| Home | The Book | Training | Events | Tools | Stats |
March 31, 2005
CAN-SPAM Helps Promote the Lies
There are tons of "email marketers" out there (who produce megatons of spam), and I'm convinced that most of them believe in their hearts that they're doing nothing wrong because they adhere to the U.S. CAN-SPAM law. But when they start lying in their spammy pitches, they don't deserve even the support of the Direct Marketing Association.
Case in point...
I was scanning through a few days' accumulation of spam suspects that had collected on my server. These messages are contained in a single text file, which I download in that form and view in a text editor. These messages never see the light of an email client program or HTML rendering engine.
On Tuesday came a message that was giving me a chance to opt out of further mailings from this source. How did he get my address? Here's what he says:
Please understand, the only way I could have your email address, is because you have given it to me along with your name through one of my advertising efforts.
You may have filled out your name and address to obtain one of my special gifts of a product, subscription, eBook, merchandise, vacation, business information, etc.
You, most likely, did this over the Internet, but it could have been at a booth show, at a state fair, through a mail-in coupon or any of a host of methods used in my various advertising campaigns.
As proof, he supplies a copy of the information I had "submitted." It includes my first and last name, email address, city, state, and ZIP code. There were blank fields for my address and day/evening phone numbers.
He signed with his name, U.S. address, and an instant message address, along with a removal email address. All very CAN-SPAM-ish.
Two days later comes another mailing from the same fellow. He begins:
First of all, I want to Thank You for staying on my contact list. In case you don't remember, you were given the opportunity to remove yourself in the last letter that I have verified you received 2 days ago.
I won't even bother getting into the business of how he got my email address and contact data. The chance that I supplied such info in response to an advertising campaign of his is next to zero. And I've never been to a State Fair. But this information is so readily available among spam list traders that my assumption is that he got the data that way. The mortgage spammers seem to have even more details, so the data this guy has is small potatos. If he doesn't bother to keep a real audit trail of his list sources, he can't prove otherwise.
(I also Googled the guy's name, and found that a couple of years ago he had spammed, noting in his message that he had accumulated databases of contacts and partners, as well as acquired addresses from network marketers. Oh, yeah. Those are all trustworthy sources of opt-in email addresses! In any case, now we know how he really gets his addresses.)
It's the second email message that reveals all. First, there is no possible way he can verify that I received any piece of mail. Is it because the first one didn't bounce? What decade is he from? Fewer and fewer email servers are bouncing messages after they have been accepted, even if the addressee is invalid (to reduce the scatter caused by forged From: addresses in spam and viruses). That an incoming mail server accepts a message is absolutely no guarantee that the message will ever reach the addressee. In truth, I hadn't ever "received" the message until I spotted it in this several days' collection of suspected garbage.
But the bottom line here is that this message sequence demonstrates the folly of an opt-out system when put into the hands of a typical email marketer. To this guy, the fact that I did not opt out means that I have opted in. I'll get all his mailings now. Well, actually, I won't because future messages from him will be immediately and unceremoniously deleted at the server...but he'll be able to "verify" that I received them.
So, what's an email marketer to do? My advice would be to convert to a confirmed opt-in (or, in DMA-speak, double opt-in) system. That means giving your current list a chance to really opt-in, and discard those addresses that don't. Your list will be much smaller, but much happier.
Something tells me that the chance of this email marketer changing his ways are as low as the chance that I filled out one of his response forms at a State Fair.
Posted on March 31, 2005 at 12:10 PMMarch 29, 2005
The Single Double Opt-in
Spam Wars readers know that I make a big deal about the use, misuse, and abuse of various spam-related terms. When a spam-fighter hears the term "double opt-in," the red flags pop up because email marketers commonly decry the three-stage registration process (user registers; mailer sends a coded confirmation message; user confirms receipt of coded message) as being unduly burdensome on potential registrants. Spam fighters call this sequence "confirmed opt-in."
The problem is that the Direct Marketing Association (DMA) uses the term "confirmed opt-in" to mean that the mailer simply "confirms" to the registrant that the registration has been received. What spam fighters call "confirmed opt-in" the DMA explicitly calls "double opt-in."
[Stage Direction]
(Extend your index finger and position it horizontally in front of your lips. Move your finger up and down approximately one inch in each direction rapidly while humming.)
If that weren't confusing enough, I saw an article in the March 29 issue of The New Zealand Herald in which the term "double opt-in" appears with yet another definition. Here's how the article claims one email marketer defines it:
Atlantis operates a double opt-in approach whereby users are reminded on the first email they have opted in and can opt out of receiving emails at any time.
Whoa, dude! That's not "double opt-in" by anybody's definition. Has a life of watching your toilet flush swirl in the "other direction" made you loopy?
To cap it all off, the article quotes David Harris, the author of a white paper submitted to the government that is considering a new anti-spam law. Although he sorta gets "double opt-in" right, he's recommending against the technique being legislated. Then comes this direct quote:
"The general experience of the industry is that malicious subscription is not a big problem[.]"
He fails to understand that "malicious subscription," as in your next door neighbor's kid signing you up to a sex newsletter, is not the issue. The "opt-out" scheme (which is what the marketer wrongly described as "double opt-in" above) does not protect recipients from getting their addresses harvested and added to all kinds of lists—maliciously. We here in the U.S. currently have a legislated opt-out system (the CAN-SPAM law). While the law makes harvesting illegal, the practice is impossible to stop, and lots of people get lots of mail they don't want, would never sign up for, and dare not opt out from.
At this writer's mail server, the general experience is that malicious subscription is the primary problem.
Posted on March 29, 2005 at 04:47 PMMarch 27, 2005
New Phish Ploy - Part Deux
No, I'm not psychic. But when I predicted last Friday afternoon that the "you've changed your email address" phishing ploy would be picked up by others, I didn't expect to see another one so soon.
In it came on this Sunday evening. An eBay phish using a very similar ploy—and the exact same IP and ISP Host data from last Friday's PayPal phish. Tonight's eBay version isn't quite as artful as the PayPal one...no eBay art, and a bit of logic that isn't very logical. The real link is to a U.K. domain with the word "ebay" as part of the domain name. Unfortunately, it's still up and running.
I guess wamu is next.
Posted on March 27, 2005 at 09:05 PMMarch 26, 2005
A Threefold Clueless Phisher
I sure have been posting a lot about phishers lately, but they've given me plenty to talk about.
Like a Washington Mutual (wamu) one arriving today whose From: address is service@paypal.com, and whose "re-confirm your account information by" date is January 15, 2005 (today is March 26th).
Unfortunately, this phisher hosts his Web form through a hijacked server in China, so it may take awhile before it gets shut down.
Fortunately, the link in the wamu phish message links to a PayPal phish form.
I keep hearing in my head a "Simpson's" audio montage of several dozen Homer "d'oh" sounds in rapid succession.
Posted on March 26, 2005 at 07:37 AMMarch 25, 2005
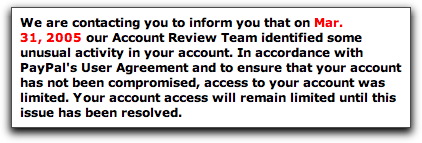
This Weekend's New Phish Ploy
I just saw a new psychological tactic in a PayPal phishing message that (unfortunately) will probably become quite effective. The message (with all the graphic trappings of a PayPal mailing) is supposed to be a confirmation that you have just successfully changed the email address for your PayPal account. To "prove" it, the message includes this little tidbit:
Change of E-mail address request was made from:
IP Address: 201.188.117.10
ISP Host: cache-dtc-ae11.proxy.msn.com
You're supposed to think that someone with an MSN account is twiddling with your PayPal account. Spam Wars readers know not to be intimidated by this kind of technobabble.
Here are the clues that this message is all phoney baloney:
- A check of the IP address provided above reveals that it is part of an unallocated block. It does not yet exist on the Internet, and certainly not today at msn.com
- The message header reveals that the message originated from an unnamed server in the Philippines, not one of PayPal's servers.
- The real URL behind the bogus visible link is to a domain that contains the word "paypal" in it, but isn't the same as the link shown in the message.
- Upon visiting the real PayPal site (through a bookmark you had set after typing in the real URL some time ago), the site already knows your current email address login—and it still works.
I'm happy to report that the destination for this particular phishing message got shut down lickety-split (easy pickings at a U.S.-based ISP). But I'm sure the tactic will surface on other phishing messages whose servers will be more difficult to shut down.
Posted on March 25, 2005 at 04:21 PMMarch 23, 2005
Yet Another Phisher Mind Game
I can't believe the Washington Mutual (wamu) phishes are still coming, but they arrive relentlessly. Sadly, in one I noticed today, the phish message tries to increase its credibility by embedding what looks to be a real attempt by a crook using your account for no good. Look at this little tidbit in the middle of a "Security Center Advisory!":
We recently received a request from Nike Central Store, Maine to enable the charge to your card in amount of $349,95.
THE PAYMENT IS PENDING FOR THE MOMENT.
If the purchase was made by yourself, please ignore or remove this email message. If you authorize the purchase, the billing will be approved and it will be shown in your monthly statement as "Nike goods Maine Central Store".
If the purchase was not made by you and would like to decline the $349,95 billing to your card,please follow the link below to decline the transaction:
Few recipients might notice the comma between the dollars and cents amounts. We North Americans use the decimal point, while a good chunk of the rest of the world uses a comma to separate big and little currency units. That the author of this letter ain't from around these here parts should trigger some level of suspicion, but this detail may be too subtle for most.
I'd wager that if you were a wamu customer with a credit card account, this message would catch your eye. If you failed to investigate the message to see if it's legitimate, you'd probably click on the link in an effort to decline the charge. To do so, you'd have to supply your wamu user name and password (in the least) to the real-looking, but totally bogus form.
Say "auf Wiedersehen" to your account balance.
Posted on March 23, 2005 at 08:49 PM
I show a few examples in Spam Wars where Rule #3 stupid spammers send out who knows how many millions of messages without using their software correctly. Among the telltale signs in the source code of HTML messages are the placeholders where their software is supposed to merge in text from fixed lists of words or phrases—sometimes just random numbers.
In one spam du jour for an online BA, MA, or PhD degree without no stinkin' "books, courses, tests or studying" I had to laugh when the operative URL behind the clickable link was specified as follows:
%RND_URL
It's great that this mailing went out without a workable link. The spammer self-induced my ZERO RESPONSE plan.
Posted on March 23, 2005 at 08:12 PMMarch 21, 2005
Three Cheers for Fast Anti-Phishing
The companies whose names and logos show up on the most phishing mailings have been working toward reducing the amount of time it takes to shut down the phishing Web site. I suspect that the most damage to individual victims occurs in the first 24-48 hours of a phish attack, so getting the bogus forms taken down quickly is important to protect victims from themselves.
I may have seen a result of that work today. Although I don't know when this particular eBay attack started, the message that found its way to me arrived at my server at 12:12pm local time. I spotted the message at about 12:25pm and got disgusted at the hidden domain name of the button that recipients are supposed to click. The domain name (registered way back yesterday) included the words "safeharbor" and "ebay." Domain registration data showed what looks to be a real name and address—very likely the data of a previous phishing victim (it has been done before). Unlike some phishers who hijack existing sites, this was an outright attempt to set up a scam Web site from the get-go.
The site was hosted at a small Pennsylvania ISP I had not heard of before. Like automated domain registration, I take it that signing up for a five-bucks-a-month-on-a-stolen-credit-card Web hosting account doesn't have any human intervention that might have taken notice of the fishy/phishy domain name.
But somewhere along the line, the ISP got the message before I had a chance to report it. By the time I tried to look at the phishing form no more than 20 minutes after the phishing message hit my server, the entire site was gone. History. Non est. In the bit bucket.
Kewl!
The domain name record is still active, so our crook may popup again, but not today.
Posted on March 21, 2005 at 12:33 PMMarch 18, 2005
The Old Switcheroo
The phisher gangs aren't doing a good job of keeping their wannabe phishing partners informed.
A lot of phishing messages urge action before some date in the future or (I'm so scared) my account will be suspended. The dummies forget to replace the default date with a future date, making the message sound really stupid.
There must have been so much of that going around that one phish kit supplier changed the spiel to let an old date work by saying that suspicious activity was noted on some past date. But what if this template gets into the hands of a phisher who normally puts the date forward? This is what you get:
This message arrived on March 18, 2005. Is it that the phishers don't read the garbage they send out, or is it that they can't read it? That so many of the links go to hacked South Korean servers leads me to believe the latter.
Posted on March 18, 2005 at 08:00 PMMarch 17, 2005
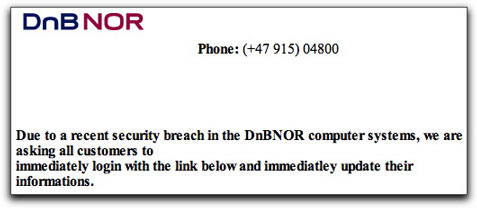
Signs of Phisher Desperation?
I've received phisher spam claiming to be from banks in several different countries. This is the first one I've noticed for a Norwegian institution.
You'd think for St. Patrick's Day the phishers would have picked on a bank from Ireland.
Now I'm wondering if we should be collecting phishing email messages like a world postage stamp album. Or like travel bumper stickers on the back of a station wagon.
Posted on March 17, 2005 at 12:03 PM
I noticed an odd pair of spam messages this morning that makes me wonder if spammers expect recipients to look at the URLs and domain names they include in their messages.
One medz spam (or should I say "p harm" spam) has a link to a domain name that includes the word "refi," as in "refinance." And a mortgage spam (or should I say "M0rtg age" spam) has a link with a domain name that includes the word "medico."
I did like the fact that the mortgage spammer gives sufficient clues to the observant recipient. The complete link (with domain name disguised) is:
http://bereave.ampersand.dis_guised.com/prime/liar/
Has he been reading some of my recent blog posts?
Posted on March 17, 2005 at 07:27 AMMarch 16, 2005
I Appear to be Deemworthy
By now most of the planet with access to the American TV show "Seinfeld" will have heard the term "sponge-worthy," a term that Elaine uses to rate her boyfriends. That word came to mind when I saw the following disclaimer on yet another mortgage spam:
Lastly, if uninterested please discard this email. It was only sent to a selected few that we felt deemworthy of this oppurtunity.
Ain't that a purty pitcher!
I did discard the email...after forwarding a copy to the FTC's spam refrigerator (spam@uce.gov). They've used chilled evidence to close down one big mortgage spammer already. I'm glad to give 'em some more to chew on to help them nab the next one. And the next one. And the next one.
Posted on March 16, 2005 at 11:36 PMMarch 15, 2005
The Warm-and-Fuzzy Liar
Spammers have no shame when it comes to outright lying to get you to visit their spamvertised Web sites. Look at this medz spammer message, whose Subject: line reads "Refill Reminder":
Hello,
As a valued customer, we provide you with occassional information and updates.
Our records indicate that you may be in need of a refill.
We hope that you will once again, give us the opportunity to offer you a great selection, low prices, and superior customer care. If you would like to place an order or browse our current products and specials, please visit the link below:
Let's see what's wrong with this spam (aside from the grammar snafus).
- The From: field lists a name of "Kari Dailey" with an email address belonging to an Australian domain (ending in ".net.au"). The account name at the domain is something that a chimpanzee would have typed (11 letters, one of which is a vowel).
- The message is signed by Tonya Steckle, not Kari.
- If I'm such a good customer, wouldn't you want to address me by name, rather than a cold "Hello"?
- Most prescriptions I've received (for things that would need a refill) provide enough of a supply for 30 days. But your registration record for the spamvertised domain was issued 15 days ago. Hmmm.
- The spamvertised Web site is hosted in Russia, and the domain name claims to belong to someone in Canada. If you're so legitimate, why do you need to use a "bulletproof" hosting service?
- The domain name is an amalgam of (count 'em) five everyday words, none of which indicates anythink associated with medicine.
- I've never ordered anything from you, so how could you have any record of me?
I gotta hand it to the author of the message, however. Except for one dangling participle and a misplaced comma, the message tries to sound professional and cuddly—looking out for my needs.
But you're a spammer sending spam by way of China. And a liar.
Posted on March 15, 2005 at 10:08 PMMarch 14, 2005
A Different Kind of Blog Spam
Bloggers who allow comments to their postings have recently had to fight off abusers who try to post the equivalent of spam messages to weblog pages in the form of comments below blog entries. It had become a way to get search engines that crawl popular blog pages to follow links to spamvertised Web sites to boost listings in search engine results. Bloggers have had to counter with a variety of defenses, including inserting a link tag attribute within all comments that instructs search engine crawlers not to follow links. That still doesn't keep blog spammers from abusing comments (and is the main reason I don't open this blog to automated comments).
I encountered a different kind of "blog spam," where the blogger is the culprit. It's not spam in the unsolicited mail sense, but more in the Monty Python spam-spam-spam sense. The posting announces the release of an update to a JavaScript-related product for Web developers. The product description occupies a couple of paragraphs.
Then comes this huge list of JavaScript-related terms in plain view—776 of them if I counted correctly. The terms are words and word combinations that scripters probably use in Google, Yahoo, and other search engines to find the kind of solution that the product offers. View the blog posting, if you like.
One of the terms in the giant list is my name. I've been associated with the technology since its inception, and currently have three books on the subject in print. But since I have no connection with the product and do not mention it or describe it in any of my writings, it would be grossly unfair and misleading for the product blog page to show up in a search that included my name.
I posted a comment asking to have my name removed from the list. I didn't know it when I wrote the post, but that blog doesn't use the "nofollow" link technique, so I may benefit a smidge by having this page link to my dannyg.com Web site. That wasn't my goal. I'd much rather the Web be populated with links to this Spam Wars site to build its traffic, but that would have been very off-topic to the posting.
(An entire industry has evolved to 'game' the search engine system. I'm probably in the minority because I refuse to play those games.)
The type of keyword abuse perpetrated by the blogger described here is the stuff that bloggers blog about. Bloggers blogging about bloggers and blogs seems to be rather popular in the blogosphere.
Posted on March 14, 2005 at 09:40 AMMarch 13, 2005
Going For the Ripoff Record?
Spamdom is flooded with offers for so-called OEM software. Translation: Pirated software at prices that are, indeed, too good to be true. Forget about getting support or an upgrade to the next version. A lot of the sites also don't deliver the software, but are interested only in your credit card data.
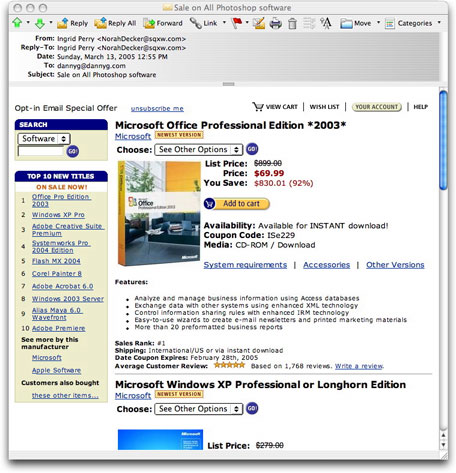
There's one guy who goes to a little more trouble than most in the hopes of fooling recipients into thinking the offer is legitimate. His HTML email message imitates the amazon.com Web page format, right down to stealing the images directly from amazon's site (the image source URLs are from amazon). The only thing missing is any displayed textual reference to "amazon.com" in the email message, presumably as a defense against whatever amazon's lawyers might wish to pursue.
After making sure that there were no Web bugs or other nastiness in the message source code, I viewed the message in my email reader. Here's how it looks:
(You can also view the full-size 218KB image in a separate window.)
The first item up for sale on "The Price is Not Right" is Microsoft Office Professional 2003. If you compare the phony lookalike offer to the real amazon offer, you'll find plenty of ripped-off text and art. All of the product and purchase related links, however, go to the OEM scammer's Web site.
Notice how the "OEM" retail price is $899.99, while amazon's retail price is $499.99. Makes the OEM savings percentage look real good when you artificially inflate the retail price. Imagine how the OEM version gets a 5-star review (from 1,768 reviews) while amazon's authentic version gets only 3.5 stars (from 27 reviews). Oh, and scammy forgot to change the Date Coupon Expires date.
I get a huge kick out of the next offering in the email: "Microsoft Windows XP Professional or Longhorn Edition." Scammy's site is hosted in China, where one can reportedly get DVDs of movies even before the films are released anywhere in theaters. Does that work for software, too?
I'll let Microsoft, Adobe, Symantec, and other publishers whose products are being pirated fend for themselves. They don't need my help. The same goes for amazon. What peeves me, though, is the deception perpetrated on recipients of these messages. If recipients associate the look and feel of the message with amazon.com—I mean there are thousands of Web pages that offer products through legitimate amazon affiliate connections—buyers might expect the same level of customer service and communication they receive from amazon—and be severely disappointed.
Just because an offer looks slick doesn't make it any more legitimate than the text-only version. It just means that the scammer knows something about HTML. Whoop-de-freakin'-do.
Posted on March 13, 2005 at 03:11 PMMarch 12, 2005
Mr. [Random Name] has $[Random Amount] For Me!
Most mortgage lead spammers want you to believe that you're hearing directly from a lender. In truth, all the spammers do is gather your contact info and sell it (for big bucks) to the actual mortgage brokers and lenders. Lenders wouldn't dream of getting their hands dirty with prospecting directly for new customers.
Anyway, if I were to believe the pitches (I obviously don't), today's collection of suspects have a bunch of similar messages following the same formula. These things have been coming in for weeks, but there is an impressive array in this batch. Look at the range of subjects:
- Mr. Figueroa has $040,664 for you
- Mr. Duvall has $945,537 for you
- Mr. King has $099,050 for your family
- Mr. Waller has $299,261 waiting for you
- Mr. Chambers has $479,396 waiting for you
- Mr. Dempsey has $332,922 for your family
One guy thinks I'm only good for 40 grand, while another will supposedly take me to nearly a mill.
To my mortgage lead spammer friends:
Mr. Goodman has $000,000 for you.
Posted on March 12, 2005 at 10:11 PM
Even when doing a quick scan of spam suspects, some words stick out like sore thumbs. And when the spew machine uses combinations of random words in the Subject lines, those words may appear out of nowhere.
Such was the case in a message I spotted from a medz spammer whose two-word subject included (I kid you not) the "n" word. Checking the header of the message, the entry point to the Internet appears to be a cable subscriber in the U.K. (the Newport area, I believe).
It's impossible to know if more than just the one message I saw had that word combination in it (there were no other reported sightings I could find). But I wonder if such a message had gotten into a litigious inbox, whether the zombie PC's owners or ISP could get into hot water, even if they were unaware of the material spewing from the out-of-control PC.
Wide awareness among non-techies that such abuse exists might be enough to get them to care enough to clean up their PCs. Getting the word out is the hardest part.
Posted on March 12, 2005 at 09:52 PM
Plenty of spam messages make you scratch your head when you try to figure out why on Earth you're receiving an advertisement for something that you wouldn't have an interest in over the next million years. It proves my belief that spamming is virtually the antithesis of direct mail marketing, where it's too expensive (printing, postage, list rental, etc.) to send mailings to the wrong people campaign after campaign. A lot of spammers seem to believe that the more messages sent, the merrier. A successfully targeted email piece is one that gets past spam filters, regardless of the demographics of the recipient.
Just when you've thought you've seen everything, in comes a message selling a drivers license guide for the United Arab Emirates. That's right. It's a beginner's manual that supposedly teaches me how to obtain a driving license for use within the U.A.E.
The spamvertised domain is registered in the U.A.E., and has been in existence for three years. Although I didn't visit the Web site, it's quite possibly a legitimate business that has hired an "email marketing service" to help spread the word. The message contains several less obvious pointers to a domain whose name contains "emarketing" in it (with a suspicious domain registration record, to boot).
Here's my guess as to what's going on. The driving school hired this "emarketing" outfit to do some targeted email advertising on the school's behalf. The school may have even received a spam message pitching the service. Who knows? "Emarketers" flaunt targeted emailing campaigns, but if my inbox is any measure, their targets are on the scale of a broad side of a barn at close range. I can't imagine how my email address (presumably harvested from my other domain and/or circulating in spammers' databases) could be associated with a desire to get a drivers license in the Mideast. I don't think my blind cat would be a candidate, either. And (pardon the pun) making a blind mailing to the world about such a specialized product would seem an exceptional waste of time and money (even on spam terms).
For a brief moment, I actually have a tiny sliver of compassion for the driving school, because it may have been a spam victim on the other side of the equation. But the fact that it failed to perform due diligence on the "emarketer" it may have hired puts it right back into the spamvertiser column in my ledger book.
Posted on March 12, 2005 at 09:20 PMMarch 10, 2005
A Spammer Lies...Oh My!
Here is a good example of how a spammer hopes to trick the unwary recipient into visiting his spamvertised Web site. The Subject: line reads something like:
Subject: Inquiry Response
The aim, I believe, is to make the recipient believe that this message is in reply to some inquiry that the recipient made. The From: field, however, contains just an email address at a non-descript domain (in fact, it's not even registered as I write this).
Curiosity (which, as Colonel Potter once noted, "KO'd the feline") leads the recipient to check the message (in a safe way, I hope). It's a short message, beginning:
Thank you for visiting our website.
And then a spiel about how great the shopping experience is at the site, with a URL to get you there. If you take the spammer at his word (a huge mistake), you may wonder if you actually visited the site previously, and click on the link.
By that point, the score is
Spammer: 3 You: 0
The spammer scored three points by
- Getting the message into your inbox
- Getting you to open the message
- Getting you to visit the spamvertised site
If the mailer is paid by the visit, you've just put some change in the spammer's pocket so he'll know to keep doing it to earn some more. But even an unpaid Web site hit (as recorded by the spamvertised Web site's server) gives the spamvertiser hope that the spam is working by driving traffic to his site.
What's worse, since you don't know who this guy is or what's at the other end of that link, you might alternatively find your computer open to all kinds of nastiness (spyware installations, in particular). Upon visiting that site with an unprotected and unupdated PC, your final score may be -10. Or -100 if the spyware gets your user IDs and passwords to various accounts.
Let's not reward the liars. ZERO RESPONSE 'em.
Posted on March 10, 2005 at 01:50 PMMarch 09, 2005
How to Win Friends...
Here is how one medz spammer hopes to win the affection and business of potential customers:
Subject: Hey baldy !
The message doesn't promote hair restoration medications, but maybe his Web site does. I'll never know.
Posted on March 09, 2005 at 07:29 AMMarch 07, 2005
A New Worm on the Phisher's Hook
I don't read every phishing message that comes through here, but I noticed one today that is taking a new (for me) tack on the social engineering tricks used to convince bank customers to yield their personal identity info.
This one claims to come from Washington Mutual (the big wamu, again!) and wishes to thank me for being a loyal customer. Rather than terrorizing me about suspended accounts and attempted fraud, the lure here is all warm and fuzzy:
We offer you special discounts in all stores all over USA with your credit card and a special cupon offered free by our bank.This offer includes over 15000 shops located all over the country.
This is our Spring gift for our clients so don't miss this special occasion
All you have to do is to confirm your name and subscribe for your account and in 72 hours you will have your cupon. Click below for our special offer.
OK, some of the spelling is a little fuzzy, too, but that's not the point. The attraction here are words like "discount" and "free"—potentially dangerous words that Spam Wars readers know something about. I'll bet these guys snag more victims with this honey than with fear.
The actual link behind the wamu-looking link in the message is a numeric IP address, and the form at the destination site asks for the same stuff that all phishing forms do. It's probably the same form the phisher uses for his more threatening come-ons.
Unfortunately it has come to this: Unless you're willing to look behind messages claiming to be from someone holding your private information, you simply can't trust the message—especially when they ask you to supply information they should already have on file. EBay had to institute its own messaging system to try to put trust back into its communications with customers (alas, customers still succumb to phishing emails).
Financial institutions want you to do more things online (it saves them labor costs); yet it's increasingly more difficult to trust email communications from those institutions. Customers' brains should start exploding at any moment.
Posted on March 07, 2005 at 04:39 PM
There's an informative Consumer Reports article that reports the results of tracking various investment advisories that come either as newsletters or spam. There is great advice there, especially this tidbit:
Our advice: Whenever newsletter mailings have disclosure boxes saying the content includes paid promotions of company stock, toss them immediately. (Also toss any unsolicited stock-touting newsletters or e-mails.)
Most of the stock tip spams I've seen over the years are not only unsolicited, but also unidentified. The return address is bogus and there is no pointer to any Web site. And yet most of them feel compelled to include disclaimers. Thus, the following disclaimer on today's stock tip spam was particularly amusing:
This Profile is not in any way affiliated with the featured company. We were compensated 3000 dollars to distribute this report. This report is for entertainment and advertising purposes only and should not be used as investment advice.
Now there is some good advice.
Posted on March 07, 2005 at 08:23 AMMarch 05, 2005
Phishers Getting Stupider By the Minute?
It appears that what I suspect as being "phishing kits" put in the hands of wannabe crooks don't come with very good directions. In the gazillionth Washington Mutual phishing message I've seen, the sender neglected to adjust the deadline date by which the recipient is supposed to hand over his or her identity to the crooks, or risk indefinite suspension of the bank account. The date in this message isn't wrong by just a few days. No, the deadline was Christmas of 2004, probably the default date in the template.
I mean, c'mon. The date appears in bold, and sticks out quite clearly in the message. That is, if the crook had bothered to preview the message in an HTML viewer or Web browser.
And, no, I am not offering my services to write Phishing for Dummies, despite what seems to be a sizable market.
Posted on March 05, 2005 at 09:55 PM
I wish to correct one part of the technical description about how email works in Chapter 4. The first paragraph of page 37 incorrectly states that your email program downloads mail from the server in one swoop. While it may appear to be the case to the user, in truth, the most common email system described in this section (POP) transfers email messages to the email software on your PC one at a time, as the result of a "conversation" between your PC and the POP server. After the server authenticates your email program's connection request as being legit (e.g., through password verification), the typical "conversation" goes like this (translated into English):
- Your Email Software (Client): Got any mail for me?
- Server Software (Server): Yes, 2 messages.
- Client: Send me the first message.
- Server: OK. Here's how big it is, and here comes the message (followed by entire message content and an end marker).
- Client: Delete the first message on the server.
- Server: First message is marked for deletion.
- Client: Send me the second message.
- Server: OK. Here's how big it is, and here comes the message (followed by entire message content and an end marker).
- Client: Delete the second message on the server.
- Server: Second message is marked for deleteion.
- Client: I'm done. See ya!
- Server: Over and out.
With the successful close of the transaction between client and server, the server deletes from its email file those messages marked for deletion. The system is designed to prevent deletion of email on the server in the event of disruption during transfer of individual messages.
Posted on March 05, 2005 at 08:02 PM
The guy mailing this phishing message is in such a hurry to scam Charter One Bank customers of their identities, that he forgot to change his mailing template thoroughly. Here's the From: field:
From: "Charter One Bank" <aw-confirm@ebay.com>
The Reply-To: field of the message header points to the same eBay address.
A spelling checker wouldn't hurt, either, as indicated by this line:
Subject: Reactive Your Registeration
I won't bore you with even more horrendous language that tries to scare me about suspicious account activity "which resulted in your account temporary suspension."
The phishing pros must cringe when they see rookies exposing the scam for what it is. He he he.
Posted on March 05, 2005 at 06:50 PMMarch 04, 2005
Click...Boom!
If you've ever wondered why the Internet is cluttered with over a million zombie PCs, here's a lesson for you and your mother.
One of today's spam suspects had the Subject: line "Complete your registration!" and the From: field said "BestHyip Forum." In my quick scan of this info, I didn't associate "Hyip" with its well-worn acronym for "high-yield investment program"—frequently associated with the schemes that guarantee a 1000% return on your money before breakfast.
I did see the "forum" part, and thought at first that this message might be a confirmation message for a legitimate online forum. Indeed, checking the body of the message in the source code, I found the typical confirmed opt-in message ("Thank you for registering blah blah. Before we can activate your account blah blah."). Although I know I hadn't signed up for this forum, I figured the forum registration software got a spam or virus message with my email address forged in the From: field. While I don't like getting automated responses to stuff I didn't send, I'd sooner receive a confirmed opt-in blockade message than having my address blindly registered to some crap I don't want to get. At least if I ignore a confirmed opt-in confirmation (which requires me to click on a coded URL to confirm my registration), that will be the end of it.
But a few things got my nose twitching about this message as I started safely looking at its source code (Spam Wars readers know how to do this). In particular:
- The return address associated with the "BestHyip Forum" in the From: field was a gibberish user name at yahoo.com, while the forum appeared to have its own domain (i.e., this was not a Yahoo Group).
- The message entered the Internet email system from a server in Japan, while the forum's domain is both hosted and registered (plus or minus bogus domain registration) in Texas.
- If I had been viewing the message in the regular email view, I would not have seen that the forum's link URL was disguising the true destination to a numeric IP address. That IP address was not the same as the forum's, and was hosted in a different state.
In my experience, the vast majority of spam links pointing to numeric IP addresses lead to one of three types of places:
- Outright scam sites
- Virus propagation sites
- Pornography sites
What stuck out to my eye was that the plain-view URL invoked the "hyip" moniker, which has its share of scaminess associated with it. Whoever was behind this, was hiding behind something that a good number of recipients might already consider shady. How bad could this Bad Guy be?
A little safe snooping revealed the answer.
Anyone who clicks on the link is first delivered to a nearly blank page, which, before redirecting the clicker to yet another site, installs a rather dangerous payload into Windows PCs that ultimately allows control of the PC to be handed over to others. The particular vulnerability being exploited is one that definitely affects Windows XP prior to SP2 and perhaps even those with SP2 installed (using Internet Explorer).
Visitors get no warnings about the installation. The first one is quick, but it opens the door for the machine to have additional software installed (e.g., key loggers that capture keystrokes while you're connected to secure sites such as your bank). Your email address book may be ripped off (and your friends will get lots of spam or similar lures to these types of sites). Your PC may end up spamming the world.
Tons of these kinds of messages flood inboxes around the world each day. Unsuspecting recipients who click on the links don't know what they're getting their computers and their identities into. The tactic is called a "drive-by," but in this case, it's the victim who does the driving...straight into the line of fire. In January, I reported on a similar, consumer oriented trick I saw.
Today's message is, in a way, more efficient in finding its victims. Most people clicking on the link for the message I describe here would know what the "hyip" acronym means because they want to join a forum on the subject. In my searches around the Web, I see a lot of associations between "hyip" and what are called e-gold accounts. Someone clicking the link in this message is someone who probably has a higher-than-most likelihood of logging into one or more online accounts involving monetary transactions and/or investments. Wowie...what a PC on which to get a keylogger installed!
All I can say is that clicking on a link embedded in any unsolicited message is one of the riskiest actions any Internet user can make. Updated OS, antivirus, and antispyware software might reduce your exposure, but it's no guarantee you won't be hit with something that was released to the Net just today.
Didn't your mother warn you against accepting candy or rides from strangers? Today she should also warn you about clicking on links from unknown sources. Or maybe you should warn her. Today. Right now.
Posted on March 04, 2005 at 01:01 AMMarch 02, 2005
How to Scare Phisherees...Not!
In their attempts to get potential phishing victims to click on the bogus links in their messages, phishers are getting increasingly strident in the presumed consequences of ignoring their messages. But for Pete's sake, it's hard to take anyone seriously when the warning (as in this Western Mutual phish) reads like the following:
If you choose to ignore our request, you leave us no choise but to temporaly suspend your account.
And they split an infinitive, to boot! If regular law enforcement can't stop these guys, maybe the Spelling or Grammar Police can.
Posted on March 02, 2005 at 03:19 PM
One of the major spammer tricks that the U.S. CAN-SPAM law aims to eliminate is the deceptive Subject: line that lures unsuspecting recipients to open the message. It's the primary tactic that a spammer (and scammer and virus writer) uses to achieve the second of his three dearest wishes (itemized on page 134 of Spam Wars).
The more spam and other garbage that an email user has received over time, the more suspicious that user typically is. Being burned by the deception hundreds or thousands of times over the years makes one (I hope) more likely to smell a rat.
When scanning through my list of unread incoming mail, I focus first on the column that shows the From: field information of those messages. When I encounter a sender I don't recognize, my suspicions ratchet up a notch, and I next look at the Subject: column for that message. (Even a message "from" a sender you recognize is not always safe, as I detail in the book.)
Interpreting a message by its Subject is a skill that you learn over time. When the liars are really out to get you, their Subject: lines can raise enough doubt that you might be drawn to open the message.
Here's one I saw this morning. The From: column reads "Kimberly L," a name I did not recognize. The Subject: column reads "March Water Bill." The sender in this case wants me to think that Kimberly works for the local water utility, and that this message has something to do with billing.
This is precisely the juncture at which you need to exercise those "little grey cells" to think this through. The likelihood of my local water utility having my email address is extremely remote. While it's true that they could conceivably use a service (called email appending) that tries to correlate physical and email addresses, it's not foolproof, and they would have no way of knowing without further confirmation that they had the right email address for one of their customers. Further, experience tells me that the more ominous (or strident) a message sounds (like the eBay phishers who warn about impending account closure), the more suspicious I become.
The (non-Spam-Wars-reading) email user who doesn't get a lot of spam or is an email newbie would likely be fooled by this message's deception. To the unwary eye, it looks like a notification from the water company. But this is precisely the email user who needs to learn what kinds of deceptions are being used and how to inspect the message safely before opening (for ham) or deleting (for spam) the message.
As for "Kimberly," she's a medz spammer. Surprise, surprise (yawn).
Posted on March 02, 2005 at 09:32 AM