| Home | The Book | Training | Events | Tools | Stats |
June 29, 2008
That E-Card Isn't From Hallmark
For many years now, malware distributors have sent email messages telling recipients that they have received an e-card, and that they should "click here" to retrieve it. The links to, and bogus identities of, the e-card holders were typically lesser-known e-card businesses—usually a legitimate Mom & Pop type online business whose name had been abused by the crooks.
One of the best known greeting card brands in North America, Hallmark, is being used today in a lure to get unsuspecting victims to load a well-known Trojan onto their systems:
From: "hallmarkonline.com" <cards@hallmarkonline.com>
Subject: A Hallmark E-Card from your Friend
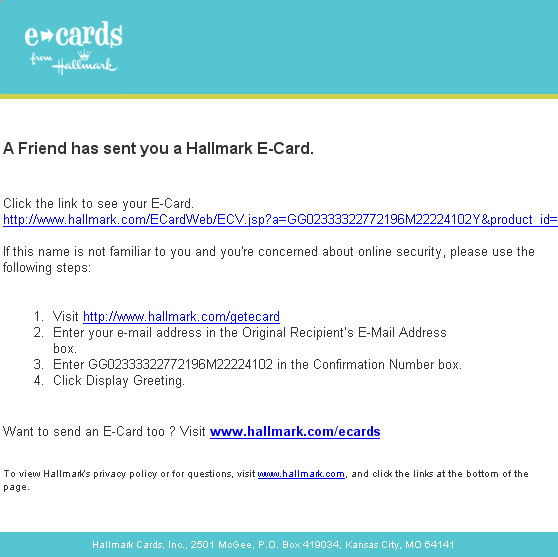
If you display the message's image, you see this:
It's rich that the message shows steps to follow if "you're concerned about online security," because if you click anywhere on the image, you actually click a link directly to the Trojan file (card.exe) located on a hijacked web server in the U.K. Clicking the link downloads the file, which, if then opened by you, will install a backdoor for crooks to take over your machine.
Not only do you not get a card from "a friend," but you've just given a great gift to a criminal gang. And it's exactly what they wanted.
Posted on June 29, 2008 at 07:13 AMJune 28, 2008
Phishers Will Sniff Out Anything of Value
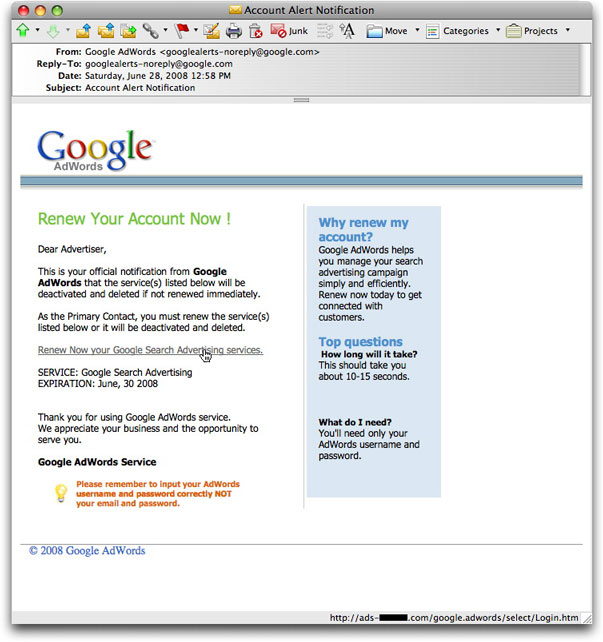
Look at this well-designed phishing email message:
Its goal is to capture login names and passwords for Google AdWords accounts. The bogus destination page is (except for one busted image) an identical twin sister of the actual Google AdWords login page. The page is also written with an added script that uses a browser cookie to prevent your browser from visiting the fake page a second time—if you try, it immediately redirects you to the real page.
If you perform the rollover test of the clickable link in the message (shown in the image above), the link isn't to Google's site, but to a domain that has what may be a convincing alternate name. I mean, it has "ads" in the name, right? That domain, by the way, was created waaaay back on Wednesday. The domain registration has information from someone in Paris, but no crook in his right mind would leave a trail of bread loaves. The fake site is hosted through a Spanish ISP.
The lesson to learn here is that obvious financial targets, such as financial institutions (banks, credit unions, PayPal) and popular e-commerce sites (Amazon, eBay, Best Buy), aren't the only ones that phishers have their eyes on. If there is an account anywhere on the Internet that has one thin dime in it (or has data that can be turned into a dime), you can be sure phishers will root through your emotional defenses for that dough like a pig hunts for truffles.
Posted on June 28, 2008 at 10:14 AMJune 26, 2008
Backscatter Poo
Automated systems can be just so damned dumb (I must reserve the word "stupid" for other purposes in this posting).
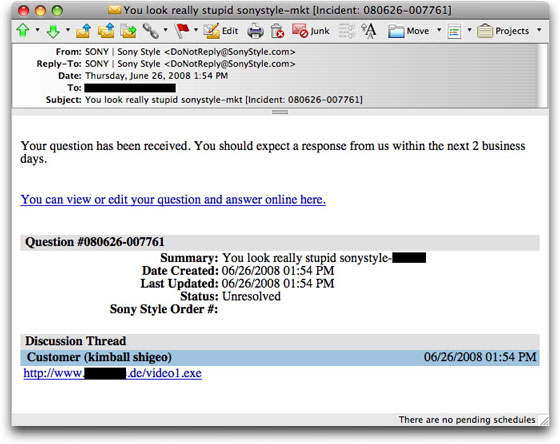
It appears that Sony Style's Customer Care system allows any Tom, Dick, and Harry Z. Robot to submit an issue via email without any kind of authentication or proof that the sender is human. I know this because earlier today I received an automated response from Sony, acknowledging "my" request for help:
Allow me to translate. At 01:54 PM today, a Sony email account user name of sonystyle-[removed] received a question from a customer whose name is Kimball Shigeo, and whose email address is...one of my email addresses. The question consisted of a URL to a German web site hosting a file named video1.exe.
In our last episode, you remember, I wrote about the "You look really stupid [so-and-so]" malware lures flooding message space in the last couple of days. Sony received one of these, complete with a forged From: address, and entered it into their system. Their system (actually, a system belonging to the customer relationship management company they use) then spit out the confirmation above.
Stee-rike One.
Since they provided a link to view the question and answer thread and after verifying that the link was legit, I clicked to see what, if anything, they'd show. Oddly enough, I couldn't view it because to do so required an account and password—theoretically one that I would have had to set up to submit the question in the first place.
Hmmm. Something tells me that the Sony email address targeted by the botnet isn't the normal way to submit support questions. It might be some kind of back door address that sneaks past the account-creation process.
Stee-rike Two.
At 4:00 on the button, Sony Style issued another e-missive. This one was titled:
Subject: Your recent Sony Style Customer Care experience
Some relevant excerpts:
Recently you contacted Sony Style Customer Care. In order to enhance the Sony Style customer experience, we invite you to complete a short survey that specifically targets your Customer Care experience. ... You received this email because our records show you contacted Sony Style Customer Care and we wish to improve our service.
Because I understand what's going on here, I simply get pissed off, rant about it in a blog entry, and load up a customer service survey with vitriol. But I'd wager that almost anyone else receiving a confirmation like the one above would be confused beyond belief. Worse still, they might venture to that URL to download and run the Trojan installer. Yikes!
Stee-rike Three. Yer out!
June 25, 2008
"You look really stupid"
Yes, that is the Subject: line of a malware lure. It arrives appended by your email account name. Thus, if your email address is johndoe@example.com, the Subject: line reads:
You look really stupid johndoe
The message body is simply a URL to a file named video1.exe, located on a hijacked web site. If your email client turns that URL into a clickable link, then clicking it (or copying and pasting the URL into your browser) begins the download of that Windows executable file to your machine. If you fear that the video caught you in a less-than-intelligent act, and you open the file on your PC, you've just enlisted your PC into a botnet army.
Congratulations.
NOT!
Posted on June 25, 2008 at 09:57 AMJune 23, 2008
Yet More Storm Quaking
The Chinese earthquake (not the real one, but a later 9.0 one that never occurred) malware lure (here and here) has revved up again, but this time with links to numeric IP addresses, rather than domain names. Although the linked sites look the same, the payload (still called beijing.exe) has apparently morphed a bit, as VirusTotal didn't recognize it as previously scanned when I passed it through for analysis. Some AV programs that caught the earlier version didn't catch this one; while others that didn't catch the first one caught this one. Total score at the moment: 10 of 33.
Posted on June 23, 2008 at 08:36 AMJune 18, 2008
Fake Quake Takes Cake
Checking my logs for the day, here are the fake Beijing earthquake malware lure Subject: lines that knocked on my server's door:
- Subject: A new deadly catastrophe in China
- Subject: China is paralyzed by new earthquake
- Subject: China's most deadly earthquake
- Subject: Chinese people are horrified by new earthquake
- Subject: Deadly catastrophe in Chinese capital
- Subject: Earth tremors in China is going on
- Subject: Terrible earthquake devastated Beijing
- Subject: The most powerful quake hits China
- Subject: Toll mounts in China earthquake
- Subject: Unprecedented earthquake in China
I received duplicates of only two, so there are probably more Subject: lines in the wild. Links in the messages lead to lots of different .cn (China) domains whose IP addresses change with each trace.
Posted on June 18, 2008 at 11:02 PM
Here is a new malware lure, using the same type of shock tactic that led many Aussies a couple of years ago to find out more about a false heart attack of then-PM Howard. This one claims to link to info about a new earthquake:
Subject: A new deadly catastrophe in ChinaRecent china earthquake kills million http://[removed].cn/
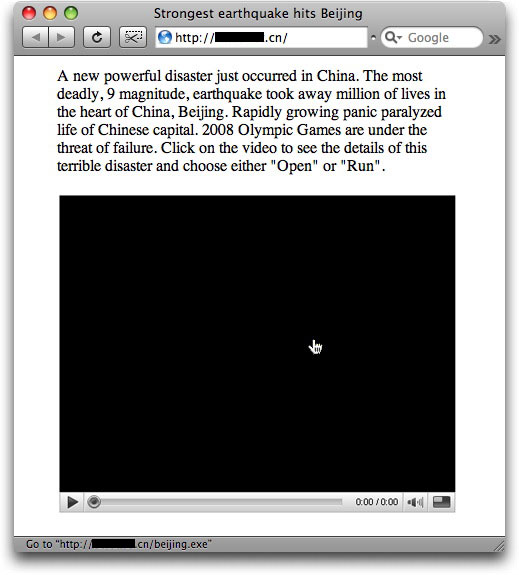
The web page contains all the fake details:
The image looks like a movie player, but it is just a dead image wrapped inside a link. Clicking the link downloads beijing.exe, a piece of malware that currently hits only 8 of 33 tests on VirusTotal.
I just received a second email message with different wording, but the same gist, leading to yet a different .cn domain. This is probably going to become widespread.
Don't fall for this one, kids. If you ever receive a message about a newsworthy item, check it first at cnn.com or your other favorite genuine news web sites. They may not always get it right, but if there is no news there about a 9.0(!) earthquake, you can be sure the unsolicited email message from someone you don't know is pure hokum, and can only lead to your own personal disaster (which also won't be in the news, despite ruining your computing life for awhile).
Posted on June 18, 2008 at 12:22 PMJune 14, 2008
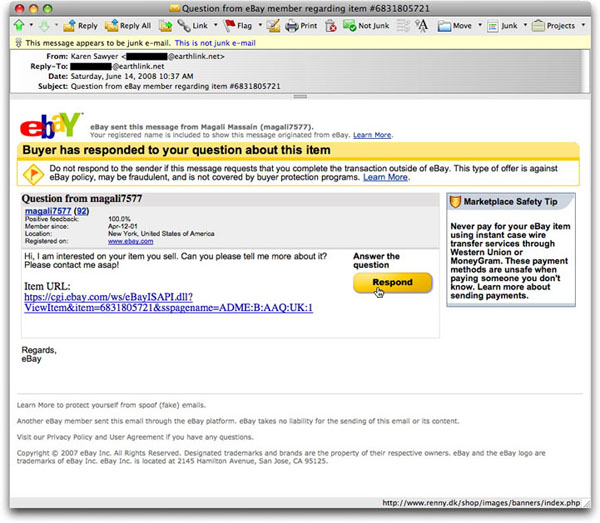
Spotting an eBay Phish [Updated]
This post is for eBay users out there, especially those who actively sell items through the auction site. It is you sellers for whom the following phishing spam can be troublesome if you're not on the lookout for crooks trying to nab your login credentials. Note that what I'm saying here applies to all users, regardless of operating system—this is not a Windows-only situation, because Mac and Linux eBay users can lose their login credentials just as quickly as anyone if they respond to these types of phishing messages.
Here is a message that found its way into my email client today:
I have blocked out only two pieces of information—the user name of an email account that might be a real address of an innocent bystander. There is nothing else in this message that has association with reality, but more about that in a moment.
If you are an active eBay seller, you have probably received messages from potential buyers asking questions about an auction or item you have for sale. If you have your preferences set to send these messages to your account email address, such messages look like the one above—at least in a macro sense. Look a little closer, however, and there are numerous signals that this is not genuine.
The first signal is that the recipient is not named at the top of the message (to the right of the eBay logo). Although the message accurately snatched eBay's warning ("Your registered name is included to show this message originated from eBay."), the supposed sender's name is shown, not the recipient's.
The second signal is evident if you take a moment to roll your mouse over the Respond button (or, in this case, all links in the message). Most email clients reveal at least the start of the hidden URL associated with a clickable image. In the above screen shot, I've positioned the mouse above the button to reveal (down in the bottom status bar) the destination URL. This button ain't goin' to eBay, but to a Danish web site (the .dk country domain), whose page would replicate eBay's login screen, prompting you to enter your login ID and password. I normally block out these addresses in images shown here, but the ISP hosting that domain was Johnny-on-the-spot and had suspended the entire site by the time I saw this message. That warmed my cochleae cordis.
So, those are two obvious things you can see without having to know anything about email message headers or how legitimate versions of this type of message operate. Although in smaller, grey print, the use of last year's copyright date would be a third clue.
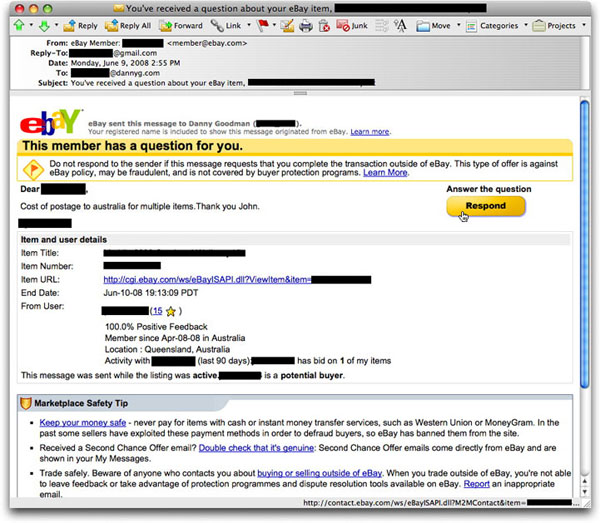
In contrast, I'll show you a genuine message of this type from my own inbox:
You'll immediately notice that I have redacted a lot of material, some for privacy reasons, and some for the sake of eliminating any kind of self-promotion of one of my (now ended) auctions. But the amount of redactions—compared to the phony message earlier—is also a good indication of how much truly identifiable information is conveyed in genuine eBay messages of this type. For example:
- My name and eBay user ID are explicitly mentioned at the top of the message (to the right of the eBay logo).
- My eBay user ID is used in the salutation ("Dear so-and-so") of the message.
- Very explicit details about the auction item, including title (which also appears in the Subject: line), are spelled out in full.
Using the rollover test, the link attached to the Respond button begins with something that looks legitimate. But because the complete URL isn't shown, it is not sufficient to trust the link just by that fragment. A long URL can be coded in a way in which a legitimate-looking prefix is actually ignored, and some other site becomes the real destination.
Just because the second message appears to be genuine should not be enough, however. Although phishers tend to work in bulk, a more diligent crook could specifically target you with a message that looks exactly like the second one above. Indeed, the crook would have to do a little research, but everything he would need to replicate this message—except your email address, unless you also (foolishly) include that in your item description—can be derived directly from any one of your auction listings.
How, then, can you prevent yourself from being fooled by a bogus eBay email message? You can continue to let your email inbox receive copies of eBay messages, but never, ever, ever respond to one of these messages through your email client. Instead, log into your eBay account as you normally do, and visit the "My eBay" section of the site, where you can find a link to your messages ("My Messages"). Use only the My eBay message facilities to send and receive initial contacts with eBayers you don't know. Additionally, whenever you send a message or reply to someone's query, be sure to check the box at the end that prevents your email address from being sent with the message. Let eBay provide the address only to those who buy from you, or from whom you buy stuff.
Additionally, heed eBay's further advice about keeping transactions solely within the eBay system. If someone has had his or her eBay login credentials phished, that means that a crook can hijack the account and initiate a shady, off-eBay deal with you through the eBay My Messages system. The minute you or another party try to get creative, you lose any protection that eBay might afford you if you follow the rules.
EBay accounts and goods offered on eBay are rich targets for crooks. I hear countless stories from former eBay users who won't touch it because of a bad experience. I suspect a large percentage of those folks are mad at eBay because the company wouldn't make good on a foolish mistake the user made. It's like getting mad at the bank whose Automated Teller Machine yielded hundreds of dollars from your account to the friend of your roommate to whom you gave your ATM card and PIN.
I've bought and sold casually on eBay since December of 1996. Even as I write this, I have some hobby-related items up for auction. Perhaps the key to being a happy user is remaining vigilant against possible intruders or those trying to "game" the system. Keeping an eye out for phony messages is one of the first steps you should take to prevent yourself from getting into trouble.
UPDATE (17June2008): This bogus eBay seller, magali7577, has shown up on similar phishing messages to French ebayers, with the message and destination phishing site replicating French eBay material. Merde!
Posted on June 14, 2008 at 06:29 PMJune 13, 2008
Malformed Phish, or Cracked Web Site? [Updated]
Every once in awhile, something comes in over the transom that causes me to get a cardio workout even though I'm still sitting on my butt. It gets my blood flowing and puts all my sensors on high alert.
Such was the case today when I received what looked like a typical PayPal phishing message. This one was of the oft-used variety that claimed someone had just sent me a couple hundred bucks, and I could click the image link to view the details of the transaction. The usual deal here is that the link is to some other site, either a freshly-minted one or one hijacked from an established domain and server. They're after my login ID and password. Plus, it's Phriday, so that's what I expected.
As is my usual modus operandi, I checked the URL of the actual link in the message's source code before doing anything. To my amazement, the linked URL was to the real PayPal domain, complete with SSL protocol (https). The only thing that differed from the plain https://www.paypal.com address was the addition of a forward slash and a two-character subdirectory name—which I won't mention here. There were none of the URL spoofing tricks that I've seen in the past, such as the one whereby the URL is intentionally malformed so that the URL that gets linked to is hidden further down to the right of a long URL.
The message was definitely a phishing message. It did not originate from a PayPal server; the text began "Dear Member;" it was addressed to an address that is different from my PayPal login address; and there was no reason for some fellow in Canada I didn't recognize by name or email address to be sending me two hundred dollars. For the record, here's the body text of the message:
You've got new funds! Dear Member,Robert Cooper just sent you money with PayPal.
Robert Cooper is a Verified buyer.----------------------------------------------
Payment Details
Amount: $200.00 USD
Transaction ID: 2XC29017VB4724053
As I recommend to anyone receiving an unexpected message about a financial-related account, I logged into my PayPal account via the bookmark I've used for years—just to see what the account says about the matter. Needless to say, there was no payment to me for $200.00. Simply confirming my assumption.
I was, however, curious about that link. Would it, ultimately, take me to PayPal?
I clicked it. (gasp)
To my amazement, the link not only took me to a real PayPal SSL URL, but the page even read my PayPal cookie to insert my actual PayPal login email address into the login form, just like the main PayPal page does. The Address bar showed the same URL I had seen in the email message—the real PayPal domain plus the two-character subdirectory.
At this point, I thought of those scary movies where the terrified heroine has the cops trace phone calls that have frightened her all night...and they tell her, "The calls are coming from inside the house!" Had someone inside or outside of PayPal embedded a phishing page within the PayPal servers? If so, had I just revealed my login email address to a crook (via the cookie), who could then try brute force password attacks to attempt to access my account?
I thought I should at least bring these possibilities to PayPal's attention as quickly as possible. I've ranted before about trying to convey what might be vital security information to a large company, and this effort was no less satisfactory. The frustration of dealing with customer support reps from the other side of the planet who are schooled in appeasing customers with insincere sympathy and supplying stock answers to questions I didn't ask only infuriated me even more. A supervisor did more of the same, but with less of an accent. I really don't need to hear the basics of Phishing 101. All I wanted was for this information to get to the right security people within the company as quickly as possible. If their systems had been compromised, you'd think they'd want to know about it pronto. The only thing I know for sure as the result of my phone call is that my suspicions were marked on my account record. B.F.D.
It has been about five hours since my report (and forward to PayPal's Spoof Department). Using a non-cookie-propagating way to check the URL, the page is still active. I find it hard to believe that PayPal—assuming the security folks have heard about it by now—would let an alleged compromise of this scale go unabated. Perhaps that URL is to a genuine PayPal login page—some kind of alternate page with a specific, legitimate purpose in mind. This would mean that the phisher screwed up by not entering a URL of a crooked site (it is unlucky Friday the 13th, after all). But then, again, why would the URL placeholder have the alternate PayPal URL in it, and not the regular plain URL? And how did the phisher know about this alternate login page?
Or was this message a one-off, instigated by my doctor to get my heart a-pumpin'?
Too many questions. Not enough answers.
UPDATE (14June2008, 0900PDT): Overnight I received another "Robert Cooper" PayPal phishing message. The link on this one was to a hijacked web site in the UK, which, in turn, redirected to the actual phishing page in a hijacked Spanish physician's web site. This is pointing more and more to a case of a malformed phishing message for the one that rang alarm bells here yesterday. I'd still like to know what that alternate PayPal login page is all about, just to settle my curiosity. In the meantime, I feel better about the integrity of that PayPal page.
Posted on June 13, 2008 at 04:38 PMJune 11, 2008
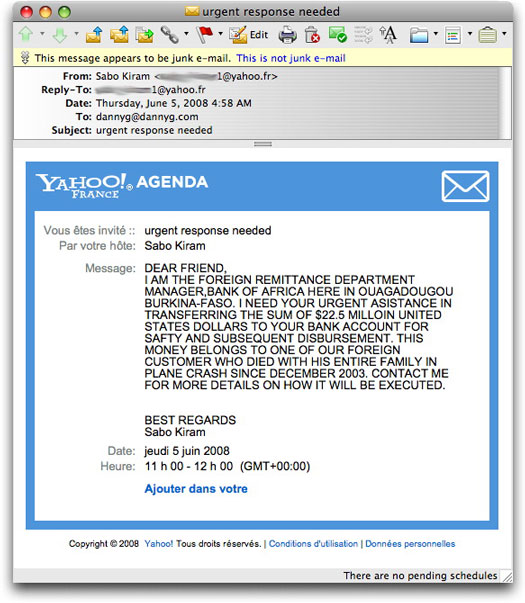
419—United Nations Style
This has been going around since at least last October, but one fell into by inbox today.
The message claims to come from the United Nations Foundation, telling me that I've been chosen as one of the final recipients to receive oodles of cash. None of that worthless USDollar dough...Pounds Sterling, yah! Here's the message in full (mostly to help seed search engines in case a more gullible recipient performs a shred of due diligence):
United Nations Foundation
1800 Massachusetts Avenue,
NW, Suite 400 Washington, D.C.
20036Attention:
The United Nations Foundation (UNF),would like to notify you that you have been chosen by the Board of Trustees as one of the final recipients of £3,000,000.00 (Three Million GBP) for your personal, business, or educational use to aid the underpriviledge in your teritory/country The UN Foundation was created in 1998 with entrepreneur and philanthropist Ted Turner‚s historic $1 billion gift to support UN causes and activities.
The UN Foundation builds and implements public-private partnerships to address the world‚s most pressing problems, and broadens support for the .U.N.through advocacy and public outreach. The .U.N. Foundation is a public charity and winners are selected without any criterary,
You are required to contact the Claims Officer below for qualification documentation and processing of your claims. After contacting our office with the requested data,you will be given the bank details contact to optain your donation pin number,which you will use in collecting the funds.
Please endeavor to quote your Qualification numbers (UNF-039455-UNOG) and Amount won in all discussions.
To file Your claims Send listed requirements to:
Contact European Finance Officer
Dr.Letts Roger Bernard
E-Mail- [removed]@sify.com
E-Mail-united_nations.claims@[removed-but-well-known-free-email-domain].com
Sincerely Mrs,Julie Hans
Chairman of the Board
© 2008 UN Foundation,All Rights Reserved
Now, there really is a United Nations Foundation at the Washington, D.C. address shown in the message, and funded in part by Ted Turner's billion-buck donation. But they don't hand out multi-million-pound awards on a whim—any more than Microsoft sponsors a Dutch lottery to encourage people to use the Internet. Nor would an organization with its own domain name have to use free email accounts in India and the U.S. to handle such "important" work.
I'll add a couple of BTWs ("by the way"). First, contrary to the signature in the message, Ted Turner is the Chairman of the Board for the U.N. Foundation. Second, I'd like the sender to contact me regarding my disregard for the copyright notice.
Posted on June 11, 2008 at 08:14 PMJune 05, 2008
Spamming Via Yahoo! Calendar
Put a free service on the Internet, and someone will surely find a way to abuse it. And so it is with the Yahoo! Calendar invitation service, which emails invitations to an event you place on your calendar. You supply the message and invitee email addresses, type in a CAPTCHA code (or use one of the CAPTCHA crackers out there), and you've just spammed a long list of addresses. The message headers are clean, in that the backward chain consists entirely of yahoo.com IP addresses—giving the message a better-than-average chance of making it through blocklisting spam filters.
Here is a 419-type spam I received today from the French version of Yahoo! Calendar:
Notice that the sender's account ends in the numeral 1. As Yahoo shuts down his accounts for abuse violations, he'll probably increment the number for each new account. I'd do things a little differently if I were this 419-er, but then again, I've seen the best at work over the years. I'm not about to offer him advice for free or otherwise.
Posted on June 05, 2008 at 09:51 AMJune 01, 2008
Confused Spammer
A long-time, carpet-bombing medz spammer must be taking some of his own pillz. I've seen messages today whose Subject: lines clearly point to offering erectile dysfunction medz—the ol' "ED" pitch. But the one-line message bodies talk of other issues:
- Dont give up on loosing hair. You can stop it right today.
- Summer is coming, best time to drop off some kilos.
This is the same guy who (he's not alone) frequently promotes Canadian pharmacies. Except he's in the Far East—and I'm not talking Newfoundland.
He also hasn't gotten the memo that most U.S. recipients wouldn't know a kilo if it dropped onto their toes.
Posted on June 01, 2008 at 11:26 AM