| Home | The Book | Training | Events | Tools | Stats |
August 29, 2010
Phony Shell Oil Star Promotion
Don't be taken in by this variation of the 419 lottery scam. The text portion of the message is as follows:
Dear Winner,Find attached your winning Notification,in the Shell 2010 Online drwas.
Do contact our payment Manager for the immediate release of your funds.
Name: Attorney Cynthia Benton
Email address:[removed]@yahoo.com.hk
Phone/Fax: +44-7624-[removed]
Congratulations!!!!!
Shell Payment Department London.
30/08/2010
The message includes an image containing the Shell corporate logo:
Greedy recipients of this message won't realize that the email address of their contact is a free account from Yahoo! Hong Kong. Think for a minute: Why would a gigantic oil corporation not use its own email system for this highly valued award? (And, if you knew how to read email headers, you'd also ask why Shell Oil U.K. would send you a prize winning notification through a botnet computer in Taiwan.)
If you get sucked into communicating with these crooks (the phone number is for a cell phone, by the way), they'll get you to fork over all kinds of fees and taxes out of your own money, and you'll never see a dime of the award money. It doesn't exist. Shell Oil does not give away money like this. This scam has been running for years and years under the guise of other corporate and government sponsorships.
That's right, hit Delete. Now.
Posted on August 29, 2010 at 11:47 PMAugust 26, 2010
Repeat After Me: "The From Field is Forged"
Spammers and crooks know it: Lots of email recipients treat the From: field as if it must be telling the truth. If an email message that makes it to your inbox says it's from Joe Blow, well, by God, it's from Joe Blow.
This blind faith about unsolicited email messages is what gets so many computer users into trouble.
A case in point is that someone managed to find his or her way to this web site (spamwars.com) and went to the trouble of filling out the contact form thusly:
I received an e-mail from this address saying I made an online payment of $500 not true. Remove all information
I suspect the person found the site by searching Google, which pointed to this article. So, I write an article blowing the lid off this scam, and I'd send out more messages after I implore you to not react to the messages? WTF?
Worse yet, this person included his/her email address in the contact form. Luckily for him/her, I don't harvest addresses (or send out any kind of bulk email of any kind). Voluntarily revealing one's email address to any kind of spammer or scammer is the most idiotic thing one could do — and he/she obviously thinks I'm a spammer/scammer, right?
I've tried to educate computer users about how email headers can be forged from here to Azerbaijan, but they either don't listen, or just have overriding faith in what they see in their in boxes. For the record: Everything from the header that your email client displays can be forged, including the From:, To:, Date:, and Subject: fields. And when it comes to spam or scam messages, the From: field is almost always forged with other addresses from the spammer's databases (i.e., other spam recipients). These addresses have been harvested from infected computers and other sources for years and years. An infected computer will supply Bad Guys with addresses of everyone with whom the infected computer has corresponded — which is how addresses belonging to owners of clean computers have been captured. If you are receiving spam, there is a very good chance that your address has been plugged into the From: field of spam going to others at some point.
Most computer users can't be bothered to learn how the spammers and scammers make them dance like marionettes. Put on your tap shoes.
Posted on August 26, 2010 at 10:36 PMAugust 20, 2010
Spampaign Analysis
The activities of one particular spammer has caught my eye, and I've been monitoring the activity directed my way over the past few months. I don't know the identity of the spammer — the one responsible for putting the spam into inboxes — but all of the spamvertised domains are registered (privacy locked, of course) through Dynamic Dolphin, for many years one of Scott Richter's alleged homes.
What brought these messages to my attention is that the subject matter isn't the typical medz, knockoff goods, or other items pitched by the bulk of the world's spam. Look at these selected Subject/From combinations:
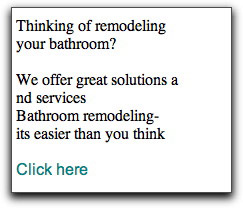
Residential House Painters Painting Become a CNA Certified Nursing Assistant Training Train to become a photographer Photography School No repair will go unfixed with a handyman Handyman Renovate your old bathroom Bathroom Remodeling Healthy careers inside Best Medical Billing Training Hire an expert to repair your roof today. Roof Repair Take a seat and sneak a peek at Private Jets. Private Jet Save on Contact Lenses and Supplies Contact Lenses Lasik Eye Surgery Lasik Government grant money is available Government Grants Record it all on a spy camera Security Cameras Discount air conditioners - energy efficient Air Conditioners Discount dog supplies online Dog Supplies Auto-Answering Service Answering Service Dont waste time cleaning. Hire a maid service. Housekeeping Service Easily save for retirement 401K Plans Find local personal injury lawyers. Personal Injury Lawyer
What struck me as being so odd is that many of these messages appeared to have a local appeal. I mean, a global spam campaign by a handyman service just doesn't seem right.
I'll come back to this in a minute, but first, more about the message content.
Over the past four months, the message body designs have changed. They started out with a simple format like this:
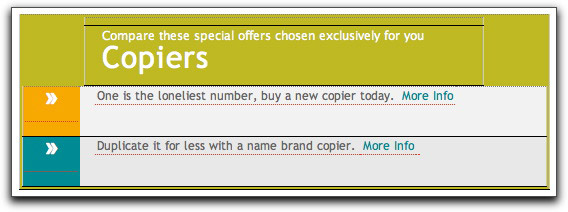
More recently they've been using a couple table-oriented layouts. One doesn't use images:
The other employs images in a variety of table cell proportions. Here's one (without downloading the images, as I'll explain in a moment):
The reason I don't show you all of the images is that each downloadable image URL (and link) is encoded with three identifying numbers. My assumption about these numbers is that they identify the actual advertiser account, campaign, and the recipient email address (the long number). I have my email client set to not download any remotely-accessed content without my approval, so this was one way to prevent my address from being confirmed to the spammer.
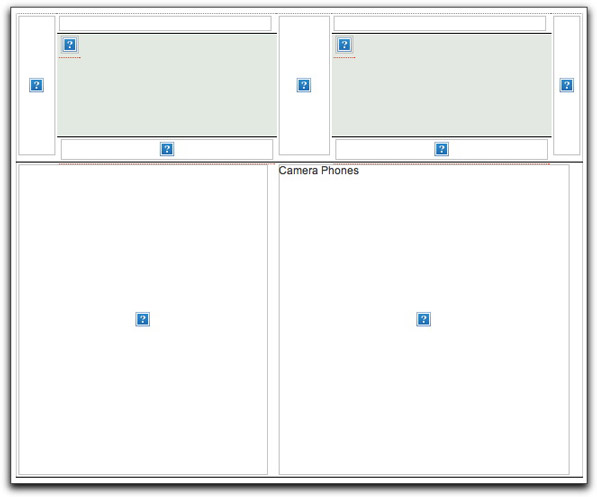
I did, however, find a workaround to conceal my address code, and here is an example of one of the image-based email bodies:
Notice that there is no identification of the entity offering the training being advertised. The same was true of the image-less ads. The From: email addresses were to the domains (gibberish) hosting the images and receiving the click-throughs.
What about CAN-SPAM, you ask? At the very bottom of every message is a link and purported mailing address to be removed from the mailing list. Here is what one of them looks like:
I say "one of them" because across the span of these mailings, I've seen several addresses in at least five states. One of them lists a company name, TLE Inc. Good luck with that. The "unsubscribe" links lead to an unsub.cgi program, and the URL is coded with the campaign and addressee ID numbers. I wouldn't click on one of those links with a ten-foot mouse.
Deeper inside the message is more stuff so typical of a spammer trying to beat the content filters by loading up the invisible body with tons of hash busting text. The general format of the hash-busting text is similar throughout all of the mailings, but their sending routines substitute words here and there to prevent being identified by the same strings.
All of the hash-busting text is embedded within a phony <style> tag (whose content doesn't render for the user to see). Here's a brief excerpt of stuff that's supposed to resemble style sheet specifications:
table .foulmouthed{ background:#D3E4E5;
border:1px solid gray;
border-collapse:collapse;
color:#fff;
font:normal 12px verdana, arial, helvetica, sans-serif;
}
caption .comfits{ border:1px solid #5C443A;
color:#5C443A;
font-weight:bold;
letter-spacing:20px;
padding:6px 4px 8px 0px;
text-align:center;
text-transform:uppercase;
}
howls td, bathrobe th { color:#363636;
padding:.4em;
}
argufy tr { border:1px dotted gray;
}
But then there are further blocks, sometimes of random dictionary words bashed together:
cacao/circulariserhydroxyproline/audit/crevice/bareknuckle/expressive/flutterboard/Decca/computerisation/flimsily/expurgator/apeldoorn/bondsman/concision/intraorganization-advocacy/idiotism-Crockford/clauses/bituminisingbummaree.carer/horizontalisationsacknowledgements/Koheleth/communalizes
plus many dozens of lines with single words between more dozens of blank lines between them. A typical message is formatted to contain over 3000 lines (mostly empty) with a character count approaching 20,000. The actual visible content portion is a tiny fraction of that.
By now, you must be wondering what's at the end of these links. By way of an email address identifier disguise, I found out for at least a couple (which I would wager is a sufficient sample size for this spammer).
I chose the police training and copier sites. The police training link navigated me beyond the domain in the emails to an online division of a small university in Ohio. Although I had never heard of the university, the .edu domain had been alive since 1994. The copier link delivered me to a company's web site that has (possibly) been around since 1997. But it's not that simple, it turns out.
Both sites lead the visitor through a multi-screen questionnaire that (in the sales biz terminology) qualifies the visitor for what kind of information they want to receive. In the case of the police training, the site actually advertises numerous curricula from which to choose. As you navigate through questionnaire screens, they want to know what your current education level is, your age, when you want to begin school, whether you're a U.S. citizen — all the kinds of things that an enrollment office for an online university would ask. The same was true for the copier site, which wants to know how many copiers you're looking for, whether you do mostly color, b&w, or both, your copier volume, how fast a copier you need, and so on.
Both sites have a quality feel to them. Although the designs are quite different, there is a similarity in how they report one's progress through the qualification stages (there is literally a progress bar). The copier site claims to have an A+ rating with the Better Business Bureau — an online claim that is worthless after having been so horribly abused by spammers over the years.
My takeaway from this lengthy series of campaigns is that an "email marketing" company (shudder) is either selling lead generation services to smaller organizations (including web site design), or it's gathering the leads on its own to rent out to other firms. In the process it is also gathering live email addresses through image retrievals and click-throughs (in fact, all clickable URLs have "clickthru" as part of the URLs).
Heaven knows what kind of B.S. these guys sell the people who buy their services. I'm sure it's full of stuff like "we email only to opt-in addresses" and the like — the same lies being peddled under the guise of email marketing for years and years. If they were so legitimate, they'd use one of the verified sender systems to guarantee delivery to those who want their messages and not load their messages with hash busters.
Although I'd like to know the identity of the sender, enough of my curiosity has been satisfied that I can now block these guys and never be bothered by them again.
Posted on August 20, 2010 at 11:31 AMAugust 13, 2010
LinkedIn, Part Trois
They're back to the LinkedIn message body, but this time with a huge ED medz image right in the middle of the LinkedIn lookalike body.
The previously mentioned attachment in Part Deux has now been examined, and has a very low (17%) AV detection rate. Presumably this is just signature testing, and hopefully the actual detection rate including behavioral examination is better. Still, it's potentially dangerous stuff.
Color me: Officially bored.
Posted on August 13, 2010 at 03:54 PM
Only about six hours after the first barrage, the same senders have changed up the message content and Subject, while keeping all the LinkedIn header stuff intact, including the X-LinkedIn header fields and a reference to linkedin.com in the From: field.
The new content is a mix of text come-ons, like the following:
Hi,I have attached the SRP Cool Cash Application below as well as a computer copy of your invoice.
We appreciate your business!
Have a great day!Veronica Bacon
===========================
Hi, If you thought you had a tight parking space in the garage, check out the attached.
Sabrina
===========================
Hi,
Sorry it took me so long to get this to you.
The ARI certification is # 3373385
The installed price is $5480 plus sales tax.
Less $600 Manufacturer's instant rebate
Less $300 discount for buying 2 systems
Less $425 SRP Rebate
Less 30% of original purchase price (up to $1500) Federal Rebate CreditWe will see you on the August 12th and then your friend on the 19th of August.
I attached the certificate for you.
Darrin Koehler
All messages come with a .zip attachment (~170KB) with different names. VirusTotal is down (being DDOSed?) so I'm not sure what the attachment is. It can't be good.
And then I realized that Friday the 13th is only half over. Ugh.
Posted on August 13, 2010 at 12:59 PM
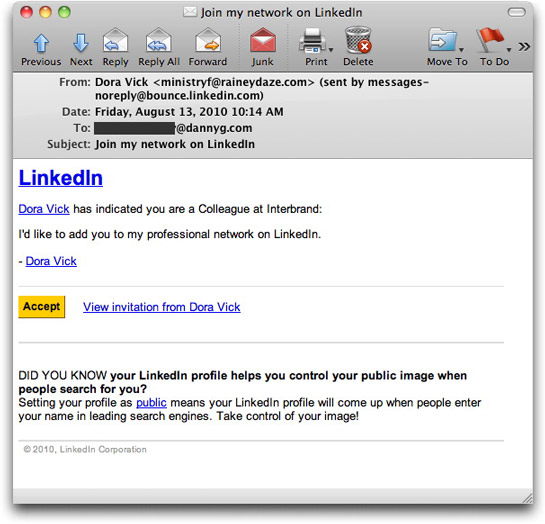
Friday the 13th is certainly unlucky for me: My inbox got flooded with a series of what looked to be invitations to join LinkedIn networks from people I had never heard of. Now, that, in itself, is not unheard of, as I often get real invitations from people who try to connect to my network because we know someone in common. Little do they know that my micro-fame and perceived (never real) influence faded a long time ago...but that's another matter for another day (not!).
Anyway, back to these invitations. On the surface, they look real:
I've discovered subsequently that Interbrand is a real company, but the name didn't mean much to me (poor branding?). In any case, you can be assured that I have never worked for the company, so someone claiming to be a colleague is a bit of a joke.
As is often the case, the deviousness of these messages lies in the hidden URLs behind the clickable links and buttons. They all point to a domain and a page named x.html. That x.html page contains a hidden iframe and a meta redirector to a Chinese site. Because the redirection URLs have affiliate IDs in them, I won't visit with the complete URL — which means I won't see the actual destination.
It doesn't really matter, because I'd wager good money that the destinations are either malware loading pages or Canadian Pharmacy medz sites. They've been using the x.html page way too long.
The senders went to a bit of trouble to try to make the headers look legitimate. They include some X-LinkedIn fields and a completely phony (but potentially real-looking) Received: header field:
Received: from mail14-d-ai.linkedin.com (mail14-d-ai.linkedin.com [208.111.169.155]) by smtp.perimeterusa.com with ESMTP id u34fd9864511dsm.370.2010.08.13.09.37.33; Fri, 13 Aug 2010 20:33:47 +0300
Of course the one, true and mostly reliable Received: header written by my server reveals that the message actually originated from Azerbaijan. The sender also omitted, naturally, the DomainKey signature that genuine LinkedIn messages contain.
If these clowns hadn't sent me a half dozen messages in a short burst, but just one, I might have let my guard down and clicked on one of the links to investigate the purported sender more closely. It's just a reminder to even the most cautious among us to suspect every incoming email message until you can safely verify its authenticity.
Posted on August 13, 2010 at 10:45 AMAugust 06, 2010
Express Payment
Here's a scam message that will ultimately lead to pwnership of quite a few PCs on the scammer's email address database:
Subject: Thank you for your EXPRESS payment
***PLEASE DO NOT REPLY TO THIS MESSAGE***
Dear [removed -- recipient's email address],
Thank you for your online payment of $500.00. Your payment will be applied on Fri, 6 Aug 2010 08:35:18 -0800
Remember you can manage your account online, view statements and pay your bill at www.mycardcare.com/express.
The hidden link beneath the visible URL is to a highjacked web site where the file contains a redirector (complete with affiliate ID so that the spam originator gets credit for your visit) to a site claiming that your PC is infected with viruses. That page also has tons of silent-loading nastiness embedded within.
Especially in these economically difficult times, receiving news of some large, unauthorized payment can really get the blood boiling, sending your mouse racing to the link to find out what's going on. If you have found this posting because you are performing some due diligence prior to clicking the link, then pat yourself on the back for being a smart user...and DON'T click that link, no matter how much virus protection you have installed.
Posted on August 06, 2010 at 09:05 AM