| Home | The Book | Training | Events | Tools | Stats |
November 29, 2008
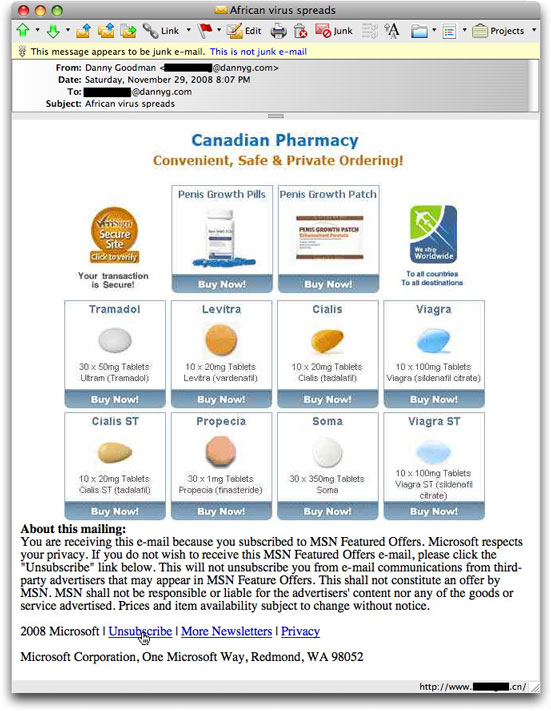
Canadian Pharmacy in Full Deception Mode
How long will it be before these "Canadian Pharmacy" a-holes get their comeuppance? Here's a sample of one of their latest:
Most of the crap in this message has been in the recent flood that I wrote about in my previous post. This includes the From: field forged with my own name and address, as well as the abuse of the Microsoft tag at the bottom making it sound as though the recipient begged for the message because he or she is subscribed to MSN Featured Offers (even when not).
Virtually all of the recent "self-addressed" spam I had seen from these guys had used Subject: lines such as:
- RE: Message 32779
- RE: Order 88514
- Your Order
Now the Subject: lines are getting way off-topic, veering into the same type of sensational headlines that bot-net malware lures have used:
- African virus spreads
- Barack Obama's Victory Speech
- mass kidnapping
- Gunmen remain on the East coast
The bot-net senders and Canadian Pharmacy senders pull from the same address lists (including my spamtrap addresses), so it's clear to me that they're one in the same. When they need to replenish their army of zombies to send out more medz spam, they switch over temporarily to sending out malware lures.
It obviously takes deep pockets to pursue the global tangle that these jerks use to keep their underground economy flowing. I have my doubts that regular law enforcement, on its own, can do the trick. But that so many of these recent messages abuse Microsoft's brand name and services gives me hope that the spammers might poke the Redmond bear one too many times. If any organization has the stake and resources to hunt these guys down and—with the help of law enforcement—string these guys up, it should be Microsoft. I know where I want Microsoft to go today.
Posted on November 29, 2008 at 09:28 PMNovember 26, 2008
Sending Spam to Myself
I've heard that some sleep aid medications can cause takers to do weird things in their sleep, such as emptying the refrigerator into their mouths and even going for a drive. There are no such tablets in my house, so apparently I'm not the one responsible for the slew of spam in the last couple of days that arrived at my server sent From: Danny Goodman. This type of thing has happened occasionally in years gone by, but recent arrivals have seemed more like a flood.
Much of the self-addressed spam was for that wretched "Canadian Pharmacy." Some others were written in Italian, pushing a work-from-home scam from which I supposedly can earn 584-1123 euros per week (how precise!) if I respond to a gmail.com address.
Sales trainers tell students that people like to hear the sounds of their own names. The opposite is true when some robot sends spam in your name. You never know if just the one message you received has your name and address on it, or if tens of thousands of messages will cause you to be labeled a spammer in the minds of recipients who don't understand that From: fields are easily forged.
Seeing the list of spam with my name and address in the From: field reminds me of the schoolyard bully who grabs the wrist of an unsuspecting classmate and repeatedly hits the victim's face with the victim's own hand, while saying each time "Stop hurting yourself." At least I'm comforted knowing that I haven't been sending email in my sleep...which is good because Canadian Pharmacy has no pills for somnospamnia.
Posted on November 26, 2008 at 08:50 AMNovember 18, 2008
Tax Refund Scam - O, Canada!
The U.S. Internal Revenue Service isn't the only taxing authority to be abused by scammers (here, here, and here). The Canadian equivalent, the Canada Revenue Agency, is also on scammers' hit lists.
Here's one I saw today:
From: security@cra-arc.gc.ca
Subject: Canadian Revenue Agency - Online Refund Form
Canada Revenue Agency
Online Refund Form
After the last annual calculation of your fiscal activity we have determined that you are eligible to receive a tax refund of 386.00.
Please submit the tax refund and allow us 3-9 days in order to process it.
A refund can be delayed for a variety of reasons. For example submitting invalid records or applying after the deadline.
To access the form for your tax refund, please click here>>
Copyright Canada Revenue Agency. All rights reserved. www.cra-arc.gc.ca
Astute Canadian recipients would be suspicious with the Subject: line, which refers to the agency as "Canadian," rather than the start of its official name, "Canada." The body of the message gets it right.
The link, of course, was not to the agency, but to a domain originally registered through EstDomains (ugh) by a person claiming to be in Russia.
Although the site was quickly taken down, the template obviously exists for repeat transmissions of this phishing spam when they set up the site elsewhere. While the CRA may, indeed, find that a citizen is due a refund, the announcement won't come in the way of an email message with absolutely no reference to the recipient's name as it appears on the tax return. For what it's worth, in the U.S., the IRS simply mails you a check or direct deposits a refund before you're even aware that you were due the refund. There is no form to fill out to claim your refund. They have all—and I mean all—necessary personal identity information without you having to supply an ounce of data in some stupid form.
Posted on November 18, 2008 at 08:05 AMNovember 17, 2008
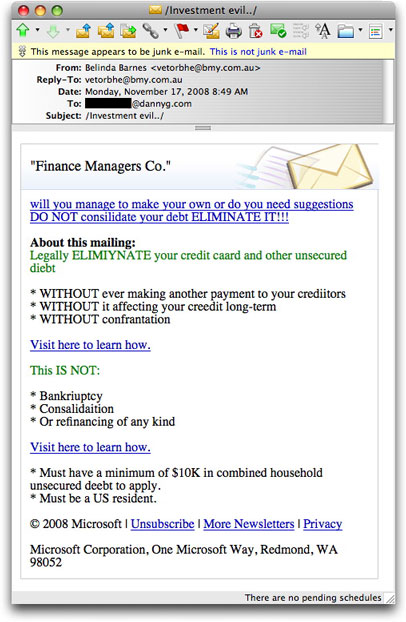
Weaving Tangled Webs
Oh what a tangled web we weave,
When first we practise to deceive!
-- Sir Walter Scott, Marmion, Canto vi. Stanza 17
It starts with a spam message that appeals to a potentially desperate audience of people hounded by personal debt:
At first glance, it looks to have some blessing from Microsoft, despite the intentional misspellings to get the message past some content filters. All of the links—including those at the bottom that look like they'd point to Microsoft—take you to a domain registered a few years ago to an address in Saudi Arabia. The domain, by the way, is flagged from here to Timbuktu as being a baaad place by multiple malware-detection services (e.g., Finjan).
But the links in this email message (they're all to the same URL) are to a page within that site, a page that redirects attempted visitors to a different domain that was registered a couple of days ago to someone claiming a Moscow, Russia address. The page hosted there shows no company name or other identity, but serves as a lead-generation page for (possibly) debt "elimination" services. A form on the page asks for minimal personal information, and no account numbers or passwords. It does say, however, that by submitting the form, you grant permission to be contacted, including by telephone.
Anyone filling out that form would be dealing with yet another deceiver weaving a tangled web. This page includes three logos at the bottom boasting protection by VeriSign, review by Trust*e, and compliance with the CAN-SPAM Act of 2003. Absolute lies on all three counts!
These are tough financial times for lots of families. That spammers and scammers target the most vulnerable is, to all but crooks, unconscionable. Be careful of any lifeline thrown your way via spam: The other end of the line is most likely tied to an anvil.
Posted on November 17, 2008 at 09:41 AMNovember 16, 2008
Falling Hard For a 419 Scammer
Just a couple of months ago, I wrote that people still fall for 419 scams. A sad story out of Oregon proves the point to the tune of $400,000 (TV news video story).
A couple of things about this tale are worth noting.
First, the victim is a registered nurse and sign language interpreter. While she may not be savvy about Internet scams, she is no illiterate rube. Once she was on the hook with the scammers, no one, including local law enforcement officials, could dissuade her from trying to cross the finish line. This seems to be the case when most 419 victims finally fess up in public to their situations. I've known of many cases where professionals (physicians, attorneys, university professors, successful business people) get caught up in the scams. It's almost as if the smarter they are, the more immune to scamming they feel—when in truth, their greed knows no intellectual bounds.
And, no doubt about it, the scammers are quintessentially skilled in being persuasive and supplying phony documents, emails, and photographs to keep the victim on the hook. It's like when I see film of deep sea fishing: once the marlin takes the bait, the skilled fisherman knows how to reel in a bit, then let the line out to give the fish a chance to think it's winning, and then reel in some more, each time reducing the overall distance between fish and boat. Unless the line breaks, the marlin loses every time.
A companion written article by the TV reporter was published online and open to comments, which brings me to my second point worth noting. A vast number of commenters couldn't believe that anyone falls for these "obvious" scams anymore. They are chest-thumpingly proud that they automatically delete these messages, and assume that everyone else does, too. It is simply beyond their comprehension that anyone would respond to a 419 message...or open an email attachment from a stranger.
Therein lies a significant problem in trying to educate the world about potential hazards that arrive by way of messaging (email, IM, Skype, etc.). Those who deal with this stuff on a daily basis—and can sniff out a scam before the message arrives in the inbox—can't even imagine anyone falling for such "obvious" frauds. "Education, shmeducation! Nobody falls for that stuff anymore!"
One Oregon woman has 400,000 reasons to disagree.
Posted on November 16, 2008 at 11:54 AMNovember 13, 2008
The Old Survey Phishing Scam
I hadn't seen this type of thing in my inbox for quite awhile, so it's worth reminding email users that unexpected notices claiming to come from financial institutions—especially those with "click here" types of links—should be treated with full hazmat gear.
From: JPMorgan Chase & Co.
Subject: Add 50$ to your account in 2 minutes!
Dear Customer,
You are invited to take part in our nation-wide 5 question survey. Your time is very important to us so $50 will be credited to your account upon the completion of this survey.
Please note that no sensitive information will be required, collected or stored. The information will be used to further improve our services
To take part please click here
© 2008 JPMorgan Chase Co.
The hidden link is to an IP address. Apparently the server at that IP address is unused because there is evidence that either the phisher or someone else not only hacked into the server, but even left a note on the home page about which holes were used to gain access (including a reference to "week passwords").
If a recipient clicks the link, a redirect or two leads to another subdirectory on the same server, which displays a page containing what looks to be a typical customer survey, along with the Chase logo. At the end of the survey are some fields where the survey taker is to insert information so that the $50 will be credited to his or her debit or credit card account. You guessed it: you have to supply everything that a credit card thief needs to use the account or even create a phony card with magnetic stripe—including the ZIP code (which I've seen more and more gas pumps request before dispensing what until recently had been ultra-precious liquid).
Note that the message said that "no sensitive information will be required, collected or stored." Gimme a "B," gimme an "S."
With that, I'll relate a quick story. I picked up my ringing phone today. After that dreaded momentary delay signaling a computer-dialed call, a woman with a very heavy accent tried to identify herself as calling for Ziff-Davis. Her VOIP connection was very bad, and I'm still trying to get over a cold, so I had no patience for this intrusion. She asked when would be a good time to call me back. I replied, "If you're selling anything, I don't want you to call." "Oh no, sir," she countered, "I'm not selling anything. I have something free for you!" To that I said, "In that case you should certainly take this number off your list and never call again."
Posted on November 13, 2008 at 04:32 PM
The From: field claims to be the administrator of your email address domain. The Subject: line is compelling:
Subject: Free one year trial
If you open the message, however, you're not supplied with any information about what the free trial is about. Instead, you see this:
The message cannot be represented in 7-bit ASCII because it contains personal and sensitive data, so has been sent as a passworded attachment.Please use the following password the read the attachment
Password: 9599
Most recipients haven't a clue what "7-bit ASCII" means, but if it's safeguarding "personal and sensitive data," it must be a good thing, right? And, after all, the file is further protected with a password.
The attached file is named Secure_Details.zip.
Unfortunately, as of this hour, only 22% of VirusTotal signature tests spot this attachment for the nastiness that it contains.
November 12, 2008
Spam Levels Down? Not Here [Update:Maybe]
The spam-fighting world was abuzz yesterday and today with reports of a major spam source having been cut off entirely from the Internet. Brian Krebs of the Washington Post had much to do with the takedown. You can read all the details here.
Today, Brian says that several spam tracking sources reported a significant drop in spam yesterday, notably cutting off at the hour when the spammer's plug was unceremoniously yanked. These guys deal in such huge volumes that they track spam on almost a per-second basis. If you look at my stats page, however, you'll notice that Tuesday was only slightly less than Monday, and still ahead of all days of the previous week.
My stats are tabulated only on a daily basis, with the cutoff at approximately 0600 GMT. Even so, I would have expected a more substantial drop in yesterday's flow if my spam was coming from the same source that had been axed. I can only surmise that the bulk of spam I receive originates from other sources—sources unaffected by yesterday's takedown.
It seems that whenever a spam kingpin is dethroned, I don't see much in the way of a reduction of crap headed for my email server. My addresses must be on the "wrong" lists out there.
UPDATE (13 November 2008). The stats for the full day of Wednesday showed an uncharacteristic drop of about 25% of spam addressed to me. There was, however, no reduction in the spam addressed to bad or garbled addresses at my domain (many of which have been on the books for years). I'll keep my fingers crossed that this reduction holds for awhile.
Posted on November 12, 2008 at 11:32 AMNovember 11, 2008
"Contract" Malware Lure
This is pretty flimsy, but many a struggling small business owner or manager might be fooled into opening the attached file, Contract.zip:
From: MSU ltd.
Subject: Record in debit of accountGood day
We have already made ready the contract and we also joined some points you'd asked to add to it.
The lawyers change some points on the last page. Read the contract, please, and if there are no objections from your part we can pay for the first batch on Friday.
You can find the contract in the attached ZIP Archive.We also ready to send it by fax if you need
Expecting for your decision
According to a VirusTotal scan, most of the major antivirus products catch this malware loader, assuming that recipients' AV software is up to date.
Whenever you see a paperclip (attachment) icon next to an item in your inbox—regardless of sender—it's time to go on HIGH ALERT.
Posted on November 11, 2008 at 07:35 AMNovember 10, 2008
So Now I'm a Hotel Owner?
My email address has been mysteriously entered to some odd mailing lists over the years. For a long time, I was supposedly in the real estate business; I'm also theoretically interested in attending Malaysian business conferences. Now, according to one German-language spam message, my dannyg.com web site—the one about my books and computer programming—is proof that I'm in either the restaurant or hotel business.
The spam message tells me that a search for my restaurant or hotel at dannyg.com resulted in a negative evaluation. Oh, man! Is somebody writing trash about a deflated souffle coming out of my kitchen, or a hair left in the bathroom sink? Damn you, blogosphere!!
The message goes on to tell me that if potential customers find negative evaluations or test results when they Google for my restaurant/hotel, I won't be able to turn them into customers. Oh, no!
Fortunately, the sender is a professional public relations firm specializing in search engine optimization for the restaurant/hotel industry ("Ihr Restaurant/Hotel PR für Suchmaschinen Team"). To prove they are sophisticated Internet professionals, the link in the message isn't to a web site, but to a gmail address, whose account name includes the words "hotel" and "public relations."
Two words:
No Vacancy.
Posted on November 10, 2008 at 11:51 AMNovember 07, 2008
Who Needs Soap Operas?
I'm convinced that 419 message writers—if only they knew how to use the CapsLock key—could find legitimate work writing for soap operas. Just like the daily TV "stories," 419 messages are tall tales that repeat themselves from time to time, usually involving death, sorrow, intrigue, and a hope for a better tomorrow.
Last month I wrote about a 419 message that included the story line of someone trying to muscle in on my "lottery winnings" by claiming to represent me in claiming the dough. That was supposed to get my dander up and trigger me to call/email the 419er.
Another variation on that theme arrived today. This time the letter was better-crafted than most, and claimed to originate from HSBC Bank in London. Get a cup of coffee, open up a box of bon-bons, and enjoy the story:
HSBC BANK PLC LONDON.(REGISTERED NO.1026167).
ADDRESS: 8 CANADA SQUARE LONDON , E14 5HQ ,
UNITED KINGDOM.Chairman Committee On Foreign Contract And
Inheritance fund Payment Notification
FROM:HSBC BANK PLC LONDON.Attn: Beneficiary,
The U.S.A Government, World Bank And United Nations Organization Official Has Approved to pay you part payment of your contract/Inheritance Fund payment Valued at USD$1.3m in conjunction with British Government and HSBC BANK PLC LONDON.
This decision was made last week.With this development, a woman by name (MRS: JANET WHITE) came to our office with an application stating that you gave her the power of attorney to be the beneficiary of your outstanding contract/Inheritance/award funds. She made us to believe that you are dead and that she is your next of kin. We got your email address and decided to send an email through this address hoping to find out if you are dead or alive and also to find out if you at any time gave this woman the power of attorney to represent you.
Please let us know also if you are aware that we are almost ready to transfer part payment of $1.3m USD of your outstanding funds to her nominated bank account stated below:
Bank Name:Washington Mutual Bank
Address:1723 Palmdale Bulv.
Palmdale Ca. 93550
Acct # : 3573813158
Rout # : 322271627
Swift code # : WMSBUS66
Beneficiary:JANET WHITEIf you are not aware of the above instruction, do respond to this email immediately by contacting the Chairman of the International remittance department (Mr.Douglas Flint)
His contact information are written below:
Name:Mr.Douglas Flint.
Direct Telephone Number:+44-70-[removed]
Fax Number:+44-870-[removed]
Email:[removed]dept@hotmail.comFor immediate transfer of your funds be informed that you are not allowed to correspond or contact any person or office with respect to this transfer other than this office, you are required to send to him an email with your full following information below:
1) YOUR FULL NAME__________________
2) RESIDENCE ADDRESS, CITY, STATE AND COUNTRY_______________________
3) PERSONAL CELL PHONE, FAX AND MOBILE PHONE NUMBER_________________________
Yours Sincerely,
Mr. Alex Hungate.
HSBC BANK PLC LONDON.
This guy reached deep to add respectability to his missive, dropping the names of the U.S. Government (whatever that is), World Bank, United Nations, and British Government. As preposterous as this sounds to experienced 419 readers, I certainly can see technophobic retirees getting caught up in this scam, failing to recognize that someone claiming to be an HSBC department chairman is relying on a free Hotmail account for official correspondence.
The belief that someone is roaming around London claiming to have power of attorney for your non-dead self could be a scary prospect to the unwary. All that Washington Mutual bank information looks mighty real, too (there really is a WAMU branch at that Palmdale address).
But it's all a hoax to get you to engage with the crooks. Once they have you on the hook, they'll reel you in like a carp.
Posted on November 07, 2008 at 09:08 AMNovember 04, 2008
419er - No Shame, No Logic
Here is a 419 message I saw today (thankfully devoid of all uppercase letters):
Subject: Seeking Your Help.Dear Sir,
I am writing on behalf of my client Ms. Maria Stevens, an (America Citizen) seeking for your assistance towards receiving the sum of $2.7M US dollars her late husband Roland Stevens deposited in a bank. Security Company will assist her in getting back her late husband estates with your cooperation and trust.If you are willing to help her out on that, she needs your attention immediately and your trust worthy will help a long way in serving her kids better. You can view her on the BBC News site displaces thus; < http://news.bbc.co.uk/1/hi/world/africa/918781.stm >.
Thanks and God bless.
Yours truly,
Mr. Shaban I.B.Kabala.
The BBC News link is a common ploy of 419ers to lend credibility to their otherwise preposterous story. But this guy goes too far in taking advantage of a tragedy experienced by Maria Stevens, who, indeed, lost her husband to ethnic-political violence in Zimbabwe in 2000. Ms. Stevens is from Sweden, not the U.S., so there is yet another lie in this message intended to tug at heartstrings.
I also fail to understand the logic of this message. Since Ms. Stevens is still alive, what's in it for me to help her retrieve $2.7 million? That amount (in full) is on the low side of recent 419 promises, and in this case, the bulk of the (non-existent) money would certainly go to the widow. This clown failed to put enough "what's in it for me?" answers in this initial message. I mean, c'mon man: If you're going to appeal to greed, put enough cheese in the trap!
So, on this U.S. election day, I vote for this 419er in the category of Most Despicable and Stupid at the Same Time.
Posted on November 04, 2008 at 08:11 AM