| Home | The Book | Training | Events | Tools | Stats |
November 29, 2017
Bad Old Spam Days
Anyone who follows this blog knows I completely detest any kind of fakery, lying, and deceit. Olde tyme spammers used those tactics with abandon. Unfortunately, the CANSPAM law in the U.S. did not do nearly enough to get bad actors out of our inboxes, especially when the sources are outside the U.S.
I received the following message today, seeming to be a throwback to days gone by when spammers didn't care about their branding or honesty, because their goal is simply to get something of value from recipients without them even noticing it.
SUBJECT: Requesting Your Approval
DivTECH LLC wants to send you emails, but we need your permission before we do so.
We value your time and privacy, and will only be sending information that is relevant to your work. Messages could be in the form of promotions, updates, white papers and other awesome content.
However, we understand if you do not want to receive such emails. If this is the case, simply click on the blue "Opt Out" below, and we'll make sure that your email address is taken off the list.
Thank you for your time!
The information contained in this message is confidential. If you have received this message in error, please delete it or Opt Out if you no longer wish to receive my emails.
If needed, you can reach us at DivTECH LLC, 181 Union St., South Weymouth, MA, United States, 02190. For my records, I show your contact information as: [removed]@dannyg.com.
If this message had been framed according to the Subject: line and first line of text, I would take it to mean that they are simply asking me to confirm if I wanted to receive their messages, and doing nothing would stop it. But, as you see, the actual mechanism is the opposite. If I don't "Opt Out", I'll continue receiving their messages. BUT, the link of the Opt Out button leads to a completely different domain created just a couple of weeks ago. I have no idea where that opt out request ultimately goes. But I know it will confirm my address as being valid, ripe for additional spamming by untold hordes of spammers who rent the list of verified addresses.
I believe the mailer may have hijacked the DivTECH LLC identity as a cover for the mailing. The company does (or did) exist, and has a Facebook page that hasn't been touched since 2014. The link winds its way to a Canadian-owned domain (supposedly).
In any case, lots of recipients of this message will click on the link in the hope that they'll be opted out of this mailing. Nothing could be further from the truth.
November 08, 2017
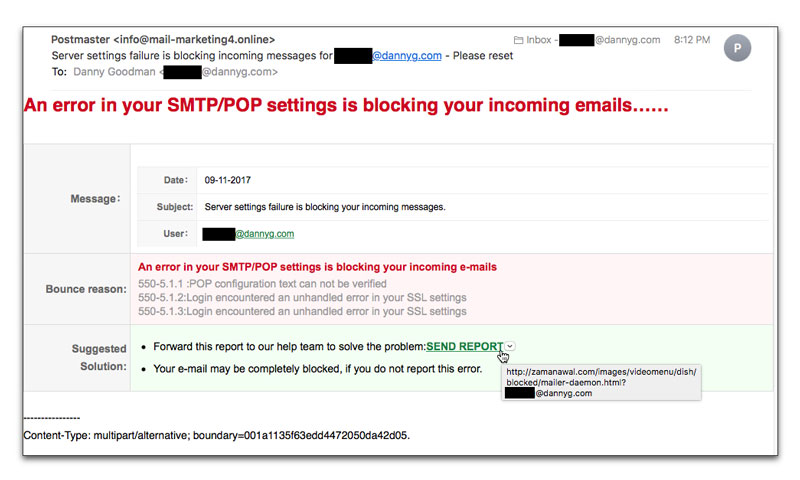
Fake Email Server Settings Warning
Aside from a little formatting ugliness, the following email is an unfortunately decent attempt to phish for your email password (and, then, conceivably, to your account on the server and further server intrusions from there).
The Subject: line is pretty threatening:
Server settings failure is blocking incoming messages for [redacted]@dannyg.com - Please reset
To many typical computer users, the "Bounce reason" data would appear as gobbledygook, but to someone who also manages the personal or business email server (perhaps at your domain's ISP), it's very plausible gobbledygook. But even if you don't know what it means, the message goes on to provide a convenient link to follow to send a report to the mail team so they can fix the problem.
And that's where you get into big trouble.
If you follow my forever guideline to rollover any link before clicking it (something that would have saved John Podesta from a dumpster full of trouble), you'll see the destination URL is something you probably don't recognize. The URL includes your email address (the one used to get this message to you in the first place), so that if you follow the link, you reach a similar-looking page in your web browser that pre-fills a field with your email address. There's no magic to this feat: Any 12-year old with a little bit of JavaScript experience could do it. But the other, blank, field requests your email password. Fill that in and submit it, and you're toast.
BTW, there is another telltale sign to this American that the message comes from someplace other than my American-based ISPs: The body specifies a date in the dd-mm-yyyy format, rather than the expected mm-dd-yyyy format. The date was filled in by the crooked email bot sending the email from somewhere in the Eastern Hemisphere. I know this because my email server processed the message in the U.S. late in the evening of November 8.
Be careful out there.
Posted on November 08, 2017 at 09:36 PM