« Bogus Facebook Friend Requests | Main | Phony Apple Store Order Acknowledgment »
| Home | The Book | Training | Events | Tools | Stats |
April 08, 2012
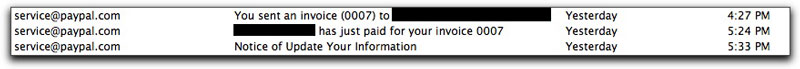
The Power of CoincidenceI was involved in a PayPal transaction yesterday — nothing unusual about it. But look at the following sequence of items in my email inbox on a slow Saturday afternoon as a result:
I was certainly expecting the first two messages, a notice of sending an invoice and the payment in return. But then nine minutes after the payment comes a third message also claiming to be from service@paypal.com. Now, I've seen this message and it's grammar-challenged Subject: line many times before in recent weeks, so I knew that this message had no connection with: a) my transaction; and b) reality. Yet consider the power of attention this bogus message had in the wake of two legitimate messages, especially the message that conveyed information about money coming to me.
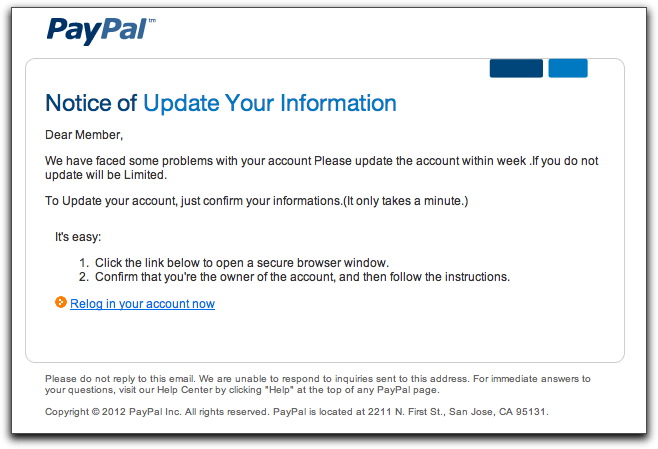
For the sake of completeness, here is the content of the third message:
The overall look of the message, aided by images downloaded directly from a PayPal web server, might also get the recipient's attention. If you know English, however, the whole thing starts to fall apart with horrific grammar and punctuation in the first two lines. My mind's ear puts the first paragraph into the mouth of the Soviet submarine captain in the movie comedy "The Russians Are Coming! The Russians Are Coming":
"Emergency! Everybody to get from street!"
By the way, here's a hint for you bogus email spotters out there: Whenever you see "information" spelled as a plural ("informations"), you can be guaranteed the message was created by an English-challenged writer, living in a non-English-speaking country.
Readers of this blog and my book know that I encourage development of healthy paranoia when it comes to one's email inbox. When something like a phishing email message arrives right on the heels of some legitimate activity you've just had with the institution being phished, that paranoia might lead you to think the institution's servers have been hacked or monitored by bad guys, and you are being personally targeted as a result of your legitimate activity. It happens to me a few times a year.
True, the coincidence is unnerving, but it is nothing more than coincidence. In the case of this particular email sequence, I knew the last one had nothing to do with the first two because the last one was sent to a different email address than the one I use for PayPal. If you still feel uneasy, simply log into your account via a previously saved bookmark. If there were truly a problem with the account, you'd learn about it there.
While I'm on this message, let me also address other advice that I give about rolling over links in potential phishing/malware messages to examine the actual URL of the link. This phony PayPal message employs a technique that bad guys have used for years to try to trick non-techies who think they know about URLs. Here is the URL of the "Relog in your account now" link from the above message:
http://paypal.com-us.cgi-bin-webscr-cmd.login-submit-dispatch.74fghghs68g48fyrt4mn86wvnchtor26hgbfn83m48hg3ufghd4sbnghtyrtdf.[removed].com/account.php
In the rollover tooltip, the uninitiated user might be fooled by the leading references to paypal.com and think all the gobbledygook following it is like the stuff you frequently see in browser address fields. But the actual domain (which I've removed) is just to the left of the slash near the end. The domain has been registered for over 10 years, so this looks to be a typical hijacking. It's possible that the hijacker set up a subdomain whose name is all the gobbledygook, or he modified the server to accept any subdomain.
Thus, even the best advice might not always be easy to follow. You might have to dig out your magnifying glass and deerstalker cap to follow the clues.
Posted on April 08, 2012 at 12:10 PM