« University Degree--No Larnin' Needed | Main | E-Profiteers Ready for Disaster »
| Home | The Book | Training | Events | Tools | Stats |
August 31, 2008
Alert Message PhishingPhishing is pretty much all the same—luring you to a web site that looks just like the login page for a financial institution or anywhere else where a username/password combination opens the gates to goodies.
If one is wary of the overt style of phishing message—the one where there is a problem with your account, and you should log in to fix it—the shields might lower for a moment when the phishing message has a bit of indirection to it. Such is the case of one I saw this morning, which tries to lure a Capital One customer to view a message within the bank's web site messaging system. The institution with which I do online banking has a Mail section of the web site, where we can communicate with each other electronically. I believe this is fairly common. And, of course, the only way you can view such messages is by logging into the site.
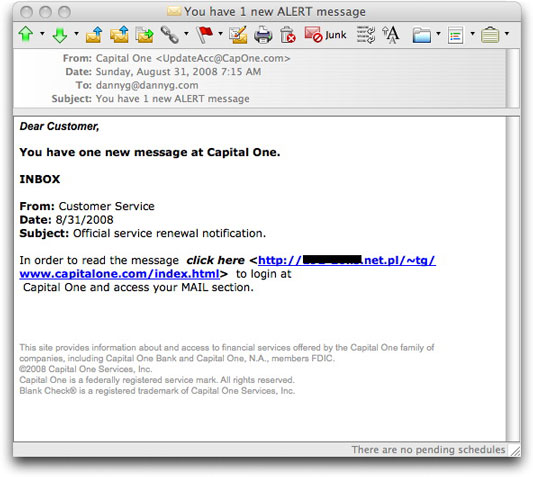
The phishing message wasn't particularly professional-looking, but here it is just the same:
Note that my email client, Microsoft's Entourage for the Mac, renders hidden link addresses in plain view. Most recipients of this phishing message would just see "click here" as a clickable link, with no visible URL. Thus, even if they knew what to look for, they might not recognize that the URL is to an IP address in Poland.
Now, I've heard of outsourcing, but humongo Capital One isn't going to host its login pages at a hacked server in Warsaw.
This serves as a reminder that if you receive any type of communication purporting to come from a financial institution with whom you do business, use your established bookmark to visit the site and log in through that page.
I also go one step further—even with bookmarked pages—to make sure that the login page has the correct URL in the Address bar and the SSL certificate is in force (at least as much as the browser reveals). I perform that check for every page that requests login credentials, even accounts that seem harmless in that they don't contain much personal information. Why am I so paranoid about this? Because if a crook gets hold of any one username/password combination, there is a good chance that that combo will open doors at other sites (no, I don't have individual combinations for each freakin' site that requires a login—and it seems as though you've gotta open an account at more and more sites these days just to get basic information). It's trivial for crooks to set up robots that try your credentials at thousands of sites. All it takes is one success to expose further personal or credit card data stored on those servers associated with that username/password pairing.
It's sad that we have to concern ourselves about this stuff. But taking a What, me worry? attitude puts you directly in the line of fire from way too many Bad Guys.
Posted on August 31, 2008 at 09:49 AM