| Home | The Book | Training | Events | Tools | Stats |
November 30, 2009
Sears Card Phishing
A Sears card lets one shop at Sears and Kmart, both in brick-and-mortar and online stores. If you have a Sears card and yield to the tricks of one of today's phishers, you will hand over your account to someone capable of having a real shopping spree. Moreover, if your login credentials are the same for your Sears card and other major banking one e-commerce sites, you and your credit history could be in for a world of hurt.
Here's the simple Sears phishing missive seen today:
From: Sears Card
Subject: You have one new message from Sears Card
You have 1 new message
Please log-in to your Sears Card account.
Your Internet Banking Account may be locked.
Please identify yourself by visiting our Online Banking service:
Sears Card ONLINE
© 2009 Sears Card Online. All rights reserved.
The destination URL redirects to a site whose domain was registered waaaay back earlier today. And the page is a complete ripoff of the actual Sears Card page, including the same HTML errors as the original.
BTW, Sears Card is managed by Citibank. When there's a problem with your Sears Card account, Citibank goons are the ones who come after you.
November 29, 2009
An Email From Hillary Clinton
Oh yeah, I travel in elite circles, so of course I'm going to get email from the U.S. Secretary of State, Hillary Clinton. That's as good a name as any to abuse in a 419 scam that invokes the U.S. and British governments, as well as the United Nations. He tosses in a Citi Bank branch in Nigeria for good measure.
Thanks to one missing letter, this scammer's missive gets off to a rocky start:
From: MR HILLARY CLINTON
Subject: SECRETARY OF STATE
Let me pause right here. A snarky diplomat recently called Bill Clinton "Mr. Hillary Clinton" to imply that his various activities are under Hillary's control. Needless to say, the email's error was good for a mini-laugh.
UNITED STATE OF AMERICA
OFFICE OF THE SECRETARY OF STATE
COMMITTEE ON FOREIGN PAYMENT
RESOLUTION PANEL ON PAYMENT)
WASHINGTON DC
Attention: BeneficiaryI wish to use this medium and my new office to inform you that your CONTRACT/INHERITANCE Payment of USD$10m (TEN Million Dollars) from CITI BANK OF NEW YORK has been RELEASED and APPROVED for onward transfer to you via an ATM CARD which you will use to withdraw all the USD$10m in any ATM SERVICE MACHINE in any part of the world, but the maximum you can withdraw in a day is USD$10,000 Only
The UNITED STATE OF AMERICA government has mandated CITI BANK OF NIGERIA, to send you the ATM CARD and PIN NUMBER with other relevant document from our government and British government and the united nation, You are therefore advice to contact director and the Head of ATM CARD Department of CITI BANK OF NIGERIA for further instructions and to release your approved ATM CARD to you.
Contact Person: Mr. PHILIP EZE
CITI BANK OF NIGERIA
Phone number: +234[removed]
EMAIL: (mrphilipezee@[removed free email domain].com)Tell Mr. PHILIP EZEE that you received a message from the OFFICE OF THE SECRETARY OF STATE to send you the ATM CARD and PIN NUMBER AND ALL THE DOCUMENT which you will use to withdraw your USD$10 Million Dollars, also send him your direct phone number and contact address where you want him to send the ATM CARD and PIN NUMBER to you BUT YOU WILL PAY FOR THE LITTLE INSURANCE AND SHIPMENT FEES FOR DELIVERY.
All the document regards to the release of the fund has been handed over to Mr. PHILIP EZE for delivery.
I am very sorry for the delay you have gone through in the past years. Thanks for adhering to this instruction and once again accept my congratulations.
Best Regards.
MRS. HILLARY CLINTON
At least the crook warns recipients that there will be some upfront fees. But they won't be little, and they won't stop with the first installment. Nor do such an ATM card and fund even exist.
I'd like this guy to be caught for only one reason: to be brought to Washington where Hillary can give him the stank eye for five minutes. That might scare him straight.
Posted on November 29, 2009 at 04:50 PMNovember 15, 2009
Using Insecurity Fears to Spread Insecurity
As if on cue, one Bad Guy seems to be using very recent news of an unpatched Adobe Flash security flaw to help spread a backdoor Trojan. The campaign begins with a simple email message:
From: flashplayer@adobe.com
Subject: We've created a new version of the famous video Adobe Flash player !!Hello
A new version of the Flash player for better quality is now available
for download click here
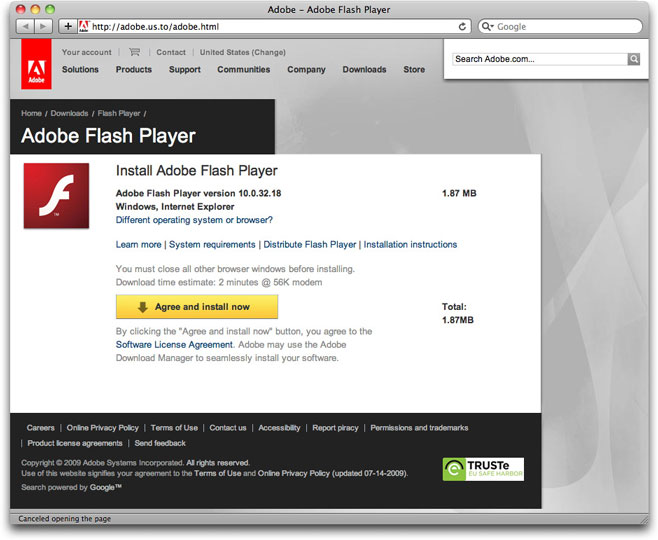
If you bother to inspect the URL in the real message (the one above is blank, and shows the URL of the page you're now reading), it might look sufficiently legitimate to some: http://adobe.us.to/adobe.html.
And if you then click on the link, you get one darned-good imitation of an Adobe web page:
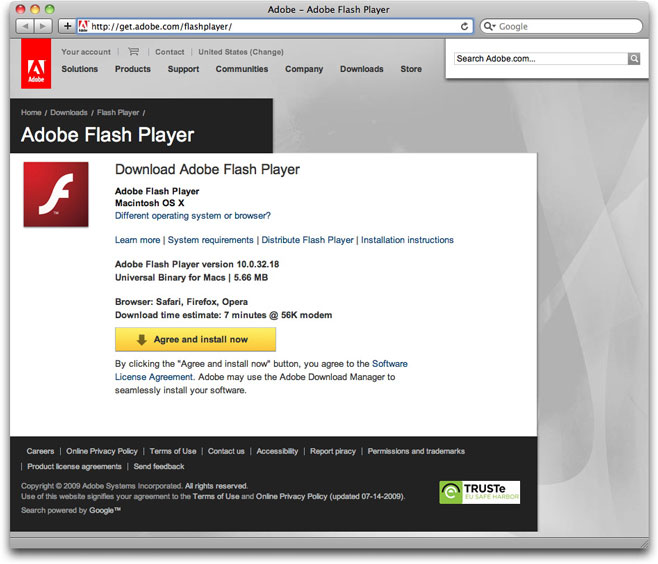
How good is the imitation? Well, here's the real Flash Player download page:
The primary discrepancy, of course, is that the fake page insists on presenting a screen suggesting I'm using Internet Explorer for Windows, even though I accessed the page with Safari on a Mac. The real Adobe Flash Player download page recognized my operating system, and presented the appropriate download. Obviously, someone reaching the phony page on a Windows machine wouldn't see anything wrong.
Unlike the real Adobe page, the Bad Guy's page downloads a file called Flashplayer.exe, which is actually a backdoor Trojan of the Zapchast family. This particular instance is a fairly old one, and most antivirus products identify it for what it is (78% coverage at VirusTotal).
Ultimately, the joke is on the poor user who installs this Trojan. While he or she might believe he or she is heading off potential infection through Flash, in truth, he or she has just granted the Bad Guy an All Access Pass to the entire PC system and data, without ever going near Flash.
Posted on November 15, 2009 at 11:49 AMNovember 10, 2009
PayPal Phish With HTML Attachment
It's Tuesday morning here, so it must be time for yet another PayPal phishing attempt. Well, okay, any time is PayPal phishing time.
One such attempt I saw today used a technique I don't see much, wherein a short and simple email message has a real HTML file attached to it (not some other type of file masquerading as an HTML file). As you'll see, this can cause a problem for traditional antiphishing techniques.
First, the plain text message (including misspelling):
From: "www.paypal.com" <service@paypal.com>
Subject: PayPal .INCTo make sure everything is in order,please download the PayPal Security Account Verification and fill in all the required data for verfication.
The attached file is named: PayPal Security Account Verification.html.
Now, I know not to get picky with grammar and technical accuracy practiced by criminals, but I would think the notion of downloading is something rather different from opening an attachment. From a purely pedagogical perspective, the instructions provided by the crook fail to, well, instruct.
Of course, that won't stop many recipients from double-clicking that HTML attachment.
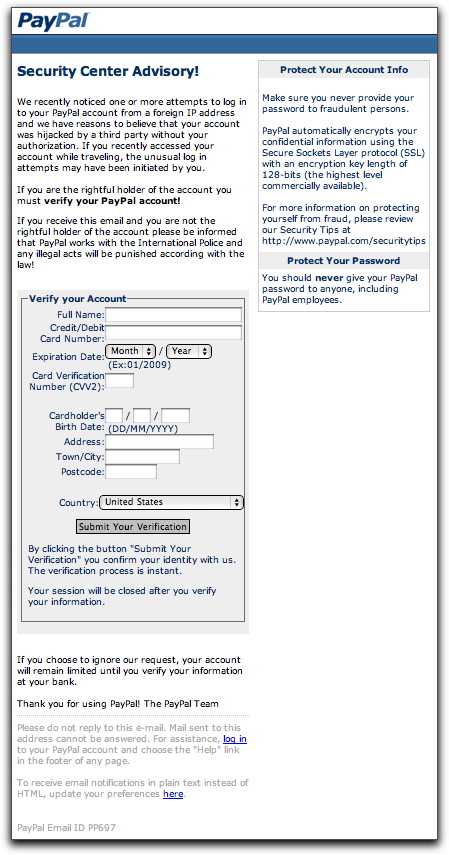
And what will they see? Their default web browser will open with the following page:
The HTML code for this page probably came from a phishing kit. Normally, this is the page that gets served up on the hijacked site being used to gather credit card or login credentials. This crook chose to include the form as an attachment.
Submitting the form sends the credit card data to a numeric IP address coded with hexadecimal numbers (e.g., http://0xb5.0xa9.0xd1.0xc3/...). Hapless Mac users who try to submit the form or click on either of the links at the bottom of the page (also coded in hex) will be saved from themselves: Safari and Firefox for the Mac don't interpret hex IP addresses, yielding a "server not found" type of error. Windows users? Not so lucky.
As more and more browsers installed out in the world have antiphishing powers built into them, it's possible that we'll see more of this type of attachment coming in future phishing attempts. Instead of getting a warning when trying to click a link in a phishing message, the user simply gets the attached HTML file opening in the browser as a local file, thus avoiding any check against the antiphishing URL database. As I write this, the antiphishing database used by Safari and Firefox does not have the numeric IP address of the form's submission URL on file, thus allowing the submission to go through without complaint (to a hijacked Czech poker site).
Arg, another mole! Time to whittle us a new whacking stick!
Posted on November 10, 2009 at 12:25 PMNovember 05, 2009
Facebook, Part Two
Earlier today we had a Facebook phishing scam to capture login credentials. Now Facebook is being abused as a way to get spam recipients to install a Trojan:
From: "Facebook Support" <confirmation@facebook.com>
Subject: Facebook Password Reset Confirmation.Support Message.Hey [removed] ,
Because of the measures taken to provide safety to our clients, your password has been changed.
You can find your new password in attached document.Thanks,
Your Facebook.
The attachment is a file named Facebook_Details_11c97.zip. Unfortunately, VirusTotal shows only 5% recognition by antivirus products.
Posted on November 05, 2009 at 10:30 PM
Here's a believable phishing message aimed at capturing Facebook accounts and username/password pairs to accomplish a variety of nastiness:
From: "Facebook" <update+zzbvjrnbpbnx@facebookmail.com>
Subject: New login systemDear Facebook user,
In an effort to make your online experience safer and more enjoyable, Facebook will be implementing a new login system that will affect all Facebook users. These changes will offer new features and increased account security.
Before you are able to use the new login system, you will be required to update your account.Please click on the link below to update your account online now:
http://www.facebook.com.[removed].eu/globaldirectory/LoginFacebook.php?ref=20244492275620965881064893464436522177812276399621698&email=[removed]@dannyg.com
If you have any questions, reference our New User Guide.
Thanks,
The Facebook Team
It was easy for me to recognize this as a fake from the inbox listing because I'm one of the few remaining people on Earth who doesn't have a Facebook account. But even if you're a Facebook user, any email message that talks about security, logging in, or passwords should set your Suspicion switch to High. This carefully crafted message uses a long URL that looks to be to facebook.com — unless you understand how URLs work, in which case you'd see that the URL is actually to a .eu domain. Moreover, the URL and very Facebook-looking phishing page at the URL destination are wired to display your login name (email address) already filled into the login form — most likely just like a real Facebook login page.
Many malware followers wonder how any user could be fooled into yielding login credentials to a phisher, even after so much publicity about such attacks. This is how.
November 02, 2009
Party Pooper
Here's another guy who, depending on his business relationship with the final destination web site, could make a bundle by simply spamming the notion of a party:
Subject: Party reminderHello dannyg,
Party reminder
http://www.[removed].cn/Best regards,
Tatum Hikel
2009-11-02
If you put this message into the mailbox of every single-ish Gen-[late letter of the alphabet]er, how many would follow the link? I'll bet it's a pretty high percentage, despite the Chinese domain name. And how many of those responders have ever heard of Tatum Hikel? Zero percent.
I can't tell you for sure what's at the end of the link — whether it's selling medz/warez/knockoffz or performing a drive-by malware download — because the spamvertized site uses a server redirect to the actual destination. I chose not to follow the redirect (I don't use a typical browser for these initial investigations) because it's possible that the spamvertized web site pays for referrals: Let some poor schlub take the risk and expense of spamming, while the seller pays a pittance for every visitor whose referring web site (automatically tracked by almost every web server) belongs to the schlub. I simply don't want the spammer to gain the tiniest fraction of a yuan from my curiosity.
Unfortunately, such will not be the case of all those whose main mission in life is to party hearty.
Posted on November 02, 2009 at 10:40 AMNovember 01, 2009
Spam, 1980s Style
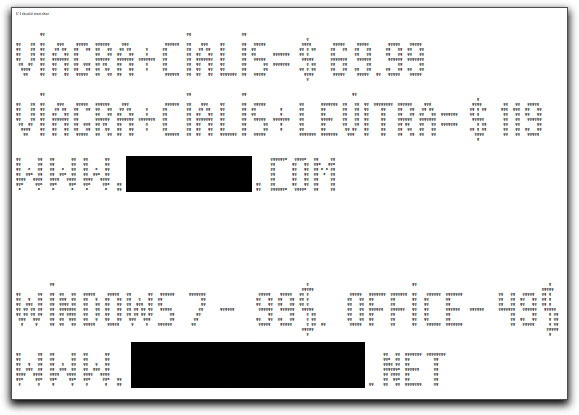
One semi-advantage of being the old fart that I am is that I have seen a lot in my many years and can recognize things from decades ago (just don't ask me where I set down my car keys). Such is the case with a spammer doing most of his operation out of China who is using what is known as ASCII art to convey his message.
Put on your time traveler hat, and set the dial to the early 1980s, when personal computers usually printed on fanfold paper, most commonly in a monospaced typeface. That is, every character, whether the slim "i" or fat "w", occupied the same horizontal space in a line. It not only made it easy to line up columns of numbers for boring reports, but also provided an invisible grid that could be replicated in every printer. By carefully placing letters in positions on the grid, one could create a mosaic-like piece of art. When viewed at a bit of a distance, the "image" could be plainly seen. This technique actually started back in the early typewriter days (late 1890s), moving onto clattering teletype machines, and, in the computing days, became known as ASCII art (named after a standard character set).
ASCII art is almost a lost art because these days printers and computer screens successfully render proportional font families, which are generally more pleasing to read. And if there is one thing that a proportional font does really well, it's screw up ASCII art that depends on a monospaced font.
But that didn't stop our spammer from using HTML and a tag that renders in a monospace font to convey his medz and warez spam message (a one-stop shopping spammer) via the lowercase "g" character:
For extra measure, this guy surrounded the ASCII art portion with fragments from English poetry (Ralph Waldo Emerson and Lord Byron, respectively) — a common hash-busting technique to trick content filters.
Yawn.
Posted on November 01, 2009 at 10:19 AM