| Home | The Book | Training | Events | Tools | Stats |
July 31, 2008
Now We Know Where All the Oil Profits Go
After being gouged at the petrol pump, one might feel inclined to collect a rebate:
Subject: THIS IS FOR YOUI am Herron Thanks, Financial Controller of Exxon Mobil in London, http://www.exxonmobil.co.uk) We are seeking your assistance to transfer of FIFTEEN MILLION,FIVE HUNDRED> POUNDS STERLING to your account for further private investment.Please reply with your names,contact address and> cell phone no
Herron Thanks
Yes, this is how mega corporations invest their funds: By sending out email to anyone with an email account, and taking replies only through a yahoo.com email address. And, of course, they'll gladly put thirty million bucks into any ol' bank account, even if it's some shaky local bank whose accounts are insured only to $100K.
As loony as this 419er appears to be, I can also envision a recipient on the financial edge being desperate enough to get caught up in this scam in the hope of skimming a little something off the top. In this battle of Greed vs. Greed, funds move only in the direction of the 419er.
Herron, no thanks.
Posted on July 31, 2008 at 08:35 AMJuly 30, 2008
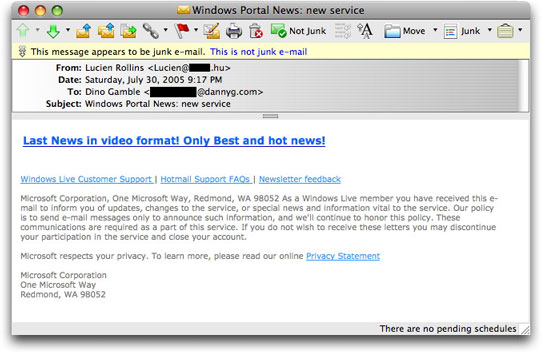
Windows News Malware Lure
I've seen a series of email messages tonight that have Subject: lines generally referring to "Windows Portal News" or "Windows Team." The message bodies tend to be nearly incomprehensible in English. Here are some samples:
- Last News in video format! Only Best and hot news!
- Last new: The American junky eats the eyes. Look at sample!
Links are to various domains in the following format:
http://[removed].com/upp/fast.php
The destination program redirects to a page that automatically downloads a file named video.avi.exe, for which VirusTotal reports a pretty dismal 10/35 identification rate.
Unlike some of the other recent malware campaigns, which aim for minimalism in their bodies (simple text line and URL), these have both text and HTML-formatted segments. Both segments include an official-sounding trailer that makes the message appear to be delivered as part of the recipient's membership in Microsoft Live:
These guys also took the time to program some strange stuff in the message header. In particular, they insert a second Received: header line making it look as though my email server generated the line (which it definitely did not). The (presumably botnet) program that sends the messages customizes each message's extra Received: line. There is also a mistake in their program because the line includes two placeholders for randomized numbers. D'oh!
Given the low virus program detection for the payload, this could be a pretty nasty chunk of Bad Stuff. Don't go there.
Posted on July 30, 2008 at 10:14 PMJuly 28, 2008
Supermarket Tabloid Spam
Although "tabloid" generally refers to the physical size of a newspaper page—smaller than the traditional newspaper page—here in the States the term more commonly connotes newsprint publications that have glaring and sensational headlines. Visit nearly any grocery store checkout line, and you'll see copies of The National Enquirer, The Globe, Star, and others shouting headlines about celebrities (dead, alive, or otherwise) in dire situations, UFOs, freaks of nature, bogus medical breakthroughs, and so on. The veracity of the stories and photos...well, I find it hard to believe that JFK had a love child with an alien from another galaxy.
Now, look at some of these sensationalist headlines:
- F.B.I. Looks Into Facebook
- US athletes banned from Beijing Olympics
- Research show that London is the second capital of India
- Air pollution forces Beijing closure
- Steve Jobs diagnosed with pancreatic cancer and has about a week to live
- A-rod dropped from team
- MRI show promise for detection of early Alzheimer's
- Dark Knight disapproved by Vaticans due to satanic links
- Cars that really transform
- British PM to quit
- China denies visa to German athletes, angering world community
- Huge oil spill off California coastline
- Bomb scare in UK stops traffic
- Army Of Two, Dick Cheney And John Mccain Invade Iran
- Cannibalism!........In The Usa
- [audio] Hillary Receives 3 A.M. Phone Call From Drunken Bill Clinton
- Miss USA falls in Miss Universe
- Trump tower collapses following fire
- Al Pacino investigated by police for mob funding
- Savage dog attack leaves students in critical condition
- New York Knicks team killed in bus accident
These are just some samples of the subjects and bodies of malware-luring spam that arrived here over the past few days. And these aren't the really sick ones.
The destination pages of the URLs supplied in the messages typically include a link that supposedly shows a video, but in truth downloads an executable malware loader. At the same time, those pages silently try to load malware through an invisible iframe element—particularly targeting unpatched Windows machines visiting with Internet Explorer web browsers. From my peeks into the iframe script attacks, it seems to me that more than one gang is at work here. Thus, the gangs appear to be competing for victims' attention through increasingly outlandish email lures.
It's like being in the supermarket checkout line while sitting in front of your computer. But when you're checking your iPhone email while actually standing in the checkout line, you are sucked into a vortex that makes you believe that Angelina Jolie's twins were delivered looking exactly like Sonny and Cher.
Posted on July 28, 2008 at 09:32 AMJuly 24, 2008
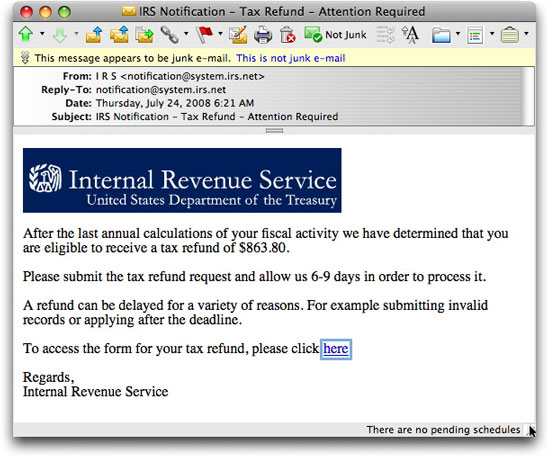
The Mother of All IRS Refund Scams
Phishing messages hiding in Internal Revenue Service clothing are nothing new (see here [2006] and here [2008]), so I barely gave one that arrived today much thought at first:
After verifying that the destination of the link (to a free web hosting service) wasn't going to blow up my computer, I checked out the page in a web browser to see how this crook was going to try to pry personal identity info from visitors. In the past, IRS phishing scams have aimed at Social Security numbers (the primary way the IRS distinguishes one private citizen from another) and credit card data (where the refunds are supposedly to be credited—what a joke!).
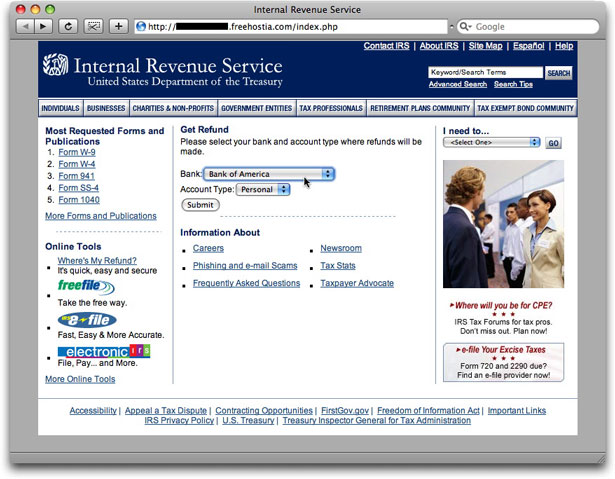
The destination page, however, was not something I had seen before:
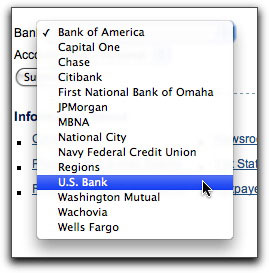
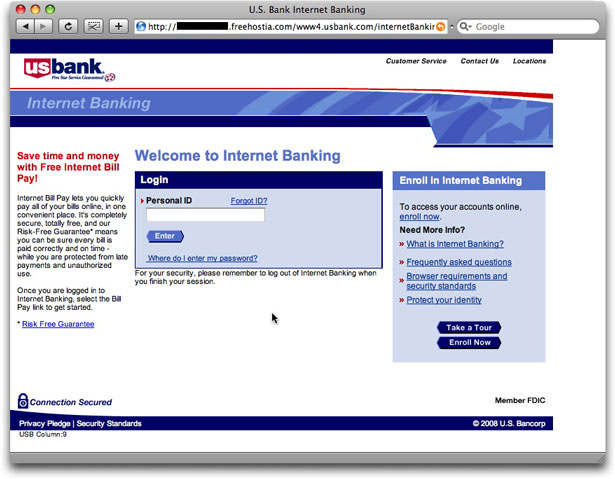
This one doesn't ask for any personal ID info on the landing page. Instead it presents a popup list of banks from which to choose where you want your refund posted (like the IRS offers for regular tax refunds):
When you click the Submit button, you are presented with a facsimile of the chosen bank's online banking login page, like this one:
Yes, friends, this guy had set up bogus login pages for every one of the banks in the list. In other words, by way of a single style of phishing message from an organization that would get every U.S. citizen's attention, this crook has found a way to phish for fourteen financial institutions! No more confusion for recipients who are, say, Bank of America customers but who receive a phishing message about Washington Mutual. One scam fits (nearly) all!
So, this really isn't an IRS scam. It's a Massively Multibank Online Phish, or MMOP for short.
To freehostia.com's credit, the entire site was taken down within a couple hours of my phishing message having been sent. A lot of work went into creating all that content—I mean, this guy had to rip off login screens from 14 bank web sites—so I fully expect the full package to resurrect itself elsewhere in the future. It seems that to Ben Franklin's precious list, "death and taxes," we must add "scammers."
Posted on July 24, 2008 at 08:39 AMJuly 22, 2008
The Amero?
Storm-like malware lures are flowing now with subjects and message bodies referring to an imaginary currency to replace the (sagging) U.S. Dollar, Canadian Dollar, and Mexican Peso. They call it the Amero (get it, an American Euro?).
The landing page has a picture of a supposed 20 Amero coin:
You have to admit that these crooks sometimes go to a fair amount of effort to make their clickable lures appealing to the unwary.
In addition to telling visitors to click on the false site image to download amero.exe, the page also includes a hidden iframe element, which loads the same obfuscated JavaScript (via ind.php) discussed here.
These guys keep pushing the Outrageous meter into the red zone with their email messages and phony sites (case in point, one that just arrived—Subject: Police open fire on elderly in Iowa). Pretty soon, you won't be able to believe anything that arrives in an unsolicited email. Heh heh.
Posted on July 22, 2008 at 08:34 AMJuly 18, 2008
Empty Medz
I love it when a spammer screws up such that any spam that gets through filters is bereft of meaningful content—there is no action that the user can take to benefit the spammer. It means that the spammer has expended something of value that is guaranteed to generate zero return.
<glee>Woo hoo!</glee>
Such has been the case over the past several weeks. A rather persistent medz spammer continues to spew empty messages with forged From: addresses mentioning well-known drug companies:
From: Pfizer Plans
From: Pfizer Market
From: Pfizer Promotions
From: Pfizer Discount
From: Pfizer Ltd.
From: Lilly Notice
From: Lilly Online
From: Lilly Group
From: Lilly Value
Most of the Subject: lines suggest that the message is about an order renewal. Of course there was never any original order to renew, but he hopes that mention of a renewal will get recipients to open the message.
Something in either the spam-sending bots or the way he's commanding the bot senders is cutting off the message part way through the email header.
<sarcasm>Boo hoo!</sarcasm>
July 17, 2008
Phisher Sniffing Out Moola
I hadn't even heard of Digital Insight until I started getting a series of phishing emails like the following:
From: account-updates@digitalinsight.com
Subject: Read carefully - Important NotificationDear Administrator,
We inform you that your account is about to expire. It is strongly recommended to update it immediately. Update form is located here <http://digitalinsight.ebanking-[removed].com/onlineserv/CM/> . However, failure to confirm your records may result in account suspension.
Confidential: Please be advised that the information contained in this email message, including all attached documents or files, is privileged and confidential and is intended only for the use of the individual or individuals addressed. Any other use, dissemination, distribution or copying of this communication is strictly prohibited. This is the automated message. Please don't reply.
From what I can gather at the legitimate web site for the company, it provides software and services to financial institutions so that those institutions can offer online banking. In other words, the customers aren't consumers, but financial institutions. The company claims to have nearly 1800 customers, almost all of which must have at least a modicum of interest in online security.
Thus, it seems odd to me for a phisher to try to spew phishing spam willy-nilly in the hopes of finding not only one of the 1800 customers, but to also find one who is gullible enough to fall for a phishing message. On the other hand, I've received phishing emails for tiny regional banks in the past, so this isn't completely out of the ordinary.
Perhaps the phisher is under the impression that because Digital Insight is an Intuit company that the login credentials might also work at an Intuit account. Kind of a stretch to me, but then I'm not a crook (jowls wobbling Nixonesquely).
The links for the several phishing messages I've seen lead to freshly minted domains whose (gotta be bogus) whois records list a variety of Russian and neighboring country addresses. The phisher is also having a helluva time getting the sites to work, or work for long. But he's still trying.
It reminds me of a story that Dr. Murray Banks, a comedian-psychiatrist, used to tell about a child who was unstintingly optimistic. When his parents gave him a box of horse dung as a Christmas present, he dove headlong into the contents and clawed his way through the muck, yelling, "You can't fool me...I know there's a pony in here somewhere!"
Posted on July 17, 2008 at 09:35 AM
I don't know if the following Subject: line for an ED medz spam was a slip of English translation or intentional:
Improve your organism state.
At least he didn't make any references to a microorgan-ism.
Posted on July 17, 2008 at 09:14 AMJuly 14, 2008
Another Day, Another Load [Updated 2]
I've been busy today away from the spam world, but I just wanted to comment briefly on a couple of items I saw in circulation.
The first is a modern variation on the 419 advance-fee scam. Instead of some prince bequeathing millions to me because he died in a car accident while on vacation without a will or living heirs (sheesh), this is a short and sweet invitation to the gullible and greedy:
From: <david@[removed].com>
Subject: ATM CARDThis is to officially inform you that ATM Card with a fund worth $6.8 Million Dollars has been accredited in your favor, Please Contact Mrs. Linda Hill (lindhill@[removed].net) With the following,
Full Name:
Delivery Address:
Age:
Occupation:
Phone Number:
Country:Best Regards.
Senator David Mark
Needless to say, the email address of my supposed contact person is at a free email hosting service. And a Google search of "Senator David Mark" shows it to be a longtime email scam name for a variety of 419 and other "offers."
Too bad. I could use $6.8 mill about now. What I'd really like to do is take that card and try to empty it in one visit...and watch the ATM implode.
Second, and more bizarre is the following:
Subject: Cheap fuel available in TexasMagic Johnson dies of AIDS at 49
http://[removed].ru/main.html
Aside from the disconnect between Subject: and body, the message displays a level of cruelty that is downright sick. The destination Russian web site uses no fewer than three ways to try to download view.exe:
- Through a clickable link on the page surrounding an image (only) of a YouTube knock-off video player (complete with added animated .gif spinner and words encouraging you to click to play the video).
- An automatic <META> refresh tag.
- A hidden iframe that loads and runs a JavaScript script to exploit old Internet Explorer vulnerabilities as a way to download and then run the file.
Obviously, the execution of this campaign is rather slapdash—not something usually associated with the Storm business. The scripting isn't anything interesting, and the view.exe file is already recognized by over 70% of the VirusTotal tests. Even so, those who might fall for this sick gag would be least likely to have up-to-date PCs—or know to check with real news sites.
Well, back to the grindstone to see if I can ever catch up on my behind.
UPDATE (14Jul2008/11:00PDT): The second item above has some company. Not as sick content-wise, but perhaps even more alluring to the unaware:
Subject: New Star Wars movie to be releasedYour friends have requested you to join them online
http://[removed].org/main.html
Same malware loading scheme as above. I suppose we'll see a ton of unrelated variations on the theme. The only thing that the email messages have in common is the URL to a page named main.html.
UPDATE (16Jul2008/09:25PDT): The campaign continues, with additional disconnects between Subject: line and message body, probably just selected at random from lists inside the bot's spamming program. Things like:
Subject: Rat poison found in bottled watersOur boss just screwed her real good
http://www.[removed].com.br/about.html
The destination URL for this one now ends in about.html. The page, itself, tries to load watch.exe via the same three methods described above. On the other hand, the crook has now attempted to obfuscate the JavaScript delivered to the hidden iframe. He managed to find a huge obfuscation library, and uses 400 lines of JavaScript code ultimately to generate a very simple script—the same one described above to exploit woefully unpatched PCs.
Posted on July 14, 2008 at 07:13 PMJuly 12, 2008
It's Tough to Be Opaque on a Transparent Internet
Several days ago, I posted about someone apparently trying to hack into my Apple ID account. Today there was a more directed attack, as I received a notice from Apple (yes, a real, unphishy notice) that someone had made too many invalid attempts to answer my account's security questions.
Security questions come in all shapes and sizes. Typically, they ask you to enter your favorite this or that. On the one hand, you want to choose questions that have answers you'll remember three years from now; on the other hand, you don't want to supply answers that everyone on the planet knows. For instance, Charlie Brown might be tempted to select the "favorite pet's name" question because he'll know to answer "Snoopy" even when approaching senility. But everyone on his block also knows that answer because it's something widely known—including to a worldwide audience who reads the cartoon strip (blog precursor). Charlie must either choose a different security question, concoct a memorable (but undiscoverable) system for weaving numbers into the letters of the name, or intentionally submit a radically different name to throw off the thieves. Snoopy's relatives aren't candidates because they, too, are known and would be guessed by crooks.
With so many social networking and personal web sites on the Internet these days, it's all too easy for trusting souls to reveal everything they like—their favorites, their coolest vacations, their house paint colors—to try to hook up with like-minded people. Unfortunately, it can be dangerous to use this kind of public information to try to secure something as valuable as your various internet accounts.
And to the clown who's trying to get into my Apple ID account, I repeat that my web site writings, books, and Usenet postings dating back to the Stone Age offer no clues to my secret questions and the strings of characters used for answers. Allow me to offer you the words of Bender Bending Rodríguez: Bite my shiny metal ass!
Posted on July 12, 2008 at 02:27 PMJuly 09, 2008
A Gazillion Reasons--Pick One
I was looking up the whois information for a spamvertised domain today, and encountered what seems to be the ultimate in lazy user interface design programming. It's possible that the "designer" thought he was being helpful by offering reasons why a search didn't work, but this laundry list approach is ridiculous:
[Querying whois.internic.net]
[Redirected to whois.internet.bs]
[Querying whois.internet.bs]
[whois.internet.bs]
We are unable to process your request at this time. The whois informationis [sic] unavailable for domain ([removed].com) for one of the following reasons:(1) Too many simulataneous [sic] connections from your host;
(2) The domain you requested is not with this Registrar;
(3) You have exceeded your query limit;
(4) Your IP address has been restricted;
(5) Whois data is not available for this domain - check back in 48 hours when our server is updated;
(6) Access has been restricted to ensure operational stability;
(7) A system error has occurred;
(8) The time limit for your request has expired;
(9) The IP address provided is not valid or the host specified by the IP address does not exist;
(10) There is an error in what you have inputed [sic] or requested;
(11) An unknown error has occurred;
(12) The domain is not currently registered;
(13) The domain you requested contains invalid characters;
(14) The domain you requested is too long;
(15) The domain you requested begins or ends with a dash;
(16) The domain you requested is a third or fourth level domain;
(17) You did not specify a domain name.
Yeah, that should cover it.
Note that the registrar here is internet.bs, where the .bs country code top-level domain is for the Bahamas. I can imagine a laid back lifestyle in the Bahamas, but the coding behind this error message is just too laid back. I mean there must be code branches that trigger errors (raise exceptions) for each of those cases. The programmers clearly are aware of the possible cases and even have error wording for each case. I get the feeling that if any error condition occurs, they simply spit out the whole list, rather than report the specific issue that raised the exception. Supplying too much information in this case equals supplying no information.
.BS. Really!
Posted on July 09, 2008 at 08:49 AMJuly 08, 2008
Storm Upping the Ante: War on Iran
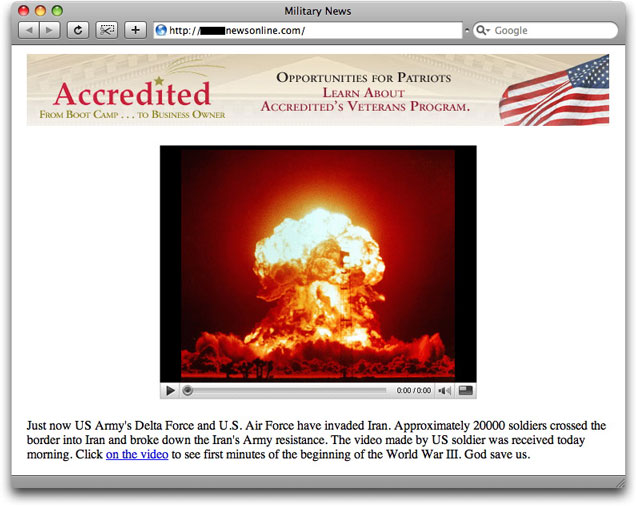
Here we go again. A phony "report" of a 9.0 earthquake in Beijing wasn't enough. Now Storm is trying to spread itself on the pretense of supplying news about the U.S. declaring war on Iran. Here's the one sample I've just seen:
Subject: Plans for Iran attack beganUSA declares war on Iran http://[removed].com/
There will certainly be many more variations on this theme in other messages. The destination page is in the same format as the July 4th page:
Clicking on the upper banner image downloads form.exe; clicking on the fake movie player image downloads iran_occupation.exe. The page also includes the same hidden iframe attack with the ind.php program described at length here (PDF file).
News of this nature would obviously be monumental, if it were true. Check with cnn.com or other trusted news sources before clicking on any link in an unsolicited message, no matter how official the link's domain may appear.
Posted on July 08, 2008 at 05:00 PMJuly 07, 2008
An Unnerving Password Reset Email
This has happened to me a few times in the past, but it's no less creepy when it happens again.
I received an email from Apple today supplying me with instructions on how to reset my Apple ID password. This is the kind of message you get from a account suppliers when you click the "Forgot password?" button or link on login pages.
Now, before you think it might have been a phishing trick, I checked the message's headers and closely examined the URL supplied in the message. The body of the message addressed me by the name I use with my Apple ID account. This really came from Apple, no question about it.
It means that someone had entered my login address into an Apple login page and clicked that button. Did someone try to get into my account by testing some passwords? Quite possibly. An Apple account is a valuable target because it's the gateway to buying iTunes and Apple Store stuff. Many of the screenshots I've posted in this blog clearly reveal me as being a Mac guy, so it would be logical that I'd have such an account. As I've said before, if you have something of value, one or more crooks will try to take it from you.
Just to be sure, I manually logged into my account and found everything to be in order. If crooks believe they can find clues to my passwords in the verbiage of my web sites, they're sadly mistaken. Or, from my point of view, gladly mistaken.
Posted on July 07, 2008 at 05:30 PMJuly 03, 2008
July 4th. Storm. Duh. [Updated]
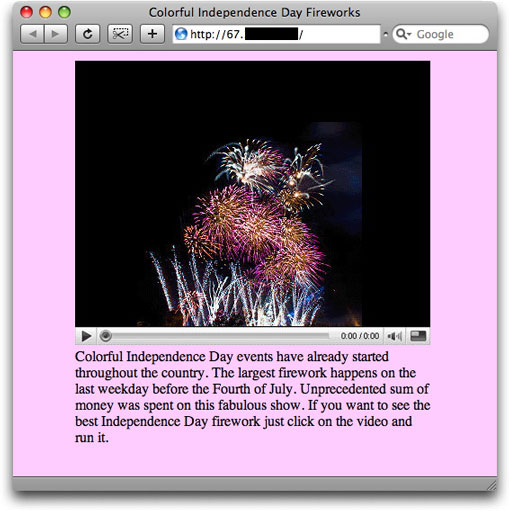
As night follows day, the Storm guys are doing their thing for the U.S. Independence Day holiday, July 4th:
Subject: Celebrations have already begun
The email message is a simple sentence, such as "Happy Fourth of July" followed by a numeric IP address. The destination page is the same format as the phony Beijing earthquake malware lure:
Content is a false video player image, which is a link to download fireworks.exe, a malware load that VirusTotal shows identification by 15 of 33 antivirus systems. But the page also includes the same hidden iframe element and ind.php program described in Love Hurts Even More. Check the scripting analysis document linked from that post to learn more about this multiple-exploit drive-by attack.
Don't let this M-80 explode inside your PC.
UPDATE (4 July 2008): Just saw this subject line variant: "Stars and Strips forever." Ooh, so close. Sounds more like an ad for a Las Vegas adult revue.
UPDATE (6 July 2008): On July 5, the same email messages continued to arrive, but with links to domain names rather than numeric IP addresses. The domain names I've seen have the word fireworks embedded somewhere within.
Posted on July 03, 2008 at 04:26 PMJuly 02, 2008
Love Hurts Even More
Back in May, my blog entry Love Hurts told the quick story of a Storm-like email message that tried to lure victims to a site that automatically downloaded an executable Windows program. A month later, a new wave of such messages started flowing, but the destination at the end of the email links is far more insidious.
As before, the range of message Subject: lines, while all in a romantic vein, are all over the place. Here is a sampling of ones I've seen:
- Can't stay away from you
- Lucky to have you
- My heart belongs to you
- I want to be with you
- I Wanna Be With You
- Crazy in love with you
- Lost In Love
- For you...Sweetheart!
- You make my world beautiful
- My heart beats just for you
- I'll Still Love You More
- Love me tender, love me true
Ugh. I'm getting that bad taste one gets from having eaten one-too-many of those chalky candy hearts with ooey-gooey phrases on them. "I Wuv You."
Message bodies are a continuation of the one-sentence theme employed by not only a lot of recent malware lures, but recent medz and knockoff brand-name goods spammers who use the same address lists. I'd repeat some of the message bodies here, but reciting too many lines in the spirit of "Missing you with every breath" will make me vomit.
What these messages want you to do is visit the URLs at the end of the sickly sweet lines. Some email clients turn anything they recognize as a URL into a clickable link, unfortunately making it easier to go in search of your untrue love. The URLs are to a bunch of plain-language .com domain names, such as makinglovedirect.com (now suspended the last time I checked).
Visiting any of those sites with an unpatched Internet Explorer could land you in a world of hurt. If you ever see the following page, it could be too late for you:
No, I really wasn't the lucky 10,000th visitor. Everyone is the lucky 10,000th visitor. Just as I've written that the assertion "this is not spam" means that it's spam, the assertion that "this is not a joke" means that it's a joke.
Although two downloads require clicking on either the image or "click here" link, there is an unseen iframe element that automatically targets numerous vulnerabilities. The malware distributor uses obfuscated JavaScript to make the initial delivery. Because I've been a JavaScript nut since before Day One, I spent some time deconstructing the delivery mechanism of this iframe. Rather than bore non-scripting blog readers with the gory details, I've created a separate document that shows my findings. You can download the 374KB PDF file here (Creative Commons licensed).
Almost all of us want to be wanted and loved. Malware distributors exploit that desire by making us believe we have secret admirers and might even get lucky with the right connection. With this malware campaign, you won't get laid, but you might well be screwed.
Posted on July 02, 2008 at 09:23 AM