« Facebook, Part Two | Main | Using Insecurity Fears to Spread Insecurity »
| Home | The Book | Training | Events | Tools | Stats |
November 10, 2009
PayPal Phish With HTML AttachmentIt's Tuesday morning here, so it must be time for yet another PayPal phishing attempt. Well, okay, any time is PayPal phishing time.
One such attempt I saw today used a technique I don't see much, wherein a short and simple email message has a real HTML file attached to it (not some other type of file masquerading as an HTML file). As you'll see, this can cause a problem for traditional antiphishing techniques.
First, the plain text message (including misspelling):
From: "www.paypal.com" <service@paypal.com>
Subject: PayPal .INCTo make sure everything is in order,please download the PayPal Security Account Verification and fill in all the required data for verfication.
The attached file is named: PayPal Security Account Verification.html.
Now, I know not to get picky with grammar and technical accuracy practiced by criminals, but I would think the notion of downloading is something rather different from opening an attachment. From a purely pedagogical perspective, the instructions provided by the crook fail to, well, instruct.
Of course, that won't stop many recipients from double-clicking that HTML attachment.
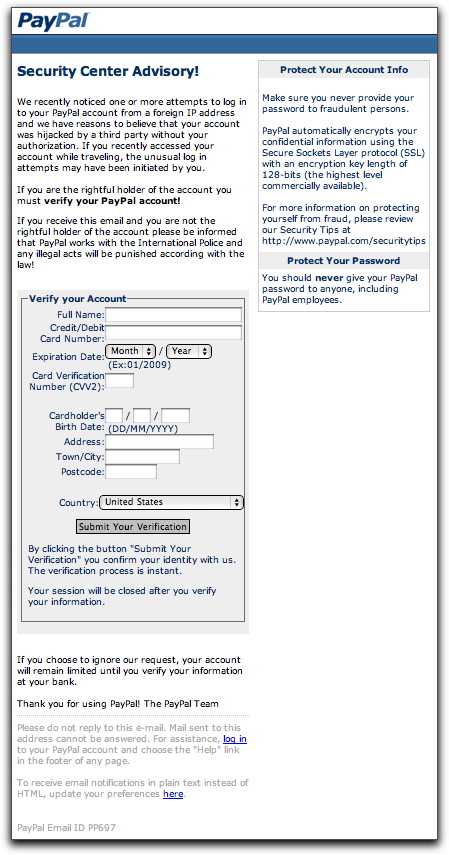
And what will they see? Their default web browser will open with the following page:
The HTML code for this page probably came from a phishing kit. Normally, this is the page that gets served up on the hijacked site being used to gather credit card or login credentials. This crook chose to include the form as an attachment.
Submitting the form sends the credit card data to a numeric IP address coded with hexadecimal numbers (e.g., http://0xb5.0xa9.0xd1.0xc3/...). Hapless Mac users who try to submit the form or click on either of the links at the bottom of the page (also coded in hex) will be saved from themselves: Safari and Firefox for the Mac don't interpret hex IP addresses, yielding a "server not found" type of error. Windows users? Not so lucky.
As more and more browsers installed out in the world have antiphishing powers built into them, it's possible that we'll see more of this type of attachment coming in future phishing attempts. Instead of getting a warning when trying to click a link in a phishing message, the user simply gets the attached HTML file opening in the browser as a local file, thus avoiding any check against the antiphishing URL database. As I write this, the antiphishing database used by Safari and Firefox does not have the numeric IP address of the form's submission URL on file, thus allowing the submission to go through without complaint (to a hijacked Czech poker site).
Arg, another mole! Time to whittle us a new whacking stick!
Posted on November 10, 2009 at 12:25 PM