01, 2010
Spooforama [Updated-2]Whenever you receive an unexpected email message whose content gets your blood a-boilin', that's when it's time to crank up your Suspicion Machine 3000 to eleven. That's even more the case when the email message appears to come from an individual or company you know (and perhaps love). I have two recent cases to report.
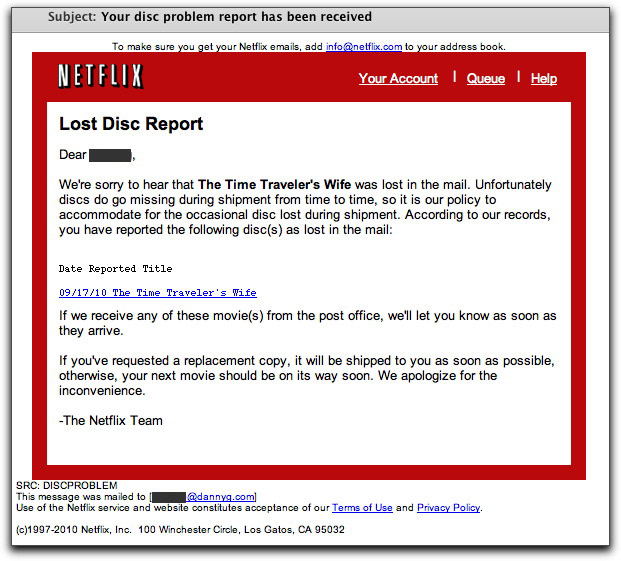
Exhibit One tries to look like a message from Netflix. The Subject: line reads "Your disc problem report has been received." It has been a long time since I've had a Netflix disc problem, so I don't know for sure what their current problem response email messages look like. But they could certainly look like the one I received:
So, this message claims that I had reported a lost copy of "The Time Traveler's Wife." The chance that any recipient of this email message had actually reported this DVD as being lost in transit approaches zero. And that's exactly what the sender hopes. He wants the recipient to react by thinking, "Hey, I didn't report that DVD lost. Hell, I haven't ever had that movie in my queue!" What does the sender hope for next? Why, for the recipient to click the link to investigate.
And then the trouble begins.
The link, of course, is not to Netflix, but to a page inserted into a hijacked web site. The page is named 1.html, a temporary fingerprint of one of the malware/spammer gangs.
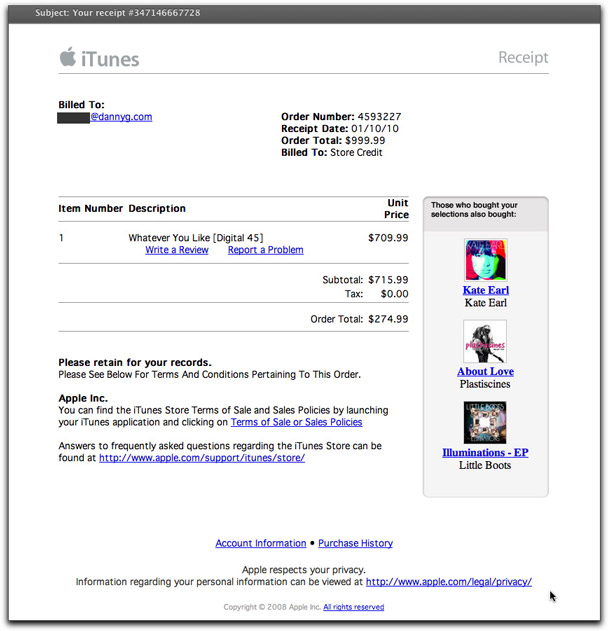
Exhibit Two attempts to get your adrenaline flowing by posing as an iTunes receipt for something costing hundreds of dollars:
The originator of this pitch isn't quite as clever as the one who assembled the faux-Netflix message. This looks nothing like the real receipts that iTunes sends out. Additionally, the dollar amounts (which appear to be filled in with random numbers) don't even come close to adding up.
I'm thrilled to report that the domains for the links I've seen — a batch of gibberish .info domains created way back earlier today — have all been suspended. Kudos to whoever is responsible for the quick action. Therefore, I can't tell if these links were to plain old phishing sites (to capture one's Apple ID login credentials) or to a malware/spam network.
The quick takedown work won't stop this or other miscreants from composing future email messages that attempt to trick recipients into action. That's the key, folks. The Bad Guys want you to react to their message content and then act by clicking, opening, or installing. Any message that asks for these kinds of actions deserves special scrutiny.
UPDATE 1Oct2010 1330 PST: The campaign continues, but the link is now to a single medz spam site, apparently hosted by a bulletproof hoster in Russia.
UPDATE 2Oct2010 0915 PST: Messages continue to flow with the same type of Subject: line and outer content wrapper. But the bulk of the body is now a direct medz ad. I've seen this sequence of content changes over the course of a couple of days before. The links are to a different set of .info domains (which have not been shut down), from which visitors are redirected to the medz spam site mentioned in yesterday's update.
Posted on October 01, 2010 at 10:00 AM