| Home | The Book | Training | Events | Tools | Stats |
September 27, 2007
Stormy Games, Part Deux
The lure of free computer games (initially reported here) continues. Sadly, it must be working to turn lots of new machines into bots. Lots of bots.
One example of today's simple email messages:
Subject: Would you like to play a game?The internet is FREE again, thanks to Arcade World. 1000's of Free
games. http://[USA.numeric.IP.address_removed]/
Hosted on someone's computer in or near Austin, Texas is the following professionally-looking web page:
Click on any link or "click here" image, and the ArcadeWorld.exe file wings its way to your machine. Double-click, and you are pwned. Within a day or two, your PC, too, will host a professionally-looking malware page like this one...or send tons of spam...or lure more users to a different infection site...or participate in a denial-of-service attack on a legitimate site...or give up all your financial web site usernames and passwords. 1000+ ways to hand over your computer and private info to crooks for FREE, FREE, FREE!
Posted on September 27, 2007 at 08:03 AMSeptember 22, 2007
An In-Your-Face Phisher
Except for the complete idiots among them (recent example "Subject: PayPal Account® Posible Fraud - Notification"), most phishing social engineers try to present their email message with the same level of professionalism as one would expect in a genuine email message from the organization they're pretending to be. Thus, I was rather startled at the subject line of a message purporting to come from PayPal:
Subject: Your account was hijacked.
Perhaps I've been a PayPal customer for too long, but that language is so out of character as to be laughable. It also has no bearing on the content of the message.
The body of the message retrieves a PayPal logo image that had been lifted from PayPal's site and is now hosted at a Romanian server—information not normally investigated by recipients. Thus, the logo may fool some.
As for the message, itself, it's fairly standard "someone tried to access your account" stuff:
Dear PayPal valued account holder,We recently noticed one or more attempts to log in your PayPal account from a foreign IP address and we have reasons to believe that your account was hijacked by a third party without your authorization.
If you recently accessed your account while traveling, the log in attempts may have initiated by you.However if you are the rightful holder of the account, click on the link below and submit, as we try to verify your account.
Please click here to login into your PayPal account and then fill in the required informations. This is required for us to continue to offer you a safe and risk free environment.
The log in attempt was made from:
IP address: 128.232.xxx.xxx
ISP host: [subdomains removed].cl.cam.ac.ukIf you choose to ignore our request, you leave us no choice but to temporally suspend your account.
We ask that you allow at least 48hrs for the case to be investigated and we strongly recommend not making any changes to your account in that time.* Please do not respond to this email as your reply will not be received.
Thank you for your patience as we work together to protect your account.
Copyright © 1999 - 2007 PayPal. All rights reserved.
I'll admit that this guy did some of his homework in that the IP address that supposedly tried to access my account is within a block assigned to the University of Cambridge Computer Laboratory. In so many other messages of this type, the IP address info is rather random.
Unfortunately for most other recipients of this message and others like it, they aren't aware of how PayPal actually deals with unauthorized attempts to log in to someone's account. I've been through it for real and reported it. Additionally, in every communication I've received from PayPal (the real PayPal), the message body is addressed to me by name, not "valued customer" or other generic greeting (this, of course, could be faked because a lot of spam email address lists also have real names associated with the email address). Of course, I also have a very private email address for my financial accounts, and this phishing message (like all the other phishing messages) was addressed to my highly spammed public address.
Everyday users continue to fall for phishing messages because the phishers still take the time to pursue the tactic. There are some days I'd like to sit the world's email users down in one room and show them a thing or three.
Posted on September 22, 2007 at 09:28 AMSeptember 15, 2007
Stormy Games
Here's the latest Storm lure:
Subject: Stop paying for gamesGo http://[numeric.IP.address.ohmy]
All links on the destination page download an executable called ArcadeWorld.exe.
Needless to say, don't do it.
Posted on September 15, 2007 at 04:40 PMSeptember 10, 2007
Another Malware Lure. Not So Stormy?
Here is the malware lure du jour:
Subject: You have just recieved a NEW message!You have just recieved a new Google Message!
You can view your message here: http://www.google.com/gmsgid=4289472Note: If you do not already have Google Message Viewer installed, you will be prompted to install it.
The Google URL is an HTML link bearing a hidden actual destination at a hijacked South Korean computer on a broadband connection. The destination automatically downloads a file named GoogleSetup.exe. It's a new one, which very few antivirus products have definitions for as I write this.
This one doesn't seem to be as clever (or as correctly spelled) as the recent Storm invasions. Probably an independent production.
Posted on September 10, 2007 at 01:03 PMSeptember 08, 2007
Yet More Stormy Weather
These guys are damned good social engineers. They've done the "you're a member of a neat club" trick, then the YouTube lure, and last weekend used the Labor Day holiday (in the U.S.) as bait. Being a new weekend and all, the newest one I've seen goes after Americans' insatiable appetite for anything football. Here's what arrives in the email:
Subject: Football Fan EssentialsSeason is open.... and we do mean FOOTBALL!
Know all the games, what time, what channel and the stats.
Keep on top of all the games with our online game tracker:
http://[numeric.IP.address.removed]/
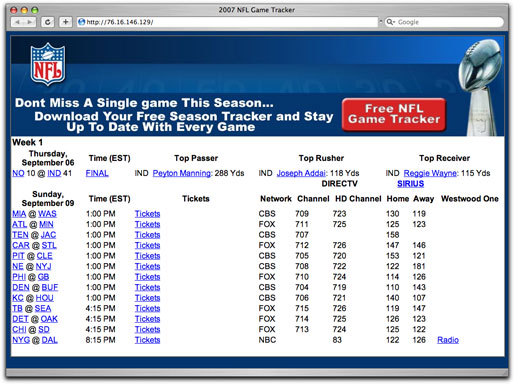
The page at the end of that URL has a bunch of National Football League data about the pro games playing tomorrow:
The links in the table go to the real football team sites. But the lure is the "Game Tracker" button in the upper right. I'll bet there will be lots of fans who download this guy. Unfortunately, this particular download is malware through and through. Even more unfortunately, a lot of major antivirus products do not yet detect this program. So, if you think you're safe by having, say, McAfee or Symantec AV running as a safety net, forget it (until they update their malware definitions).
Oh, and lest you think that all of this stuff is going on via hijacked computers in dark dungeons located in rarefied regions of the world, the IP address of the message's link I received belongs to Comcast in Chicago. It's more of bots using bots to bot the bot-bot.
So, if you fall for this trick, while you're enjoying the game in front of the TV, your PC will be doing something like "the wave," except it will be mooning you from across the room.
UPDATE (15Sep2007) -- Although the volume has subsided a bit, more recent web sites using this NFL ruse have all links pointing to the malware download. It must have been a tough call for the guy(s) behind this one. On the one hand, having so many links point to real NFL team web sites (if a visitor bothers to check the browser status bar while rolling over the link) gives the page more credibility; on the other hand, having all links start the download will more likely garner a greater number of downloads from those visitors who aren't suspicious (and are more likely running unpatched/unprotected machines).
Posted on September 08, 2007 at 12:04 PMSeptember 04, 2007
Sloppy, Sloppy, Sloppy
It's amazing to me that a scammer with only the tiniest grasp of the English language would deploy a phishing scam aimed at English-speaking peoples (sorry, an old Winston Churchill reference). Look at this "amazon.com" phishing message sent in plain text:
From: "Onlline Verification"<online@amazon.com>
Subject: Stay ProtectedDear Member,
Because of all the frauds attempts we decided to renew our security, but we need all the help we can get so that we can beat all the spam emails.
Please click on the link bellow and go through the whole process :
http://[obviously French-language domain name]/.www.amazon.com/amazon.html
Best regards,Lidya Joseph
"Amazon Comunitty"
The phishing site software must be from a kit, because except for a couple of fine-print typos on an unusual intermediary page, the regular login page is a pure amazon.com rip-off, like the ones deployed regularly around phishdom.
But as for posing as an amazon.com email message, this phisher is rather Clouseau-esque with a false moustache crookedly glued to his forehead.
UPDATE (5 September 2007) - Maybe our phisher had another beginning English lesson today. If so, the lesson was lost:
Dear Consumer,Posted on September 04, 2007 at 08:53 AMBecause of all the frauds and spam emails, we decided to modify our security and updated as soon as possible, but for this to happen we need all the help we can get.
First of all all we need you to confirm you're email so we can see who are the real people and who are the scammers with the fake emails.
For you to confirm you're email you need to acces this link :http://[same French domain (sigh)]/.www.amazon.com/amazon.html
Best Regards,
Monica Felea
Online and account security.