| Home | The Book | Training | Events | Tools | Stats |
October 14, 2006
Comcast Fails to Filter Comcast PhisherLike millions of residential broadband customers in the U.S., I connect via Comcast. Unfortunately, in my little town, it's the only choice for broadband, so it's that or dial-up. The result is that I have (among many others) a Comcast email account, which I use infrequently.
It used to be horrible at detecting and sequestering spam in my inbox. Even though I had not used my Comcast address anywhere, it had been discovered, either through dictionary attacks on Comcast or (as happened at AOL a year ago) insider theft of account names. Once your address is in spammers' hands, it's like flatulence: It can't be put back, and it stinks.
I have to admit, however, that after a few sessions of marking up tons of messages as spam, the account suddenly got much smarter about pre-deleting garbage and shunting the handful of remaining spam messages to a "Screened Mail" folder.
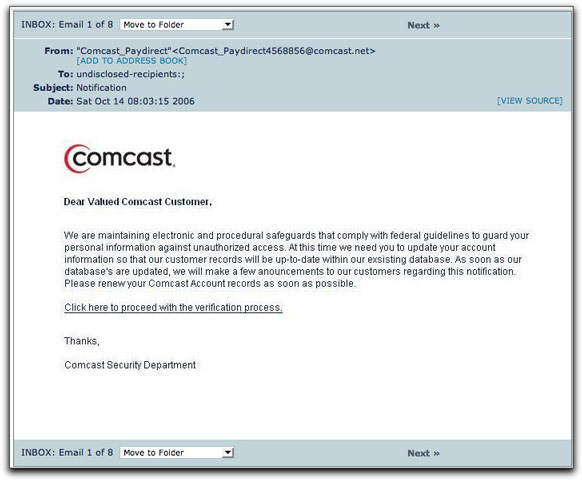
Imagine my surprise, then, to see that my Comcast inbox contained both a legitimate promotional message from Comcast and another one that immediately rendered as follows:
Now, my account is set up to not download images. But this message—which consists of nothing more than one downloaded image surrounded by a link—fetched the image from a server in Colombia. Was this solely because the From: address was forged as a comcast.net address? The originating IP address of the message had nothing to do with Comcast anywhere.
The page at the other end of the link is the kind that contains a form asking for everything but your shoe size (credit card info, Social Security Number, date of birth, mother's maiden name, and drivers license number). It asks for everything that allows a complete false identity to be created—with your name. And, yes, more than 12 hours after this message arrived, Comcast freely allows me to visit the IP address of the phony, identity-thieving page.
Incredible. Incredible. Incredible.
Posted on October 14, 2006 at 11:54 PM