| Home | The Book | Training | Events | Tools | Stats |
April 18, 2012
Bogus Fire Safety Test Notification
This one is obviously intended for recipients who are employees in companies big enough to have a Human Resources department and something like a fire safety policy (spelling errors are in the original):
Subject: RE:Enclosed Tutoring Materials
Dear Colleagues
It might be useful for you to know that we are taking part in a joint event with Fire and Counter Terorrism Safety icnluding 3 written tests on Thursday.
Last year four in ten epmloyees survyeed could not pass the Fire Safety test.
Each of you will find enclosed a Fire Safety Policy and your role decsription. Please take a look at the enclosed materials before April.
Kind regards,
Susan
Department of Human Resources
The attached file is named Fire Safety Guidance.pdf.zip, apparently trying the old chestnut of hoping the PC is set up to not display file name extensions (thus making this file look like an Acrobat file — not that PDFs are necessarily safe, but that's another story). Opening the attachment in an unprotected Windows machine will load spyware and/or a Trojan loader, which can then load and spy on anything you've got. In fact, if your machine gets infected, you might wish for a fire, and toss the PC into it on your way out the door.
April 16, 2012
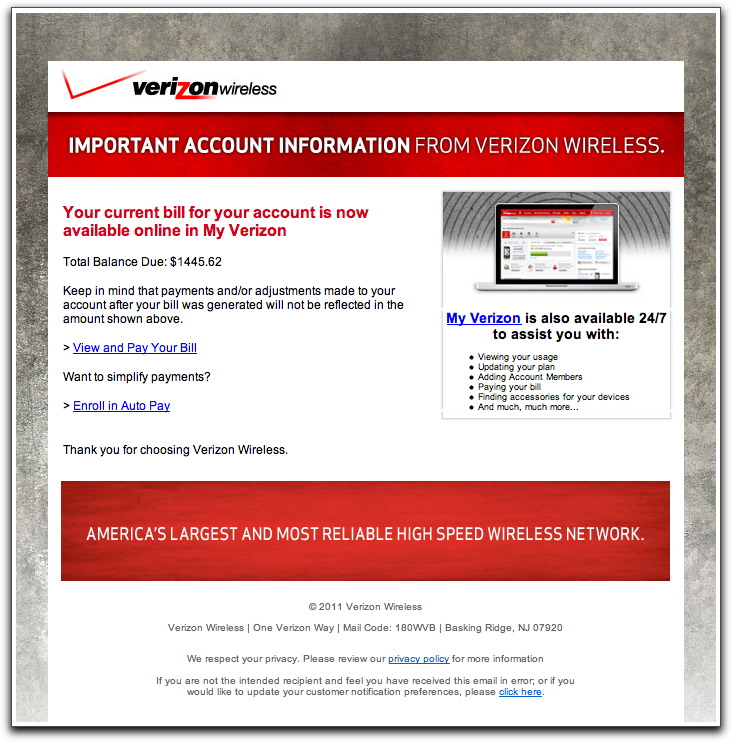
Phony Verizon Billing Notification
Using the same behind the scenes modus operandi of the recent fake Apple Store order acknowledgment mailing, today's version (Subject: Your Bill Is Now Available) abuses Verizon's name and artwork:
If you are a Verizon customer and suddenly see an impending $1445 bill coming, the adrenalin flow will likely trigger a click of the link to see how your bill could have gotten so high. The links, of course, are to a hijacked web site, where a "WAIT PLEASE Loading..." visible screen masks the loading of obfuscated JavaScript from three other hijacked web sites. The scripts then begin their attack on your PC.
Remember that spammers and scammers rely on you to act, and will use every trick in the book to outrage you and get that mouse button a-clickin'. Roll over the links to check the URLs. If you're still not certain, log into your account via a previously-saved bookmark. Once there, you'll see that you don't have a $1445 wireless bill.
Posted on April 16, 2012 at 09:33 AMApril 09, 2012
Phony Apple Store Order Acknowledgment
This morning, the malware bad guys have been sending out messages titled:
From: Apple Store
Subject: Order Acknowledgment W273706813
The order numbers vary from message to message. The body is a well-formatted HTML page that is very reminiscent of the actual order confirmations that Apple sends out (under a different Subject: line, mind you).
Bill to and Ship to names and addresses are apparently filled in from a random database under the crook's control. You won't recognize the names, but you will be terrified that you are being charged for a 17-inch Macbook Pro to the tune of about $2600.00.
Whatever you do, do not click any links in that email message. The links I've seen go to hijacked web sites. Although the pattern of what the link serves up has been used before (links to auto-load multiple JavaScript pages that then redirect to a different destination), and those in the past have been used to deliver Windows malware, these days even Mac users can't be too careful — thanks to the drive-by Java exploit that some experts say has infected over one-half million Macs.
If you are concerned about the possibility of your Apple account having been hacked (most likely through phishing, by the way, so you were the one who gave yourself over to the crooks), visit the Apple Store through a previously-saved bookmark and inspect your order history. You'll find nothing whatsoever about these bogus orders. Let the adrenalin drain from your system, and get on with your day.
Posted on April 09, 2012 at 11:38 AMApril 08, 2012
The Power of Coincidence
I was involved in a PayPal transaction yesterday — nothing unusual about it. But look at the following sequence of items in my email inbox on a slow Saturday afternoon as a result:
I was certainly expecting the first two messages, a notice of sending an invoice and the payment in return. But then nine minutes after the payment comes a third message also claiming to be from service@paypal.com. Now, I've seen this message and it's grammar-challenged Subject: line many times before in recent weeks, so I knew that this message had no connection with: a) my transaction; and b) reality. Yet consider the power of attention this bogus message had in the wake of two legitimate messages, especially the message that conveyed information about money coming to me.
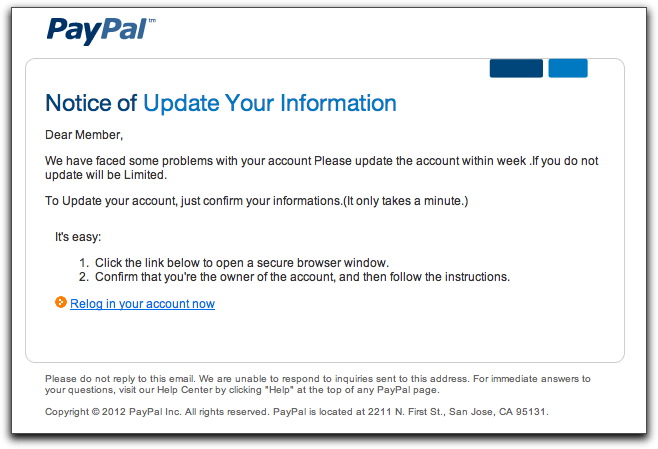
For the sake of completeness, here is the content of the third message:
The overall look of the message, aided by images downloaded directly from a PayPal web server, might also get the recipient's attention. If you know English, however, the whole thing starts to fall apart with horrific grammar and punctuation in the first two lines. My mind's ear puts the first paragraph into the mouth of the Soviet submarine captain in the movie comedy "The Russians Are Coming! The Russians Are Coming":
"Emergency! Everybody to get from street!"
By the way, here's a hint for you bogus email spotters out there: Whenever you see "information" spelled as a plural ("informations"), you can be guaranteed the message was created by an English-challenged writer, living in a non-English-speaking country.
Readers of this blog and my book know that I encourage development of healthy paranoia when it comes to one's email inbox. When something like a phishing email message arrives right on the heels of some legitimate activity you've just had with the institution being phished, that paranoia might lead you to think the institution's servers have been hacked or monitored by bad guys, and you are being personally targeted as a result of your legitimate activity. It happens to me a few times a year.
True, the coincidence is unnerving, but it is nothing more than coincidence. In the case of this particular email sequence, I knew the last one had nothing to do with the first two because the last one was sent to a different email address than the one I use for PayPal. If you still feel uneasy, simply log into your account via a previously saved bookmark. If there were truly a problem with the account, you'd learn about it there.
While I'm on this message, let me also address other advice that I give about rolling over links in potential phishing/malware messages to examine the actual URL of the link. This phony PayPal message employs a technique that bad guys have used for years to try to trick non-techies who think they know about URLs. Here is the URL of the "Relog in your account now" link from the above message:
http://paypal.com-us.cgi-bin-webscr-cmd.login-submit-dispatch.74fghghs68g48fyrt4mn86wvnchtor26hgbfn83m48hg3ufghd4sbnghtyrtdf.[removed].com/account.php
In the rollover tooltip, the uninitiated user might be fooled by the leading references to paypal.com and think all the gobbledygook following it is like the stuff you frequently see in browser address fields. But the actual domain (which I've removed) is just to the left of the slash near the end. The domain has been registered for over 10 years, so this looks to be a typical hijacking. It's possible that the hijacker set up a subdomain whose name is all the gobbledygook, or he modified the server to accept any subdomain.
Thus, even the best advice might not always be easy to follow. You might have to dig out your magnifying glass and deerstalker cap to follow the clues.
Posted on April 08, 2012 at 12:10 PMApril 05, 2012
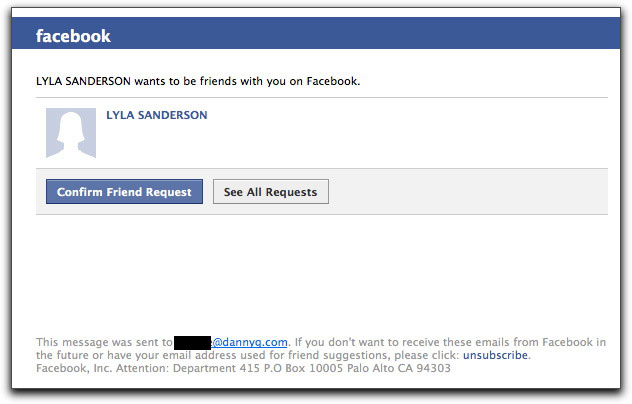
Bogus Facebook Friend Requests
If you are a Facebook user, the format of the following message will certainly look familiar to you:
It's a dead ringer for the real thing. You won't know the person requesting your friendship, so the first instinct is to click on the person's name to view their profile (or perhaps you're so desperate to increase your friend count, you click the Confirm button without thinking). No matter which link you click in this message, if your PC isn't fully protected and patched, it (and all your active login credentials) will soon belong to some crook.
Each link in the above message goes to a different hijacked web site, where an obfuscated JavaScript script starts your PC on its way to hell. If you've been reading this Spam Wars Dispatches blog recently, you'll recognize a pattern in the multiple links to malware loading web sites. What's a bit different in this one is that instead of frightening you to click a link, this message uses your typical response to a familiar email from a source you probably trust (although inherently trusting Facebook is perilous in itself).
So, how can you tell if this is phony?
Two ways:
- The easiest way is to hover your cursor atop each of the links without clicking. In most email readers, you will see a tooltip showing the URL of the link — in this case, definitely not to facebook.com. (BTW in the email client on iOS devices, you can press and hold on a link to get the same kind of popup revealing the URL. Just be sure to cancel the popup, rather than navigating to the link.)
- I'm also an advocate for learning how to read email message headers to spot when the sender isn't who it claims it is in the From: field you see in the message. Almost everything in an email header can be forged without consequence to the sender. Understanding what's true is vital to interpreting headers and avoiding being scammed.
It is email messages like this one that leads me to distrust every piece of email until I can satisfy myself that it is genuine. As is proven here, crooks count on your automatic response to familiar things. Be smart about it.
Posted on April 05, 2012 at 10:35 AMApril 03, 2012
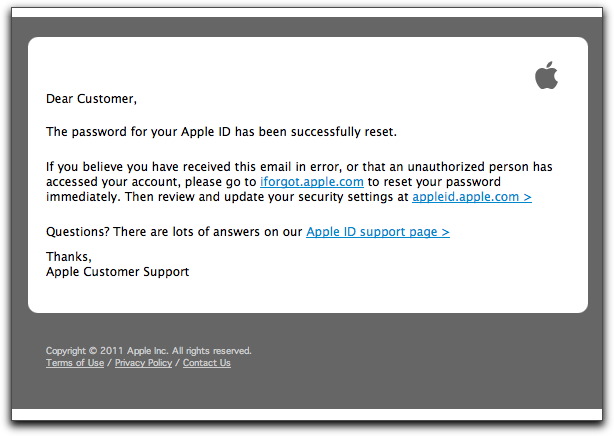
Apple ID Password Message
If you receive a message like the following, do not click any links in the message:
The Subject: line of this message, "Your Apple ID password has been reset", is like the one that Apple sends out when you really change your password. But when this message arrives when you haven't changed your password, you might think that someone has gotten into your account and ripped off your Apple ID (and is now buying up the iTunes and Apple Stores on your credit card).
Although the above message is credible-looking (unless you dig into the message headers, which immediately reveal its origin not from Apple), each link is to a different hijacked web site where malware loaders are standing by to take over your machine.
Due to recent revelations of Java-based silent takeovers that can affect Mac OS machines (without requiring the user to enter any system passwords), it's best to avoid even coming close to a page that could grab your computer with a simple visit. Rolling the cursor over the links in the above message shows that the links are not to Apple — one simple way to check out the veracity of this and similar messages.
If you receive a message like this from any (apparent) source that has one of your passwords, visit the site from a previously-saved bookmark. If there is a problem with your password (a possibility approaching zero), you'll find out there.
Posted on April 03, 2012 at 10:14 AM