« Amazon Unusual Sign-In Activity | Main | Malware Blasts Keep Coming »
| Home | The Book | Training | Events | Tools | Stats |
March 22, 2016
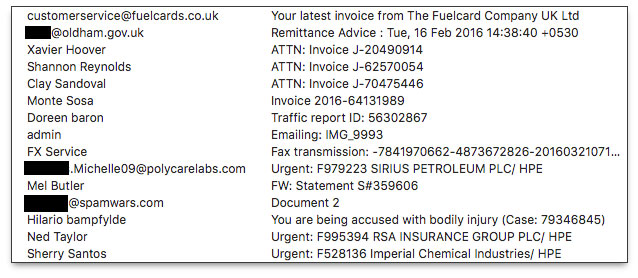
Persistent and Escalating Malware Delivery CampaignIt's easy for me to ramp up my suspicions when an unsolicited email arrives with an attachment: I'm just one guy in total control of everything my business does. Thus, when I see that my inbox contains something identifying itself as an invoice from a company I don't recognize, all shields go up. Such has been the case for the following inbox listing gathered over the last month or so (potentially valid, but hijacked personal email addresses redacted):
I knew all of these emails were bogus without even opening them, including the one that "came from" my own domain. I may be getting older, but I'd still remember sending myself an attachment within the last few minutes. Heck, I even know where my car keys are.
What I fear most about these types of email messages is that they might slip through a variety of spam and malware filters to land on PCs of users who aren't as paranoid as I am. Small business employees may be the most vulnerable because things like invoices, transcribed faxes, and "urgent" messages naming big companies could easily trigger a double-click on the attachment to investigate the details claimed in the email message. Even if the recipient doesn't handle Accounts Payable, a curious employee will want to snoop on an invoice to see how the company is spending its money.
Or, how about that message that indicates the recipient is "being accused with bodily injury", complete with Case number? Yikes!
Let's look at bodies of some of these messages to examine the social engineering tricks the senders are using to convince recipients to open an attached file. I discuss these all in one batch because they are all formatted in a similar way that points to them leading back to a single, nefarious source.
First, the Fuelcard invoice:
Please find your latest invoice attached.If you have any queries please do not hesitate to contact our Customer Service Team at customerservice@fuelcards.co.uk
Regards
The Fuelcard Compa
The Fuelcard Company UK Ltd
St James Business Park Grimbald Crag Court Knaresborough HG5 8QB
Tel 0845 456 1400 Fax 0845 279 9877
http://www.thefuelcardcompany.co.ukPlease consider the environment before printing this email.
________________________________________
This email and any files transmitted with it are confidential, maybe legally privileged, and intended solely for the use of the individual or entity to which they are addressed. If you have received this email in error, please notify the system administrator and then kindly delete the message. If you are not the intended recipient, any disclosure, copying, distribution or any other action taken is prohibited, and may be unlawful. Any views or opinions presented in this email are solely those of the author and do not necessarily represent those of the company. Please note that once signed, The Fuelcard Company terms & conditions take precedence over all prior communications by any employee or agent of The Fuelcard Company. Once a client signs The Fuelcard Company terms & conditions, this will form the full extent of The Fuelcard Company’s agreed contract with the client.E-mails may be corrupted, intercepted or amended and so we do not accept any liability for the contents received. We accept no responsibility for any loss caused by viruses. You should scan attachments (if any) for viruses.
Head Office: The Fuelcard Company UK Ltd, St James Business Park, Grimbald Crag Court, Knaresborough HG5 8QB
Registered number: 5939102
[attachment: invoice.xls]
Other than a few missing characters in the message signature, it could pass for something legitimate if you didn't know whether your company had an account with Fuelcard. And, lest you think an Excel file is harmless, the one attached here is a known Trojan, which is capable of loading all kinds of nastiness on your PC and business network.
Here is a simpler variant (ATTN: Invoice J-20490914):
Dear [recipient email account ID, not full name],Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice.
Let us know if you have any questions.
We greatly appreciate your business!
Xavier Hoover
CMS Energy Corporation www.cmsenergy.com
[attachment: Invoice_J-20490914.doc]
Simple. To the point. And it appears innocuous, until you discover the Word file is another type of Trojan.
Another variant includes what appears to be more specific details about the invoice:
Hi [recipient email account ID, not full name],Here's invoice 2016-64131989 for 68,27 USD for last weeks delivery.
The amount outstanding of 463,59 USD is due on 23 Feb 2016.
If you have any questions, please let us know.
Thanks,
Monte Sosa
Avnet, Inc. www.avnet.com
[attachment: SCAN_INVOICE_2016_64131989.doc]
Many North American recipients might be confused about the currency formatting used here: commas where periods usually go. But it's the common format in Europe and elsewhere, signifying that the author of this email message body is not American. Kind of odd when the message claims to come from an American company (based in Arizona). The Word document attachment is a known Trojan.
The Bad Guys attempt to accelerate their fear mongering with the "traffic report" message:
Dear Citizen,We are contacting you on behalf of a local Traffic Violation Bureau.
Our cameras have detected that the driver of the vehicle associated with your personal number on March 10th, 2016 has committed a violation of the rules with a code: 92136
Unfortunately, we will have no other option rather than passing this case to the local police authorities.Please, see the report with the documents proofs attached for more information on this case.
[attachment: scanned_doc-0864A0A.zip]
I really hate this kind of trick because it can trap virtually anyone with a driver's license and vehicle. Several U.S. states have an agency called the "Traffic Violation Bureau", so the message can seem quite legitimate to a fair number of folks. We know we're being spied on all the time, especially at traffic intersections, toll booths, and speed traps. You can bet your sweet buns that numerous recipients of the above message have opened the attachment to find out what they are being accused of, if not how good they look in the photo capture. Alas, the attached file contains no such information. The executable malware dropper in the sample I received has been widely distributed for years, which means that it continues to be effective in infecting Windows PCs that aren't protected by anti-virus software.
It may seem difficult to resist double-clicking this email attachment. But think for a minute: How would the "Traffic Violation Bureau" know to associate your license plate number with your email address? It's extraordinarily unlikely. Additionally, like the Internal Revenue Service and law enforcement entities, such accusations would arrive either by snail mail or a personally-served warrant. Don't be fooled by email.
Here's another Old Chestnut, which is forged to appear to originate with the administrator of your email domain:
Your message is ready to be sent with the following file or link attachments:
IMG_9993
Note: To protect against computer viruses, e-mail programs may prevent sending or receiving certain types of file attachments. Check your e-mail security settings to determine how attachments are handled.Please consider the environment before printing this email.
E-mail messages may contain viruses, worms, or other malicious code. By reading the message and opening any attachments, the recipient accepts full responsibility for taking protective action against such code. Henry Schein is not liable for any loss or damage arising from this message.The information in this email is confidential and may be legally privileged. It is intended solely for the addressee(s). Access to this e-mail by anyone else is unauthorized.
[attachment: IMG_9993.zip]
Recipients are supposed to read between the lines here, assuming that the corporate email administrator had temporarily quarantined one of your outgoing messages to check it for viruses. Of course you don't remember sending a message with the named image file, so you zoom to the attachment to open it and see what the image is. Ooooh, bad mistake! The file has a malware dropper executable in it, ready to hose your PC and network.
Finally, I'll jump ahead to perhaps the most troubling message of this batch:
Hello,
You are being charged with articles 309 to 312 of the Criminal Code. The amounts indicated for committing a crime in this section is ranging from $5,000 to $12,000.
The plaintiff also claims a moral damage compensation amounting to $11666
Please, find more information on the case (ID: 79346845) in report enclosed.
[attachment: money_79346845.zip]
No one likes to be accused of a crime, especially if there was no crime. Having read this blog posting up to this point, a couple things should ring out about this message's Bogus Factor. First, any legitimate document citing a "criminal code" would also clearly state the jurisdiction, such as a city, county, or state. More importantly, a matter of this alleged severity would not be handled by email. A snail mail or hand-delivered summons would be in order here. The From: field of the email is also quite revealing. It belongs to a Belgian company dedicated to dispensing information to ostomy patients. Oh, my. This From: address placement was not intentional. The Bad Guys simply fill in the From: field with random addresses from their spam To: lists. If you receive these emails, your address could find its way into other malware delivery emails like this one.
Makes you want to send a full ostomy bag to the Bad Guys.
Posted on March 22, 2016 at 12:55 PM