| Home | The Book | Training | Events | Tools | Stats |
September 30, 2009
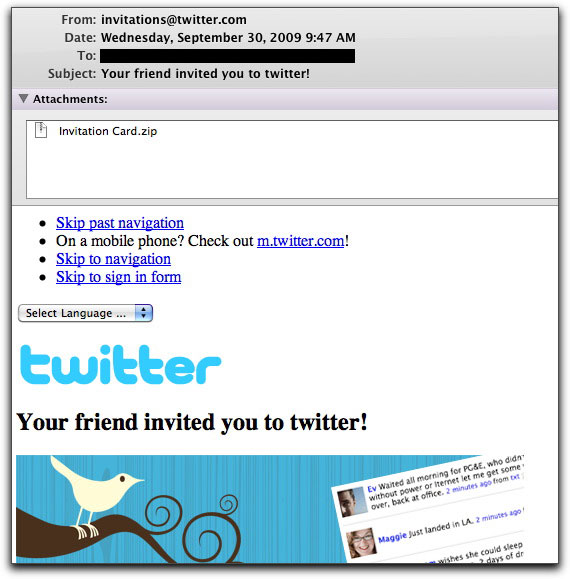
More Twitter Invitation Malware Lures
Just saw a blast of faux Twitter invitation email messages. Their look hasn't changed from earlier campaigns:
Lower down in the message is a link to a (dot.sub-hosted) video that explains Twitter, followed by a login form. Although you might suspect the form is phishing for login credentials, the form actually submits to Twitter. No, friends, this isn't a phishing expedition. It's a malware delivery vehicle, where the payload is in the attached file named Invitation Card.zip.
Why should the crook bother grabbing just one set of login credentials when the Trojan that gets installed can load a password stealer for all your logins?
Posted on September 30, 2009 at 10:20 AM
It arrives as a simple message "from" an address you don't recognize (a forged address at the University of Maryland in the sample I saw):
Subject: Good dayHere are your banks documents.
Attached to the message is a file (body.zip in the latest one I've seen). To the unsuspecting recipient comes questions such as, "How did some stranger get hold of my bank documents?" and "What information is in there that the stranger could see?" Unzipping the file and double-clicking the resulting .scr file poisons an unprotected PC with the Mytob worm, essentially offering up the PC to control by crooks.
Fortunately, the copy of the file I saw was detected by over 90% of the VirusTotal tests. But unless you pass every attachment through VirusTotal before opening it, you never know what lies inside a piece of attached malware. Nor can you rely on even the most up-to-date antivirus software to protect you from a sneak attack.
Posted on September 30, 2009 at 08:54 AMSeptember 28, 2009
419er Invokes the International Monetary Fund
About a year ago, I posted two Dispatches (here and here) about 419er email messages trying to convince recipients that not only was some recently discovered money due to them, but that someone was trying to claim the money in their names without permission. The goal of this approach is to get you riled up about the impersonation and spur you to get in touch with the crook.
Today I saw a similar approach, but this time, the "impostor" was after my money by claiming he was my next of kin and that I was dead. Here's the tale:
Subject: RE: URGENT ATM ALERT
Finance Department DirectorUNITED TRUST BANK LIMITED
80 Haymarket London
SW1Y 4TE
EnglandATTN BENEFICIARY:
I found your name in the Central Computer among the list of unpaid
(Contractors, Inheritance next of kin and lotteries winners beneficiaries that was originated from American, Europe, Asia plus Middle east and Africans) among the list of individuals and companies that your unpaid fund has been located to the Standard Chartered Bank, HSBC,Barclays Bank, Natwest Bank, Standard Chartered Bank, African Bank,Trade Bank, ICB, African Development Bank,Bank of America, Eco Bank plc, United Trust Bank Plus ATM payment. Your name appeared among the beneficiaries who will receive a part-payment of US$5.5 million and has been approved already for months. You are requested to get back to me for more direction and instruction on how to receive your fund.However, we received an email from one Dr. Robert Walter who told us that he is your Next of kin and that you died in a car accident some time ago.
Dr Robert Walter account co-ordinate as follows:
Name of Bank: BANK OF AMERICA
Name of Account Holder: Robert Walter
Account Number: 0046 1697 4294
Routing Number: 011000178
Bank Address: 740 Gallivan Ave., Boston, MA. 02124
SWIFT CODE: BOF AU3N
WIRE TRANSFER NUMBER: 026009593He has also submitted his account for us to transfer the fund to him. We want to hear from you before we can make the transfer to confirm if you are dead or not.
Once again, I apologize to you on behalf Of IMF (International Monetary Fund) failure to receive your funds in time, which according to records in the system had been long overdue.
Yours Sincerely,DOUGLAS ADAMS
Finance Department Director
UNITED TRUST BANK LIMITED
As in the earlier attempt, today's message includes bogus account information on the interloper to make it look more legitimate. The street address and ZIP code of the BofA branch are slightly off (the real branch is on Gallivan Blvd in 02122 — info that took me all of 10 seconds to discover on Google Maps), and whether the various numbers and codes are real (mostly doubtful) is not worth investigating.
The crook-sender of this email, already disguising himself as a bank executive, throws one more log on the fire by apologizing on behalf of the International Monetary Fund. Sheesh.
One of the things that caught my eye about this message was the crook's use of the name Douglas Adams. When you see the From: name of a message that is the same as someone you've known — the late, great Douglas Adams — it does peak one's curiosity. I first got to know the real Douglas a long time ago when he was using HyperCard in the course of research for his Last Chance to See project. I have no way of knowing if this 419er even knows the heritage of the name, or if it was just a name composed at random. Alas, the crook's meaning of life may well be a number, but it's the number of dollars — far more than 42 — he can scam from unsuspecting victims.
Posted on September 28, 2009 at 10:44 AMSeptember 27, 2009
Lottery Scammer With a Web Site
I don't recall seeing a 419 lottery scammer go to the trouble of creating a web site aimed at strengthening his credibility. But, just as most 419ers use free email accounts as points of contacts, the Thai lottery scammer discussed here uses free web site hosting offered by officelive.com (a Microsoft product).
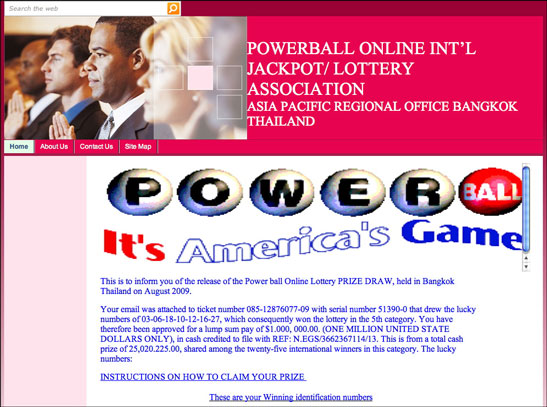
Let's get to the email message first. Interestingly, although the phony lottery is identified as being in Asia, it invokes the pretty well-known U.S. game, Powerball (albeit with slightly different construction).
From: Power Ball Int'l Lottery Ass
Subject: Congratulations!!!POWER BALL ONLINE INT’L JACKPOT/ LOTTERY ASSOCIATION
ASIA PACIFIC REGIONAL OFFICEDear Sir/Ma,
We are Pleased to inform you that your email was selected among the winning numbers of the recently Lotto conducted from the Lotto Website and we shall be glad if you can claim your prize, please respond to this mail within 72 hours otherwise we will assume that you are not interested.
We conduct the Lotto using Lotto as part of our tax relief program set up by the International Lottery Board and America Government, on this note we congratulate you and wish you best of luck as you claim the prize attached to this Lotto.
For more details visit:http://ojpowerbl.web.officelive.com/default.aspx
THAILAND CONTACT PERSON: REV. KANE LEE.
(Winner’s directorate office)
TEL: + (66) 823-337-743
Office Fax: + (66) 273-452-16
LOTTERY CO-ORDINATOR.
Coordinator Power ball Jackpot Lottery
Regd No: 79472002
Some pretty funny (as in "ha ha") things in the message. How a lottery would be associated with tax relief escapes me. Since when have taxes gone international? And then to have a member of the clergy acting as a lottery contact person is just too bizarre.
The web site is a combination of smooth templates supplied by officelive.com and absolutely butt-ugly extra content supplied by the scammer.
Among the treasures is an image ripped off from the actual U.S. Powerball lottery, boldly declaring "It's America's Game!". Would a recipient wonder what America's game is doing in Thailand? I'd like to think so, but then again it wouldn't surprise me to have uncritical thinkers blow a brain fart whenever they think they've won a big chunk o' cash. Further images at the bottom of the page show photos of winners of other lotteries holding those oversized novelty checks.
To me, the real joke is that the landing page for the site — not requiring any visitor identification to view — reads like a personal message aimed directly at the email recipient. It tells me that my email was attached to ticket number blah-blah.
As preposterous as this whole campaign appears to those who follow 419 lottery scammers, there are plenty of email and internet users out there who will fall for the trickery. Even if they might be skeptical of an email message, the web site, with its professional-looking template, will convince them that it's legitimate. They'll be out thousands or tens of thousands of dollars to cover fees, documents, taxes (no tax relief here!), and other totally fake costs before they realize they've been taken. And Microsoft isn't helping by allowing this site to be operational for at least 24 hours after the emails started flowing.
Posted on September 27, 2009 at 04:05 PMSeptember 25, 2009
A Phisher, A Faker, A Malware Maker
Rub-a-dub-dox, Three crooks in my inbox.
If only there were just three!
First up is a phisher whose email Subject: line caught my eye, but for reasons probably unknown to the sender:
Subject: Dear Abbey Customers Upgrade
When I first saw this, I was unaware of a UK financial institution called Abbey. Instead, my brain connected "Dear Abbey" with the late Abigail Van Buren's newspaper advice column, "Dear Abby" (still being written today by her daughter). Misspellings are so common in spam, that the "Abbey"/"Abby" differential was insignificant. In any case, the context of a newspaper column notifying people of a customer upgrade caused my brain to do a backflip.
Once I figured out what Abbey was, the rest of the picture fell into place. This was just another run-of-the-mill phishing scam aimed at grabbing login credentials from Abbey customers. Why the phisher is bothering spewing this missive to a [very poor quality, I can assure you] list of email addresses worldwide is beyond me. The message I received was among a batch of 50, whose addresses were itemized in the To: header field (don't get me started). Had this crook really done his homework to target likely candidates, I'd expect to see more than just the one .uk country code top-level domain address. (Not that everyone in the UK has an email address with that ccTLD, but just 2% of this batch?)
Whenever a phishing attempt arrives on my server aimed at tricking customers of highly regional financial institutions nowhere near me, I assume that the originator is a phishing newbie. Results from such campaigns sent far and wide can't possibly pay for themselves, no matter how cheap it is to buy the phishing kit, rent the addresses, buy cycles on a botnet, and perhaps even pay for a hacker to break into a legitimate web site to host the phishing site. Unfortunately, those who sold the raw materials profit regardless. And the spamonomy continues to flourish.
My second crook du jour is pulling the lottery-based 419 scam. Invoking two well-known computer-related companies, this attempt was signed by a Lawrence McDonald, who claims to be a Public Relations Officer.
On its way to tell me I've won a million pounds (oddly printed as $1,000,000 (One Million ) Pounds Sterlings), this prototypical lottery message begins:
Subject: EMAIL LOTTERY ANNOUNCEMENT...TICKET NUMBER:008795727498
SERIAL NUMBER: MIC-AOL/8303-09
LUCKY NUMBER: 04-18-35-38-53-46 (12)
Dear Sir/ Madam,
The prestigious Microsoft and AOL has set out and successfully organized a sweepstakes marking the year 2009 anniversary we rolled out over $400,419,864 USD. for our end of year Anniversary Draws. Participants for the draws were randomly selected and drawn from a wide range of web hosts which we enjoy their patronage.
I don't care if you are freakin' Microsoft and AOL, no entities (except governments) are handing out 400 million bucks in 2009.
Suckers who fall for this 419 message are supposed to contact a Michael Goldfine. He has a (free) AOL email address, thus lending a shade of credibility to the AOL connection with the bogus lottery. One can also reach Mr. Goldfine by phone at a number that happens to be a UK mobile phone number.
BTW, if you want to educate and entertain family and friends who might be susceptible to these lottery scams, just take something from the email message that is supposed to be unique — like the "ticket number" — and toss it at Google. The results show that this is one darned lucky ticket number, having been the winning ticket for at least the past two years.
Crook Number Three for today is spreading malware via an age-old trick:
Subject: Thank you for setting the order No.475456Dear Customer!
Thank you for ordering at our online store.
Your order: Sony VAIO A1133651A, was sent at your address.
The tracking number of your postal parcel is indicated in the document attached to this letter.
Please, print out the postal label for receiving the parcel.Internet Store.
Attached to this message is a .zip file (invitingly named open.zip), weighing in at a lightweight 14.05 KB. How harmful could a 14K file be? Maybe the file really is just an invoice and label. OH NO YOU DI'NT! Running the file through VirusTotal reveals that it's a backdoor Trojan capable of subsequently loading anything its commander and controller wants.
This "we're shipping you something expensive that you didn't know you bought" tactic is the quintessential trick aimed at getting an unsuspecting recipient to act on the sender's behalf (and to the recipient's detriment). The recipient fumes upon reading the message — "Hey, I didn't order that thing!" — and will double-click that attachment before the full release of adrenalin has reached all extremities. Even if the user has antivirus software installed, and the invading malware is stopped in its tracks, the recipient is still left with an uneasy feeling. "Is someone out there racking up credit card charges?" "How can I check with the company about this order?" And so on. You have to get a few of these under your belt before your eyes just roll and your adrenalin doesn't even drip out its glands.
This crooked threesome didn't arrive in a tub, but their messages are going into one here. It's labeled Trash.
Posted on September 25, 2009 at 12:06 PMSeptember 18, 2009
419er Fails to Win Me As a Friend
If you've watched enough reality television programs, you have certainly heard a sound effect that is played whenever a show participant says or does something that is so off-the-wall that it brings the proceedings to an instant halt. That sound effect replicates the noise of a phonograph arm and needle skipping wildly across grooves of a phonograph record (yes, I know it's only one spiral groove...go away). I feel the need to explain the sound because I doubt that many young people under the age of 20 in developed countries have ever heard that sound on a real phonograph and record.
That sound played in my mind when I started reading today's 419 email message, which begins thusly:
Subject: PropositionConfidential Message:
I hope this message will meet you in good faith, please pardon me for reaching you in this manner because you do not know me, I have an obscure proposal of mutual interest to share with you. I got your email address from the Internet through my search for a relatively unknown person who will assist me in securing a large sum of amount.
[cue sound effect]
Relatively unknown? How dare you! Have my 30 years of writing and 45 books left me in a state of relative unknowingness? Hrrrmph.
This "proposition" claims to be from the dean of a Ugandan university. Interestingly, the name of the person, Joseph Owor, belongs to the real Dean of Faculty of Business Administration at Uganda Christian University. His photo is even on the university's web site.
So, no, this offer cannot possibly have originated with the real Joseph Owor. Instead, a crook has hijacked the dean's name and reputation — doing the same with Christian charity, if you read his whole appeal.
Contact is to be made through his "secure email address," a free mcom.com address (a domain owned by AOL).
I feel badly for the real Dean Owor. Because the university email contact point is a centralized email address, there will certainly be some backlash by recipients of this 419 message that will cast aspersions on the gentleman. He'll have to defend himself against something he may not even understand. He will, much to his chagrin, no longer be "relatively unknown."
Posted on September 18, 2009 at 09:08 AMSeptember 09, 2009
Faux United Parcel Service Delivers...Malware [Updated]
Ah, the tricks that malware propagators use to get unsuspecting recipients to open email attachments. For example:
Subject: UPS Delivery problem NR 9133992465.Hello!
We failed to deliver the postal package you have sent on the 11th of July in time because the addressee's address is inexact.
Please print out the invoice copy attached and collect the package at our department.United Parcel Service.
Inside the attached file, named Mae4e28ca.zip in the email I saw, is a backdoor Trojan recognized by only 35% of VirusTotal test suites.
The message was rather sloppily done. For instance, the forged From: address made no reference to UPS. I mean, if you're forging, why not do something that adds credibility to your bogus missive? Also, the United Parcel Service does not deliver postal packages (although in rare cases, such as in my ZIP code, they will hand off a parcel to the local Post Office for delivery). And how about that word inexact? Someone just got a new thesaurus. If you screw up an address of a UPS parcel, they'll use far more colorful and direct wording to let you know you're a doofus.
Chalk this one up to yet another attempt to trick recipients to taking action on behalf of the sender to the detriment of the recipient.
UPDATE 1745 PDT: Just saw another one under the guise of DHL Delivery Services. In place of inexact is the more forceful wrong. Attachment on this one was named D36ebd4a3.zip. Attachments for this campaign could be uniquely named per email message.
Posted on September 09, 2009 at 08:07 AMSeptember 05, 2009
No Holiday for E-Crooks
I doubt any Americans are behind the scams described here, so the perps may not be aware that this weekend is Labor Day weekend in the United States, with Monday being the actual holiday. It marks the psychological end of summer here, with kids back to school, vacations over, and the start of the inexorable march toward the depths of winter.
It used to be the case that email tended to go unopened until travelers returned home Monday night or got to the office on Tuesday morning. These days, however, a sizable number of emailing folks have WiFi-enabled devices and smartphones with them 24/7. If their email addresses are on the crooks' lists, they may discover these attempts to steal and infect long before the holiday's end.
PayPal phishers are out in force (as I mentioned earlier). One of them, whose Subject: line mysteriously says
Subject: Paypal ownership verification
has a fairly well-crafted message body, formatted in HTML and using a logo image retrieved directly from the real paypal.com. Here's the text of the spiel:
Dear Customer,
As part of our security measures, we regularly screen activity in the PayPal system. We recently contacted you after noticing an issue on your account.We requested information from you for the following reason: Our system requires further account verification. Case ID Number: PP-000-087-024 This is a third and final reminder to review and renew your account, you will be provided with steps to restore your account access. We appreciate your understanding as we work to ensure account safety. In accordance with PayPal's User Agreement, your account access will remain limited until the issue has been resolved. Unfortunately, if access to your account remains limited for an extended period of time, it may result in further limitations or eventual account closure. We encourage you to review your PayPal account as soon as possible to help avoid this.To review and renew your account and all of the information that PayPal used to make its decision to limit your account access, please click here you will be automatically logged into your account.
We thank you for your prompt attention to this matter. Please understand that this is a security measure intended to help protect you and your account. We apologize for any inconvenience.
Sincerely
PayPal Account Review DepartmentPayPal
Veteran phish spotters will immediately recognize the Dear Customer greeting as a dead giveaway that PayPal didn't send the message. In fact, so-called "account verification" pitches from any online business that begins with Dear Customer or Dear Member without referring to you by name (not email address) is a sign to delete. Of course, some email lists also have names attached to addresses, so just the presence of your name in the greeting does not guarantee legitimacy; but lack of your name guarantees crookdom.
Another PayPal phishing attempt isn't as polished. This one, titled
Subject: PayPal - New Message
looks as though it was composed by someone who failed HTML 101. The message body is short and to the point:
You have 1 new ALERT message Please login to your PayPal account in order to read the message.To proceed, please click here
Thank you for using PayPal
Copyright © 2009 PayPal Inc. All rights reserved.
Ugh. Not even a "Hi, howareya?". The link is to a hijacked Roadrunner (rr.com) account. First of all, even if PayPal sent out such notices, they wouldn't do it with such an u-g-l-y message. Second, the only way you should log into your PayPal (or other financial) account is via a browser bookmark that you created after having manually typed the URL the first time (don't forget the https: part) and verified that it's the real site.
And finally this morning(!), we have a greeting card malware distribution scam. As with the gazillions like it that have come before, this one abuses the domain name of a legitimate online greeting card firm, claiming to have originated from greetings.com (owned by Hallmark). Here's the email message:
Subject: Hey, you have a new Greeting !!!Hello friend !
You have just received a postcard Greeting from someone who cares about you...
Just click here to receive your Animated Greeting !Thank you for using www.Greetings.com services !!!
Please take this opportunity to let your friends hear about us by sending them a postcard from our collection !
Clicking the link in most email clients will start a download of a file named card.gif.exe, hosted on an otherwise legitimate site of an Ecuadorean rose grower. This backdoor Trojan file has been around the malware circuit for about a month and a half, and has pretty good antivirus coverage according to VirusTotal. Even so, I wouldn't want to open that file on any production Windows PC. I contend that antivirus software should be installed as a safety net against accidental exposure to Bad Stuff. A message asserting some anonymous admirer is best left for dropping into the vent hole of a high school student locker.
Posted on September 05, 2009 at 10:45 AMSeptember 03, 2009
Some spamwars.com Statistics
I'll take a break from my usual anti-BadGuy rants and share with Dispatches readers a few tidbits about visitors to this site. The information comes from Google Analytics, which I embedded within this site about a year ago. It was primarily for my personal curiosity, since I have no advertisers to appease and no other overlords dangling swords over my head.
First, on the techy side, here is breakdown of the most popular browsers and operating systems visiting this site:
| Browser / OS Platform | Pct. Visitors |
|---|---|
| Internet Explorer / Windows | 31.95% |
| Firefox / Windows | 29.68% |
| Firefox / Macintosh | 11.72% |
| Opera / Linux | 10.02% |
| Safari / Macintosh | 4.54% |
| Firefox / Linux | 4.35% |
| Chrome / Windows | 2.84% |
| Opera / Windows | 2.08% |
| Mozilla / Linux | 0.95% |
| Konqueror / Linux | 0.38% |
| Safari / iPhone | 0.38% |
If you merge the operating systems, Firefox is the winner here, with IE running second with pretty dismal penetration — certainly below industry estimates for IE's overall user share. I take this to mean that spamwars.com visitors tend to be on the savvy side when it comes to security. I wouldn't use IE on a production PC for daily web surfing on a dare.
Linux and Mac users are just about even. I imagine that most of the Linux users hold admin or similar posts in IT departments. That so many of them prefer Opera signals that they practice security through obscurity...not a bad practice if you're responsible for keeping a network clean.
As for which content areas of this site are favored by visitors, I'm a bit surprised. After the main entry page, the most popular destinations are the Tools pages, especially the base64 decoder. While the tools I provide are certainly workable, they are (intentionally) not ultra-sophisticated. I don't monitor what types of content visitors are decoding on these client-side tools, but I am curious about whether it's the tech-savvy or general consumer visitors who take advantage of these tools. I would think that experienced admin types would have other tools — if not utilities that they, themselves, wrote — to handle these tasks. Whatever the case, I'm glad the tools are being used.
I'm a little disappointed in the traffic on the Stats page. A lot of the problem must be attributed to my failure to get that page reasonably ranked for Google searches of the phrase spam stats, even after nearly five years of daily content changes and enough keywords to get anybody's attention. When this site hits its five-year anniversary this coming November, I will reevaluate whether I'll continue publishing those stats. If you like them, let me know.
One final note about visitors finding this site is that many arrive here by using search engines to hunt down phrases or names found in various spam and malware campaigns reported in this blog. It is for this reason that I quote liberally from particularly nasty or tricky email messages — so that the curious email user will be able to discover the truth about a message aimed at bilking him or her out of money, private information, or computing power. If one of my tirades here has helped prevent a regular email user from being tricked into acting on behalf of a crook, then this long effort is worth it.
Posted on September 03, 2009 at 09:55 AM