| Home | The Book | Training | Events | Tools | Stats |
March 28, 2006
Another Idiot Closer to Home
No sooner do I rant about the Idiot Italian Spammer than a spammer from northern California pulls some of the same idiotic stunts.
From what I can gather (that is, by means other than visiting the spamvertised Web site), this message is promoting a self-published book, produced in California. The spamvertised site's domain appears to be registered to the author. The blurbs make it sound like part thriller, part romance novel with religious overtones. I can't really tell. I don't really care.
Two things tick me off Big Time about this mailing.
First, this message violates major provisions of the U.S. CAN-SPAM law. Let me count the ways:
- The subject suggests the message is an "update." Update to what? There is nothing of news or new information in the message body—just a sales pitch and testimonials from people I've never heard of. Misleading.
- There is no mailing or physical address identifying the advertiser or sender.
- There is no provision to opt out of the mailing list.
I also want to know how my email address got onto the list. Harvested perhaps (another violation)? I looked through the list to see if I could identify any other names in search of a possible connection. At most I found one name that could belong to someone I know but haven't had contact with in years (and the actual address doesn't look right to me, anyway).
Second, like the Italian job, this message exposes 270 email addresses in plain view to all recipients by listing them in the To: field. This is so dangerous to all 270 of us that my blood boils. If even one of these recipients has an infected PC (there's a very good likelihood that the infection percentage is in the double digits), all addresses will be captured and sent off to additional spam/phishing/virus gangs so that we'll get even more crap from the worst of the worst. Thank you very much.
As an author, I know how difficult it is to get a book noticed. You slave over a title you believe is excellent, yet sales are horrible. BTDTGTTS (been there, done that, got the T-shirt). But spamming—breaking a federal law and putting all recipients' email addresses at grave risk—is not the way to do it. And if the author was hoping that even negative publicity is better than none, I've been careful to omit any references that would lead a Google search to his doorstep.
Posted on March 28, 2006 at 08:10 AMMarch 24, 2006
Idiot Italian Spammer
I happened to see a spam message that not only did so many things badly, but it was a complete waste of bytes and bandwidth. And, boy, did he waste bandwidth!
It comes from an Italian computer retail store called Tutto Computer. If that were in the States, I think it would be called "Everything Computer." I wish I knew Italian so I could call this guy whatever "Everything Stupid" would be in Italian.
- He mailed batches of 1000 messages. How do I know? He included the alphabetical selection of 1000 addresses in the To: field of the message. My address was between those whose user names started with "ch" and "de." That list, which was sent with every freakin' message occupied more than 28,000 bytes per message. It also exposes those 1000 addresses to each recipient in that block. It's an international group, with domains from Italy, Portugal, Spain, Brazil, Germany, United Kingdom, France, Romania, Canada, and dozens more, including the worldwide .com and .org domains. If any one of those recipient's PCs is infected with a typical virus, that virus will harvest all 1000 addresses from the email file or Web page cache.
- Speaking of harvesting, a kind of disclaimer indicates that this spammer intentionally harvested email addresses from Web pages. I believe he has made the assumption that displaying one's address on a Web page is the equivalent of opting in to his list.
- He's trying to be international with his offering, but does so in the most ludicrous way. The offering is made, obviously, initially in Italian. But then he includes translated copies of the offering in English, German, French, and Spanish. Now, I have no quibble with someone trying to be multi-lingual. But pleeeeeze do not rely on computer translations (such as Babelfish) to do all the work of the translation. The English, for instance, is practically unintelligible (capitalization preserved for your enjoyment):
KIND CUSTOMER, I WRITE TO THEM IN ORDER TO INTRODUCE THEM THE FUTURE OF COMPUTER SCIENCE TO THE BEST PRICES ON THE MARKET.WE ARE A COMPANY IN EXPANSION WITH A LARGE One WE WANT TO MAKE TO GROW The MARKET Of the COMPUTERS And TO MAKE TO LOWER the PRICES Of COMPUTER SCIENCE IN KIND.
IF WE DO NOT DISTURB IT TOO MUCH WE WILL BE LIETI TO MAKE TO VISIT THEM OUR SITUATED OF SALE ON LINENS IN DAILY INCREASE, And WILL BE MUCH HAPPY IF HE WANTED TO COMMENT OUR PRODUCTS GIVING To US COSì WAY TO IMPROVE, And COSì MAKING TO IMPROVE The GENERAL ECONOMY OF A BY NOW COMMON INTEREST To MANY.
With this message originating from Italy, I'm assuming this spammer couldn't give a rat's butt that this message violates several provisions of the U.S. CAN-SPAM law. I'd also wager that it violates at least one provision of the European Community Directive and Italy's implementation thereof.
But, hey, this guy runs a computer store, so he's gonna use the technology to promote it. I believe the name applies in both English and Italian: Idiot.
Posted on March 24, 2006 at 04:35 PMMarch 23, 2006
Images in Email Messages
Spam Wars, and just about every article on the subject, recommends turning off the display of images in your email client and in Web-based email preference settings. This choice prevents automatic retrieval of an image from possibly confirming your email address to the spammer (if the image download is coded with what are often called "web bugs"). Even if you're set up to avoid image downloading, you may be wondering how an image sometimes appears in a spam message, and what kind of risk such an image offers.
Depending on how you view your email, you may not even know that such an image is embedded in the message—it arrives as a portion of the data comprising the entire message. My Microsoft Entourage (Macintosh) email client indicates in the list of incoming messages that such messages have one or more attachments. Over at Comcast Web-based email, however, awaiting message lists do not signify attachments of any kind until you open the message—and then only if you've set your Display preferences to "List HTML as an attachment only," a choice that probably confuses lots of non-techy users.
Although it takes a little more work for themselves, it appears that an increasing number of spammers like embedding graphics in their messages. The graphics are typically of text—text that cannot be searched and filtered for spammy words and phrases. Because the graphically-represented text isn't searchable or scannable, spammers are free to use the real spelling of "Viagra," pump-and-dump stock scam phrases, and the true names of human body parts. Moreover, if the recipient retrieves the message on a laptop computer and disconnects from the Internet, the message will display the images with the computer off the grid.
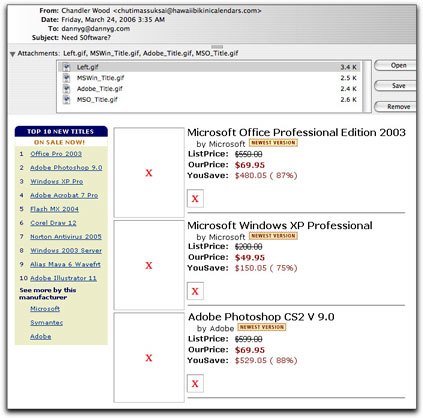
The following screen shot shows a pirate software spam message that has both self-embedded images and links to downloaded images from amazon.com. Because I have automatic image retrieval turned off, the amazon.com images are shown only as placeholders:
(If you are interested in how images ride along in the source code of an email message, Spam Wars offers a gentle introduction to the subject of email content types and multi-part messages. This knowledge helps demystify the gobbledygook you'd see if you inspect the source code of such a message.)
Spammers who use this technique and appreciate the need for speed at least try to compress the images to be as small as possible. The smaller the total size of the message, the more messages can be sent per second (through zombie PCs around the world). Note, for example, that the four embedded images of the message shown above occupy less than 11 kilobytes. The entire header, message content (including some meaningless text-only content offered to help bypass content filters), and attached images come to less than 17,000 bytes. Contrast that with a jumbo message from a different—and absolutely clueless—source that contained six images ranging in size from 140KB to 482KB—a message total of nearly 1,500,000 bytes. (Ironically, this tubby message from Hong Kong was selling accessories for GSM mobile phones, which, if used to receive the message might blow up in the recipient's hand.)
The question remains: How safe are these kinds of embedded images?
If the data is genuinely that of an image, the act of rendering the image should not be giving away any identifying information about you. With respect to malware, before late December 2005, I would have said such embedding would be harmless. But 'round about that time, the Windows Metafile vulnerability reared its ugly head. Without getting too technical about it, this vulnerability could potentially allow the rendering of an attached image (of a particular type) to grant external access and control of your PC to a Bad Guy. Microsoft came forward with a patch, but the discovery of this flaw (as well as others on more than just the Windows platform) makes me uneasy. It reinforces the fact that even things that seem safe may contain as-yet undiscovered vulnerabilities that could put users at risk if Bad Guys find the holes and instantly spam the world (a "zero-day" exploit) with "harmless" messages that ultimately take over your machine.
The problem with succumbing to that level of paranoia is that it makes email nearly impossible to use. Not all spam or viral email is easily identifiable from just a Subject line. If you use Web mail, you may not have the ability to scan the source code of the message without first viewing the message. Despite the comparative difficulty that popular email clients often present to view the source code, it is still the safest way to examine a message for spam potential, allowing you to delete it without exposing you or your computer to any harm. It is my standard practice with any unexpected or manifestly unidentifiable incoming email message.
Spammers and malware authors like to take advantage of defaults and convenient operating behaviors that open doors for their tricks. Knowing this, I don't mind the little extra effort I expend to handle all suspicious (i.e., unknown) email. Unfortunately, most users aren't even aware of the potential dangers arriving daily in their inboxes.
Posted on March 23, 2006 at 05:02 PMMarch 19, 2006
Loan/419 Hybrid
Mortgage spam has been out of control for years. So have the 419 advance-fee scammers. New (to me, anyway) for 2006 is a hybrid of the two. Unlike true mortgage spam, however, this one is probably less interested in your personal information, but is really interested in extracting some money from you before you receive (not!) your loan.
I'll spare you the lengthy drivel of the message that begins:
You could be chosen for this Life Time Opportunity.
This clown has the audacity to claim he represents (I kid you not) The United Nation Development Loan and Scheme Project (UNDLSP). The priority of this project, we're told, is:
to provide a low interest scheme loan to private individuals and companies to help combat the debilitating effect of poverty globally.
In the course of fighting global poverty (hold your sides):
We also provide home equity line of credit, where our accredited bank gives you a checkbook or credit card to make purchases, which then accrue against your home's equity.
See, Bono, all that hard work has finally allowed struggling homeowners to get a line of credit from $50,000 to $1,000,000! Woohoo!
Here's how to start the process:
Candidates who are interested in the UNDP Loan Scheme Project are advised to send copy of their identification document, age, profession and contact telephone/fax number to the "Loan Officer" in De Hague, Netherlands and request for "Loan Application Form" which must be completed and return to the accredited Loan Officer who has the mandate to begin the process of analyzing and verifying the information on the application form to determine the client's creditworthiness.
I'm not exactly sure what an "identification document" is, so I guess I can't apply for this great loan opportunity. Otherwise I'd send off the email right away, since I don't consider it odd that such a prestigious organization (even if the "United Nation" isn't exactly the "United Nations") would use a Google gmail.com address.
One thing is certain: This isn't a "no points, no fees" kind of loan. In fact, anyone who applies will have to pay nothing but fees, and even then never see a dime.
I grade this 419er a C+ for creativity.
Posted on March 19, 2006 at 02:21 PMMarch 14, 2006
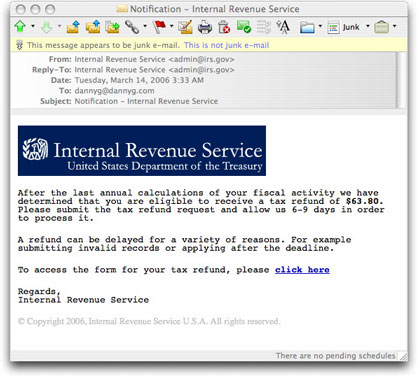
The IRS Refund Phish
Like probably millions of others, I received a new phishing message that has been making the rounds. This scam claims to come from the U.S. Internal Revenue Service, complete with actual logo image from irs.gov. The message alerts "me" to the fact that I am owed an income tax refund in the amount of $63.80. Rather than cut a check (like they normally do, or direct deposit into your bank account that you supply when you file your tax forms), they will refund by depositing funds into your credit card account. Here's the message:
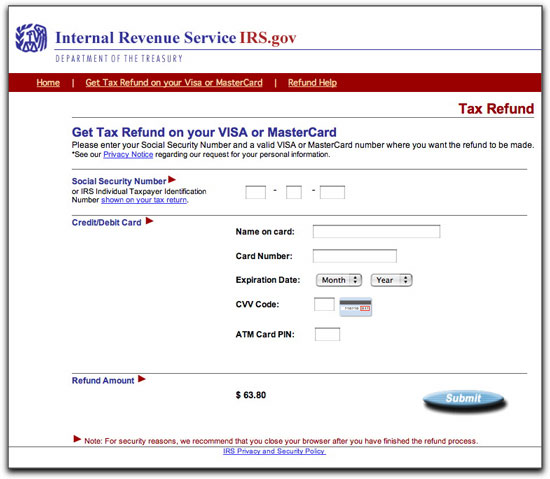
When I first saw this message, I suspected the destination link was a malware loading page, but so far I don't see that. Only a typical phishing page that asks for your identity information:
The source code of the Web page reveals that it uses style sheet and JavaScript files from the real irs.gov Web site. There are even instances of this "official-looking" notice:
<!-- ============================================================================== Copyright (c) 2001 Internal Revenue Service The US Government possesses the unlimited rights throughout the world for Government purposes to publish, translate, reproduce, deliver, perform, and dispose of the technical data, computer software, or computer firmware contained herein; and to authorize others to do so. ===================================================================== -->
But this page ain't from the I.R.S. No, it's hosted in China. In fact, it looks like a run-of-the-mill server hijacking, a tactic so common among phishers. According to the New York Post, the I.R.S. isn't very happy with this misuse of its good name, and is on the hunt for the scammers.
I wish the agency well. I really do.
Posted on March 14, 2006 at 08:19 AMMarch 07, 2006
Who Falls for This Crap?
I suppose that if you've been out of work for some time and are getting desperate, you might respond to the following spam. But this thing smells so badly, I can't imagine anything good coming from it:
Dear Mr(Mrs)! We are looking for an efficient and well-organised to assist our company in running bussines. This offer is part of a job-share working-some hours per day.You will have excellent word processing self-motivation, initiative and the ability to work independently are also essential, as is tact and discretion. Annual Salary 25-60K GBP. Bonus every mounth. Weekly salary about 1000-1500 EURExcellent Benefits Include:
-Paid Holiday of 20 days for the first complete year worked and then increasing by 1 day a year to a maximum of 30 days
-Paid over-time
-Defined contribution pension scheme (invitation to join after 3 months))For further details please contact, Gretta Lourenz, director World Trans Inc
e-mail: [removed]@aol.com
My guess is that this is one of two scams. The first possibility is that you will be asked to fork over some up-front dough for supplies or other stuff that you'll never get—a variation of the advance-fee (419) ploy. The second possibility is that you will be asked to launder funds for some kind of international racket. I've read of cases like this in the past, where the laundering intermediary (you, if you take on the "job") wound up in the slammer here in the States. Both scenarios require "tact and discretion" on your part to avoid alerting the authorities who will either try to talk you out of sending 419 money or arrest you for money laundering.
Oh, and I don't think I'd be in a hurry to work for an international company whose "director" uses an AOL email address.
Posted on March 07, 2006 at 09:20 AMMarch 05, 2006
Email Continues to Break
One of the worst things that happens in the spam wars is the false positive—that piece of good, desired email that silently gets filtered out or trashed before it ever pixelates before the eyes of the recipient. This kind of collateral damage can occur for a variety of reasons, which I discuss at length in Spam Wars.
As spam filters become more aggressive to fight off increasingly sneaky attacks by spammers and crackers, they catch plenty of good email. If the filtering mechanism in place at the incoming email server doesn't segregate suspect messages for a user to scrutinize manually, the message goes into the "bit bucket." Even if the message manages to get into a "suspects" folder, there may be so much in there that the recipient doesn't bother looking for the golden needle in the haystack, and sets the whole stack alight, sight unseen.
I know that some good mail occasionally gets trashed in my own email server. Even though I'm totally in charge of how suspects are handled, I simply don't have the time to look through thousands of otherwise deletable messages every day for the once-in-a-while good message. I let the server summarily delete those items tagged as spam. If some human whom I haven't already whitelisted really wants to reach me, I provide multiple ways to get past the filters. For example, using the contact form for this Web site guarantees your message will reach me (and won't be forwarded or copied anywhere, so those few jerks who try to hack the form handler can stop trying to see if it relays email). At my dannyg.com Web site, I provide instructions for a "secret string of characters" that you can copy into the message to guarantee its delivery. My primary email address was hosed years ago, so I don't bother trying to disguise it. I know that my address is repeatedly harvested from the site, and when I first implemented the "secret string" process a few years ago, I thought I'd have to change the string perhaps once a month to keep it off the spammers' lists. Surprisingly, I have not ever detected a spam message that exploited that string. Spamming humans never visit the page to read what's there, and the crawlers that have harvested the address from the page on the Web and in cached copies of the page in Trojaned PCs around the world haven't picked up on it, either.
What brought the false positive into view for me recently was a message I received from a reader of my Dashboard book (a Mac OS X technology). Buyers can request a username and password to use to download the companion files for the book from the publisher's Web site. This reader wrote directly to me to complain that although he had requested the username/password twice from the publisher, he had not received a reply. I thought this odd because in my experience, SpiderWorks is incredibly responsive to customer issues. A phone call and an email later, I learned that the publisher had not only received both requests, but had responded with the desired information promptly both times.
For whatever reason, the reader's Verizon email server was not passing SpiderWorks email to the recipient. I checked to see if SpiderWorks' email IP address might be in a range that is listed on a blocklist. Nope. The copy of the original email message I saw was a plain text message (not HTML), included no attachment, and doesn't contain ads for Viagra. So what's the deal?
We may never know. I forwarded a copy of SpiderWorks' message to the reader. I know he got an earlier email message from my email server, so we'll see if one sent by me with the SpiderWorks content will get through.
That we can no longer trust email is a cryin' shame. These days, if you want to send an email message to someone who hasn't previously whitelisted you, your rate of success is starting to approach your rate of success with a lottery ticket.
Posted on March 05, 2006 at 02:49 PMMarch 02, 2006
Mortgage/Diploma Spam
For the past few weeks I've had this creepy feeling that the increase in diploma spam and the style of some of the messages reminded me a lot of mortgage spam. Call it a seventh sense (the sixth sense, apparently, is reserved for those who see the dead).
I wasn't paying close attention to the spamvertiser URLs of the messages as I sped copies to the Federal Trade Commission's "refrigerator" (spam@uce.gov). But in short order today, I received both a diploma spam message and a mortgage spam message that brought everything into focus.
The spamvertised domain (not revealed here to prevent anyone from hitting the site and jacking up the hit counter) was the same in both messages. The only difference was the subdirectory to which each message led. The diploma spam went to the "mba" directory, while the mortgage one went to the "was" directory.
Naturally I checked on the domain name registration. I found exactly what I expected: Network Solutions (registrar) displays a record created Monday with completely bogus data:
- A street address in Denver that doesn't exist.
- A ZIP code for Denver in the 29000 range (Denver is in the 80200 range).
- A contact email address that is rejected by the mail server for that address.
The domain record was created on Monday and modified on Tuesday (it's now Thursday), so it's possible that the registrant used a valid email address during registration, and then changed it to a phony one after the registration was completed. I'll file a dispute out of a sense of duty, but by the time anything happens (don't get me started), the spammer will be using a new and different domain.
Most of the diploma spam I've seen over the last several months ask idiot responders to call a U.S. phone number (the number is to an outfit that acts like an answering/forwarding service, as noted by Brian McWilliams). But what about this confluence of mortgage lead and diploma lead spamming? That a diploma mill would find it necessary to hide behind a lead generator (as many legitimate mortgage brokers do with their "don't ask, don't tell" policy about how leads were acquired) seems kind of bizarre to me.
I can only hope that the software that crawls through messages forwarded to the FTC refrigerator can pick up on the connection. The messages not only don't come close to meeting the requirements of the CAN-SPAM law, they're virtually demonstration examples of how to thumb one's spamming nose at the law. Perhaps the FTC can assist in making this spam operation perceptible by the sixth sense.
Posted on March 02, 2006 at 09:34 AM
Seen in today's listings:
Subject: Get your deploma today
'Nuff said.
Posted on March 02, 2006 at 08:49 AMMarch 01, 2006
Charter Communications: The Phisher's Friend
I've encountered plenty of clueless ISPs in my days as a phisher stomper, but Charter Communications is climbing rapidly to the top of my list. One of their customers' computer has been compromised since at least 27 February. The machine is acting as a Web server for a PayPal phishing collection page (just one of the many things that your computer can become if taken over by a botnet). I have received ten—count 'em—phishing emails with hidden links taking recipients to the fraudulent page. The messages have a variety of subject lines, and they are coming from yet other compromised PCs (botnet zombies) from a variety of U.S.-based providers.
I did my usual reporting thing to Charter's abuse address back on the 27th. As is my custom, I included a quoted copy of the phishing email message source code (including headers) just as further evidence that messages are spewing around the Internet leading users to the compromised computer.
At first I received a typical automated reply, which I tend to ignore because it doesn't really mean anything. But then I received another that said because the phishing message didn't originate from a Charter IP address, they're dropping the incident.
After counting to ten (not knowing it would become the number of phishing messages I'd soon have stacked up leading to the same Charter address), here was my reply:
I am reporting a fraudulent Web page in your IP space. The location of the fraudulent site is at charter.com, which is registered to Charter Communications.Please advise if you wish me not to report such activity in the future.
Despite their initial quick first response (within minutes of my original submission), Charter has not responded to my second missive (not that I expected any response other than the removal of the offending page—that's all I care about). Two days later, the page is still up, and it must be performing well if the phisher is continuing to direct phishing victims to the site.
I understand the frustration that leads some spam fighters to want to flood an offending site with something like a denial-of-service attack. Perhaps if this customer's computer ground to a complete freeze under the burden of millions of request connections to the hidden PayPal phishing site, he'd give his support rep at Charter a call, and someone would look at the traffic at that IP address. Or at least the site might become inaccessible to the majority of potential victims.
But I do not agree with D-O-S tactics on principle. So that's out of the question.
Perhaps the word will get back to Charter that there is a hole in their support/abuse reporting system. There are forms of abuse other than sending spew. Hosting fraudulent Web pages (knowingly or un-) is another form of abuse, and believe it or not, dear Charter, it can happen to your customers. Get with it, and stop contributing to the phisher's cause by turning a blind eye to the problem (or turning a seeing eye verrrry slowly).
UPDATE (5 March 2006): It only took a week (HTML needs a contextual tag for sarcasm), but the offending Web page is finally down. The tally of phishing messages I received through the week pointing to that address was an astounding 17! That the page is now down could also mean that the Charter customer's computer got so sluggish with victim traffic that he restarted his computer and modem, in which case Charter's servers may have handed out a different IP address. If that's the case, it shouldn't take long before the infected machine announces itself to the botnet controller, and we'll be at it again. In any event, with a one-week window of operation, the phisher won this round Big Time. If I were a victim of this phisher, I'd first be mad at myself for falling for the scam; but I'd also be angry at Charter for allowing this activity to go on for almost a week after acknowledging the report.
Posted on March 01, 2006 at 05:25 PM