| Home | The Book | Training | Events | Tools | Stats |
October 26, 2006
Something New in Spam Crockery
Spammers sometimes try to make their illegal messages sound legitimate in one way or another. Look at this piece of trash:
From: "Email" <Email@------.net>
To: dannyg@dannyg.com
Subject: Mail.Fwd
Hi, we are a forwarding service which is forwarding this website & material to you as per requested by the individual.
Request Sent By: Sara
Regarding: Weight
Message: Thought you might be interested in this or be able take advantage of it.
Website: http://www.011.-----------.com
Burr Forwarding Services Inc.
New York, NY
If there is such an outfit as Burr Forwarding Services, Google (Web and News) doesn't know anything about it (until this posting). Their "forwarding" service uses a botnetted PC in South Korea. What a classy service. Frankly, it all sounds like burrshit to me.
Posted on October 26, 2006 at 10:18 PMOctober 24, 2006
Sophisticated Tools in the Hands of Idiots
Crooks can buy phishing kits, which give them all the software and templates they need to set up a phony site on a hijacked server and send the phishing messages through botnets.
But put the kit in the hands of an idiot, and he'll try to do something special with it. Customize a bit here or there.
And so, we find one genius who uses a competently composed PayPal phishing message template, only to give it the following Subject:
Please Confirm Your Tranzaction!
Sorry, but PayPal just isn't that kewl.
Posted on October 24, 2006 at 10:44 AMOctober 22, 2006
[Sigh]
There are so many hijackable servers currently running in the world that phishing gangs have the equivalent of enormous site hosting facilities at their disposal—for free.
These servers come in all shapes and sizes. ISPs have default web servers running on IP addresses they have yet to assign to customers. Organizations that manage their own IP address blocks (educational institutions in particular) also have these silent, unused systems running 24/7, often readily available to access through default passwords or unpatched applications that every cracker worth his salt knows how to crack. Some hijacked servers aren't really web servers, but, rather, email servers that have enough basic software installed to allow a cracker to erect a phony phishing web site on a different port or in a semi-hidden subdirectory.
Crackers constantly scan IP addresses around the world, looking for a variety of vulnerabilities. It's as easy as counting to 255 (see Spam Wars, p.313). Some crackers are looking for PCs to take over for botnets; others are searching for servers that can be used for additional nefarious acts.
Unlike hijacked active web sites, where the site owner has a vested interest in getting the fraudulent phishing pages off the server, these ghost-like servers are often difficult to get taken down. When I trace a phishing site's IP address to a block belonging to a Chinese government ministry, I dutifully report it, but also sigh inside, knowing that the likelihood of quick action is extremely low.
I suspect that part of the problem in getting quick action in many countries is that they don't appreciate the harm that can accrue from online identity theft or fraudulent online banking transactions (e.g., a PayPal withdrawal made from your account after you've surrendered your address/password to a PayPal phisher).
I also imagine that another part of the problem is that some of these hijacked servers are so buried within established systems that the current administrators may not even know where they are physically (e.g., on a university campus) or how to disable them (the original user and his/her password are long gone, and the administrator doesn't have cracker skills).
To me, the cavalier mindset with which IP block holders treat hijacking incursions is frightening. A phishing site is the least of the problems that a hijacked server could cause. A vulnerable system is a vulnerable system. If one crook can install some simple PHP software to run a phishing site, another crook can install a component of a massive denial-of-service attack on the same server. Multiply that times hundreds of servers, coupled with delays of days or weeks in getting such systems shut down, and we've got a huge problem.
Ideally, IP block holders should be held accountable for securing their systems quickly. But I can't even imagine a global enforcement scheme that could work.
And so, as I informally monitor progress in taking down phishing sites that I report, I sometimes get discouraged by the lack of action. After I confirm through safe means that a phishing site's HTML/CSS/JavaScript code isn't doing anything harmful, I load the page in a Mac browser window tab and periodically see if the page is still active.
When the tab bar fills up, with some tabs dating back a couple of weeks, I sigh inside again. I fear for the phishing victims. And the Internet.
Posted on October 22, 2006 at 11:58 AMOctober 14, 2006
Comcast Fails to Filter Comcast Phisher
Like millions of residential broadband customers in the U.S., I connect via Comcast. Unfortunately, in my little town, it's the only choice for broadband, so it's that or dial-up. The result is that I have (among many others) a Comcast email account, which I use infrequently.
It used to be horrible at detecting and sequestering spam in my inbox. Even though I had not used my Comcast address anywhere, it had been discovered, either through dictionary attacks on Comcast or (as happened at AOL a year ago) insider theft of account names. Once your address is in spammers' hands, it's like flatulence: It can't be put back, and it stinks.
I have to admit, however, that after a few sessions of marking up tons of messages as spam, the account suddenly got much smarter about pre-deleting garbage and shunting the handful of remaining spam messages to a "Screened Mail" folder.
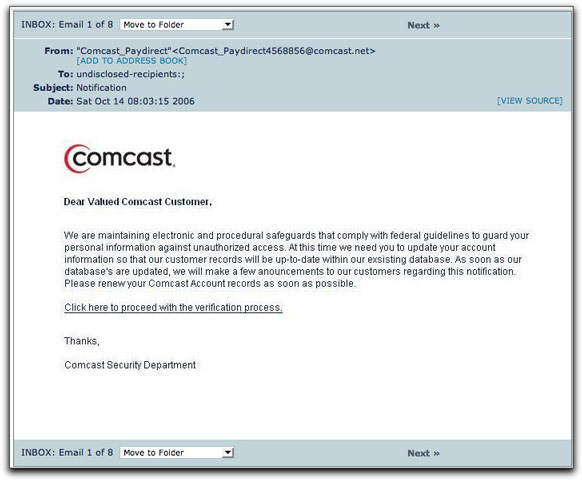
Imagine my surprise, then, to see that my Comcast inbox contained both a legitimate promotional message from Comcast and another one that immediately rendered as follows:
Now, my account is set up to not download images. But this message—which consists of nothing more than one downloaded image surrounded by a link—fetched the image from a server in Colombia. Was this solely because the From: address was forged as a comcast.net address? The originating IP address of the message had nothing to do with Comcast anywhere.
The page at the other end of the link is the kind that contains a form asking for everything but your shoe size (credit card info, Social Security Number, date of birth, mother's maiden name, and drivers license number). It asks for everything that allows a complete false identity to be created—with your name. And, yes, more than 12 hours after this message arrived, Comcast freely allows me to visit the IP address of the phony, identity-thieving page.
Incredible. Incredible. Incredible.
Posted on October 14, 2006 at 11:54 PM
West African (and elsewhere) scam artists try to make their messages sound like personal appeals to the addressee. They want the addressee to believe that he or she has been luckily singled out from all people in the world (with email addresses, anyway) as the one to benefit from a fortune hidden away in a secret account blah, blah, blah.
Such is the tone of one I received today, which reads...
Dear Good Friend,
Compliments of the day and God's blessings .
I am glad to inform you that I have successfully concluded the transaction, the money has been transferred to Swizerland.It is done through the assistant of MR.JAMES who is a Swizerland base business .Currently I am in Swizerland with him and children.
However, I did not forget you because you are the source of my success,you made me what I am now though you are not there to complete this project with me but I gave all the credit and thanks to you. I know it is not your fault or rather your wish to back up on me and the transaction.
In appreciate of your assistance I have mapped out as a compensation and wrote on your favour a certified bank draft worth of $2,500,000.00 Million United States Dollar Only I left the draft with my Secretary MR.CHRISTIAN on my departure to Swizerland. I would like you therefore, to contact him on the below info so that he can mail it to you.
ATTN: MR.CHRISTIAN
Email: <removed_for_your_safety>@yahoo.fr
I would have love to call you from Swizerland where I currently reside but due to the recent terrorist attack Mr.Ferraro advice me not to call because all internatonal calls are been monitored by the Swizerland authority.
Contact my secretary in Republic of Benin so that he can release your bank draft to you. I will stop here. Once again, thank you very much and remain blessed with your family.
Regards,
MR.JAMES
Boy, I could use a break like that. Someone finally recognized me for my contribution to his success. Woohoo!
Except...
...this idiot included all 80 email addresses in this particular burst in plain view in the To: field of the message. Not BCC (where there may have been more, but you can't tell from the header). My address is in a block of "d" user names (a bunch of Dans and Dave/Davids).
So much for feeling special. No, Mr. James, you don't really care about me. You make me feel so insignificant. Boo hoo.
Plus, you really piss me off because if any of my 79 blockmates receive this message, and if their machines are infected with any one of thousands of pieces of malware (a 35% chance by some estimates), my email address will be harvested from their computers and added to yet more porn/medz/phishing/419/etc. spam lists. It's the Circle of Strife.
Posted on October 14, 2006 at 11:25 PMOctober 07, 2006
Ooh, Stanley. I Can Hardly Wait!
Sent from an IP address somewhere in Spain (possible vitals xxx'd out):
Date: Sun, 08 Oct 2006 09:48:48 +0800
Reply-To: "Stanley" <xxx@balitribune.com>
From: "Stanley" <xxx@balitribune.com>
To: <dannyg@dannyg.com>
Subject: Re: Possible meeting
Hire,
i am here sittin!g in thea internet c!affe. Found your email and decided to write. aI mighta be coming to your place in 14 days, so I decided to email you. May be we can meet? I am 25 y.o. girl. I have a picture if you want. No need to reply here as this is not my eamail. Write me at xxx@xxxemailz.com
When you get to "my place," drop me another email. Please note, however, that (assuming you are a girl ["Stanley" or otherwise]) you'll have to compete for my affections with "Sara" who wrote to me last night from an IP address in France and a different response address with this:
Date: Sat, 07 Oct 2006 20:14:53 -0900
From: "Sara" <xxx@fast.net>
To: <dannyg@dannyg.com>
Subject: Re: Possible meeting
Hire,a
!
i aam here sitting in the internet caffe. Found your email and decided to awrite.! I might be coming to your place in 14 days, so I decided to email ayou. May be we can m!eet? I am 25a y.o. girl. I have a !picture if you want. No need to reply here aas this is not my email. Write me at xxx@xxxemailz.com
Three-way. My place. In 14 days.
UPDATE (8Oct2006/13:10PDT): I just discovered that the email addresses used for both contacts are to a medz spamming domain. I have xxx'd out part of the domain to prevent accidental visitation. And maybe it means that "Stanley" and "Sara" will bring plenty of VrIgAzGoRqA to our three-way.
Posted on October 07, 2006 at 06:14 PMOctober 04, 2006
Speechless
Ok, maybe not speechless, since I'm writing about it. But I'm left scratching my head nonetheless.
At approximately 11:00am PDT on Sunday, 24 September 2006, I filed an abuse report via email to the holder of an IP block containing an IP address of a server that had been hijacked by a phisher. The company, Corporate Colocation, Inc., is based on Los Angeles. I don't know anything more about them than what their Web site advertises.
It's not uncommon for an IP block owner to parcel out blocks to smaller ISPs, who then resell Internet access on a local or regional level. Unfortunately, IP whois records rarely reveal contact information for the last link in the chain—the small ISP responsible for customer contact. Therefore, I expect the big block holder to forward the complaint to the sub-block holder, who can then handle the situation with the customer whose server has been hacked. From what I can tell, this type of communication happens frequently, and phishing pages are regularly and relatively promptly taken down in these situations.
So, this morning in my inbox is a copy of an email that Corporate Colocation sent to the small ISP about my abuse report. Normally, I would consider that a nice touch to keep me informed about progress in handling the complaint. But in this case, Corporate Colocation took ten days to pass along my complaint.
T E N D A Y S!
Since phishing sites are most effective (a.k.a. damaging) in their first 48 hours, why is this outfit waiting ten days to release the hounds? In truth, their "Abuse Department" probably didn't even check the URL I had submitted. My original report also went to another contact address, and the site was taken down much closer to the original report date. Sending this notice was a complete waste of everyone's time.
Can an IP block holder and supposedly modern-day service provider be so clueless about the speed needed to take down a phishing site? Apparently so.
Posted on October 04, 2006 at 11:34 AM