| Home | The Book | Training | Events | Tools | Stats |
April 28, 2005
Not All Phish Messages Are Harmless
I've looked through the source code of probably hundreds of phishing messages through the years, and don't recall ever encountering one that wasn't essentially harmless to view, even in HTML. A little importing of the financial institution's logo art and a hidden URL to a phony login site, and that was it.
Until today.
The Subject: line was like so many others that float around the Internet: Urgent Safeharbor Department Notice. Safeharbor is an eBay thing, so this was going to be yet another eBay phishing message. But lurking in the body was a virus loader that fires (in the right environment) upon viewing the message in HTML form.
After doing some checking, I found that the potential infection is for a rather old virus, called VBS.Redlof.A This virus dates back to the era (all of three years ago) when viruses were mostly written and distributed by precocious youngsters, earning them the name "script kiddies." Most of these idiotic tricksters were interested in seeing how far and how quickly their inventions could spread.
Those days are gone, but their viruses live on in some computers around the world. Such computers either have absolutely no virus protection, or they haven't updated their virus definitions since early April of 2002.
The phishing message that contained the Visual Basic Script loader for the virus (requiring a Windows computer to execute it, by the way) was sent through a zombie PC. It's not easy to tell if the zombie is infected with the virus or if the phisher who generated the message is. Whoever is infected, the virus turned the HTML code for the message into an unsolved Rubik's Cube—pieces chopped up and distributed all over the place within the document.
But the lesson is clear: Messages you may have thought could be harmless are not necessarily so. With so many phishing messages not only going out but being opened by recipients, I had been waiting for a sign of this kind of exploitation for awhile. In this case, I believe it was unintentional (somebody in the chain doesn't know that his or her computer is hosed). But phishing messages and the sites they lead to could become a huge vector for all kinds of nastiness, even if you just open the message and visit the phony site without logging in.
The same safety rules I supply in Spam Wars apply to phishing messages. The infected message I received today indicates that everyone needs to take this stuff seriously.
Posted on April 28, 2005 at 09:05 AMApril 26, 2005
Incomprehensible Medz
I get plenty of spam in Russian, Korean, and Chinese—none of which I can understand. But here's one that is supposedly in English:
Our manufacture supports you retain on costly directions drugs with prices which are as many as 96 per cent smaller than retail pharmacy equals.
Our output are refered out within 22 hours of the processing of the order and will be carryed to you within 12 working days. The medicine provided by our discharge service colleagues are drug and food administration general medicaments carryed out by the exacting contexts and superintendence.
Our medicine gain in blister packs which insure their confidence and originality.
What a sweet-talker! And I bet the medz—if you ever received them—are just terrific.
Posted on April 26, 2005 at 10:41 PMApril 24, 2005
"Email Marketing" Is Its Own Enemy
A scan through my spam suspects today revealed a lengthy HTML-formatted message wishing to entice me to hire the outfit to do some email marketing on my behalf. Well, not my behalf personally. On behalf of whoever receives this spam.
The message Subject: and title says:
Media Rama Email Marketing Service
Then the message starts by indicating that it is a newsletter, and that the sender is "the one stop shop for all your e-mail marketing needs and solutions." Oh good, I thought I'd have to hunt high and low to find an email marketer.
Next we get to the body. It begins,
Dear Subscriber,
BZZZZZT! Oooh, wrong answer. There's no way in hell I would have ever signed up to an email marketing newsletter. Especially one that is so proud of its identity, that the From: address of the sender is some gobbledygook user name at hotmail.com.
I read between the HTML tags to see what is being promised here. First on the menu is a service whereby they will send out emails to my opt-in list. Isn't that special! I give them my list (if I had one) of carefully qualified and confirmed opt-in addresses to do my mailing for me. You don't suppose that they'd take a copy of that list for their own use, do you? They also claim that they'll do the mailing from their email servers. Well, if that's the case, why did they send this message through a (China-based) server that shows up on every proxy/trojan block list I checked? Or, by "our servers" do they mean the zombie PCs in the bot nets they control?
If I don't have my own address list, I can choose a different service that lets me mail to their list of "550 million subscribers." I'm sorry. There's no way that 550 million individuals (perhaps half the world's e-mail users) have subscribed to your service. Voluntarily, at least. They claim their lists are used by "fortune 500 companies" (it's easier to avoid false claims when you don't use the proper "Fortune" capitalization) and government agencies. Hmm. Perhaps the addresses were lifted from such companies and agencies, so, yes, the addresses were used by these outfits before they were misappropriated.
Then they say:
You don't need to worry about spam complaints, legal issues or ISP problems. In fact we list our own address in the emails to be CAN SPAM compliant since the[s]e are our own lists.
So, let me get this straight. You claim to mail CAN-SPAM compliantly and include your own address in the messages. But you failed to do that in the message selling your own services. The message was sent through a hijacked PC, with a phony Hotmail return address, with no postal mailing address, and an unsubscribe link to an email address hosted in India that is, as the Brits say, a bit dodgy. That's a minimum of three to four CAN-SPAM infractions in your own pitch.
The active response link in this message is not to a Web site, but to an email address. The domain of the intended recipient is hosted in Lebanon. And nowhere in this message is there ever a name of this company. If "Media Rama" is supposed to be the name, they're sure not very proud of it.
Buried within the HTML code is a clue about who's behind this: a disabled link to a domain whose name contains the word "optin" (not one of the domains I've seen associated with Scott Richter, so don't second-guess this one). I visit that site to see what its spiel is. I've seen dozens like this one before. It has all kinds of vague wording about how they can build your business through email marketing (the site also looks like crap in Firefox, despite what appears to be some otherwise slick-looking graphics). It has all the right marketing buzzwords, but no genuine substance. A top-level manager at a multi-national technology company I once worked for called this stuff "marketing bullshit." There is no indication where (i.e., even on which continent) the firm is located. All contact is through email or a submitted form. No names of the principals, thank you. If I want more information (including how to become an "affiliate"), I can sign up to their newsletter (which is probably different from the one they had spammed in my direction). The domain's registration is hidden behind a Domains by Proxy registration shield.
I also did some Googling on this name, and found it to be buried within hundreds of email marketing pages around the Web. I get the feeling that this outfit has gotten lots of affiliates to add blocks to the pyramid scheme that uses email marketing to sell email marketing to sell email marketing. My fear is that somewhere along the way, genuine small business people have bought into the vague promises at the slick Web site. Then you and I get the spam.
I've written in Spam Wars about how so many of the so-called email marketing companies lie their way into the wallets of unsuspecting businesses and lie their way into our in boxes ("You're receiving this message because you subscribed...."). There may be honest and good email marketing firms out there, but the well is so poisoned by the slime, that I'd be hard pressed to trust a one of them.
Posted on April 24, 2005 at 06:06 PM
By "out there," I mean in the domain registration and Web hosting worlds. I continue to find it incredible that a crook could not only register a dot-com domain name that includes the words "verify," "paypal," and "account," but that a brand-name Web hosting service would blindly grant hosting space to such a domain.
Sure enough, the interior link in one of this morning's PayPal phish messages points to such a domain (the visible link displays the real PayPal URL, as expected). The domain was registered yesterday. It's hosted at yahoo today. Peoples' lives will be ruined tomorrow. Incredible.
Posted on April 24, 2005 at 11:20 AMApril 17, 2005
Failing a Drug (Spam) Test
With the types of spam that slips through the cracks here, I'm glad I don't work for a major corporation that has all kinds of policies for monitoring employees' email and drug testing. I can only imagine what might happen if such an employer came upon the all-too-common medz spam that implies the recipient has an ongoing business relationship.
Like this one:
Your V1C0DIN Refill is now Available Please Verify Info
http://ehx.[redacted].com/dameds
Customer #: 337897922
Re-Fill #: 511415
User Name : [redacted]
The domain name of the spamvertised Web site is quite apropos. Although the actual name uses numbers for some of the letters, the name can be deduced to read "fixcentral dot com." That's just great! This spam could put its recipient in the hot seat as a suspected Vicodin junkie.
Whew! I'm glad there's no boss looking over my shoulder to catch me popping M&Ms like...candy.
Posted on April 17, 2005 at 11:34 AMApril 10, 2005
Ah, So That's Why...
Like a lot of you, I get tons of phishing messages pretending to be from financial institutions with which I don't have an account. In fact I hadn't even heard of some of them until the phish message arrived (maybe the banks should pay the phishers for all the advertising—not!). I've wondered how confused inexperienced email recipients get when receiving such dire messages from places they don't know.
Well, one phisher has answered the call. One of today's Charter One Bank phishing messages has this disclaimer in small, but red type:
Note:
This e-mail was sent on behalf of the online banking community, if you do not have an online banking account with Charter® One then this message does not apply to you and you may ignore this message.
I'll fill in the missing part: If you do have an online banking account with Charter® One, then this message still does not apply to you and you should ignore this message.
Posted on April 10, 2005 at 11:03 AMApril 06, 2005
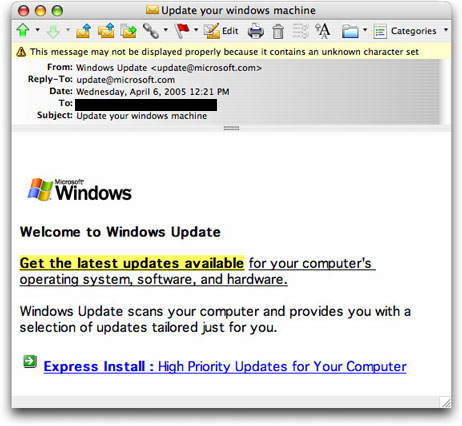
Windows Update Phishing
I don't know why it took so long for this to show up in my inbox, but this phishing trick is sure to con a ton of folks into probably handing their computers over to a "bot net." Here's the message (which I viewed only after checking the source code to see that the message, itself, did no harm):
On the surface (except for formatting that doesn't really look as good as Microsoft might produce, even when viewed in a Windows machine), it looks to come from Microsoft. It even has the little arrow icon from the genuine Windows Update page (the image files really come from Microsoft's site). But a quick peek under the hood (as Spam Wars readers know) reveals that the message did not originate from Microsoft, nor does the link really lead to Microsoft. Instead, the link goes to a numeric IP address hosted in China.
I don't know what happens when you visit that link. Fortunately (perhaps), the URL is unavailable (I have safe ways to check). But it could be that the site is under attack from the very recipients of the spam message—so many recipients are clicking the link that the site is inundated. In any case, I wouldn't expect anything good to come from a successful connection with this site. I also expect a lot more lookalike messages to arrive. They're phishing not for your identity (directly, anyway), but for your computer and your Internet connection. If they plant a keylogger into your system, they'll get your identity and/or online bank account eventually.
Pick up the phone and tell your friends.
UPDATE: At least one of the major antivirus firms has confirmed that these phony Windows Update sites install what is known as a backdoor Trojan, which means your computer becomes a slave to a different master.
Posted on April 06, 2005 at 01:59 PM
If you've been off the planet for a few years and want to know what's hot and what's not, simply look through the Subject: lines of the spam that my server deletes daily. If a spammer claims that he wants to give you something for free, you can be sure that something of value to you (money, privacy, identity, time) will slip out of your reach and into the spammer's pocket. The lure, alas, is irresitable to many.
The Apple iPod has been the hot ticket for quite awhile. I've seen several schemes, some of which have a decidedly pyramidal shape to them, and I can't imagine that there haven't been some outright scams, all in the name of iPod. The new portable Sony PlayStation (PSP) may try to eat into the iPod's territory on the free scam playing field, but I mean, who wouldn't want an iPod? Even this grizzled gadget junkie wouldn't give up his iPod for a PSP (and back in the Atari/Intellivision/Odyssey/Coleco days I used to review video games!). I gotta wriggle in silhouette as if fighting off a swarm of bees while sporting white ear buds.
But forget about the PSP's challenge to iPod's "free" dominance. Today's deleted email (from a spammer who's domain ends in "dealz") reveals the next craze:
Subject: Get the Biography of Pope John Paul II, for Free.
Now, who will be the first spammer to offer a free iPod with the papal biography already loaded as a free audio book?
Posted on April 06, 2005 at 09:32 AMApril 03, 2005
Guess the Scam
This is one of the more bizarre scammy spams I've seen in a long while:
hello,
this is kenny jem l will like to place an ordrer and i will like to know if u shipped international and if u shipped to west africa and if u accept creditcard for ur payment asnd i will like u to mail me back with ur website so that i can send u the item that i needed and i will like to know ur shipping method that u use and i will /like the order to be shipped through via ems express and i will l;ike to knopw if u can make the payment through via ems express so i will like u to get back to me with ur website and the ems shipping price so that i can send u my item that i needed and i only make my payment through via my creditcard number abnd i will like u to get back to asap and i will like u to kindly get back if u do shipp to nigeria
Thanks
Regards
Kenny is one confused fella. It also seems like an odd way to attract suckers who will ship goods against a stolen credit card. And how lazy could this guy be that he needs someone else to point him to Web sites that sell stuff? Let's see, there must be one or two somewhere....
Posted on April 03, 2005 at 11:46 AM