| Home | The Book | Training | Events | Tools | Stats |
March 29, 2016
Malware Blasts Keep Coming
The same underlying campaign discussed in this recent post continues to spew its trickery to try to get unsuspecting recipients to load a very bad Trojan into Windows PCs. Even through the message content varies quite a bit, there is a similar look and feel to them all.
Most of the messages refer to invoices supposedly owed by the recipient or payments intended for the recipient. Some examples:
Subject: FW: Overdue Incoices [sic]Dear [recipient username],
Please find attached copy updated statement as your account has 3 overdue incoices.
Is there any reasons why they havent yet been paid?Best Wishes,
Lakeisha Oconnor
Chief Executive Officer
[attachment: [recipient username]_copy_346509.zip]
Subject: Requested receipt ID:736685Dear [recipient username],
Please find attached your receipt, sent as requested.
We are making improvements to our billing systems to help serve you better and because of that the attached invoice will look different from your previous ones.
Kind regards,
Harland Floyd
Key Account Manager
[attachment: 6DC0C_ [recipient username]_736685.zip]
Subject: CCE29032016_00076[attachment: CCE29032016_00076.rar]
Sent from my iPhone
Subject: FW:Your transaction has been successful. More information in the document below.
[attachment: copy_[recipient username]_744004.zip
Subject: Bill N-590C2DDear [recipient username],
Please check the bill in attachment.
In order to avoid fine you have to pay in 48 hours.Best regards
Demarcus Leach
Key Account Director Municipalities
[attachment: [recipient username]_e-bill_590C2D.zip]
I had to laugh at the ones that misspelled "invoices" as "incoices" in multiple places. This slip has the hallmark of an author who is more comfortable with a Turkish keyboard (and who fails to proofread his/her output).
As for the messages claiming to come from iPhones, the headers are forged to make them look to originate from the recipient's own email account. But there are a couple of problems when you investigate the headers further. For one, the iOS devices I've been using the past week are all running iOS 9.3, whereas the messages identified themselves as coming from iOS 9.0.2 devices. More tellingly, the messages originated from a variety of South Asian countries—while my butt has been firmly planted in California for months.
Sadly, I believe this campaign is far from over. The minimalist messages—with not much more than an attachment—may be the most hazardous because they pique one's uncritical curiosity. And, of course the threatening email ("you have to pay in 48 hours") can also send the recipient to open the deadly attachment (which could, in turn, load malware that ransomizes all files on the PC).
It's a dangerous world in email-land. Anti-virus software doesn't necessarily cover all bases. Only knowledgeable and paranoid humans have the full power to stop the madness.
Posted on March 29, 2016 at 11:49 AMMarch 22, 2016
Persistent and Escalating Malware Delivery Campaign
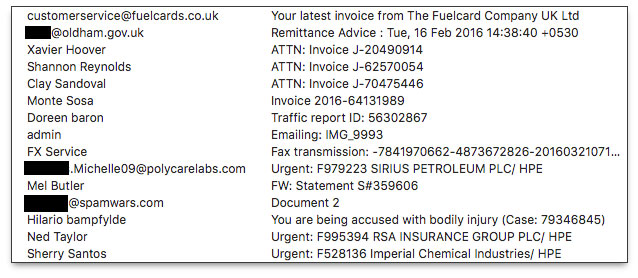
It's easy for me to ramp up my suspicions when an unsolicited email arrives with an attachment: I'm just one guy in total control of everything my business does. Thus, when I see that my inbox contains something identifying itself as an invoice from a company I don't recognize, all shields go up. Such has been the case for the following inbox listing gathered over the last month or so (potentially valid, but hijacked personal email addresses redacted):
I knew all of these emails were bogus without even opening them, including the one that "came from" my own domain. I may be getting older, but I'd still remember sending myself an attachment within the last few minutes. Heck, I even know where my car keys are.
What I fear most about these types of email messages is that they might slip through a variety of spam and malware filters to land on PCs of users who aren't as paranoid as I am. Small business employees may be the most vulnerable because things like invoices, transcribed faxes, and "urgent" messages naming big companies could easily trigger a double-click on the attachment to investigate the details claimed in the email message. Even if the recipient doesn't handle Accounts Payable, a curious employee will want to snoop on an invoice to see how the company is spending its money.
Or, how about that message that indicates the recipient is "being accused with bodily injury", complete with Case number? Yikes!
Let's look at bodies of some of these messages to examine the social engineering tricks the senders are using to convince recipients to open an attached file. I discuss these all in one batch because they are all formatted in a similar way that points to them leading back to a single, nefarious source.
First, the Fuelcard invoice:
Please find your latest invoice attached.If you have any queries please do not hesitate to contact our Customer Service Team at customerservice@fuelcards.co.uk
Regards
The Fuelcard Compa
The Fuelcard Company UK Ltd
St James Business Park Grimbald Crag Court Knaresborough HG5 8QB
Tel 0845 456 1400 Fax 0845 279 9877
http://www.thefuelcardcompany.co.ukPlease consider the environment before printing this email.
________________________________________
This email and any files transmitted with it are confidential, maybe legally privileged, and intended solely for the use of the individual or entity to which they are addressed. If you have received this email in error, please notify the system administrator and then kindly delete the message. If you are not the intended recipient, any disclosure, copying, distribution or any other action taken is prohibited, and may be unlawful. Any views or opinions presented in this email are solely those of the author and do not necessarily represent those of the company. Please note that once signed, The Fuelcard Company terms & conditions take precedence over all prior communications by any employee or agent of The Fuelcard Company. Once a client signs The Fuelcard Company terms & conditions, this will form the full extent of The Fuelcard Company’s agreed contract with the client.E-mails may be corrupted, intercepted or amended and so we do not accept any liability for the contents received. We accept no responsibility for any loss caused by viruses. You should scan attachments (if any) for viruses.
Head Office: The Fuelcard Company UK Ltd, St James Business Park, Grimbald Crag Court, Knaresborough HG5 8QB
Registered number: 5939102
[attachment: invoice.xls]
Other than a few missing characters in the message signature, it could pass for something legitimate if you didn't know whether your company had an account with Fuelcard. And, lest you think an Excel file is harmless, the one attached here is a known Trojan, which is capable of loading all kinds of nastiness on your PC and business network.
Here is a simpler variant (ATTN: Invoice J-20490914):
Dear [recipient email account ID, not full name],Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice.
Let us know if you have any questions.
We greatly appreciate your business!
Xavier Hoover
CMS Energy Corporation www.cmsenergy.com
[attachment: Invoice_J-20490914.doc]
Simple. To the point. And it appears innocuous, until you discover the Word file is another type of Trojan.
Another variant includes what appears to be more specific details about the invoice:
Hi [recipient email account ID, not full name],Here's invoice 2016-64131989 for 68,27 USD for last weeks delivery.
The amount outstanding of 463,59 USD is due on 23 Feb 2016.
If you have any questions, please let us know.
Thanks,
Monte Sosa
Avnet, Inc. www.avnet.com
[attachment: SCAN_INVOICE_2016_64131989.doc]
Many North American recipients might be confused about the currency formatting used here: commas where periods usually go. But it's the common format in Europe and elsewhere, signifying that the author of this email message body is not American. Kind of odd when the message claims to come from an American company (based in Arizona). The Word document attachment is a known Trojan.
The Bad Guys attempt to accelerate their fear mongering with the "traffic report" message:
Dear Citizen,We are contacting you on behalf of a local Traffic Violation Bureau.
Our cameras have detected that the driver of the vehicle associated with your personal number on March 10th, 2016 has committed a violation of the rules with a code: 92136
Unfortunately, we will have no other option rather than passing this case to the local police authorities.Please, see the report with the documents proofs attached for more information on this case.
[attachment: scanned_doc-0864A0A.zip]
I really hate this kind of trick because it can trap virtually anyone with a driver's license and vehicle. Several U.S. states have an agency called the "Traffic Violation Bureau", so the message can seem quite legitimate to a fair number of folks. We know we're being spied on all the time, especially at traffic intersections, toll booths, and speed traps. You can bet your sweet buns that numerous recipients of the above message have opened the attachment to find out what they are being accused of, if not how good they look in the photo capture. Alas, the attached file contains no such information. The executable malware dropper in the sample I received has been widely distributed for years, which means that it continues to be effective in infecting Windows PCs that aren't protected by anti-virus software.
It may seem difficult to resist double-clicking this email attachment. But think for a minute: How would the "Traffic Violation Bureau" know to associate your license plate number with your email address? It's extraordinarily unlikely. Additionally, like the Internal Revenue Service and law enforcement entities, such accusations would arrive either by snail mail or a personally-served warrant. Don't be fooled by email.
Here's another Old Chestnut, which is forged to appear to originate with the administrator of your email domain:
Your message is ready to be sent with the following file or link attachments:
IMG_9993
Note: To protect against computer viruses, e-mail programs may prevent sending or receiving certain types of file attachments. Check your e-mail security settings to determine how attachments are handled.Please consider the environment before printing this email.
E-mail messages may contain viruses, worms, or other malicious code. By reading the message and opening any attachments, the recipient accepts full responsibility for taking protective action against such code. Henry Schein is not liable for any loss or damage arising from this message.The information in this email is confidential and may be legally privileged. It is intended solely for the addressee(s). Access to this e-mail by anyone else is unauthorized.
[attachment: IMG_9993.zip]
Recipients are supposed to read between the lines here, assuming that the corporate email administrator had temporarily quarantined one of your outgoing messages to check it for viruses. Of course you don't remember sending a message with the named image file, so you zoom to the attachment to open it and see what the image is. Ooooh, bad mistake! The file has a malware dropper executable in it, ready to hose your PC and network.
Finally, I'll jump ahead to perhaps the most troubling message of this batch:
Hello,
You are being charged with articles 309 to 312 of the Criminal Code. The amounts indicated for committing a crime in this section is ranging from $5,000 to $12,000.
The plaintiff also claims a moral damage compensation amounting to $11666
Please, find more information on the case (ID: 79346845) in report enclosed.
[attachment: money_79346845.zip]
No one likes to be accused of a crime, especially if there was no crime. Having read this blog posting up to this point, a couple things should ring out about this message's Bogus Factor. First, any legitimate document citing a "criminal code" would also clearly state the jurisdiction, such as a city, county, or state. More importantly, a matter of this alleged severity would not be handled by email. A snail mail or hand-delivered summons would be in order here. The From: field of the email is also quite revealing. It belongs to a Belgian company dedicated to dispensing information to ostomy patients. Oh, my. This From: address placement was not intentional. The Bad Guys simply fill in the From: field with random addresses from their spam To: lists. If you receive these emails, your address could find its way into other malware delivery emails like this one.
Makes you want to send a full ostomy bag to the Bad Guys.
Posted on March 22, 2016 at 12:55 PMMarch 15, 2016
Amazon Unusual Sign-In Activity
Frequent readers of this blog know that I like to expose tricks used by spammers and scammers to get unsuspecting email recipients to hand over login credentials or install malware. Very often the telltale sign of a bogus email is poorly constructed English in the body of the message. And yet it occurs to me that not everyone receiving these emails necessarily has English as a first language. Instead, a fancy email HTML layout and carefully placed key words may be more than enough to trick recipients into clicking on the potentially disastrous action maker in the message.
Here is a case on point:
Years ago, a very talented artist friend of mine told me about the "squint test", which instructs you to look at a graphic through squinted eyes. Your view through this limited aperture provides a quick overall sense of the image's balance, color, and primary focus. It forces you to grab a first impression of the image without seeing too much detail.
Applying the squint test to the above email, the impression is that of an Amazon.com mailing, pure and simple. And then there is that big Security badge image aimed at amping up the alarm of the message. An unsuspecting recipient might easily overlook the bad writing and focus on the alerts about "someone other than you is trying to access your account" and "temporarily suspend your account." Potentially frightening things if you're an active Amazon shopper.
Fear and/or curiosity about the mysterious logins and account suspension are enough to draw plenty of recipients to that "Click here" button.
Now, this message may pass the squint test, but it certainly fails the stink test. It reeks of problems that should be easily detected even by recipients with only modest technical know-how.
First, it is vital that all email users be extraordinarily suspicious of any message (including email, text, or social media message) that claims to signal a problem with any kind of password-protected account. This is especially true for sites connected to your financial information (banking, investments, PayPal, government benefits agencies, insurance, mortgage, credit card companies, etc.) and shopping sites (too many millions to list). Next, I recommend ignoring (i.e., deleting without action) messages claiming to come from brand-name retail and food chains, particularly those with which you don't have ongoing relationships. That Chipotle coupon you think you'll earn by filling out a survey will likely become more aggravating and painful than a bout of E. coli.
But back to our bogus Amazon mailing.
If you're queasy about the threat of a suspended account, the best action you can take is to log into your account by way of a previously saved bookmark to the site. Do not, under any circumstances, click a link in the message to go to the site. Also don't rely on typing the URL to the site into your browser, because you may make a slip that takes you to a phony lookalike site whose domain was explicitly registered to trap sloppy typists. If there is truly a problem with your account, you will be alerted to that fact when you attempt to log in to the legitimate account via the normal process.
Now, allow me to itemize the signals that this email message is sending to invalidate it as being real. I'll start with the most obvious items that don't require any technical expertise or even good English skills (since the message is targeted at English-reading recipients). The only assumption I'll make is that large companies, such as Amazon, Google, Apple, Microsoft, and the like, push their form letter correspondence through layers and layers of writers, editors, customer support staff, and lawyers. It is exceptionally rare for this type of communication from a major corporation to be poorly written, formatted, or coded. It can happen, but the goof would be limited. Moreover, avoiding in-message links still has you covered.
- The message isn't even addressed to me. The To: field has some else's email address at a domain different from mine. That, on its own, is sufficient reason to summarily delete the message.
- By rolling the cursor (or, in a touch-screen interface, tapping and holding) atop the "Click here" button, you can see the destination URL of the big action button. In the screen capture above, I've exposed what you'd see from this particular message. The URL does not take the user to amazon.com. There's no way that some rubber company is Amazon's account update firm.
- For a message that claims to be alerting an individual to a problem with his or her account, the "Dear Amazon.com Customer" salutation is very impersonal. When companies, such as Amazon, need to alert users about their accounts (e.g., an expired credit card), the message body will address the recipient by name. Very often, the message will contain additional personal information fragments, such as the final four digits of a credit card) to indicate the sender actually knows stuff about the recipient, and isn't trolling for shoe size.
- The From: and Reply-To: addresses are suspicious. Although it's not uncommon for automated mailings to supply a From: address indicating that you shouldn't use it to reply to the message (e.g., because that address is either intentionally invalid or isn't monitored), to repeat that same "no reply" account name in the Reply-To: field is goofy. The Reply-To: field is intended to supply a valid email message that the recipient can use to respond to the message if so desired (or email servers can use to bounce messages addressed to invalid To: addresses). Additionally, the word signifying the plural of "reply" is "replies", not the singular with an apostrophe-s attached. A sure sign of a non-English author. The same goes for the all-too-common misuse of collective plural nouns that mysteriously gain "s" plurals (e.g., "informations").
- A further issue with the From: and Reply-To: addresses is the domain. True, the full domain contains the string "amazon", but the true domain is just com-dot-com. The "amazones****" part is a sub-domain wired at com-dot-com to go to a customer's server area. I've hidden part of the subdomain because it is a particularly nasty place, and I don't want anyone reading this to get caught in its greedy, potentially terrifying, clutches.
- We're getting into good knowledge of the English language, now. It starts with the Subject: line. It's missing a period after "activity" and has an extra one at the end. A real mess that would never survive a large corporate vetting.
- Language issues abound in the message body:
- Sentences that end in commas
- Sentences that end in nothing
- Subject/verb disagreement
- Verb tenses from left field
- A seemingly small item is at the very end of the message, where the copyright symbol is represented by a question mark. You can be damned sure that the lawyers would never, ever, ever, let that mistake slide.
Additional nerdy issues also litter this message. For instance, the alt attribute of the img tag used to insert the Security badge image was obviously copied/pasted from another Amazon communication. That's my guess based on the "Kindle Daily Deals" description applied to the image. Oops.
Thus ends the autopsy of the email message that is dead to me—and hopefully to you. The only "Action Required" for this message is to delete it, unclicked.
Posted on March 15, 2016 at 05:50 PM