| Home | The Book | Training | Events | Tools | Stats |
March 27, 2010
Facebook Malware Lure du Jour
Simple, and guaranteed to be downloaded/installed by plenty of unsuspecting Windows and Facebook users:
From: Facebook <noreply@facebook.com>
Subject: F is for fun!
Hi there.You got a funny picture from your Facebook friends.
To see it, click here .
Please do not reply to this email.
Enjoy it.
The link downloads a file named facebook.gif.exe, which shows about 48% coverage in VirusTotal exams as a backdoor Trojan.
That's not all that "F" is for.
Posted on March 27, 2010 at 03:03 PMMarch 25, 2010
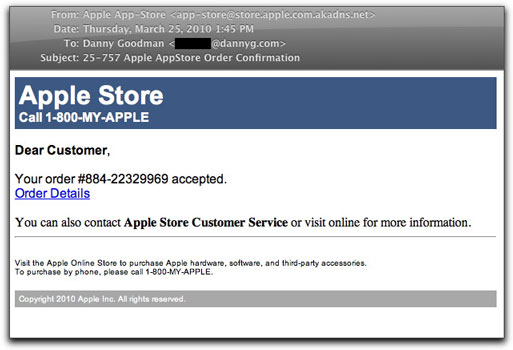
Phony Apple AppStore Order Confirmation
Some spam is more preposterous than others, yet it can often require a second look to see how bizarre a message is.
When I first saw this Subject: line in my inbox:
Subject: 25-757 Apple AppStore Order Confirmation
I didn't see the word "AppStore". Instead I figured it was some Apple Store lure to install malware or phish for my Apple ID credentials. Even though I'm an iPhone developer with apps in the real App Store, my eyes skipped over the critical word. Part of that may have come from my knowledge of the real communications that the App Store conveys to real customers: receipts for downloads. All purchases from the App Store are immediate, so there is no such thing as an order confirmation. Even the Apple Store doesn't send a "confirmation" per se. Instead, they send an "Order Acknowledgment".
Here's what the email message looked like:
If you click the link in the message, you visit a web site from Russia whose page has both an obvious link (with just the word "Click") and a hidden iframe element. The obvious link takes you to a medz vendor. Ugh. But the hidden stuff...well, I'm not exactly sure at this point. The hidden material uses the same type of JavaScript obfuscation techniques to insert additional iframes and scripts that malware distributors have been using for years. In this message, the scripts (albeit flawed in places) eventually attempt to load a page that is no longer available. Perhaps all this hidden stuff is a decoy for malware researchers to follow. I can't say for sure.
The association between medz spammers and malware distributors has been shown to be close in the past. The malware can be used to harvest new email addresses that the Bad Guy can use to spam for medz, knockoff goods, and online "dating" sites. Whoever is behind this stuff is equally happy to sell medz and install malware — it all makes money either way.
Posted on March 25, 2010 at 11:30 PMMarch 11, 2010
Another Money Mule Recruitment Letter
Jobs, jobs, jobs! If you want to earn some fast cash by ripping off small businesses so that:
a) your criminal bosses in Eastern Europe collect big time; and
b) you may get caught owing a bank many thousands of dollars (somewhere just under $10,000) you already wired to Eastern Europe
then reply to the following spam message:
Subject: Job position REF47732
From: Shelly Dubois
Compliments
I am a manager of the HR department of a large multinational company. Our company is met in many departments, such as:
- real estate
- companies setting-up and winding-up
- bank accounts opening and maintenance
- logistics
- private undertaking services
- etc.We need employees in USA:
- salary 2.500 dollars + bonus
- 1 - 2 working hours per day
- free timetable
If you are interested in this job, please, send us your contact information: Shelly@[removed]-target.net
Full name:
Country:
E-mail:
Mobile phone-number:
Note! We are searching Americans only! >Please mention your name and write the phone number. Our manager will contact you to fix an interview.
And here's a variation that just came in:
Subject: Finance Manager vacansy for USA
From: Jim Woods
Compliments
I am the personnel department manager and I am appealing to you in the name of the large-scale and first-rate partnership. Our company takes an active part in the life of its subsidiaries, for example:
-property
- bank account operations
- transportation and logistics
- private enterprise service
- etc.We have vacancies to be filled by American residents only:
- salary 2.500 dollars + bonus
- underemployment
- flexible working schedule
If you would like to work with us, please provide us the following information: Jim@[removed]-target.net
First name:
Surname
Country of residence
Place of residence
E-mail box
Contact phone number
Attention! We need American residents only.>Please provide us with your Personal data (Phone number and First and Last name) and our manager will contact to you to make a brief interview.
The email address domain was registered a couple of days ago. No web site exists at that domain (at least at the default location), but the Apache server is alive (somewhere in Russia).
Unfortunately, a lot of Americans are under financial stress these days. Offers like these, despite sounding too good to be true, will yield plenty of applicants — lambs to slaughter.
March 08, 2010
419er Disease of Choice
A common ploy among advance-fee scammers is the attempt to rend the recipient's heart because the rich sender now has a terminal illness and wants to make sure his or her booty winds up in good hands — rather than in the hands of his or her greedy and untrustworthy family members. This is a triple scam because the dying person wants the recipient to use the funds to distribute among charities — really assuming that the recipient is supremely greedy, and plans to take the money and run once the sender kicks the bucket. In other words, the scammer is assuming his victims will try to scam the dead scammer. In the process, however, it is the email recipient who will be the only one scammed out of fake processing, storage, transfer, and other fees that ultimately never yield a penny.
The medical trend I've noticed in such 419 scam messages arriving here recently has been an enormous outbreak of esophageal cancer (often with the correct spelling of the fake diagnosis). That's a safe choice, unlike one Nigerian woman who claimed some years ago to be riddled with prostate cancer.
Posted on March 08, 2010 at 03:14 PMMarch 05, 2010
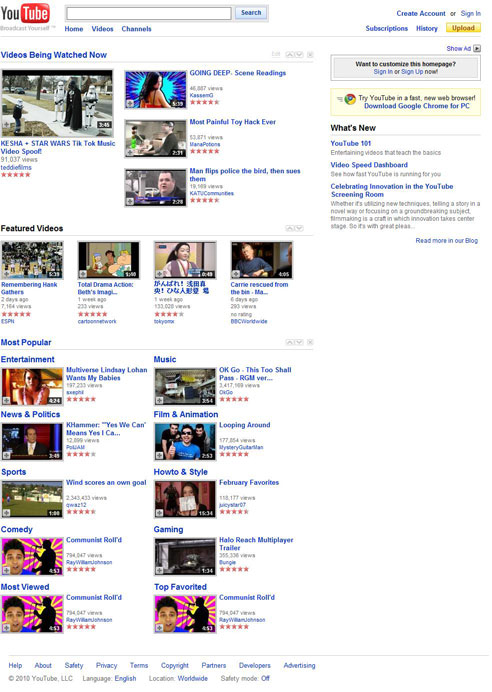
Phony YouTube Malware Lure
Look out folks, especially Windows users. A message claiming to originate from YouTube has an unwanted surprise.
The message Subject: line is:
Subject: YouTube Open the WORLD for you.
The body of the message consists of one publicly hosted image snapshot of a YouTube home page:
If you click anywhere on the image, you may download a malware file (.scr extension) from a hijacked web site.
Danger, Will Robinson!!
Posted on March 05, 2010 at 12:44 PM
I suppose there are plenty of takers for so-called downloadable or OEM software pitched by countless spam messages over the years. In the "old" days, it was just pirated software the buyer would get (if he or she got anything in return for $59). In more recent years, however, these warez sellers profit still further by embedding malware into the packages.
Thus, I got a laugh out of a spam message today that listed three easy steps to getting cheap software:
Subject: Windows7 much more stableHello, Dannyg
What does the "Downloadable Software" mean?Step 1 - Download soft archive and save it on your computer.
Step 2 - Extract archive.
Step 3 - Install it and use!Visit our Windows and MAC store
Dannyg, D33W-3459 your personal code to get 30% discount on all products.
You see, the seller left out one more item:
Step 4 - Hand over your computer and passwords to us without knowing it!
Posted on March 05, 2010 at 12:30 PM