| Home | The Book | Training | Events | Tools | Stats |
August 13, 2010
Attack of the Bogus LinkedIn InvitationsFriday the 13th is certainly unlucky for me: My inbox got flooded with a series of what looked to be invitations to join LinkedIn networks from people I had never heard of. Now, that, in itself, is not unheard of, as I often get real invitations from people who try to connect to my network because we know someone in common. Little do they know that my micro-fame and perceived (never real) influence faded a long time ago...but that's another matter for another day (not!).
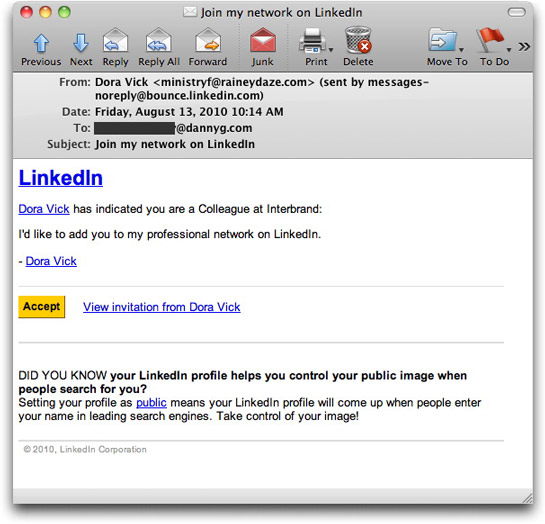
Anyway, back to these invitations. On the surface, they look real:
I've discovered subsequently that Interbrand is a real company, but the name didn't mean much to me (poor branding?). In any case, you can be assured that I have never worked for the company, so someone claiming to be a colleague is a bit of a joke.
As is often the case, the deviousness of these messages lies in the hidden URLs behind the clickable links and buttons. They all point to a domain and a page named x.html. That x.html page contains a hidden iframe and a meta redirector to a Chinese site. Because the redirection URLs have affiliate IDs in them, I won't visit with the complete URL — which means I won't see the actual destination.
It doesn't really matter, because I'd wager good money that the destinations are either malware loading pages or Canadian Pharmacy medz sites. They've been using the x.html page way too long.
The senders went to a bit of trouble to try to make the headers look legitimate. They include some X-LinkedIn fields and a completely phony (but potentially real-looking) Received: header field:
Received: from mail14-d-ai.linkedin.com (mail14-d-ai.linkedin.com [208.111.169.155]) by smtp.perimeterusa.com with ESMTP id u34fd9864511dsm.370.2010.08.13.09.37.33; Fri, 13 Aug 2010 20:33:47 +0300
Of course the one, true and mostly reliable Received: header written by my server reveals that the message actually originated from Azerbaijan. The sender also omitted, naturally, the DomainKey signature that genuine LinkedIn messages contain.
If these clowns hadn't sent me a half dozen messages in a short burst, but just one, I might have let my guard down and clicked on one of the links to investigate the purported sender more closely. It's just a reminder to even the most cautious among us to suspect every incoming email message until you can safely verify its authenticity.
Posted on August 13, 2010 at 10:45 AM