« Now Health.com Being Joe Jobbed | Main | The Malware Keeps Coming »
| Home | The Book | Training | Events | Tools | Stats |
May 26, 2009
Jessica Would Like You To Pwn YouIt doesn't get the kind of media attention of places like Facebook, but another social networking site, hi5, is supposedly fairly popular (if I can ascribe any fact to the Wikipedia entry). Frankly, the name didn't ring any bells with me, but then again, I'm more of an antisocial networker.
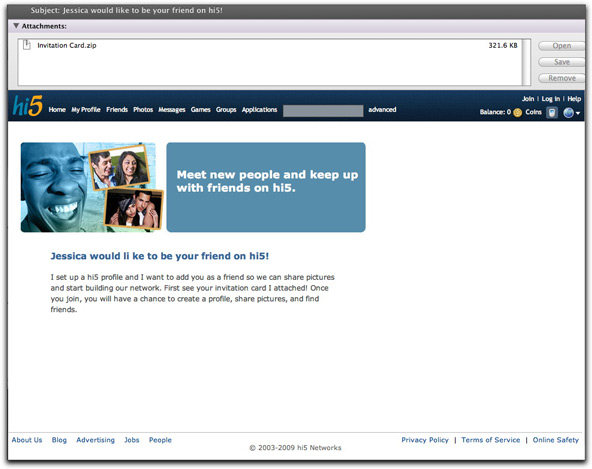
In any case, alarm bells did go off in my head when I received an unsolicited message claiming to come from hi5.com, suggesting that "Subject: Jessica would like to be your friend on hi5!". The message looked like this:
In case you can't read the fine print, the body of the message reads thusly:
I set up a hi5 profile and I want to add you as a friend so we can share pictures and start building our network. First see your invitation card I attached! Once you join, you will have a chance to create a profile, share pictures, and find friends.
I suppose if I had been a hi5 member, the layout of the message would have looked familiar (it looks like hi5's home page), and I might have taken the email as being from another hi5 member. But, as is often the case with ne'er-do-wells, the author of this message screwed up in a couple of ways that wouldn't fool the spam-educated.
First, the links in the header and footer bars were ripped from a local copy of the web site's home page. As a result, the URLs for all of those links point to local URLs, not the hi5.com site. A roll over any of those URLs produces a variety of odd results, depending on your operating system. In any case, none of those URLs resolve to anything.
Second, although the From: field claims to be "invitations@hi5.com," the message header shows my copy to have originated from a computer connected to the North Carolina State University network. Probably some student or faculty member whose machine is well-pwned in its own right.
And, finally, the use of an attached payload masquerading as an invitation card to a social networking site is just too bizarre. Businesses built around web sites want to get you to the web site ASAP. Passing the attached file, Invitation Card.zip, through VirusTotal yielded a sad 25% catch rate based on signature. Those 25% (missing some big AV names, mind you) identify the file as a Trojan or other type of malware.
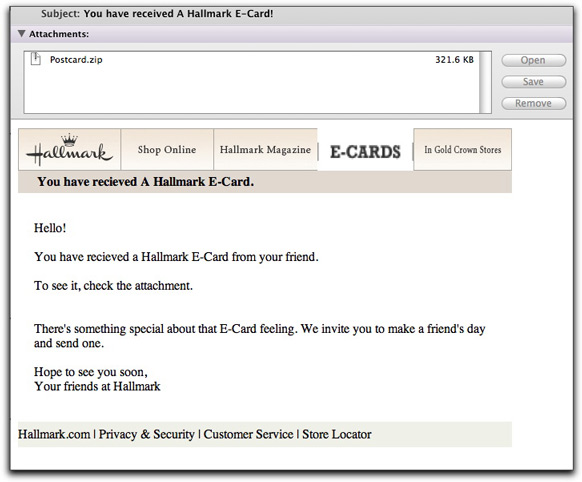
At roughly the same time, another malware delivery arrived, this time claiming to be from hallmark.com:
The Postcard.zip file was an entirely different piece of junk, recognized by a lowly 27.5% of the VirusTotal signature tests. This effort was sloppy in other respects. None of the supposed links were links at all. Also, the author of the body isn't very clear about the "i before e" rule of English spelling.
More troubling in a way, however, is that the Hallmark fake came from the same NC State network as the hi5 fake, but from a different (and not neighboring) IP address. Looks like some university needs to do outbound attachment filtering ASAP.
Posted on May 26, 2009 at 01:43 PM