| Home | The Book | Training | Events | Tools | Stats |
May 26, 2009
The Malware Keeps Coming
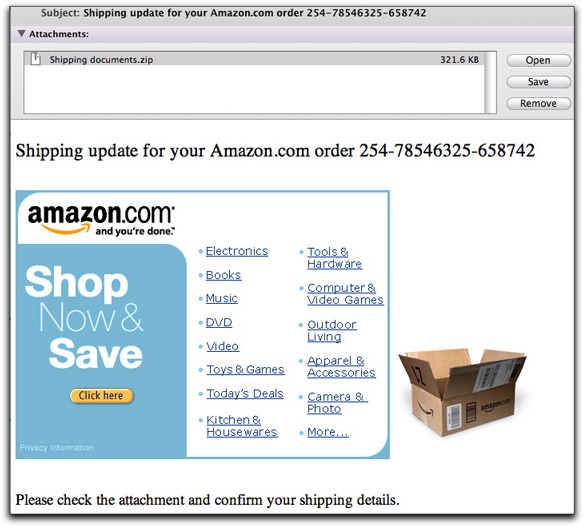
North Carolina State University computers are still at it, this time with yet a different brand name ploy. Ladies and gentlemen, I give you Amazon.com:
This one is disguised as a shipping update notification. I get legitimate ones of these now and again from Amazon.com, but the real ones never contain an attachment. The attachment, Shipping documents.zip, drew the same 25% VirusTotal score as the hi5.com attachment (including identical malware identifications, but different hash values).
Add a fake Twitter invitation to the mix now ("Subject: Your friend invited you to twitter!"). I think I'll give it a rest.
Time to pull the plug on ncsu.edu?
Posted on May 26, 2009 at 01:57 PM
It doesn't get the kind of media attention of places like Facebook, but another social networking site, hi5, is supposedly fairly popular (if I can ascribe any fact to the Wikipedia entry). Frankly, the name didn't ring any bells with me, but then again, I'm more of an antisocial networker.
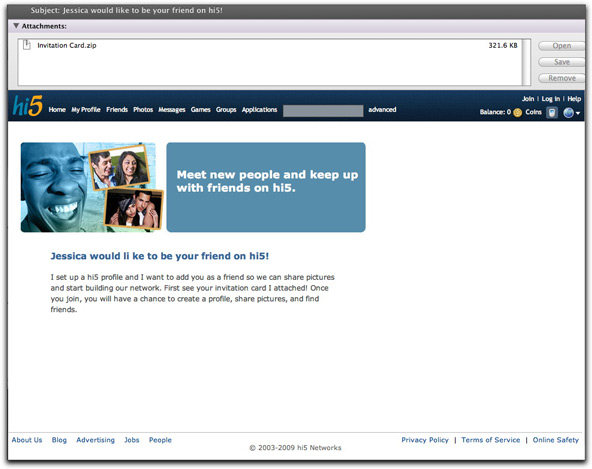
In any case, alarm bells did go off in my head when I received an unsolicited message claiming to come from hi5.com, suggesting that "Subject: Jessica would like to be your friend on hi5!". The message looked like this:
In case you can't read the fine print, the body of the message reads thusly:
I set up a hi5 profile and I want to add you as a friend so we can share pictures and start building our network. First see your invitation card I attached! Once you join, you will have a chance to create a profile, share pictures, and find friends.
I suppose if I had been a hi5 member, the layout of the message would have looked familiar (it looks like hi5's home page), and I might have taken the email as being from another hi5 member. But, as is often the case with ne'er-do-wells, the author of this message screwed up in a couple of ways that wouldn't fool the spam-educated.
First, the links in the header and footer bars were ripped from a local copy of the web site's home page. As a result, the URLs for all of those links point to local URLs, not the hi5.com site. A roll over any of those URLs produces a variety of odd results, depending on your operating system. In any case, none of those URLs resolve to anything.
Second, although the From: field claims to be "invitations@hi5.com," the message header shows my copy to have originated from a computer connected to the North Carolina State University network. Probably some student or faculty member whose machine is well-pwned in its own right.
And, finally, the use of an attached payload masquerading as an invitation card to a social networking site is just too bizarre. Businesses built around web sites want to get you to the web site ASAP. Passing the attached file, Invitation Card.zip, through VirusTotal yielded a sad 25% catch rate based on signature. Those 25% (missing some big AV names, mind you) identify the file as a Trojan or other type of malware.
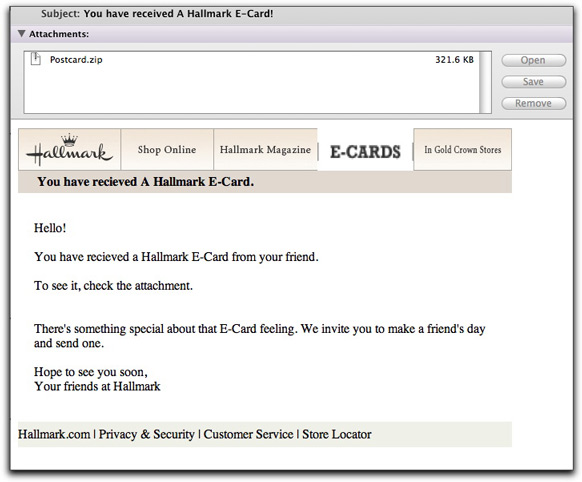
At roughly the same time, another malware delivery arrived, this time claiming to be from hallmark.com:
The Postcard.zip file was an entirely different piece of junk, recognized by a lowly 27.5% of the VirusTotal signature tests. This effort was sloppy in other respects. None of the supposed links were links at all. Also, the author of the body isn't very clear about the "i before e" rule of English spelling.
More troubling in a way, however, is that the Hallmark fake came from the same NC State network as the hi5 fake, but from a different (and not neighboring) IP address. Looks like some university needs to do outbound attachment filtering ASAP.
Posted on May 26, 2009 at 01:43 PMMay 25, 2009
Now Health.com Being Joe Jobbed
A couple of weeks ago it was Fairfax Digital (Australia) whose brand name was dragged through the mud by a medz huckster who spammed as a Fairfax impostor. Today, it's Health.com whose brand is the target of a medz spammer.
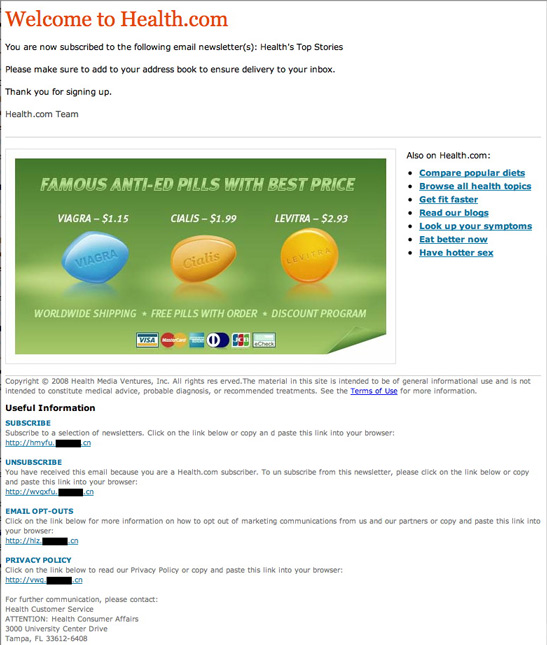
The message begins:
Welcome to Health.comYou are now subscribed to the following email newsletter(s): Health's Top Stories
Here's what the email message looks like (the large image with pills is downloaded from an external site):
This spammer isn't quite as clever as the earlier one because he leaves the links to a Chinese web site in plain view, rather than hiding them in less transparent links. The Chinese domain was registered waaay back on Saturday. Other identification in the message, however, tries to make the recipient believe it comes from Florida. If you dare follow the links (risky unless you use bulletproof browsing), the destination (after a bit of redirection) claims to be the old faithful, Canadian Pharmacy—whatever that is.
Perhaps we are in for a stretch of medz (and other) spammers hijacking the good names of web companies in an effort to gain an ounce of credibility with recipients. The economy must be tough all over.
Posted on May 25, 2009 at 06:03 PMMay 19, 2009
Fairfax Digital Followup
I'm posting this separate followup to my earlier article about the slew of spam claiming to come from Fairfax Digital. Based on the number of Google searches that have landed folks to my article, it's still a vexing problem.
As I suggested in my earlier piece, the emails which begin with:
Dear ,
Thank you for becoming a Fairfax Digital Member.
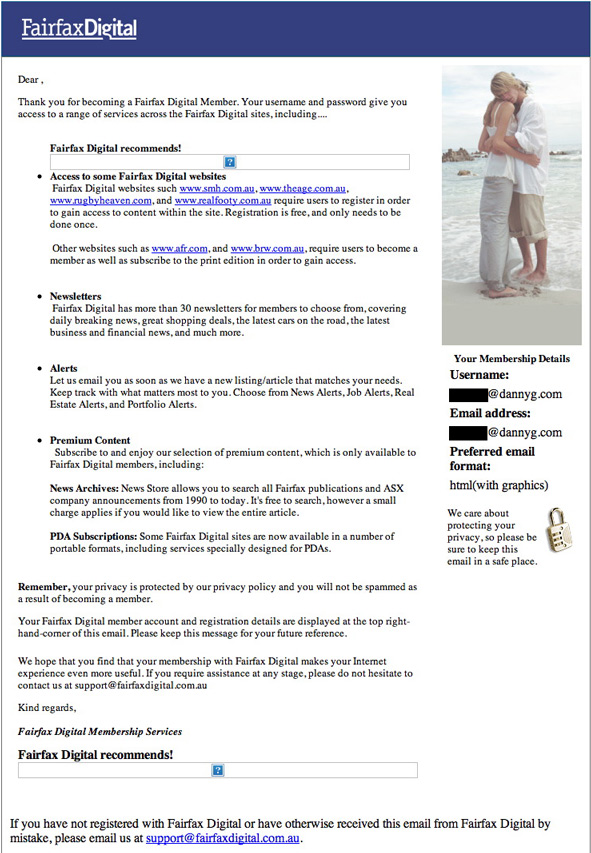
do not originate, nor are they connected with, the real Fairfax Digital firm in Australia. I have heard directly from a representative of the company, and I accept her word. There were too many signs behind the facade of the messages to suggest Fairfax Digital was responsible. In addition to the numerous pointers mentioned in my earlier posting, I should have also added that the corporate logo in the spam messages looks nothing like the company's current logo. Perhaps the criminal spammer is using an old hijacked design.
I know it's hard to undo a first impression. When that first impression consists of copious amounts of spam tied to a particular brand name, even thinking of that name might send the lip curling. In this case, at least, your curling would be misdirected. It's important not to take any unsolicited email message at face value. Sometimes the scam is intuitively obvious; other times it takes additional digging to get to the truth.
Posted on May 19, 2009 at 07:59 PMMay 12, 2009
Hitting the Quaker Oats Lottery
Advance-fee lottery scams have taken several guises over the years, but one I saw today was new to me. It is so preposterous that recipients might just believe it.
Here's the full text — long, but somewhat entertaining:
Twofour
6-7 St Cross St
London
EC1N 8UA
Date: 13th May 2009
NOTIFICATION FOR CASH AID
Dear Sir / Madam,
This is to notify you that you have been chosen By the Board of trustees of the Quaker Oats Aid Institution based in the England, as one of the final recipients of a Cash Aid/Donation for your own personal, education and business development, Quaker Oats Company as established 1850, and Quaker Oats Aid Institution was developed in 1980 by the Multi-Million groups, which was conceived with the objective of Human Growth, Educational and Community development. In line with the 73 years anniversary of this program the Quaker Oats Institution in conjunction with the United Nations (UN) and the European union (EU ), is giving out a yearly donation of Five Hundred Million Great Britain Pounds, as specific Donations/Grants to 150 international recipients worldwide in different categories for their personal Business development and uplift of their environment.
These funds are freely given to you to use for your business educational and personal development, and at least 30% to be used by you to develop a part of your environment, as this is a yearly program, which is a measure of universal development strategy, and eradication of poverty.
Please kindly note that you are not the only beneficiary in your country this year, and your country is not the only country that is benefiting from this donation, as beneficiaries have been chosen from countries from all continents. The idea of this donation is that within ten years from now, there will be notable richness among many unusual people around the world.
This will give many people the opportunity to get their lives to a stage where they had always wanted. Kindly note that you will only be chosen to receive the donation once, which means that subsequent yearly donation will not get to you again, so its your chance to spend the donation wisely on something that will last you a long time. And please do not bother following up this email, if you have benefited from this donation in previous years.
Based on the random selection exercise of Internet websites, Internet ip address and millions of Super market cash invoices worldwide, you were selected among the recipients to receive the donation sum of Ј1,671,000.00 (One Million Six hundred and seventy one thousand Great Britain Pounds) as cash aid donations from the Quaker Oats Aid Institution, (UN) and the (EU) in accordance with the enabling act of Parliament.
Kindly be aware that the Quaker Oats Aid Institution Board of trustees do not know you in person or your curriculum Vitae (C.V), you are therefore required to send your C.V along with your Facial means of Identification on your contact with the Secretary for documentation and processing of your payment.
Curriculum Vitae (C.V) should contain as follows.
Full Names:
All Contact Address:
Phone number(s):
Fax Number(s):
Occupation:
Company Name:
Marriage status:
Religion:
Next of kin:
Date of birth:
Nationality:
State/Province:
Country:
Facial means of Identification, should contain one of this options, Drivers License or International Passport.
You are required to expeditiously Contact the Executive Secretary below for documentation and processing of your Cash Aid, between the hours of 8.00am - 7.30pm on Monday to Friday.
Executive Secretary- Dr. Devon Nolan
PHONE:+4470111[removed]
FAX:+4487166[removed],+4470058[removed]
Email: [removed]@live.com
Note: On your contact with the Executive Secretary with your curriculum Vitae (C.V) and Facial means of Identification , you are to request from him, his facial means of Identification on your own part, to verify that you are dealing with the Executive Secretary as advised.
Please endeavor to quote your Quaker Oats qualification code (QO4429) in all discussions. Please note that this Cash Aid payment are strictly administered by (QOI) Quaker Oats Aid Organization or (EU) European Union under delegated powers from the (UN) United Nations.
You are by all means hereby advised to keep this whole information confidential until you have been able to collect your donation, as there have been many cases of double and unqualified redemption, due to beneficiaries informing third parties about his/her donation.
*Finally, all funds should be redeemed by their respective beneficiaries, not later than One month after notification, failure to do so, implies that the beneficiary is a ghost, with this, cash aid will be cancelled and reserved for next 2010 edition.
On behalf of the Q.O.I Board of trustees, kindly accept our warmest congratulations
Yours faithfully,
Rev Andrew Walcott
G. Manager/ Notification Department
An interesting twist on this first request for information is a demand for a copy of a photo ID. From this, identity thieves can really go to town, even if you don't succumb to demands for fees, taxes, bribes, and other upfront costs you must bear before you (don't) receive your award.
I suppose that the scammers believe the Quaker Oats brand is so warm and fuzzy that recipients will automatically think this award is legitimate. They'll overlook the fact that after so much Quaker Oats branding, the contact email address is through a free email service. Yah! Falling for this scam will empty your bank account more thoroughly than Quaker Oats cleanses your colon.
Posted on May 12, 2009 at 09:58 PM
Over the past few days, a spam campaign claiming to be sponsored by Australian electronic marketing firm, Fairfax Digital, caught my eye. Here is what a typical item in HTML format looks like:
The Subject: lines have consisted of all-too-typical erectile dysfunction medz spam phrases, such as:
Subject: Try it and she won't ever see your manhood in flaccid condition.
Subject: If your boy refuses to stay, add some chemical and herbal strength in it!
At first sight, the message appears to come from a slick-ish email marketing firm that sends newsletters encased with ads. I've seen so many of these types of offerings that I roll my eyes when I see yet another outfit disguising unsolicited email as newsletter subscriptions (to which the recipient never subscribed). The kiss of death for your inbox is to unsubscribe from anyone who has "signed you up" to receive their crap. I was not about to send an email to the suggested support address.
But something wasn't right with this message. Or, rather, many things weren't right with this message.
First, rolling over the links in the first bullet and in the bottom line (for Privacy Policy and such) revealed that the actual destinations were to domains that had nothing to do with Fairfax Digital. In fact, they were all .in (India) domains whose registrant claimed to reside in Russia. The domains had been registered in late April 2009.
Second, the message headers also revealed that they had apparently been sent through botnet computers widely distributed around the globe. Just like your basic medz spam.
And third, I checked my server logs. The messages I saw were just a sample of the tons being hurled at my domain in dictionary-style attacks.
My next task was to do a bit of due diligence on Fairfax. Although Australia has some fairly strong antispam laws in place, the teeth chomp primarily on Australians attempting to spam Australians. But if this firm were concerned about its reputation as an email marketing company, would they risk flaunting the law by sending to addresses not explicitly tagged as being Australian?
I didn't jump right away to Fairfax's web site, but did a Google search first. One reason I go that route is that I have the Finjan SecureBrowsing plugin installed in Firefox. If there is any potential nastiness at the end of a search result link, the plugin flags the link accordingly.
Unsurprisingly (to this old dawg who has high suspicions of every so-called email marketing firm, even if it means throwing out the koala with the koala droppings), Finjan flagged the Fairfax Digital site as a potential adware site. Ugh. That meant putting up all shields before visiting the site.
The only reason I even considered visiting the site is that my other quick searches didn't turn up anything negative about the firm. Unlike many email marketing firms that change their names as often as I change socks (daily, if you want to know), Fairfax had been around for quite awhile and had been mentioned by many Australian business news outlets.
As I studied the site, it appeared that the company either runs or has influence over web sites for a few newspapers in Australia—perhaps accounting for the glowing news reports. But a look at their Privacy Policy made me rather uncomfortable. It represents the antithesis of a confirmed opt-in operation:
How we collect it [information]
We may collect your personal information from a variety of sources, including from you, advertisers, mailing lists, recruitment agencies, contractors and business partners.We may collect your personal information when you request or acquire a product or service from us, register with us as a member, provide a product or service to us, complete a survey or questionnaire, enter a competition or event, contribute in a fundraising event, participate in our services (including our radio programs, blogs and forums) or when you communicate with us by e-mail, telephone or in writing (for example if you contact customer service to make a complaint or provide feedback).
If, at any time, you provide personal or other information about someone other than yourself, you warrant that you have that person’s consent to provide such information for the purpose specified.
In other words, if they even get a whiff of an email address as it wafts by, it's theirs to do with as they please. Any trust that had been building in my mind went right out the window.
Still, I wanted to know if the spam campaign that had been hitting my server was in any way connected with Fairfax (an affiliate perhaps?) or if a spammer was trying to ride Fairfax coattails into inboxes. At the moment, my inclination is the latter.
I tried to use the contact form on the Fairfax Digital site to inquire, but I received an error message upon submission. I am trying other routes to contact them (at great potential peril to one of my email addresses, mind you), and will update this posting if I learn more from the company.
Posted on May 12, 2009 at 11:47 AMMay 08, 2009
Bogus Lottery Scammer Fails Elementary Arithmetic
Too bad I've never claimed the lottery winnings I've been told I've won over the years. I'm sure I could have accumulated enough to buy a Caribbean island by now.
Or not.
Today's installment comes from a "Mr. Simon Heebner," who politely (if sloppily formatted) tells me I'm one of five winners splitting something around 2.6 million pounds sterling. My cut: £531,259.00. This is all courtesy of "Lotto Unlimited" in Bolton (U.K.).
The email address I'm supposed to use to contact this mighty organization is a free Yahoo! account with a user name of:
uk.claimsofice
Perhaps we Yanks are to think that (Ricky Gervais notwithstanding) the Brits spell office with only one f. Well, I mean, they spell color with an extra u stuck in there, so anything must go over there.
But where Mr. Heebner (definitely not his real name) went all wonky is with his email technical skills. You see, my email address in the To: field was accompanied by no fewer than 399 others, all in nice alphabetical order...all in plain view. And that's just crudo@ through editor@.
Well, Simon, I just don't feel all that special anymore. So you keep your pounds, and I'll keep my dollars from being siphoned off by upfront demands for fake fees, taxes, documents, or whatever.
Posted on May 08, 2009 at 06:34 PMMay 05, 2009
The False Sincerity of Phishing Attempts
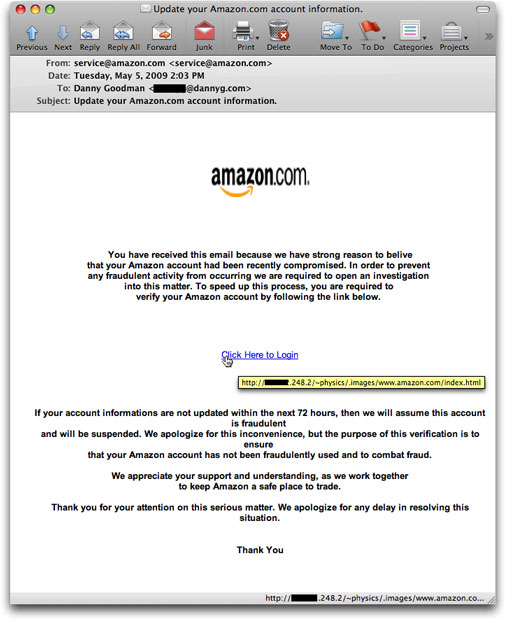
A "good" phishing story — and by "good" I mean "evil" — tries to earn the confidence of the recipient, hopefully by telling a believable story with a believable look to it. Here is an amazon.com phishing email I saw today:
Other than one unbelivable [sic] spelling gaffe in the first line, the tale is one that an unsuspecting recipient might take for being legit at face value. My email client dutifully reveals the hidden URL behind the "Click here" link, but there are probably plenty of Amazon customers who would be befuddled by the meaning behind a numeric IP address shown in this way. They might think it's a special Web location that Amazon set up just to handle these potential security issues.
The ruse of "verifying your account" is the one used most often by phishers who are seeking your login credentials to hijack your account and any credit card data associated therewith. A shopping spree at Amazon on your credit card (shipped to your "new" address) could yield some really great goodies for the crook.
Even if your liability through your credit card company is limited in terms of dollars, the hassle of getting a new card issued — and alerting all your automated payment sites to the change — is a royal PITA. In the meantime, your account data may provide the crook with enough data to open other accounts elsewhere in your name, causing difficult-to-repair problems with your credit history.
The crooks would also assume (probably correctly, alas) that you have used the same login credentials (username and password combination) at other sites, including financial institutions and other popular etailers. Robots will soon try those credentials on as many sites as possible, looking to hijack even more of your accounts.
Phishing is just another confidence game: Attempting to use a story to gain your confidence that they are sincere in trying to help you avoid fraudulent activity on your account. In truth, only by following the links and filling in the forms will you open the door to fraudulent activity on your account.
Posted on May 05, 2009 at 05:35 PM