| Home | The Book | Training | Events | Tools | Stats |
June 25, 2018
LinkedIn Phishing
I am a LinkedIn member at the free account level, but I don't use it much. Thus, when I saw the following message in my Inbox, for a half-instant I wondered if LinkedIn was planning to bounce me for inactivity:
Message LinkedIn YOUR ACCOUNT WILL BE TERMINATED!!!
In the next half-instant, I immediately figured the message was some kind of trick. Unless you start doing something illegal or rant with the "n" word, it's awfully hard to get an account terminated at social media sites. Even after you die or are abducted by aliens.
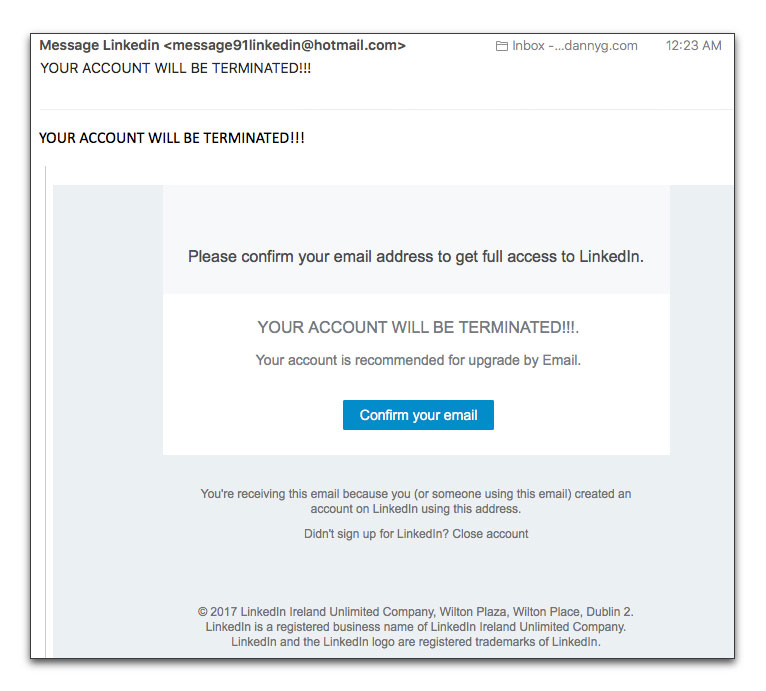
Here is the message in full:
Although the text is decent English with good spelling, there are plenty of other signals that this message is bogus. Can you spot them all?
- The From: address is a hotmail.com account, not linkedin.com
- The text promises "full access" to LinkedIn as well as something about an upgrade via email. LinkedIn has multiple tiers, but anything other than the basic service is a paid, premium service. They don't give that stuff away.
- You wouldn't know it about this particular message, but it was addressed to me at an email account I don't use for my LinkedIn account.
- The message is copyrighted 2017, rather than the current year.
- This message claims to come from LinkedIn Ireland. Now, the main company is based in Sunnyvale, CA and is owned by Microsoft. They may have an Irish branch, but why would that branch be concerned by my account?
- Rolling the cursor atop the "Confirm your email" button reveals a link to a subdomain at a free web hosting service.
- There is no LinkedIn logo art anywhere in the message. Highly unusual for any business communication from an online business.
For such a short message, this phishing email stinks quite heavily. If you're sloppy in reusing passwords, think about how giving up your corporate email address and password can be. A crook could literally log into your company's system under your userID (probably the same as your email address before the @ sign), at which point a knowledgeable cracker could burrow deep inside the system to steal secrets or disrupt operations.
That, my friends, is why we must all stay on our toes with respect to incoming messages of any kind on any service.
Posted on June 25, 2018 at 09:48 AMJune 18, 2018
Netflix Phishing
Another day, another phishing attempt.
This one is pretty run-of-the mill, but it attacks accounts held by lots of potential recipients. Unlike a phishing email I received yesterday targeting the comparatively tiny Bethpage Federal Credit Union, this Netflix attack would be much more likely to attract recipients in a massive scattershot mailing (which most phishing attempts are).
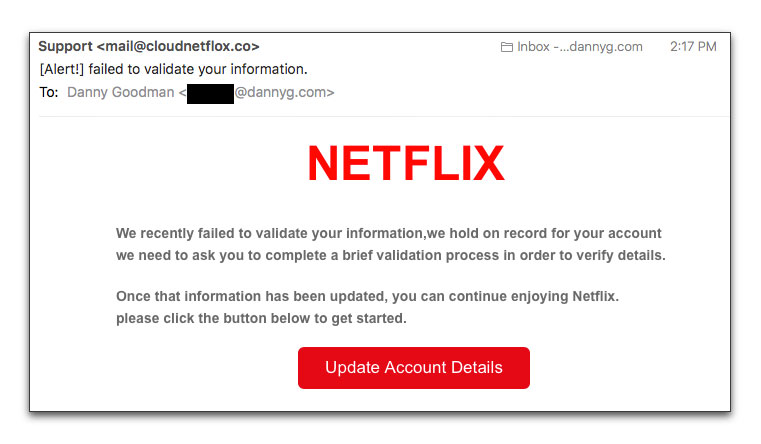
Here's the message:
Although the message doesn't look very Netflixy to my eye, it has just enough polish to fool plenty, despite a couple of grammar/punctuation problems. Two main giveaways to the smell of this one are: 1) the From: email address (netflox.co!); and 2) rolling over the Update Account Details button shows a link to a domain that doesn't look anything related to Netflix.
As always, if you have even a tinge of concern about your account, visit the site via a previously saved bookmark, and log in like you normally do (you may be automatically logged into Netflix of you visit frequently enough). If there is a genuine problem with your account, you'll learn about it then.
Posted on June 18, 2018 at 03:12 PMJune 11, 2018
Luno Wallet Phishing
I'm not a blockchain guy, so the email claiming to come from Luno Wallet asking me to verify my account was an immediate alarm to something sneaky. Here is the full text of the message:
From: Luno
Subject: Verify WalletWelcome to Luno
We have recently detected so many fraudulent SIGNUP on our website, we are hereby informing all Legit Luno users to immediately Validate their wallet by downloading attached Luno Validation form and verify your account is not a fraudulent Wallet.
Thank You
Team Luno
The attachment was an HTML file, whose source code let me see what they're up to without even having to load the page (always a risky thing to do without prior inspection). The core portion of the form included fields for your email address, your email account password (!), your Luno password, and your phone number. The destination of the form submission was to a domain created last month, but whose identity is privacy blocked.
Those four little fields contain a ton of personal information that should never be in the hands of crooks. Besides, no third party ever has the need for your email account password. Giving that up means others have access not only to your sending server, but for IMAP-style accounts, also your entire server-stored archive. Blackmail, anyone?
Account verification scams are the leading phishing techniques, used for more than two decades. If you ever receive an email asking to verify one of your accounts, ignore the email, login to your account via a previously-saved bookmark, and see if the account needs attention. 99.99% of the time, you'll be in the clear without doing a thing.
Posted on June 11, 2018 at 09:33 AM