| Home | The Book | Training | Events | Tools | Stats |
April 28, 2011
Bogus Facebook Spam Report
Another day, another badly-written malware delivery email message. This one claims to originate from Facebook, trying to make you think that your Facebook account has been hacked and is being used to send out spam. Here's the message:
From: Facebook Abuse Department
Subject: Spam from your account
This is a post notification
Spam is sent from your FaceBook account.
Your password has been changed for safety.
Information regarding your account and a new password is attached to the letter.
Read this information thoroughly and change the password to complicated one.
Please do not reply to this email, it's automatic mail notification!
Thank you for using our services.
Your Facebook!
The attachment that arrived with the message I saw was named Attached_SecurityCode66002.zip. I assume that the numerals will be different for other recipients as the random number generator does its thing when sending the messages. The attachment is a Windows Trojan loader.
This round of spam took the slight extra step of forging a part of the email header that might trick the knows-only-enough-to-be-dangerous recipient into believing the message originated from a facebook.com server. The topmost Received: header is as follows:
Received: from facebook.com (cust-66.116.106.39.switchnap.com [66.116.106.39] (may be forged)) by dannyg.com (8.12.11.20060614) id p3T0fFA8061294 for <[removed]@dannyg.com>; Thu, 28 Apr 2011 18:41:16 -0600 (MDT)
My email server composed everything in that header field except for the bit before the first set of parentheses. That part is forged. But my server looked up the originating IP address and did a reverse lookup to find the real domain and server that matches — likely a switchnap.com customer's botnetted PC, and nothing to do with Facebook.
Just like the malware-delivering email message that claims you bought hundreds of dollars of stuff (so open the attached order info document), this message uses fear, concern, and/or outrage to trick recipients into opening the attachment before thinking.
When an unexpected message asks you to act in any way — click this, open that — the only action you should take is to click Delete.
Posted on April 28, 2011 at 06:21 PMApril 26, 2011
Another Spam Cost
I saw a Trojan-attached email message this morning falsely claiming to have originated from Bobijou, Inc., a purveyor of pearl jewelry. Just so it gets picked up by search engines, here is the full text (typos left intact):
From: Bobijou Inc
Subject: Successfull Order 394311Thank you for ordering from Bobijou Inc.
This message is to inform you that your order has been received and is currently being processed.
Your order reference is 271790.
You will need this in all correspondence.This receipt is NOT proof of purchase.
We will send a printed invoice by mail to your billing address.You have chosen to pay by credit card.
Your card will be charged for the amount of 925.00 USD and "Bobijou Inc." will appear next to the charge on your statement.You will receive a separate email confirming your order has been despatched.
Your purchase and delivery information appears below in attached file.
Thanks again for shopping at Bobijou Inc.
The attachment is a tiny (9.68 KB) file named Order details.zip. Of course it's a Trojan, and the threat of being billed $925.00 will cause plenty of recipients to blindly open the attachment. If they have up-to-date antivirus software installed, they'll probably be protected, but even with such protection, I would never attempt to open the attachment.
With a little digging, I discovered that Bobijou was the victim of a similar attack in early March 2011. According to the company's official Facebook page, the previous spamming campaign caused over 7000 people to contact the company to ask, essentially, "WTF?". Imagine having to respond politely to 7000 extra emails from current or potential customers (some of whom are probably really pissed off). How much would that cost you or your company?
Scams utilizing email "order confirmations" for expensive merchandise you never ordered go back many, many years. The goal of the sender is to trick the recipient into getting in a huff and following directions to investigate the order. In the meantime, the abused brand is saddled with a huge support nightmare caused by some anonymous asshole.
Posted on April 26, 2011 at 10:19 AMApril 22, 2011
Pathetic Bank of America/AOL Mule Recruitment
I don't know where to begin with this spam message:
From: Bank of America Help You 2Today Subject: 2 minutes of your lifeHelp yourself
Our organization starts recruiting employees willing to take part in well-paying research studies conducted by leading online busineses.
Your opinion as a consumer is important for the success and profitability of many business ventures.
You can earn very well for participating in on-line surveys, focus group discussions, and product/service evaluations.
This is a one time offer for you to become one of our highly valued survey taker and earn up to 3000$ month .This is a sponsored camapaign by Aol Online and Bank of America that comes to encorage people to take on a second
part job and earn some extra founds in this difficult times.If you want to be one of the many involved in this campaing please complete the following
Full name -
Address -
City -
State -
Zip Code -
Nationality -
Sex -
Marital Status -
Date of Birth -
Home phone number -
Cell phone number -This information will not be used in any way to harm or denigrate your status neither will it be shared.
By replaying to this email we have your acceptance to engage you in this program.Thank you for your time
Sincerely,
Bank of America Help Assistence
I swear I should hire myself out as a copy editor for scammers and finally earn some money in this spam game. The above email message has so many typos, grammos, and cultureos, that my fixes could guarantee a much greater response rate. The author of the above message is not from the U.S., so my help would be especially valuable if the goal is to lure unwary Americans to the phony baloney business (I believe it's ultimately to recruit money laundering mules).
My only hope is that when the above attempt fails, the crook will tell others that internet scamming doesn't work (when, in fact, it's low quality internet scamming that doesn't work).
Posted on April 22, 2011 at 12:39 PMApril 04, 2011
Phishing Phield Day Ahead
Those of us who keep an eye on internet spamming and scamming are shaking our heads in disbelief at the revelation of a major theft of an email provider's database. The company, Epsilon, manages customer mailings for a large number of large corporations, almost all of whose names you'd recognize in an instant. The list includes many giant financial institutions, as well as companies where you conduct online commerce.
So far, 35 companies' customer email lists have been reportedly stolen. In theory, the information includes both the email address and name of the person. It's one thing to have just your email address find its way into the spam economy, but if a crook knows:
- Your email address
- Your name
- That you have done business with Company X
then it's less than an hour's programming to devise an ultra-convincing phishing scam that targets customers of Company X by name. Instead of starting the scam email message with "Dear Member" or "Dear Customer" as they usually do, it will begin with "Dear Danny Goodman" or whatever name you have on file with that vendor. Not only that, but the scammers will now be very efficient in their phishing attempts because they won't be wasting millions of messages on random email addresses hoping to find a match for a customer of the phished company.
In fact, it wouldn't surprise me if the phishers use the Epsilon breach as a premise in their phishing emails: "You've probably read about the email address theft of our accounts, so please, Danny Goodman, verify your Company X account by clicking this link within the next 24 hours or we will permanently close your account with us."
For more about the potential implications of the Epsilon theft and a list of known companies whose lists were lifted, see Brian Krebs' blog posting.
This event may be the email equivalent of the Great Train Robbery.
Posted on April 04, 2011 at 10:57 AMApril 03, 2011
Advance-Fee Scam Using Coca-Cola Brand
Coca-Cola is one of the world's most recognized brand names. The impression the average consumer has (in virtually any country) is that of a large international corporation often offering valuable prizes for various contests throughout the year. Thus, when an unsolicited message arrives via email or SMS advising that the recipient has won a substantial amount of money, plenty — and I mean plenty — of them believe it's their lucky day and begin to follow instructions to collect their alleged windfall.
There are two problems with this whole thing:
- The contest, drawing, or promotion is phony, abusing the Coca-Cola brand name.
- Many recipients get hooked by the criminals and end up losing sizable sums of money — usually money they can't afford to lose.
I have read about and seen video of victims of these advance-fee scams who are in complete denial about the possibility that the offer is a scam. After shelling out sometimes hundreds of thousands of dollars they'll never see again, these folks continue to believe there is a pot of gold at the end of the trail. I'm not talking about uneducated people, either. University professors and professional people have been victimized for the most amounts (when reported). Retirees have also been taken for not only their entire retirement portfolios, but additional amounts they've borrowed against their homes and personal loans from family and friends.
As more and more publicity about internet scams reaches the mainstream media, some recipients who don't immediately spot these scams are at least pausing for a moment to question the authenticity of a message arriving with such promising news. I truly hope it's the case with recipients of a message I saw here the other day, claiming to come from Coca-Cola in England, telling me I won £450,000.
I was doubly alarmed because the email message body was very sparse ("OPEN THE ATTACHMENT FOR YOUR ATTESTATION"), with the details contained by a Microsoft Word attachment. Now, I am fully aware that Microsoft Office documents (Word, Excel, PowerPoint) have been conduits for malware because the documents can contain programming scripts capable (in unprotected computers) of opening back doors for the installation of more malicious software. This applies, by the way, to Macintosh and Windows computers equally (depending on the version of Office for Mac you run).
Few casual computer users know how to pass a suspicious email attachment through a free virus detection system, such as VirusTotal (and it can be a little intimidating to the technophobic). As much as I wanted to examine this .doc attachment, I wasn't going to do anything with it in Word until I submitted it to VirusTotal. It came back with a completely clean exam. That's not to say the file is 100% clean — an inventive crook can always dream up a brand new exploit that is not yet detectable by the dozens of VirusTotal checks — but the message had arrived several hours earlier, giving the antivirus (AV) community plenty of time for at least some AV systems to have found any nastiness.
The attachment is a 4+ page document, originally named CONGRATULATIONS!!!.doc. I have output the contents from Word as a safe PDF file, which you can download here (1.6MB) to view at your leisure.
My copy of the attachment is a letter with a poorly designed Coca-Cola faux-letterhead. The corporate address is in Liverpool (Coca-Cola's UK office is in London) and two telephone numbers with cell phone exchanges. It begins with the following:
Dear Winner,We want you to remove every skepticism from your mind
because this award is legitimate from COCA-COLA
COMPANY ENGLAND,
Any message that begins by telling you it's not a scam or spam is lying. Period. The more a message professes its authenticity, the bigger the lie.
After more blather about filling in a verification form to let them release the check that "has been vaulted safely with out corresponding Bank", comes an image that interested me. The image is shown here, along with the caption from the message:
Prof.Alex Kingston and Dr.George Williams, Past Winner in Coca-Coca Company Online Promo England,
I studied the image closely. Unless it had been Photoshopped, it certainly appeared to have been taken at a Coca-Cola building. Knowing that the company is headquartered in Atlanta, I suspected the leftmost flag was the Georgia state flag. Two seconds later on Google, I proved that correct.
So what about the people in the shot? I didn't recognized either of them (although I should have, as I'll mention shortly). The names in the caption weren't particularly distinctive, so I didn't want to follow those rabbit trails on Google. Instead, I used Google to search for images associated with Coca-Cola Company. The results are mostly logos and advertising art. Fortunately, the image search in Google lets you view pages of results in just one downloadable Google page, so it's easy to keep looking ahead. Down around page 14, I begin to see images of one of the two men in the emailed photo:
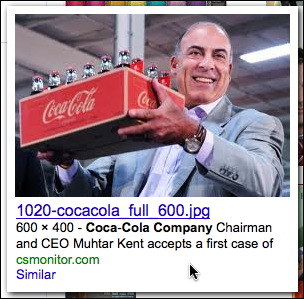
So, the guy on the right is the CEO of Coca-Cola, Muhtar Kent, and neither of the two names shown in the email photo caption. Now the hunt was on for the source of the email photo. A Google image search for Muhtar Kent yielded the following image on page 2:
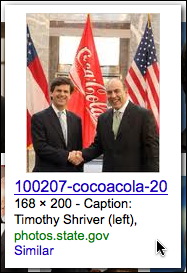
The individual on the left is Timothy Shriver, Chairman of Special Olympics. The photo was taken when Kent was appointed to the Board of Directors of Special Olympics in 2007. (Shriver had been a guest on The Colbert Report a couple of nights earlier. Although I didn't recognize him from the photo, it is definitely him.)
In all of about three minutes of Google image searches (and no high-tech examinations of email headers and such), I found the email photo caption to be a complete lie. Would that finding by a more trusting recipient have dissuaded him or her from believing the letter? It's hard to say.
Such a believer would also probably not be put off by the rest of the letter with its "Congratulations" image artwork that would have been chosen by a third-grader assembling a web page.

And how about the email address for responses? Not to coca-cola.com, but to a free live.com email address. My, how professional! I'd also swear I've seen that "Approved" rubber stamp and signature in other scam emails over the years.
What will it take to convince a believer that messages like this one are scams? What do you tell a young girl who, upon opening a birthday present filled with horse manure is thrilled and convinced there's a pony in the backyard?
It seems that those victims who send the most money to the crooks are the ones who have been warned by their banks and even local enforcement not to send a dime. This isn't like the genuine state lotteries, where you stand at least a chance — extremely small though it may be — to win something; with these advance-fee scams, you stand zero chance of receiving anything, and a 100% chance of losing your hard earned dough while being conned by some very smooth and convincing criminals.
Posted on April 03, 2011 at 04:35 PM
