| Home | The Book | Training | Events | Tools | Stats |
August 31, 2008
E-Profiteers Ready for Disaster
The good folks at the SANS Internet Storm Center have reported (here and here) that domain names containing the string "gustav" are being gobbled up in anticipation of Hurricane Gustav coming ashore along the Gulf coast. A lot of these domain names blend "gustav" with words like "relief," "charity," and "donation."
It's possible that some of this domain name parking is being done by individuals or organizations who will set up legitimate web sites if this storm does a Katrina-esque number on the same region. Make that remotely possible.
My bet is that the parking spot owners will either try to resell the domains to legitimate organizations or the domains will be used directly by phony fund raising scams. Let any tragedy occur, and there will be plenty of scum out there trying to take advantage of generous folks who truly want to help.
Remember that there are safe places to find out where you can help. The first place I tend to look is at cnn.com, where a click of the IMPACT button (near the top right corner of the home page) will bring you lists of charities and other outlets where you can help.
Disasters such as tsunamis and earthquakes come with little or no warning. Hurricanes, cyclones, and typhoons, on the other hand, are known well in advance of potential catastrophe. That gives profiteers plenty of time to be in place to reap rewards from others' suffering.
Similar domain names for Hurricane Hanna are already being registered.
Posted on August 31, 2008 at 10:33 AM
Phishing is pretty much all the same—luring you to a web site that looks just like the login page for a financial institution or anywhere else where a username/password combination opens the gates to goodies.
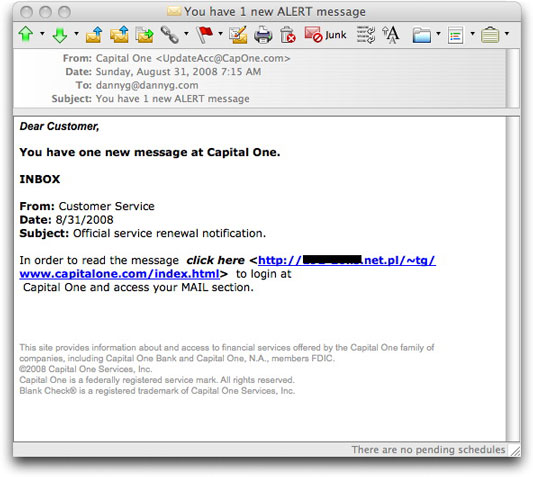
If one is wary of the overt style of phishing message—the one where there is a problem with your account, and you should log in to fix it—the shields might lower for a moment when the phishing message has a bit of indirection to it. Such is the case of one I saw this morning, which tries to lure a Capital One customer to view a message within the bank's web site messaging system. The institution with which I do online banking has a Mail section of the web site, where we can communicate with each other electronically. I believe this is fairly common. And, of course, the only way you can view such messages is by logging into the site.
The phishing message wasn't particularly professional-looking, but here it is just the same:
Note that my email client, Microsoft's Entourage for the Mac, renders hidden link addresses in plain view. Most recipients of this phishing message would just see "click here" as a clickable link, with no visible URL. Thus, even if they knew what to look for, they might not recognize that the URL is to an IP address in Poland.
Now, I've heard of outsourcing, but humongo Capital One isn't going to host its login pages at a hacked server in Warsaw.
This serves as a reminder that if you receive any type of communication purporting to come from a financial institution with whom you do business, use your established bookmark to visit the site and log in through that page.
I also go one step further—even with bookmarked pages—to make sure that the login page has the correct URL in the Address bar and the SSL certificate is in force (at least as much as the browser reveals). I perform that check for every page that requests login credentials, even accounts that seem harmless in that they don't contain much personal information. Why am I so paranoid about this? Because if a crook gets hold of any one username/password combination, there is a good chance that that combo will open doors at other sites (no, I don't have individual combinations for each freakin' site that requires a login—and it seems as though you've gotta open an account at more and more sites these days just to get basic information). It's trivial for crooks to set up robots that try your credentials at thousands of sites. All it takes is one success to expose further personal or credit card data stored on those servers associated with that username/password pairing.
It's sad that we have to concern ourselves about this stuff. But taking a What, me worry? attitude puts you directly in the line of fire from way too many Bad Guys.
Posted on August 31, 2008 at 09:49 AMAugust 27, 2008
University Degree--No Larnin' Needed
Legitimate universities—including those from whom you can earn a real degree—always put their best feet forward to attract students. Fancy catalogs, professionally-done web sites—whatever it takes to exude professionalism, class, and taste.
In contrast comes the Subject: line of one of those "dial-a-degree" spam messages, which promise that one's work experience (oops, they forgot to mention the money) is good enough to obtain a degree, including a Doctorate. Professionalism, class, and taste? You decide:
Subject: FW: Is your skills about to expired?
Is you is, or is you ain't college material?
Posted on August 27, 2008 at 08:16 AMAugust 23, 2008
Phony Anti-Virus Software
The malware lure du jour advertises security software for home or business, depending on which variant of the email you receive. Here are a few Subject: lines I've seen:
- Business Security Software
- You Computer Security. For you home.
- A new standard of Internet threat protection for your home.
The first line of the messages varies, but the balance of all the messages I've seen are identical. Here's one variant:
Anti-Virus Nero Advanced Pro. 2008. Download last update! <http://[removed].com/dhl/dhl.php>6 month free trial!
A new standard of Internet threat protection for your home or small office.
Award-winning protection against viruses and spyware, identity theft and phishing, hackers and spam.Anti-Virus Nero Advanced Pro. 2009 antivirus software with maximum spyware protection.
Protects against viruses, Trojans, and worms, spyware and adware, rootkits, identity theft and phishing attacks.
Advanced proactive protection, unmatched system performance,
automatic hourly updates and the fastest response to the latest threats.
All URLs of the ones I've seen (all hijacked web servers) lead to a PHP program called dhl.php, which automatically downloads name.avi.exe to a visiting PC. That Trojan downloader is recognized by most legitimate antivirus software, according to a VirusTotal scan.
Accepting an invitation to download and install unknown antivirus software from an unknown sender is about as safe as French-kissing a stranger in the influenza ward. Both lead to infections that you don't really want to experience.
Posted on August 23, 2008 at 07:55 PMAugust 21, 2008
Bogus Windows Updates
Two flavors of phony Windows update notices have been arriving in the past few hours.
The first arrived with a variety of Subject: lines, such as:
- Important Microsoft Windows Update
- Critical Microsoft Windows Update
Message bodies also varied a little, but generally followed the format of this one:
Dear Microsoft Customer,You are receiving this message because your version of Microsoft Windows is affected by a dangerous security vulnerability.
In order to prevent possible risk of system instability, Microsoft urges you to update at your earliest convenience.
We are providing a free update to all Microsoft Windows users.
You can update your system for free by visiting the offical website for this patch, at http://updatemanagement.[removed].net/?customerservice
Thank you for your understanding in this matter.Regards,
Wilton Silver
Business Relations Rep.
Microsoft Corp.
http://updatemanagement.[removed].net/?customerservice
The domain name, which includes the words system and update, was registered today, and the supposed registrant is [get this] "Government of St. Vincent and the Grenadines."
Almost anyone in the PC biz would know that Microsoft, itself, would never publicly label any vulnerability as "dangerous." But it's a good word to get the attention of the less technically aware.
Onto the second attempt, which arrived here in rapid succession with the same Subject: and message body:
Subject: Free Update For WindowsDear dannyg@dannyg.com, Free Update for Windows Xp,Vista
http://[IP Address Removed]/setup.exe
Each message was sent from a different botnet client, in a not atypical fire hose spray of spam. All of the messages I received pointed to the same IP address hosted in Moldova. To my surprise, the account at that address had been shut down pretty quickly—a responsible response I'm not accustomed to seeing from those environs.
At the two destinations, the techniques for infecting visitors' machines were quite different, with the first one being far more elaborate. It may be that two crooks/gangs happened upon the same email approach within hours of each other. Whether this was serendipity or an orchestrated event doesn't matter to users. Identifying bogus notices should matter a great deal.
Be it now and forever known that major operating system vendors (e.g., Microsoft and Apple) have spent oodles of money to build system updating mechanisms into their operating systems. If there were such a dire need to update an OS that it caused the companies to send emergency email messages to their customers (a near zero likelihood, BTW), both companies would direct customers to use the internal updating mechanisms, and not provide a link to visit to download the update.
There must be, however, a goodly number of Windows users out there who use pirated copies of XP and Vista. The internal Windows Update mechanism isn't available to them because their OSes fail the "genuine advantage" test. Heaven knows what else was delivered with the pirated OS already, but their users would probably be tempted to download a supposedly free update that lets them avoid Microsoft's laser-eyed stare. I don't have a lot of sympathy for the pirate users, and getting their systems pwned by a botnet might feel like Justice...except that it means that their systems will be used to flood my inbox with spam and perhaps attack my web sites. Vigilantism on the Internet usually backfires on the vigilantes.
Posted on August 21, 2008 at 08:25 AMAugust 18, 2008
Back to News (Sorta)
Malware lures continue unabated, arriving as bogus e-card announcements, supermarket tabloid spam, and, today, largely idiotic and not very clever "Weekly top news," as the Subject: lines read (yesterday, the line was "BREAKING new"). Message bodies contain a couple of sentences, a link to a hijacked web site, where the crooks have planted the index1.html file in the root web directory, and a further lure: "Read All (nn) breaking news and nn shocking videos," where "nn" are numbers that vary with each message.
Some of these "hot" news items are dull; others stupid. Here are some samples for your entertainment:
- Windows 7 details to be released — Technical information about the successor to Windows Vista will be revealed at two October conferences, says Microsoft.
- Madonna and Angelina Jolie in adoption war related lesbian romp! — Race to adopt as much of Africa as they can.
- George Bush Pardons Lindsay Lohan — President George W. Bush presided over Lindsay Lohan's trial and gave her a full pardon, but left the fine intact.
- Hundreds Flock to View Image of Jesus in Vomit Puddle — Hundreds of faithful Christians have lined up around the block of a bar in Long Beach, California to pray before an image in a puddle of vomit they believe represents Jesus Christ.
- Aliens Are Gay Says Astronaut — Former Astronaut Dr. Edgar Mitchell - a veteran of the Apollo 14 mission - claims aliens are gay and that they are responsible for many of the earth's ills including global warming, war, disease and The View.
- Bigcock Discovered In Georgia — After the discovery of Bigfoot in Georgia comes another discovery - Bigcock - a giant of a man in more ways than one and a beast that certainly needs taming.
Two words: Ree diculous.
And yet, there will be enough bored or curious PC users out there to make this campaign successful enough in its desire to enroll new PCs into a botnet.
Posted on August 18, 2008 at 11:42 AMAugust 14, 2008
No, Dammit, I Am NOT Subscribed
I've heard of someone putting words into your mouth—to make it appear you said something you didn't—but some of the slicker spammers (slick, as in greasy) want to put clicks into my mouse.
A spam message promoting a "webinar" unfortunately found its way into my email client (which suspected it was junk). From what I could tell in the text part of the message (I'm not downloading the images), this webinar is nothing more than a sales pitch for a piece of business software.
At the bottom of the message, in 10-pixel light grey type is the following line:
You are receiving this email as a subscribed reader of eChannelLine Daily News and have selected to receive promotions from our partners.
Every time I look up the word "subscribe" in dictionaries, I keep coming up with the same requirement of the subscriber having to actively participate in the action. Here are some excerpts from the Merriam-Webster Online Dictionary:
- to assent to
- to give consent or approval to something written by signing
- to enter one's name for a publication or service
Because I did none of the above, how can I be subscribed? If I never subscribed, how can I have then selected to receive promotions?
Sir, I allege that your pants are on fire.
I never unsubscribe from lists to which I have not subscribed. If the sender lies about my initial subscription, how can I trust him to do the right thing with my unsubscribe request? Even clicking the unsubscribe link could potentially cook my goose, because the URL is coded with my email address, which the server will track instantly.
Some governments have been toying with antispam legislation that requires senders of email solicitations to maintain an audit trail of how an email address found its way onto a list in the first place. I advocate this in Spam Wars if, for no other reason, it could expose liars in their lies (like the ones that claim you subscribed from an IP address—that happens to be located in Outer Crockistan). Unfortunately, that idea would also put extra burdens on those senders who have used correct opt-in procedures all along. As with a great deal of the U.S. CAN-SPAM law, such legislation makes business more difficult for those who do the right thing by their very natures, and fails to curb abuses by those who thumb their noses at the laws, especially from outside the U.S.
For the clown who sent today's missive, I'll simply delete all future messages right on my server. He can continue to flog my email address to his partners, inflating his list by one that is guaranteed to provide zero return. It's just my little contribution to a lower response rate his potential partners can count on.
Now that's something I can subscribe to.
Posted on August 14, 2008 at 09:32 AMAugust 06, 2008
E-Card Malware Lures, Part Umpteen
For the moment, at least, the run of supermarket tabloid and other phony news-related malware email lures appear to be on hiatus. In their place come a raft of messages claiming to have links to electronic greeting cards sent by "somebody," "a friend," or a "flatmate" (to those of us in the States, this last term is quaintly European). The crooks blew the dust off a golden oldie for this campaign.
Here are some of the Subject: lines I've seen come my way:
- This is for you.
- Open now for your eCard
- Greetings from...?
- You Have An Ecard
- Your Digital Greeting Card is waiting
- A greeting for you
The messages are simple, pointing to a variety of freshly-minted domain names that sound like they're right out of the dot-com boom days—containing word combinations such as "PostcardShop", "Lettercard," and "PostcardOnline." Here's a sample message:
Your friend has sent you an Ecard from [removed]Lettercard.com.To get your Ecard, goto the following link.
http://[removed]Lettercard.com/?e4e35ab2769300aa
(c) 2003-2008 [removed]Lettercard.com.
The copyright line is a touch that adds a sense of respectability to an unwary recipient ("Ooh, they've been in business since 2003...it must be legitimate.").
This is all pretty standard botnet fare. The destination servers are compromised PCs accessed through the fast flux technique, where each traceroute attempt (or click of the link) leads to a different IP address, making it difficult to take down the malware delivery sites.
The earliest e-card malware deliveries I remember came as attachments to email messages. Later, as delivery migrated to compromised servers, many e-card fakes abused the good names of legitimate electronic greeting card companies. The links were either to numeric IP addresses or other compromised web sites (actual addresses hidden in an HTML link). For this latest campaign, the crooks have created their own domains and fast flux network.
Regardless of distribution medium, the allure of receiving a greeting from a secret admirer is the same, olde tyme con game destined to enlist more vulnerable PCs to the botnets.
Posted on August 06, 2008 at 10:00 AMAugust 03, 2008
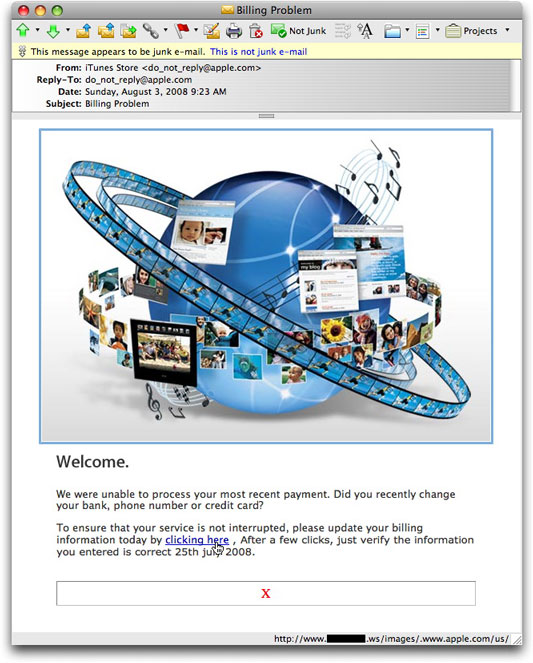
iTunes/Apple ID Phishing Campaign
I really fear that this phishing campaign will catch quite a few Apple customers off-guard. Here's what the mailing piece looks like:
With so many people these days using the iTunes store not only for music, but now downloading millions of iPhone applications (even the free ones cause the iTunes Store to generate emailed receipts), there are tons and tons of computer users of all flavors having constant contact with the iTunes Store. An alleged alert about a billing problem will get their attention.
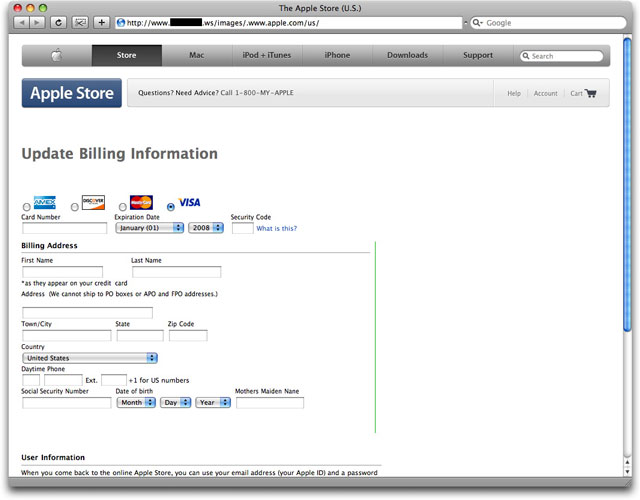
Will, however, every recipient bother to notice that the link is not to apple.com, but to [removed].ws (see status bar in the above message)? Are users advanced enough to check the message's header info to see that the message was sent from an IP address in Sweden. Worse yet, if they click on the link and see the following page, will they suspect it's not really Apple's site if they don't confirm the Address field?
Please spread the word that if any institution for which you have an online account claims to have a problem with the account, never ever follow links or URLs in emailed messages—don't even visit the phony page unless you know how to prescreen it safely for malware nastiness. Instead, log into your account through normal means (ideally through a bookmark you previously established with the legitimate site). If there is a problem with your account, you can check it out that way. In 99.99% of the cases (assuming 0.01% deadbeats), there is no problem with your account, and you can move on after deleting the phishing message.
Remember that your Apple ID provides a gateway not only to the iTunes Store, but to the Apple Store, with all its Maclicious and iPodlicious goodies that can be shipped anywhere on your credit card.
Posted on August 03, 2008 at 11:31 AM