| Home | The Book | Training | Events | Tools | Stats |
October 17, 2011
You Did NOT Win a FREE $1000 Apple iPad 2!
It starts with this spam email message:
Subject: You've Won A FREE $1000 Apple iPad 2!
Congratulations, you've been specially chosen based on the selection of your email address: dannyg@dannyg.com , as the winner of a brand new Free $1000 Apple iPad 2! To claim yours, just click on the link below:
Claim Your Apple iPad 2
Your new Apple iPad 2 gives you the best of all worlds: performance, total portability, and an innovative, rich feature-set including a 64GB Flash drive, LED lighting, a Dual-core A5 chip for twice the processing speed and super fast graphics - all in a design that's 33% sleeker and 15% lighter. No contract required. Keep it for yourself, or use it as a great gift for someone special.
Your iPad 2 is being held for you for a limited time, so please claim yours today:
Free Apple iPad 2
All the best,
Ellie Michaels
Awards Dept
Let me count the ways that this message fails CAN-SPAM compliance:
- Forged header.
- The From: field uses my email address as the displayed text, with a bogus microsoft.com address as the actual address for replies.
- The topmost Received: header field forges the sending domain as something from China, while my email server's reverse MX record shows the message having originated from an sbcglobal.net IP address.
- The Message-Id: header field identifies itself as originating from my domain.
- No identity of the sending organization.
- No opt-out provision
Oh, yeah, and the message body is a complete lie. There is no iPad sitting somewhere with your name on it. There also isn't such a thing as a $1000 iPad 2. The Apple Store lists the most tricked-out model at $829.00.
I believe this message is a lure to the type of marketing scam that has been around for ages. The attraction is a free [fill-in-the-latest-cool-gizmo]. Before you'll ever get a chance to see the item, you'll have to jump through costly hoops, endless surveys, and eventually give up your address book (or Twitter/Facebook followers) to the spammer. Your friends' email addresses will be thrown into the worldwide spam recipient database. As you slog your way over countless hurdles, the promoter is making dough through your surveys (he gets paid for each one filled out), sales of sample products, and so on. He's counting on you to give up before he has to fulfill sending you your "free" gift.
That this spammer does not even try to be CAN-SPAM compliant leads me to believe you'll never see anything, no matter how hard you work toward your goal.
The spammer wins.
You lose.
What else is new?
Posted on October 17, 2011 at 10:51 AMOctober 14, 2011
Confused Malware Lure
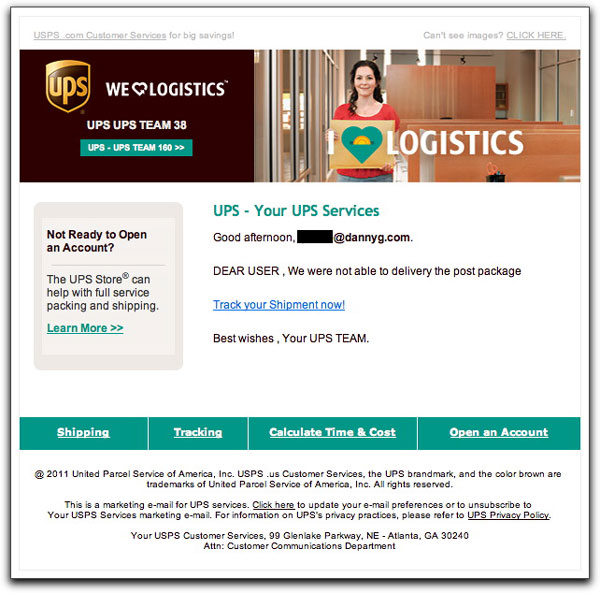
I suppose some folks confuse the United States Postal Service (USPS) with United Parcel Service (UPS), at least by name. The two organizations have created very different visual presentations for their logos and other material. The USPS wraps itself in the good ol' red/white/blue color scheme, while UPS is the Brown company. The two companies' marketing messages are very distinct.
A presumably non-US malware distributor hasn't yet grokked the distinctions. Today he sent a message:
Subject:United Postal Service Tracking Nr. H4222259476
WTF is the United Postal Service?
Now look at how a phony email message body uses lots of UPS images, while some of the fine print refers to the USPS:
There are so many other inconsistencies in this email (not to mention the major grammar booboo when they couldn't "delivery" the package) that it's really quite a mess. And having the From: address be an aol.com account doesn't help their believability case.
I was naturally curious about the link. Was it going to be to a medz site or a malware distribution point? Lo and behold, it goes to yet another of the main.php destinations I've been seeing. Although the domain was freshly minted a couple of days ago, it had not yet been shut down like the others (c'mon, registrar GoDaddy!). It did, however, give me a chance to find out what the main.php destinations are trying to serve up.
The source for the page returned by the main.php program consists of just one script tag with obfuscated JavaScript. When decoded (which, to the regular user would happen upon landing on the page), the script checks to see which potential vulnerabilities are available in the user's browser. Although some of the vulnerabilities are Old School ones, the script does perform a check for the fairly recent Chrome browser. Presumably, the attempts to load a variety of objects into the page are to alert the Bad Guy about which exploits will likely succeed with this user's PC.
I wouldn't want to go near that page intentionally with a browser, even if I had antivirus software installed.
Perhaps these guys think they're so smart with their double-obfuscated JavaScript. But with the simple stuff in the email presentation, they're dumb, dumb, dumb.
Posted on October 14, 2011 at 11:33 AMOctober 10, 2011
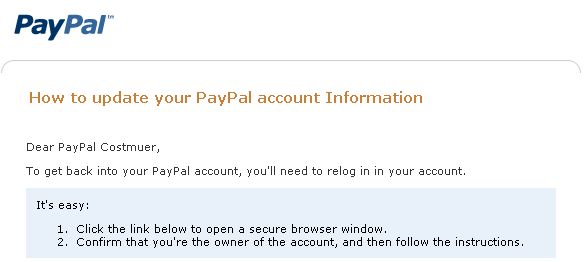
Dear PayPal Costmuer
An image from a PayPal phishing message:
Pathetic.
Posted on October 10, 2011 at 07:50 PM
So many Nigerian princes, so many European lotteries...you just never know how much these advance-fee (419) goons are going to scam out of you while you chase a pot of gold at the end of an endless rainbow. At least this Bank of America senior personal banker — who also happens to be a reverend, so he must be legit — tells you right up front the minimum you'll be paying out of your pocket (it's long, so grab a cookie now):
From: Bank of America
Subject: BANK OF AMERICA CORPORATE CENTER WITH THE transaction CODE EA2948-910.
From: BANK OF AMERICA CORPORATE CENTER
Anti-Terrorist and Monetary Crimes Division
FBI Headquarters in Washington, D.C.
Federal Bureau of Investigation
J. Edgar Hoover Building
Washington, D.C. 20535-0001
Attn: Beneficiary.This is to Officially inform you that it has come to our notice and we have thoroughly completed an Investigation with the help of our Intelligence Monitoring Network System that you legally won the sum of $800,000.00 USD from the Bank of America Online Balloting System, which was held at the Bank of America Corporate Center in Charlotte, NC. During our investigation we discovered that your e-mail was one of the 8 Lucky Addresses in this New Year Balloting Program that won the money. Your Winnings have been deposited at the Bank of America (Bank Address: 1375 N Citrus Ave, Covina, CA 91722) and the Bank have been authorized to pay you via a Certified Cashier's Check drawn from the Bank of America. I wish to congratulate you on your winnings; your email address was among those chosen during the Bank of America Online balloting from the new Java-based software that randomly selects email addresses from the web from which winners are sel ected.
Normally, it will take up to 4 business days for a Bank of America Check to be cleared, cashed and remitted into your account by another local bank. We have successfully notified the banks on your behalf that funds are to be drawn from our registered bank (Bank of America) so as to enable you cash the check instantly without any delay, henceforth the stated amount of $800,000.00 USD has been deposited with our bank, Bank Of America in COVINA, CALIFORNIA.
We have completed this investigation and you are hereby approved to receive the certified cashier's check into your personal account as we have verified the entire transaction to be Safe and 100% risk free, due to the fact that the funds is with Bank Of America you will be required to settle the following bills directly to the Bank of America Agent in-charge of this transaction whom is located in Covina, California, United States of America. According to the directives, you are required to pay for the following -
(1) Deposit Fee's (Fee's paid to setup a new account for the beneficiary by the Bank of America)
(2) Courier Delivery Fee (Fee paid to deliver the check through dhl delivery to your designated address)
(3) Insurance Fee (This is the fee paid by bank to insure the check before been deposited at the bank to avoid any deduction)The total amount for everything is $750.00 (Seven Hundred and Fifty-US Dollars). We have tried our possible best to indicate that this $750.00 should be deducted from your winning prize but we found out that the funds have already been insured and deposited at Bank Of America, Centralia, Washington and cannot be accessed by
anyone apart from you the beneficiary, therefore you will be required to pay the required fee's to the Agent in-charge of this transaction via Western Union Money Transfer Or Money Gram.In order to proceed with this transaction, you will be required to contact the agent in-charge (REV BROWN SMITH) via e-mail.
Kindly look below to find appropriate contact information:
Contact Agent Name: REV BROWN SMITH (Senior Personal Banker)
E-mail Address: [removed]@live.com
Bank of America: 1375 N Citrus Ave, Covina, CA 91722.You will also be required to e-mail him with the following information:
FULL NAME:
ADDRESS:
CITY:
STATE:
ZIP CODE:
DIRECT CONTACT NUMBER:
OCCUPATION:
ANY FORM OF IDENTITY:You will also be required to request Western Union details on how to send the required $750.00 in order to immediately deliver your Funds of $800,000.00 USD via Certified Cashier's Check drawn from Bank Of America, also include the following transaction code in order for him to immediately identify this transaction : EA2948-910.
This letter will serve as proof that the Federal Bureau Of Investigation is authorizing you to pay the required $750.00 ONLY to Rev Brown Smith via information in which he shall send to you, if you do not receive your winning prize of $800,000.00 we shall be held responsible for the loss and this shall invite a penalty of $8,000 which will be made PAYABLE ONLY to you (The Winner).
Due to the confidentiality of this matter, I decided to contact you privately to avoid imposters.
Please find below an authorized signature which has been signed by the FBI Director- Robert Mueller, also below is the FBI NSB (National Security).
ONCE AGAIN CONGRATULATIONS.
FBI Director
Robert Mueller.
Setting aside the preposterousness of the whole story (especially the part about bringing the FBI into the picture), I can guarantee you that anyone who forks over the $750 will be hit up for additional fees and taxes before the $800K is never sent. Once a 419er has a nibble, he or she will be relentless in draining funds from the gullible participant. If you want to save some time and achieve the same result with less anxiety and heartache, withdraw $750.00 in cash from your bank account and flush it down the nearest toilet.
By the way, Rev Brown Smith gets around quite a bit. According to a simple Google search, somehow he always manages to be near holdings of alleged big money. For years now.
Posted on October 10, 2011 at 11:25 AMOctober 07, 2011
Malware Links to main.php
Over the past few days, a persistent jerk has been trying to lure unsuspecting email users to visit what I believe to be malware delivery web pages. The social engineering tactics have ranged from the ACH transaction threat to fake iPhone pre-release info to today's invoice-related nonsense:
From: [a non-existent sales-related account at my domain]
Subject: Re: End of Aug. Statement Required
Good day,
as reqeusted I give you inovices issued to you per sept.
Download Invoice
Regards
KITTIE MEANS
One point that all of these attempts have in common is that the URLs lead to a main.php destination at a variety of domains. That makes them easy to spot with a hover of the cursor before clicking.
Another point that pleases me even more is that the freshly-minted domains employed for these attacks have been suspended very quickly. Somebody is watching this ass very closely. How long will it take for him to give up?
Posted on October 07, 2011 at 11:03 AMOctober 05, 2011
Malware Delivery Trick du Jour [Updated]
Any communication from the taxman — other than a refund check — generates fear in most people. And if the following winds up in your email inbox, a bit of adrenalin must surely seep into your system:
From: Internal Revenue Service
Subject: Internal Revenue Service
Notice,
There are arrears reckoned on your account over a period of 2010-2011 year.
You will find all calculations according to your financial debt, enclosed.Yours sincerely,
Internal Revenue Service.
The language of the message is odd, and certainly not American English, but I suspect plenty of recipients will glide past that to reach for the attached file named Calculations_IN15161.zip (your number will probably vary as the randomizer in the spam sending system fills in a different value). It's a backdoor Trojan loader, of course, so you don't want to mess with it at all. If you run the embedded .exe file, you might wish to trade your infected PC for a real IRS problem to reduce the headaches.
Update (13 Oct 2011): According to correspondent Vicki, this campaign is being customized for Australian email addresses by referencing the Australian Tax Office (ATO) — just to give it that homey touch. These messages, like more recent ones I've seen here for the IRS, have additional wording warning the recipient to act to clear the debt (usually with some bizarre verbiage) and threats of court action. They really want you to open that attachment so they can grab your PC.
Posted on October 05, 2011 at 10:10 AMOctober 03, 2011
More iPhony Tricks
We've had the fake Apple announcement earlier this morning. And now comes an email that promises some kind of iPhone-related download:
Subject: You have been sent a file (Filename: Iphone-5298.pdf)
Sendspace File Delivery Notification:
You've got a file called Iphone-52162.pdf, (719.8 KB) waiting to be downloaded at sendspace.(It was sent by Shaniya ESCOBAR).You can use the following link to retrieve your file:
Download Link
The file may be available for a limited time only.
Thank you,
sendspace - The best free file sharing service.
----------------------------------------------------------------------Please do not reply to this email. This auto-mailbox is not monitored and you will not receive a response.
Both links in the original email do not lead to sendspace, but rather to a web site whose domain was registered waaaay back last night. The domain has since been suspended, but I doubt that will stop the crook from signing up another.
Since the domain has been suspended, I can't say for sure that the page delivered malware. It could instead be an affiliate redirector to a medz site. In either case, it's worth noting that any email originating from, or claiming to be from, someone you don't know needs to be handled like a powder-filled envelope.
And if you think some unknown person is passing you secret iPhone pre-release poop, you are deluding yourself.
Posted on October 03, 2011 at 10:56 AM
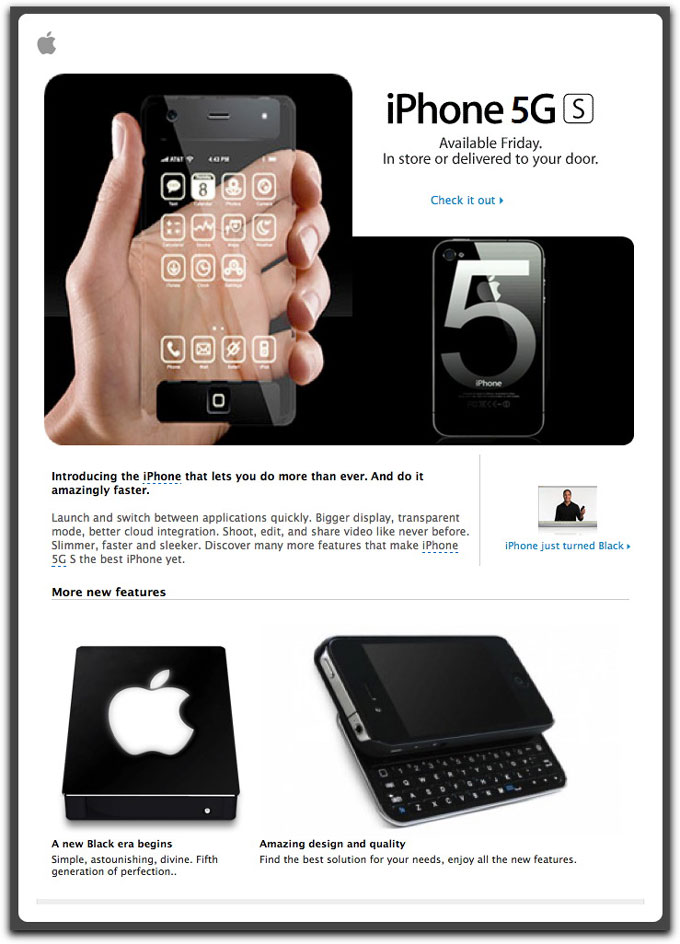
Malware delivery assholes are using the impending announcement of Apple's latest iPhone(s) to trick unsuspecting users into downloading and installing bad stuff onto their PCs. The following image is from an email whose subject is: iPhone 5G S has been released:
Except for the overlaid "5", the images are resurrected from tricksters who pulled similar Photoshop tricks ahead of earlier iPhone releases. I'm not really sure what the lower left image is supposed to be, and the caption (including the laughable misspelling) offers no clue.
The two links ("Check it out" and "iPhone just turned Black") are to download a .exe file (iPhone5GS.gif.exe) from a hijacked web site. This is obviously targeting Windows users, but a smart(er) malware crook could attempt to exploit recent vulnerabilities putting some Mac OS X users at risk.
It may be hard for iPhone fanatics to resist, but resist you must.
Posted on October 03, 2011 at 09:10 AM