| Home | The Book | Training | Events | Tools | Stats |
August 20, 2011
Back to Spam
It seems the, um, bulk of my postings lately have been about malware delivery. But regular ol' spamming is still going on. I saw a mortgage lead spam today — pretty rare these days, compared to the go-go days before the mortgage and housing markets collapsed. You'd think by now even newbie spammers would have half a brain, but this guy didn't. He revealed 400 email addresses in the To: field, rather than use BCC. Doof.
Another spammer has started to get under my skin. His subject matter changes regularly, but his underlying technique doesn't. In one example I saw today, the come-on was an offer for two free tickets on Southwest Airlines (a brand name that has been abused by scammers for years). The domain used in this example was minted this month, and the whois data is hidden behind a privacy service.
This effort is mounted by an email marketing service rather than a crumb-bum wannabe spammer. The sending email server is part of a server farm within an IP block. I deduce this by noting that the server's verfied subdomain is named suho153, and the IP address for that server ends in 153. This is not a coincidence, but a practice I've seen for years.
Another clue about the "professionalism" of the marketer is that the messages attempt to be CANSPAM compliant, complete with an unsubscribe link and a mailing address. As you might expect, the mailing address is to a UPS Store in Scottsdale, Arizona:
3370 N Hayden Rd
Suite 123-409
Scottsdale, AZ 85251
The UPS Store's suite number in the shopping center is 123. That must mean that our spammer's box number (if it's really owned by the spammer) is #409 at that UPS Store. Noticeably absent from the unsubscribe information is a company name for the sender. He's careful to avoid deceit in the message header by assigning the generic name "Airline Ticket Specials" as the plain language address (which shows up in your From email column), rather than referring to Southwest Airlines directly. That might keep the Southwest lawyers from embarking on a spammer hunting mission.
Two things really piss me off about his spam messages, however.
First, every link on the page includes a long hexadecimal identifier in the URL. The number is likely tied to the recipient's email address in the sender's database. A click on any of those links will verify that the address is good and actively used. Even if you're just curious about the two free airline tickets, your click will destroy your email address for good. If you attempt to navigate manually to just the domain, all you get is an empty page.
Second, although the visible email content is short and to the point, it is dwarfed by a huge amount of hash-busting content copied en masse from Amazon review pages for various types of products. How dwarfed? The entire message (including headers) contains 64,708 characters; the hash-busting text consists of 62,648 characters. To prevent the hash-busting text from being rendered, it is encased in a phony <style> stylesheet tag at the end of the message. There is not one lick of CSS code inside the tag.
Now, the only reason a sender would include hash-busting techniques in message content is to get past spam filters; and the main reason such messages would normally be filtered is because the recipients consider such messages to be unwanted. I'd wager a burger and a beer that the sender of these messages promotes his own email marketing services as directing messages to genuinely opt-in recipients.
Bullshit.
Posted on August 20, 2011 at 05:15 PMAugust 17, 2011
Yet Another Attachment Trick - Uniform Traffic Ticket
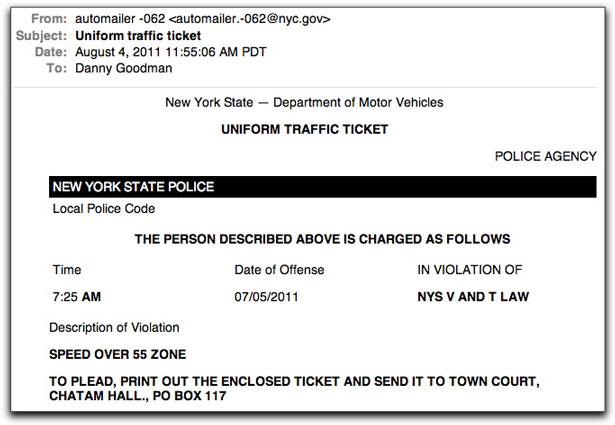
Maybe this will turn into a "One Trick Per Day" series after yesterday's malware attachment con. Today I'm in trouble for a speeding ticket in New York (uh huh):
I'm sure that many recipients of this message are incensed at being accused of a traffic violation, most likely in a place they haven't been in some time. This will, um, drive them to open the attachment, rather than examine the message for the various errors. The two most egregious are:
- The forged header's date is one day before the alleged offense. Now that's one helluva radar gun. It's clairvoyant.
- They fail to supply the city and ZIP code in the mailing address. Moreover, they're probably referring to Chatham, not Chatam.
My email client failed to show the attachment as a clickable entity. Perhaps there is an error in the multi-part coding. But from the message's source code, I see that the attachment in the copy I received is named Ticket-064-211.zip.
As the crook assembled the forged header, he did go to the trouble of making it appear as though the message originated in an IP address block owned by a New York government agency (although for New York City). Of course, I doubt any New York agency would use an email server in the middle of Russia.
So, it's just more of the same with, I'm sure, more yet to come.
Posted on August 17, 2011 at 08:56 AMAugust 16, 2011
More "Open The Attachment" Tricks
In addition to the revived flood of phony UPS/Fedex/DHL delivery notifications carrying lethal malware payloads, today I saw a variation of an old social engineering trick:
Subject: Re: FW: End of July Stat.
Hallo,
As requested I give you the open Invoices issued to you as per 30th July 2011:Regards
STEVIE HUFF
The attachment in the sample I saw was named Inv._08.8.2011_B8.zip. It's a Trojan loader, which will take over your PC with junk, including software that captures your various login credentials as you surf the web — potentially exposing you to all kinds of financial and identity theft.
Remember that crooks want to push your buttons to get you to act on their behalf. Making you think that you're in trouble and the details are in the attachment is a common ploy.
If you feel you can't resist, hold off for a second and upload the attachment to virustotal.com to see if any of 40+ antivirus programs detect the file as bad. If only a handful of products detect the file as malware, you should be extra careful with it because your antivirus software may not yet have data to save you on your PC. For instance, "Stevie Huff's" attachment is identified by only six AV products at this hour. That means it's a new variant (of the thousands produced every day), and even many major AV branded products wouldn't stop it from wreaking havoc on your system for awhile.
Posted on August 16, 2011 at 08:53 AMAugust 01, 2011
Interesting Apple Mail Phishing Protection
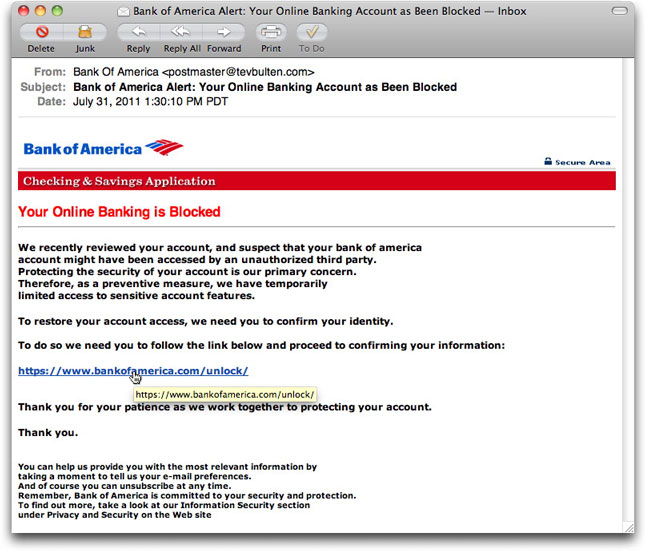
One of those continually obnoxious Bank of America phishing email messages landed in my inbox this morning. I don't even have to open the message to know it's a phony because the Subject: line claims my online banking account has been blocked (or, in today's message "Account as Been Blocked" — WTH?).
Such messages are usually written with HTML so they can provide what looks to be a link to BofA, but whose real destination is some other site that tries to grab your login credentials. I do tend to open these messages just to see if the crooks are doing anything new in social engineering (that hasn't been used repeatedly for over a decade). I'll run the cursor over the link to see where the real destination is.
[Pause that thread for a moment.]
I recently switched my email client from Microsoft Entourage to Apple's own Mail program. My reason for the switch is that I had read plenty of negative things about the most recent Mac Office upgrade to email (now a Mac version of Outlook). Eventually for other client work, I'll need to upgrade to the newest Office, and with Apple continuing to obsolete older program generations with OS updates, I felt that my comfy Entourage's days were numbered (perhaps a big number now, but that won't last). And so, with trepidation about converting over a decade of email history in the process, I gave Apple Mail a try.
The transfer of old email messages was as tedious as some online discussions had suggested it would be. Apple Mail seems to choke on trying to convert too many Entourage emails in one gulp. After much twiddling and relaunching of Mail, I finally got the historical archive into Mail.
Having lived with Mail for a couple of weeks now, I can say that I'm satisfied with it. I do like the single inbox for all my accounts and services (like I use on the iPhone), but I also have a couple of UI suggestions for Apple. This isn't the place for those, so let's move on.
[We now rejoin the previous thread.]
When you run the cursor over an HTML link in Entourage, the actual destination URL appears in both the bottom of the window (immediately) and in a tooltip (after the usual delay). In Mail, the destination URL comes up only in a tooltip, so I have to wait a second or two for that to appear. When I ran the cursor over today's BofA phishing message, imagine my surprise when the tooltip showed the real bankofamerica.com domain (albeit to an unlikely subdirectory). Cue the sound of screeching tires.
From other examples, I knew that Mail's link tooltips expand to show the entire URL, even if it runs to multiple lines. Therefore, this wasn't being truncated. At first, I thought (haughtily) that the crook had improperly coded the link tag, and that his entire phishing run would be for naught. Off to the source code!
<a rel="nofollow" href="http://www.1004bang.net/[removed]/index.html" target="_blank"><font color="#da0000"><strong><span> https://www.bankofamerica.com/unlock/</span> </strong></font></a>
So, the actual destination — a hijacked Korean web site — is in the link, but the HTML markup also includes a rel="nofollow" attribute. Although the rel attribute is part of the HTML standard, the usage of "nofollow" is somewhat controversial and applies primarily to influencing search engines. If you want to follow the paths on this subject, have a blast.
Getting back to Apple Mail's interpretation of this "nofollow" link, I was concerned that by displaying a tooltip with the tag's enclosed text, rather than the destination URL, users who knew enough to check URLs before clicking might be given the wrong information. The link could look "safe," when, in truth, the link could lead to a phony, credential-snarfing page.
What happens when a user clicks on a link marked this way?
To my surprise and delight, the default browser opened with the URL that showed up in the tooltip, not the link's href. Of course, bankofamerica.com has no "unlock" subdirectory off its root, so the server dutifully said it was a bad address ("Page Not Available").
Somewhere in the bowels of Apple Mail programmingdom, they determined that any HTML-formatted message that employed a rel="nofollow" attribute (whose usage is intended only for web site pages being crawled by search engines) is probably up to no good. This buried feature probably saved some Mac users from falling for this phishing trap.
Out of curiosity, I forwarded the message to my iPhone to see if its email client acted the same way. Few iOS Mail users know that you can tap-and-hold on a link to view the link's actual destination URL without navigating to the link. Unfortunately, the iPhone Mail app doesn't act the same way Mac Mail does. We need to be on our guard when we're on the go.
I guess this was a long piece just to describe my glee in finding an email client that takes a small step to protect users from crooks.
Posted on August 01, 2011 at 12:22 PM